The Problem with HTTPS
Despite the intent of ensuring safe transit of information to and from a trusted website, encrypted protocols (usually HTTPS) do little to validate that the content of certified websites is safe.
With the widespread usage of HTTPS protocols on major websites, network and security devices relying on interception of user traffic to apply filtering policies have lost visibility into page-level traffic. Cybercriminals can take advantage of this encryption to hide malicious content on secure connections, leaving users vulnerable to visiting malicious URLs within supposedly benign domains.
This limited visibility affects network devices that are unable to implement SSL/TLS decrypt functionality due to limited resources, cost, and capabilities. These devices are typically meant for home or small business use, but are also found in the enterprise arena, meaning the impact of this limited visibility can be widespread.
With 25% of malicious URLs identified by Webroot hosted within benign domains in 2019, a deeper view into underlying URLs is necessary to provide additional context to make better, more informed decisions when the exact URL path isn’t available.
Digging Deeper with Advanced Threat Intel
The BrightCloud® Web Classification and Web Reputation Services offers technology providers the most effective way to supplement domain-level visibility. Using cloud-based analytics and machine learning with more than 10 years of real-world refinement, BrightCloud® Threat Intelligence services have classified more than 842 million domains and 37 billion URLs to-date and can generate a predictive risk score for every domain on the internet.
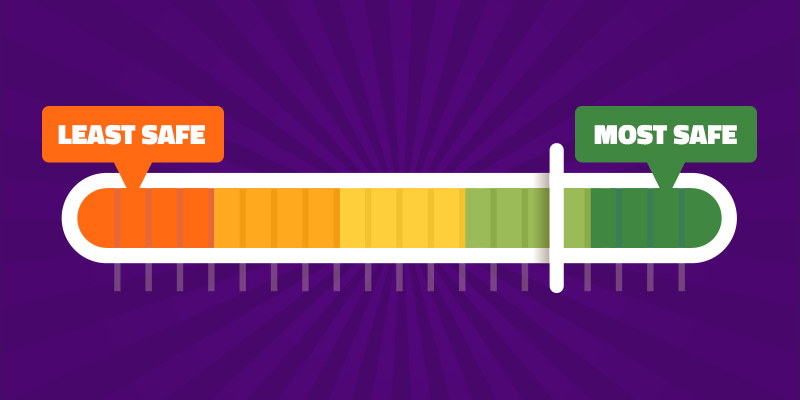
The Domain Safety Score, available as a premium feature with BrightCloud® Web Classification and Reputation services, can be a valuable metric for filtering decisions when there is lack of path-level visibility on websites using HTTPs protocols. Even technology partners who do have path-level visibility can benefit from using the Domain Safety Score to avoid the complexity and compliance hurdles of deciding when to decrypt user traffic.
The Domain Safety Score is available for every domain and represents the estimated safety of the content found within that domain, ranging from 1 to 100, with 1 being the least safe. A domain with a low score has a higher predictive risk of having content within its pages that could compromise the security of users and systems, such as phishing forms or malicious downloads.
Using these services, organizations can implement and enforce effective web policies that protect users against web threats, whether encrypted through HTTPs or not.
Devising Domain Safety Scores
As mentioned, a Domain Safety Score represents the estimated safety of the content found within that domain. This enables better security filtering decisions for devices with minimal page-level visibility due to increasing adoption of HTTPS encryption.
How do we do it?
BrightCloud uses high-level input features to help determine Domain Safety Scores, including:
- Domain attribute data, including publicly available information associated with the domain, such as registry information, certificate information, IP address information, and the domain name itself.
- Behavioral features obtained from historical records of known communication events with the domain, gathered from real-world endpoints.
- A novel deep-learning architecture employing multiple deep, recurrent neural networks to extract sequence information, feeding them into a classification network that is fully differentiable. This allows us to use the most cutting-edge technology to leverage as much information possible from a domain to determine a safety score.
- Model training using a standard backpropagation through time algorithm, fully unrolling all sequences to calculate gradients. In order to train such a network on a huge dataset, we have developed a custom framework that optimizes the memory footprint to run efficiently on GPU resources in a supercomputing cluster. This approach allows us to train models faster and iterate quickly so we can remain responsive and adapt to large changes in the threat landscape over time.
A secure connection doesn’t have to compromise your privacy. That’s why Webroot’s Domain Safety Scores peek below the domain level to the places where up to a quarter of online threats lurk.
Learn more about Domain Safety Scores, here.
Cyber News Rundown: Malicious COVID-19 Websites Surge
Malicious COVID-19 Websites Surge
In recent months, more than 136 thousand new domains have been registered that reference the current COVID-19 outbreak, many of which have yet to be flagged. A large portion of these sites are distributing phishing campaigns with fake bank login forms and inaccurate URLs, including any number of pandemic buzz words. Hopefully, some of the domain registrars will implement stricter detection for these sites to avoid the preying on of people seeking information during the outbreak.
NASA Employees Face Spike in Cyberattacks
NASA and many other federal departments are among those moving to telework and they are seeing an alarming rise in cyberattacks. These attacks include several variations of phishing campaigns designed to seek sensitive data or login credentials through requests for tax forms or disinformation about the current pandemic. NASA employees are especially seeing these types of attacks targeting mobile devices directly, since they often have fewer active security measures in place when compared to other devices.
Fingerprint Security Still Not Foolproof
A group of researchers that recently spent time studying various mobile devices’ fingerprint security measures found a shockingly high success rate from fake prints. By testing a variety of mobile devices, they learned that creating a continuously-successful print mold, while requiring a significant amount of time, could easily unlock a device before wiping features would be triggered. Advancements in fingerprint technology and better biosecurity implementations are clearly necessary.
Medical Testing Company Suffers Data Breach
After a ransomware attack by Maze authors, a major medical testing firm has had a large portion of stolen data published on the Maze “news” site. The data was leaked nearly a week after the initial attack, which the company refused to pay ransom for. While the stolen data only included victims with surnames beginning with D, G, I, and J, the testing company recommends all clients monitor their financials for any signs of fraud. This attack comes during a time where several ransomware authors pledged to avoid attacking healthcare or medical establishments, though they claim this campaign was started prior to the current outbreak.
Philippines Law Enforcement Arrests Fake News Distributors
At least 32 individuals were arrested in the Philippines for spreading fake COVID-19 information across several social media platforms. Some of the accused were reported to have instigated raids of food storage facilities after making false claims of regional shortages. The country, with over 3,000 confirmed cases of COVID-19, will maintain lockdown procedures to limit the spread of the disease until the end of April.
Cyber News Rundown: Zoom Targeted by Hackers
Zoom Video Software Targeted by Hackers
With much of the professional world now telecommuting, hackers have taken notice and are finding vulnerabilities within Zoom’s software to hijack online meetings. Over 400 new domains have been registered through Zoom in just the last month, of which many have been found to contain suspicious content or activity. Other adware variants have been found spoofing Microsoft’s Teams videoconferencing while performing malicious activities in the background.
Microsoft Takes Steps to Prevent Ransomware Attacks on Healthcare
In a push to limit the spread of ransomware throughout the healthcare industry, Microsoft has begun reaching out to hospitals that have public-facing VPNs or other remote-access services that could allow malicious activity when improperly setup. With hospitals already overwhelmed with the current pandemic, a ransomware attack shutting down their systems for any time could be devastating. In the end, it comes down to these organizations taking this notification seriously and locking down any unsecure devices or networks.
Georgian Citizens’ Data Exposed
A popular hacker forum recently received sensitive details on over 4.9 million alive and deceased citizens of the country of Georgia. It is still unclear where the database originated, but one of the users posting the leaked data claims it did not come from the country’s election commission. Much of the information stored in the database could be easily used to identify and locate any number of individuals. More worryingly, the criminals could use the data belonging to more than 1 million deceased individuals for illicit means.
Marriott Leaks Data of 5.2 Million Customers
Officials have been working over the past month to identify the source of a data leak from an internal Marriott International application, which may have compromised the data of over 5 million customers. While the app itself didn’t collect payment of personal information, it did contain basic contact info and other hotel-related information. Fortunately, Marriott International has begun offering credit monitoring services for all affected clients and has pushed a mandatory password reset for their loyalty programs.
YouTube Accounts Hacked to Promote Scams
Many YouTube accounts were recently hijacked and renamed to variations of ‘Microsoft’ while streaming hours of cryptocurrency scams, all while pretending to be Bill Gates. These types of scams used to be extremely common on Twitter but have dropped off in recent years as the platform implemented security measures, so the scammers have switched to a more forgiving platform. Microsoft commented that the hijacked channels neither belonged to them, nor were they affiliated in any way.
2020’s Most (and Least) Cyber-Secure States
For the past several years, Webroot and its partners have conducted a series of studies aimed at better understanding the attitudes, perspectives, and behaviors related to cyber hygiene in United States. This helps users determine which behaviors put them most at risk and which behavioral changes could help increase their cyber resilience.
“Cyber hygiene” can be defined as the set of behaviors which enhance (or don’t) an individual or family unit’s resilience against cyber threats including, but by no means limited to, identity theft, phishing attacks, malware infections, and other web-borne threats.
Themes in Consumer Cybersecurity for 2020
Aside from organizing U.S. states into a Cyber Hygiene Risk Index, we were also on the lookout for emergent themes in cybersecurity awareness across the country.
- Overconfidence, as we’ve seen before in previous studies, was a big theme. While the majority reported being familiar with malware (78%) and phishing scams (68%), far lower percentages were confident they could define the terms.
- Individuals who’ve progressed through life milestones—like completing a degree, buying a home, beginning to keep up with the news, or starting a family—begin to improve their risk index scores. This hard-won experience tends to belong to older demographics, parents, and those with higher levels of education and income compared to more risky peers.
- A relationship was uncovered between “tech-savviness” and risk index scores. In other words, the more technologically competent respondents in this study reported being, the more likely they were to exhibit risky behavior online.
Other Key Findings from the 2020 study
Overall, it was heartening to find that most Americans are taking at least baseline precautions for repelling and recovering from cyber-attacks. Eighty-three percent use antivirus software, and 80 percent regularly back up their data, both key indicators of an individual or family’s overall cyber resilience.
The news, however, is far from all positive. In fact, the plain truth is most Americans receive a failing grade when their cyber hygiene is examined in-depth. This is especially true when measuring avoidable risks to online data and identity. Using this metric, the average American scored a 58 percent on our Cyber Hygiene Risk Index, while no state scored higher than a D grade (67%).
Other key findings from the study:
- Almost half (49%) of Americans admit to using the same password across multiple sites.
- A spread of only 15 points separates the riskiest state in American (New York) from the least risky (Nebraska). No state scored higher than a D on our Cyber Hygiene Risk Index.
- Very small businesses (VSBs) are apt to take cybersecurity into their own hands, which often entails sharing passwords and using personal devices for work.
- Among those who do receive work devices from their employer, 55 percent use them for personal use.
- Almost a fifth (19%) of those who were the victim of a cyber-related attack, made NO changes to their online behavior
It’s not an exaggeration to call the state of cybersecurity understanding in the U.S. abysmal. Risky activities like reusing passwords, not using multiple backups, or not updating software are still rampant in every state. Given that we saw a 640 percent rise in phishing attempts over the past year, we can expect these habits will catch up with more Americans.
The above highlights represent only a small portion of the complete findings of the report. For the completed report, including the complete ranking of all 50 states according to our Cybersecurity Hygiene Risk Index metrics, download the full report.
To invest in internet security on all your devices, click here.

Lost or Stolen Device? Here’s What to do Next
It’s a nightmare, it’s inconvenient, and it’s inevitable. Losing or having your smart device stolen poses a significant, looming privacy risk— we just don’t like to think about it. However, this is an instance where hiding your head in the sand will only make you more susceptible to attack.
The personal data living on your family’s network of devices is valuable and often-times all too vulnerable. Having a worst-case-scenario plan in case of device loss or theft could save you time, money, and heartache.
So, we’ve put together a list of best practices in case the worst does happen, you’ll be prepared to prevent an identity theft disaster.
General Best Practices
Preparing yourself and your devices before they are stolen is the fastest way to avert potential breaches. Consider:
- Keeping a “Find My” app turned on for all devices. This is the best way to locate and remote wipe devices.
- Making sure your devices are secured behind individualized pin codes, fingerprints, or Face ID. This will slow down thieves trying to access your device.
- Use strong, individualized passwords on all accounts, including email and banking apps. Don’t have the time? Use a trusted password manager to automate password creation. This will help limit the scope of any breach.
- When a device is stolen, act quickly. The faster you respond, the more effective the following steps are likely to be. If the thief turns the device off, or removes the battery, you’ll be unable to remotely wipe the device.
Learn how to get automatic protection over any network, even unsecured WiFi.
Android Devices
Here is what Android users should do in case of device theft.
- First, locate your device. Go to android.com/find and sign into your Google Account.
- If you have more than one device, choose the one you’re looking for from the list at the top of the screen. The lost/stolen device will receive a notification, so you should act quickly.
- On the map on your screen, you’ll be shown information about the phone’s location. Remember this is approximate and might not be neither precise nor accurate. If your phone can’t be found, you’ll see its last known location (if available).
- Now, if you’re certain your device has been stolen, you can click “Enable lock & erase” to erase your device. But be careful. After you erase your device, Find My Device will no longer work, so make sure you are certain.
- If you believe your phone is just lost, and not stolen, you have a few options. “Lock” will lock your phone with your PIN, pattern, or password. If you don’t have a lock in place, you can set one. To help someone return your phone to you, you can also add a message or phone number to the lock screen.
An important note: If you happen to find your phone after you have erased it, you’ll likely need your Google Account password to use it again.
iOS Devices
Here is what iOS users should do in case of device theft.
- Sign into icloud.com/find or use the Find My app on another Apple device.
- Next, you’ll need to locate your device. Select the one you’re searching for to view its location on a map.
- You’ll be presented with a few options here. “Mark As Lost” will remotely lock your device, allow you to display a custom message with your contact information on the missing device’s lock screen, and track the device’s location. If you have added Apple Pay payment options, the ability to make payments using Apple Pay on that device will be suspended for as long as the device is in Lost Mode.
- If you’re certain your device has been stolen, select “Erase your device.” When you erase your device remotely, all of your information is deleted, and you will no longer be able to locate it with the Find My app or Find iPhone on iCloud.com. Make sure your phone is not recoverable before taking this step.
Device Theft Wrap-Up
After you have protected your most sensitive information with the steps above, take just a few more steps to fully wrap the crisis up.
- Report your lost or stolen device to local law enforcement. Law enforcement might request the serial number of your device. This can often be found on the original packaging.
- Report your stolen device to your wireless carrier. They will disable your account to prevent calls, texts, and data use by the thief. If you have insurance through your carrier, this is the time to begin filing a claim as well.
- Reset all of your passwords, including your Google Account and Apple ID. After a device is stolen, you can never be certain of how far the breach has penetrated. The good news is, if you are using a secure password manager, this should be pretty quick!
- Any accounts that had 2FA access, when you first set up the account would have had you save the private key or one time code. This key will allow you back into your accounts without needing the device and will allow you to remove the account from the device.
- Alert your banking providers to the potential breach and monitor your bank accounts and credit cards for suspicious activity. If you see any, get ahead of the issue and cancel and replace all of your bank cards. This will prevent the financial breach from affecting multiple accounts.
A stolen device is a headache, but it doesn’t have to be a disaster. If you have a plan in place for a worst-case scenario, you’ll be able to act quickly and confidently. Do you have device theft tips that we missed here? Let us know on the Webroot Community.
Cyber News Rundown: WHO Under Cyberattack
World Health Organization Sees Rise in Cyberattacks
Officials for the World Health Organization (WHO) have announced that many of their sites and servers have been under attack by unsuccessful hackers trying to capitalize on the latest health scare. The attack stemmed from the use of several malicious domains that attempted to gain sensitive information and credentials from WHO employees. Thousands of other malicious domains have been created over the last few weeks to exploit the uninformed victims of the Coronavirus outbreak.
TrickBot Sidesteps 2FA on Mobile Banking Apps
The creators of TrickBot have developed a new mobile app called TrickMo, that can silently circumvent two-factor authentication that is used by various mobile banking apps. The malicious app is used mainly to intercept authentication tokens, once it is installed on the victim’s device. Currently, the TrickMo app is targeting German individuals and using the name “Security Control” to disguise any ulterior motives, and even sets itself as the default SMS app, in order to steal additional information.
Google Play Finds 56 New Malicious Apps
Over 56 new malicious apps have been spotted on the Google Play store, with a combined 1.7 million installations on devices across the globe. To make matters worse, a large portion of the apps were targeted specifically at children and used native Android functionality to imitate typical user actions to boost ad revenue. Many of the apps took extreme measures to avoid being uninstalled by the users, though Google itself has since removed all of the related apps from the Play Store.
Fake Coronavirus Vaccine Sites Shutdown
A website offering fake Coronavirus vaccine kits that were claiming to be approved by the WHO has been shutdown following a ruling by a federal court. The operator of the site has been accused of committing fraud and the hosting service has received a restraining order to stop public access to the site. The site in question, “coronavirusmedicalkit.com” offered the fake kits with users only paying for shipping and entering their payment card data.
Tupperware Website Breached
The main website for Tupperware was recently hacked and used to host Magecart code to steal payment card information. The malicious code was first discovered at the end of last week, but was still active nearly a week later, even after multiple attempts to contact the company. Magecart has been a wide-spread issue for online retailers over the last couple years, and still maintains a large presence due to their ease of use and continuing success.
Hackers: Fact vs. Fiction
Have you ever watched a movie and seen a character doing something you know how to do, and thought to yourself, “jeez, that’s totally wrong. Couldn’t they have done a little research?”
That’s exactly what hackers think when they watch movies, too. For most of us, the image that comes to mind when we hear the word “hacker” is pretty stereotypical: probably a young guy wearing a hoodie and headphones, in a basement, surrounded by fancy displays full of unintelligible code that looks like it’s straight out of the 1999 movie the Matrix, with only nefarious intentions at heart. We have that image for a reason; that’s how many films have portrayed such characters.
But, just like those times when you see a movie or TV character totally screwing up the thing you know how to do, this stereotype just isn’t accurate. Not all hackers have the same motives. In fact, not all of them are even “bad guys.” Misunderstanding leads to fear, and acting out of fear is never a good thing. If you want to stay safe from cyber-related risks in the modern world, it’s important to understand the myth vs. the reality.
Common Myths
- Every hacker is a criminal with evil intentions, who wants to break systems, steal information, steal money, cause destruction, commit cyber-espionage, or engage in other illegal activity online
- All hackers are male
- Hackers work alone, exclusively
- Hackers have to work really fast, or else they’ll get caught by the authorities
- There isn’t much money to be made, so hackers have to send lots of attacks to make their efforts worthwhile
- Hackers only go after large corporations and government systems.
The Truth about Hackers
- The word “hacker” really just refers to an individual who uses computers, networking, or other technology and related skills to accomplish a particular goal. That goal may not have anything to do with criminal activity, even if it involves gaining access to computer systems. In fact, some hackers use their skills for good, helping businesses and individuals become better able to prevent attacks by malicious hackers
- Just like their varied motivations, hackers come in all shapes and sizes. While the average self-proclaimed “hacker” is likely to be male and under 35, they can be of any gender, age, ethnicity, etc.
- As with most pursuits in life, hacking tends to be most productive when conducted by a team. It’s actually pretty common for hackers to be involved in larger groups or organizations. Some of them even have salaries and set holidays, just like the rest of us in the non-hacking working world, and may have customers and sales arrangements that include things like reseller portals and component rental
- A rushed job is a bad job, plain and simple. Hackers have the time to take a slow and methodical approach to accomplish their aims. They know they’re more likely to be successful if they research targets, do recon, and take the time to work out the best angles of approach. In contrast, victims of attacks typically have a very short amount time in which to react or recover, especially in the case of ransomware.
- There’s a lot of money to be made in hacking. As of the most recent Cost of a Data Breach Report, the average cost of a data breach is $3.92 million, and nearly 3 in 4 (71%) of breaches are financially motivated. In fact, the average hacker can earn up to 40 times the median wage of a software engineer.
- Although large corporations can be desirable targets, they often have larger security budgets and teams of security professionals dedicated to protecting the business. You might think hackers have bigger fish to fry, but small and medium-sized businesses (SMBs) are prime targets. More than 70% of cyberattacks target small businesses. In particular, more attacks are focusing on MSPs specifically because of their SMB clients. Breaching a single MSP could open up data access to their entire client base.
So what do you do?
You’re already on your way. By better understanding the true methods and motivations behind the myths, you can begin to lock down your business and protect your customers against today’s biggest threats. If you haven’t already, check out our Lockdown Lessons, which include a variety of guides, podcasts, and webinars designed to help MSPs and businesses stay safe from cybercrime.
The next step is to ensure your security stack includes a robust endpoint protection solution that uses real-time threat intelligence and machine learning to prevent emerging attacks. Learn more about Webroot® Business Endpoint Protection or take a free trial here.
Cyber News Rundown: DDoS Strikes U.S. Health Department
DDoS Attack Strikes U.S. Health Department
Amidst the panic caused by the novel coronavirus, millions of people began navigating to the U.S. Department of Health’s website to find more information on the illness, but instead found the site to be offline after a DDoS attack overwhelmed its servers. This comes as only one of many unfortunate attacks that are being used to spread disinformation and panic, as well as delay healthcare workers from assisting patients or working towards slowing the overall spread of the illness.
Netfilim Ransomware Uses Old Code but New Tactics
Researchers have been tracking the spread of a new ransomware variant known as ‘Netfilim,’ which has been on a steady rise since February. By utilizing a large portion of code from another ransomware variant, Nemty, it has a quick distribution rate and keeps with the promised threat of releasing all stolen data within a week of encryption. It does differ from Nemty in its payment process, however, relying solely on email communication rather than directing the victim to a payment site that is only accessible through a Tor browser, leaving .NETFILIM as the appended extension for all encrypted files.
US Loan Database Exposed
A database containing millions of financial documents and other highly sensitive information was found freely accessible through an unsecured Amazon web service bucket. Contained within the 425GB of data were credit reports, Social Security numbers, and personally identifiable information for thousands of individuals and small businesses. The database itself is connected with a loan app that was developed by two major New York funding firms, Advantage Capital and Argus Capital.
Malicious Coronavirus Mapping Apps Spreading More than Misinformation
Many malware authors have been capitalizing on the recent coronavirus (COVID-19) epidemic by way of phishing campaigns and newly renamed ransomware variants. Their latest endeavor is an app used to reportedly “track” the spread of coronavirus across the globe, but has instead been dropping malicious payloads on unsuspecting victims’ devices. Some of these apps can lock devices and demand a ransom to unlock it, while others deliver full ransomware payloads that can encrypt and upload any files to another remote server. Fortunately, researchers worked quickly to engineer up a decryption key for victims.
Magecart Group Targets NutriBullet Website
Following a network breach in late February, Magecart scripts were found to be actively stealing payment card information from NutriBullet websites up to present. The specific organization, known as Group 8, has been using similar Magecart scripts for over two years and have claimed over 200 unique victim domains. Despite several contact attempts from the researchers who found the skimmers, no changes have been made to the affected sites, leaving current and new customers vulnerable.
Staying Cyber Resilient During a Pandemic
We’re all thinking about it, so let’s call it out by name right away. The novel coronavirus, COVID-19, is a big deal. For many of us, the structure of our lives is changing daily; and those of us who are capable of doing our work remotely are likely doing so more than we ever have before.
It’s not likely that cybercriminals will cut us a break during this difficult time of quarantine and pandemic outbreak. If anything, we will only see an increase of attacks and ransom amounts since this is when infrastructures of modern civilization are needed most but have the least amount of time to react and debate on paying or negotiating the price. Also, many of the cybercriminals who breach and ransom as a side job are now forced to either work from home or their shifts are completely canceled, leaving them with more time and motivation to make up their income elsewhere. This is a prime circumstance for increased cyberattacks, and individuals and businesses should be hyper aware of their behavior both online and offline.
Not only are phishing and ransomware attacks, which tend to capitalize on current headlines, on the rise, but business email compromise (BEC) is also up. BEC is when a cybercriminal breaks into a legitimate corporate email account and impersonates the real owner to defraud the business or its partners, customers, or employees into sending money or sensitive data to the attacker. With so many more people working remotely and less able to verify emailed requests from coworkers as legitimate, you can imagine how this threat could run rampant.
What follows are cyber resilience tips for staying safe, both for individuals in their personal lives and for businesses with remote workers.
Cyber Resilience Tips for Individuals
What to do:
- Find information about COVID-19 at the official sites of the World Health Organization (WHO) or the U.S. Center for Disease Control (CDC).
- Ensure you have antivirus protection on all your devices, and that it’s up to date.
- Exercise caution when providing personal information. Be very suspicious of requests for personal information that occur via email, phone, text message, or social media message.
What NOT to do:
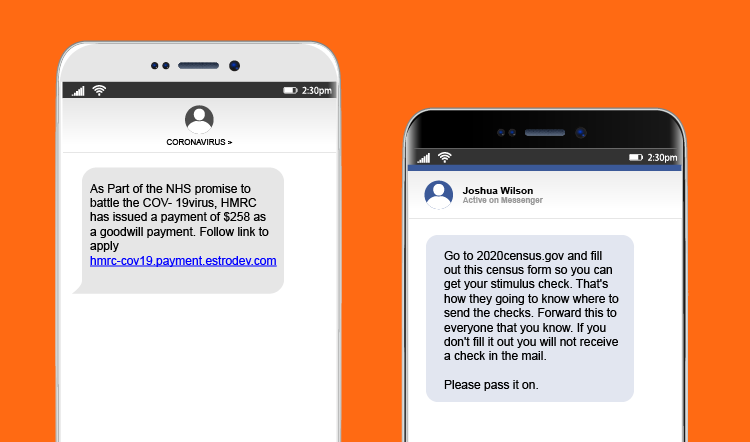
- Do not open emails regarding COVID-19 from unknown senders. These could be phishing scams.
- Do not click on links in emails regarding COVID-19. Email links can be used to spread computer viruses and other malware.
- Do not download or open email attachments from unknown senders. These could contain viruses and other malware.
- Do not click on links in social media messages, even if they are from someone you know. Your contacts’ accounts may have compromised.
- Do not click on ads or social media posts regarding COVID-19. They may be fake and contain malicious content.
Cyber Resilience Tips for Businesses
The best defense is prevention. To prevent, you have to plan ahead.
Be prepared for remote work conditions.
Life gets in the way. Between severe weather, personal emergencies, illness, and worker wellbeing, employees need to be able to work from home for a variety of reasons.
- Enable everyone to work from off-site locations.
- Ensure all employees feel welcome to work from home when needed.
- Install robust endpoint security on all devices so employees and data stay safe.
- Give all employees access to a VPN to help protect corporate data, wherever they connect.
- Implement measures to back up data saved on local devices while workers are remote.
- Add collaboration tools so teams can continue to work together while physically separated.
- Warn employees about phishing and BEC. Share the Cyber Resilience Tips for Individuals we included above, and encourage employees to be extra vigilant about unexpected invoices or other financial requests. Even when we’re all remote, it only takes a quick phone call to verify the legitimacy of an unusual request.
Be prepared for threats to your data.
From modern cyberattacks to natural disasters and physical damage, there are a lot of threats to your critical business data.
- Protect all endpoint devices, including computers and servers, with next-generation cybersecurity solutions.
- Create a data backup process for data availability at alternate business locations when the main office is closed.
- Implement high-availability data replication and migration safeguards ensure data is available, no matter what happens.
- Add protection for Microsoft Office 365 and other collaboration platforms so content stored and shared in the cloud stays safe.
- Use a solution that includes device monitoring, tracking, and remote erase functionality so lost or stolen devices can be located or wiped.
- Empower employees to become a strong line of defense by educating them about cybersecurity and data safety risks.
- Make sure to use RDP solutions that encrypt the data and use 2FA authentication when remoting into other machines as the presence of an open port with RDP was associated with 37% greater likelihood of a ransomware attack.
Our Commitment to Resilience
Rest assured, we’re practicing what we preach. All of our global employees are able to work from home securely. In these crazy times, it’s more important than ever to redouble our focus on helping each other. At Webroot, we feel it’s our social responsibility to do what we can to keep one another safe, both online and offline. We hope you’ll join us in our commitment to resilience. Stay safe and healthy, everyone.

World Backup Day: A Seriously Good Idea
“Cold Cuts Day,” “National Anthem Day,” “What if Cats and Dogs had Opposable Thumbs Day”…
If you’ve never heard of World Backup Day, you’d be forgiven for thinking it’s another of the gimmicky “holidays” that seem to be snatching up more and more space on the calendar.
(Did you know that single quirky duo, Ruth and Tom Roy, are responsible for copyrighting more than 80 of these holidays, including Bathtub Party Day, held annually on December 5?)
Not so, though, for World Backup Day. While, according to WorldBackUpDay.com, it was founded by a few “concerned users” on the social media site reddit, the day’s dedication is a decidedly serious one.
March 31 was established as “a day for people to learn about the increasing role of data in our lives and the importance of regular backups.”
Each April Fool’s-eve, the site invites humans all over the planet to not be fools and to back up their data. In celebration of World Backup Day, we sat down with Webroot Product Marketing Director George Anderson to see how users can ensure they stay cyber resilient by adhering to good data backup practices.
For World Backup Day, what’s the one piece of advice you’d give to a small or medium-sized business? An everyday computer user, like a parent?
Losing data used to be something that happened because a hard disk failed, a device was lost or stolen, or some other unforeseen accident made a device unusable. These remain risks. But these days, it’s just as likely your data is being held for a ransom or some nasty infection has destroyed it for good.
Up-to-date backups are essential. Remember: it’s not if something will happen to your data, but when. So, prepare for the unexpected. Easily restored data backups let you be more resilient against cyber-attacks and better able to recover customer data, financial information, business-critical files, and precious memories. Anything irreplaceable should be regularly backed up without a second thought, or worse, a passive “it won’t happen to me.”
Thankfully, many of today’s backup solutions are easy-to-use and affordable. My advice is to not become the next data loss or ransomware victim. Simply invest a little into backup software and rest easy knowing you’re covered.
Why is it important that World Backup Day be celebrated year-round? How can we keep the spotlight on backup and cyber resilience?
For those with backup technology in place, World Backup Day should be a reminder of the importance digital information plays in our daily lives, and to check up on existing backups to make sure they are being properly made and that they can be easily restored.
Unfortunately, “set-and-forget” technologies like automated backup and recovery solutions are rarely revisited – until we need them to be 100 percent. So, checking regularly that they’re correctly configured and working properly is important.
For those not currently backing up their data regularly, the day should bring into focus a glaring hole in your home or business data security. Perhaps take the time to consider the impact losing your data forever would have? Then take action.
Back up is no longer a “nice-to-have” capability. In a world where our lives are increasingly digital and our data is threated at lots of different angles, backup is crucial aspect of data security.
What’s the difference between backup and cyber resilience? Should companies be putting more of an emphasis on cyber resilience?
Backup is a key component of cyber resilience, though it’s not the only one. But it does make what could be an existential event, like a total loss of business or personal data, a setback that can be recovered from.
Cyber resilience is first and foremost about detecting, protecting and preventing attacks on your data in the first place. But then, even if your attack detection, protection and prevention defenses fail, your backup and recovery solutions ensure your data isn’t lost for good.
Cyber resilience is not a choice between security and backing up your data. It’s about covering both bases, so if a serious data compromise does occur, recovery is quick and painless to the business
This World Backup Day, take the pledge:
“I solemnly swear to back up my important data and precious memories on March 31st.”
And don’t forget to make sure that both cybersecurity and backup and recovery solutions are in place for your business or home office.
Cyber News Rundown: Paradise Ransomware
Paradise Ransomware Spreading Through Unusual Attachments
While Paradise ransomware isn’t new to the scene, the latest methods it’s using to spread are a bit surprising. Though it sticks to using email for transmission, it now offers up an IQY attachment instead of a typical word document or excel spreadsheet. These can make a quick connection to a malicious URL prompting the download of the actual ransomware payload. What makes these especially dangerous is that they appear to be simple text files with no internal malicious code, just commands for retrieving it, so it isn’t typically picked up by most security services.
Entercom Data Breach
One of the world’s largest radio broadcasters, Entercom, recently revealed it had fallen victim to a data breach. It was initiated through a third-party service that stored login credentials for Radio.com users and could affect up to 170 million customers. This breach would be the third security incident targeting Entercom in just the last six months. The company has already fallen victim to two separate cyberattacks that caused their systems to be disrupted. Entercom has since implemented several additional security measures and prompted all users to change their passwords, especially if reused on other sites.
Western Union Begins Fraud Payback
Western Union has started paying back roughly $153 million to victims of fraudulent transactions processed by the firm’s payment systems. According to the U.S. Department of Justice, several employees and owners of Western Union locations were involved with allowing these fraudulent payments to be made and failing to properly discipline those individuals. The payback terms have started with 109,000 victims worldwide and will eventually total $586 million in reimbursements.
Whisper App Exposes User Data and Messages
The anonymous messaging app Whisper was recently revealed to own an unsecured database containing a large amount of personal customer records. Two independent researchers first discovered the database, containing over 900 million records and reaching back nearly eight years, and quickly contacted Whisper. The company then locked down the unrestricted access. Though financial or personally identifiable information were not included in the database, the app does track location data that could be used to narrow down a specific user’s location to a home or place of work.
Online Shopper Records Leaked
Up to 8 million sales records were discovered in an unsecured MongoDB database that has been misconfigured for an undetermined amount of time. The researcher who found the database quickly contacted the third-party servicing company that managed the database and it was secured five days later. The database contained roughly four million records pertaining to Amazon UK and eBay alone, comprised mainly of payment and contact information for online shoppers.
5 Security Tips for Setting Up a New Device
The last thing you want to do when you get a new computer, mobile device, or tablet is spend a lot of time setting it up. But like any major appliance, these devices are something you want to invest a little time setting up properly. Often, they’re not cheap. And you want them to last. So, before you jump online and start shopping, gaming, or browsing, take some time to ensure your device is ready for anything the internet can and will throw at it.
There’s a caveat, though, of which Webroot security analysts are quick to remind users. “Even if you’ve taken every precaution when it comes to configuring your new device,” says Webroot Threat Research Analyst Connor Madsen, “it’s important to remember that proper online etiquette is essential to your security.”
“Clicking on links that don’t seem quite right, opening attachments from unknown senders, or otherwise ignoring your best security instincts is a good way to undermine any effective online security protection.”
Connor Madsen, Threat Research Analyst
For best results, in addition to the warning issued above, here are five tips for making sure your device, and the important files stored within it, are safe from common risks.
#1 – Update software
The first thing you’ll want to do is make sure the operating system on all your devices is up to date. One of the most common methods hackers use to launch attacks is exploiting out-of-date software. Failing to install periodic patches and software updates leaves your new device vulnerable to the numerous threats lurking on the web. Depending on how old and out-of-date your device is, it may take a while for applications to update. However long it takes, it’s preferable to the hassle and expense of having to undo an infection after it’s bypassed your security perimeter.
#2 – Enable firewall
Speaking of your security perimeter, the first line of defense along that perimeter is your firewall or router, if you’re using one. A router works as a firewall for the devices connected to it. But, if you’re not using a router, make sure your firewall is enabled to protect you from malicious traffic entering your network. This is different from an antivirus, which protects you from malicious files.
#3 – Install antivirus
Malicious files can be disguised as attachments in an email or links on the web, even the apps you download. So, it’s important to have an antivirus solution to protect your new computer. Malware attacks like ransomware make constant news these days. And everyone’s a target, from individual users to local businesses, hospitals, or municipalities. The cybercriminals launching these attacks are constantly changing, evolving threats to be more sophisticated and harder to detect. That’s why it’s important to keep your antivirus as up-to-date as your operating system and other applications.
#4 – Back up
Once you have your operating system and applications updated, your firewall enabled and an effective anti-virus application, you can begin using your computer safely. But there’s one more thing you need to consider if you’re going to be creating and storing important documents and work material on your new machine. Any new files on your computer will need to be backed up. That’s when you make a copy of the contents on your machine and store it in a safe place just in case you lose the original or it becomes infected by a virus. Since no single security solution can be 100 percent effective, it’s best to have a backup copy of important files. The thing is, you don’t want to have to decide what’s worth backing up and what’s not. That’s far too labor-intensive and it introduces the possibility of human error. Your best bet is to use a solution that’s designed for this purpose. A true backup solution protects files automatically so you don’t have to remember what you copied and what you didn’t. It also greatly simplifies file recovery, since it’s designed for this purpose.
#5 – Wipe your old device
Just because you have a shiny new toy doesn’t mean you can forget about your old machine. Before you relegate it to the scrap heap, make sure there’s nothing important or confidential on it you wouldn’t want someone to have access to. You could have old passwords saved, tax records, or sensitive work documents that you wouldn’t want shared. The best way to do this is to wipe the contents of your old device and reinstall the operating system from its original state.
Seem overwhelming? If so, it’s best to remember that one of your strongest cybersecurity tools is common sense. While things like an antivirus and backup strategy are essential for maintaining good cyber hygiene, remember Madsen’s advice.
“If it seems like an offer that’s too good to be true, or something about a link or file just doesn’t seem right, don’t click or download it. Trust your instincts.”