Cyber News Rundown: First GDPR Fine Issues in Poland
First GDPR Fine Issued in Poland
The first fine issued from the Polish privacy regulator has been issued to an unnamed firm for quietly gathering personal data for over 6 million Polish citizens and using it for commercial gains without consent. The fine of £187,000 was generated after officials learned that only 90,000 individuals had been contacted via email, as the company had seemingly no other low-cost options for contacting the remaining millions of affected citizens.
ASUS Update Utility Used as Backdoor
ASUS recently confirmed that their Live Update utility for notebooks was compromised, leading to at least 500,000 machines being affected by malicious code. While this attack was focused on a only a couple of specific servers, the announcement came nearly a month after the company was told by researchers about the issue and it continued to push the malware via Live Update. Fortunately, ASUS resolved the issue with their latest update and has provided a tool to help customers determine if they’re still at risk.
Microsoft Takes Domains Back from Hackers
Microsoft has been working for some time to combat state-backed hackers by regaining control of nearly 100 domains that have been used in spear-phishing attacks across the globe. Many of the domains used keywords relating to more popular companies to steal login credentials for the sites they mimicked By obtaining court orders for the domains, Microsoft has continued its long-term legal battle, with help from domain registrars, to take these scams offline.
Facebook Hack Exposes 110,000 Australians
After the Facebook hack in September of last year the personally identifiable information for over 100,000 Australians was compromised. While some users saw only their name and email address exposed, others had their search history, recent location check-ins, and more information available to the hackers. Facebook began notifying the proper regulatory officials four days after they themselves became aware of the breach that had begun more than a week earlier.
Cryptocurrency Exchanges Hacked
With an estimated combined loss of over $46 million in cryptocurrency, two exchanges have come forward about hacks that have taken them offline as investigations unfold. DragonEx initially announced that an attack had occurred over the weekend and that they were able to regain some of the stolen funds. They then posted the wallet addresses that had received stolen funds in hopes of having the accounts frozen and the flow of currencies stopped. The second hack on CoinBene has been denied by the company as they haven’t lost any funds, but users were able to trace significant amounts of several cryptocurrencies dumped into other markets not long after the attack on the exchange took place.
Lock Down Your Digital Identity
The last decade has been one of digital revolution, leading to the rapid adoption of new technology standards, often without the consideration of privacy ramifications. This has left many of us with a less-than-secure trail of digital breadcrumbs—something cybercriminals are more than aware of. Identity theft is by no means a new problem, but the technology revolution has created what some are calling a “global epidemic.”
Securing your digital identity is more important now than ever, and Webroot can help you start.
What is a Digital Identity?
The first step in locking down your digital identity is understanding what it is. A digital identity is the combination of any and all identifying information that can connect a digital persona to an actual person. Digital identities are largely comprised of information freely shared by the user, with social media accounts generally providing the largest amount of data. Other online services like Etsy and eBay, as well as your email and online banking accounts, also contribute to your digital identity. Realistically, any information that can be linked back to you, no matter how seemingly inconsequential, is part of your digital identity.
Digital Identity Theft
Digital identity theft occurs in several ways. A common tactic is social media fraud, where a hacker will impersonate a user by compromising an existing social media account, often messaging friends and family of the user requesting money or additional account information. If unable to gain full control of a genuine social media account, identity thieves will often set up a dummy social media account and impersonate the user using it.
A less widely-known form of digital identity fraud is internet-of-things (IoT) identity theft, where an attacker gains access to an IoT device with weak security protocols and exploits it to gain access to a higher priority device connected to the same network. Another growing threat is “SIM swapping”— an attack that involves tricking a mobile provider into swapping a legitimate phone number over to an illegitimate SIM card, granting the attacker access to SMS-enabled two-factor authentication (2FA) efforts.
Even those who don’t consider themselves targets should be aware of these tactics and take steps to lock down their digital identities.
Locking it Down
Reviewing your social media accounts’ privacy settings is one of the easiest things you can do to cut opportunistic identity thieves off from the start. Set your share settings to friends only, and scrub any identifying information that could be used for security clearance — things like your high school, hometown, or pets’ names. Only add people you personally know and if someone sends you a suspicious link, don’t click it! Phishing, through email or social media messages, remains one of the most prevalent causes of digital identity theft in the world. But your digital identity can be compromised in the physical world as well — old computers that haven’t been properly wiped provide an easy opportunity hackers won’t pass up. Always take your outdated devices to a local computer hardware store to have them wiped before recycling or donating them.
The Right Tools for the Job
This is just the start of a proper digital identity lock-down. Given the sensitive nature of these hacks, we asked Webroot Security Analyst Tyler Moffitt his thoughts on how consumers can protect their digital identities.
“Two-factor authentication in combination with a trusted virtual private network, or VPN, is the crown jewel of privacy lock-down,” Tyler said. “Especially if you use an authenticator app for codes instead of SMS authentication. A VPN is definitely a must… but you can still fall for phishing attempts using a VPN. Using two-factor authentication on all your accounts while using VPN is about as secure as you can get.”
2FA provides an additional level of security to your accounts, proactively verifying that you are actually the one attempting to access the account. 2FA often uses predetermined, secure codes and geolocation data to determine a user’s identity.
Because 2FA acts as a trusted gatekeeper, do your research before you commit to a solution. You’ll find some offerings that bundle 2FA with a secure password manager, making the commitment to cybersecurity a little bit easier. When making your choice, remember that using SMS-enabled 2FA could leave you vulnerable to SIM swapping, so though it is more secure than not using 2FA at all, it is among the least secure of 2FA strategies.
VPNs wrap your data in a cocoon of encryption, keeping it out of sight of prying eyes. This is particularly important when using public WiFi networks, since that’s when your data is at its most vulnerable. Many VPNs are available online, including some free options, but this is yet another instance of getting what you pay for. Many free VPNs are not truly private, with some selling your data to the highest bidder. Keeping your family secure behind a VPN means finding a solution that provides you with the type of comfort that only comes with trust.
The two things that only you can do to keep your identity secure? Constant vigilance and continuous education. Visit the Home+Mobile page on the Webroot blog for a host of resources to help keep you and your family safe online—at home and on the go.
Cyber News Rundown: Hacker Exposes 26 Million Personal Records
Gnosticplayers Adds 26 Million More Records for Sale
After the first 3 major data dumps, which totaled over 600 million records, the hacker known as Gnosticplayers has released his latest cache of data, which contains at least 26 million personal user records. These data caches hold customer information for 32 companies overall and have been obtained over just the past couple months, making the data that much more lucrative. The hacker claims these breaches are done simply out of frustration that security is still not being taken seriously by many major companies from across the globe, which may explain why the price tag for each dump is so low.
Hackers Set Off Tornado Sirens in Texas Towns
At least 30 tornado warning sirens in two Texas towns were triggered in the early morning hours by an unknown hacker. While officials quickly shut down the sirens, they did so just 24 hours prior to a major storm during which they might have needed to use these critical emergency systems. This attack is very similar to one that affected the entire Dallas area in 2017, when hackers successfully compromised a radio system that set off over 100 tornado sirens across the city.
Marketing Firm Exposes 230 Million Records
Another misconfigured Amazon database, this time belonging to Exactis, carries the blame for a data breach that could affect at least 230 million individuals, with more data on 110 million individual records tied to businesses. While it is still unclear exactly how long the database was accessible, the company and an external security auditor maintain that the data was not accessed maliciously during its time online, though the independent researcher who first discovered the database reports that the data may have been spotted for sale on the dark web.
Ransomware Cripples Major Aluminum Manufacturer
Norsk Hydro, a major Aluminum producer, suffered a ransomware attack that successfully shut down a large portion of the company’s operations. The attack forced the company to switch to manual operations at all of its facilities around the world, and temporarily take down their website while they worked to restore their systems from backups. Fortunately, the company retains backups for their major operations, so normal production should resume within the week.
Gearbest Leaks 1.5 Million Customer Records
Following the trend of unprotected databases, researchers recently found yet another one, this time belonging to Gearbest (a Chinese e-commerce site). This database contained unencrypted personal records for over 1.5 million customers around the globe, including payment data, ID and passport info, and even data that could compromise Gearbest itself, as URLs for an internal software platform were also exposed. The company has since claimed that the number of exposed records is much smaller than originally posted. However, they also maintain that they use strong encryption on all stored data, despite this latest evidence to the contrary.
HTTPS: Privacy vs. Security, and Where End Users and Security Culture Fit In
Since the dawn of IT, there’s been a very consistent theme among admins: end users are the weakest link in your network, organization, security strategy, fill-in-the-blank. We’ve all heard the stories, and even experienced them first-hand. An employee falls for a phishing scam and the whole network is down. Another colleague torrents a file laced with malware. Or maybe it’s something less sinister: someone wants to charge their phone, so they unplug something from the only nearby outlet, but what they unplug is somehow critical… help desk tickets ensue.
But when it comes to security issues caused by human error, it’s not necessarily always the end user’s fault. Cyberattacks are getting more and more sophisticated by the second, and all of them are designed to either circumvent defenses or appear totally legitimate to fool people. One of the major advances of this type that we’ve seen is with phishing sites and the use of HTTPS.
HTTPS: The Beginning
While HTTP is the foundation of all data exchange and communication on the internet, it wasn’t designed for privacy. Transmitting information on the web using HTTP is kind of like sending a postcard; anybody who handles that card can read it. HTTPS was supposed to be a way of adding privacy to protect users and sensitive information from prying eyes.
At first, you’d only see HTTPS on financial or health care websites, or maybe the cart page on a shopping site, where the extra privacy was necessary. And back then, getting a security certificate was much harder—it involved significant costs and thorough security checks. Then, a few years ago, most web browsers started requiring security certificates for every website, or else they’d throw up a scary-looking warning that the site you were trying to visit might be dangerous. That trained us to look for (and trust) HTTPS.
A False Sense of Security
These days, when we see HTTPS at the beginning of a URL or the accompanying lock icon in our browser’s address bar, we’ve been conditioned to think that means we’re safe from harm. After all, the S in HTTPS stands for “secure”, right? But the issue is that HTTPS isn’t really about security, it’s about privacy. That little lock icon just means that any information we transmit on that site is encrypted and securely delivered to its destination. It makes no guarantees that the destination itself, is safe.
If you unwittingly end up on a well-faked phishing copy of your banking website and see the lock icon, it’s natural to assume that you’re in the right place and all is well. Except when you try to log in, what you’re really doing is securely transmitting your login credentials to an attacker. In this case, HTTPS would’ve been used to trick you.
The Bad Guys and HTTPS
Malicious actors are always looking for new ways to trick end users. Because so many of us think HTTPS ensures security, attackers are using it against us. It’s no longer difficult to obtain a security certificate. Attackers can do so very cheaply, or even for free, and there’s really no background or security check involved.
As I mentioned during my talk on HTTPS at this year’s RSA conference, almost half a million of the new phishing sites Webroot discovered each month of 2018 were using HTTPS. In fact, 93% of phishing domains in September and October alone were hosted on HTTPS sites. When you think about these numbers, it’s easy to see why end users might not be to blame when you discover that a major security breach was caused by someone being duped by a phishing scam.
The Way Forward
As more HTTPS phishing and malware sites emerge, even the most vigilant among us could fall victim. But that doesn’t mean we shouldn’t invest in end user education. End users are on the front lines on the cybersecurity battlefield. It’s up to us to provide right tools and armor to keep users and the companies they represent safe. To be truly effective, we need to implement ongoing security awareness training programs that recur continually throughout an employee’s time with the company. If we accomplish that, the results speak for themselves; after 12 months of training, end users are 70% less likely to fall for a phishing attempt!
We also need to make sure our security strategies incorporate real-time threat intelligence to accurately classify and determine which websites are good or malicious, regardless of their HTTPS designation. In an age where phishing sites appear and disappear in a matter of hours or minutes, malicious sites use HTTPS, and at least 40% of bad URLs can be found on good domains, it’s more important than ever that we all use the most advanced real-time technologies available.
Ultimately building a culture of cybersecurity will always be more effective than a top-down mandate.. Everyone in the organization, from the CEO to the newest intern, should be invested in adopting and furthering a security conscious culture. Part of that process is going to be shifting the general IT perceptions around human error and the issues it can cause. We shouldn’t think of our end users as the weakest link in the chain; instead we should think of them as the key to a robust security strategy.
To hear more about HTTPS, phishing, and end user education, you can listen to the podcast I did with cybersecurity executive and advisor Shira Rubinoff at RSAC 2019.
Post Coinhive, What’s Next for Cryptojacking?
In late February, the notorious cryptojacking script engine called Coinhive abruptly announced the impending end to its service. The stated reason: it was no longer economically viable to run.
Coinhive became infamous quickly following its debut as an innovative javascript-based cryptomining script in 2018. While Coinhive maintained that its service was born out of good intentions—to offer website owners a means to generate revenue outside of hosting ads—it took cybercriminals no time at all to create cryptojacking attack campaigns. Cryptojacking became incredibly popular in 2018, infecting millions of sites (and cloud systems among the likes of Tesla) and netting criminals millions in cryptocurrency at the expense of their victims.
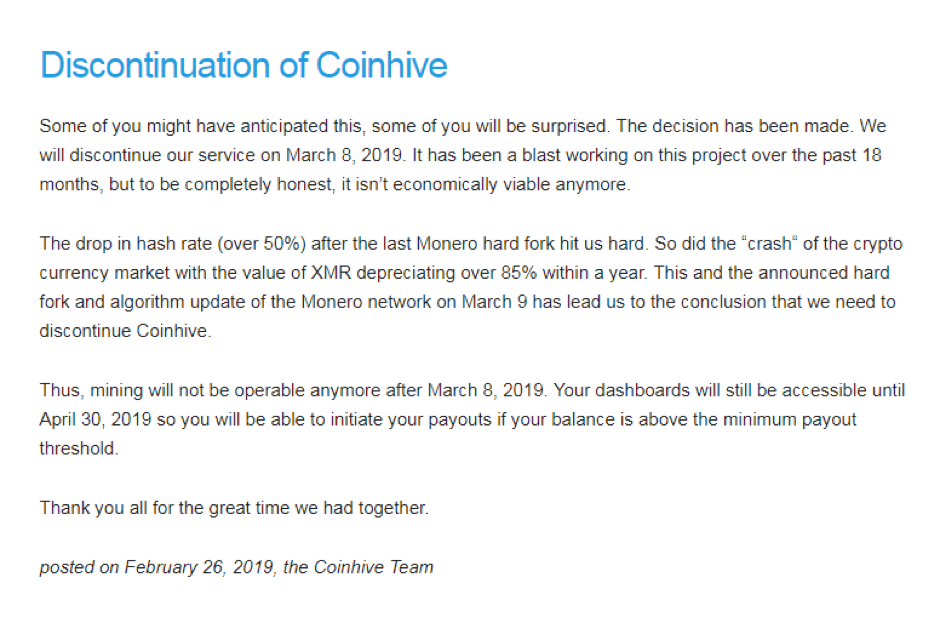
I honestly did not see this happening, but I do understand. It is reasonable to think that Coinhive didn’t intend for their creation to be abused by criminals. However, they have still kept 30 percent of ALL the earnings generated by their script, one that was often found running illegally on hijacked sites. Most of that profit came from illicit mining, which has earned Coinhive a lot of negative press.
Additionally, 2018 was a terrible year in terms of the US-dollar value of Monero (XMR), which means their service is significantly less profitable now, relative to what it once was. Combined with the fact that the XMR development team hard-forked the coin and changed the difficulty of the hashrate, this means Coinhive is making very little money from legitimate miners.
Coinhive created this service so legitimate domain owners could host their script and generate enough revenue to replace ads. Ads are annoying and I believe this innovation was aimed at attempting to fix that problem. But the ultimate result was a bunch of criminals breaking into other people’s domains and injecting them with Coinhive scripts that essentially stole from visitors to that domain. Without consent, millions of victims’ computers were subject to maximum hardware stress for extended periods of time, all so some criminals could make a few pennies worth of cryptocurrency per computer.
Would you continue to operate a startup business in which most of the money you earned was a cut of criminal activity—stealing from victims in the form of an increased power bill? Maybe a year ago, when the hashing difficulty was easier (you earned more XMR) and XMR was worth 10 times what it’s worth now, it might have been easier to “sleep at night” but now it probably just isn’t worth it.
Even before this news, there were plenty of other copycats—Cryptoloot, JSEcoin, Deepminer, and others—so criminals have plenty of similar services to choose from. At the time of its shutdown, Coinhive had about around 60% share of all cryptojacking campaigns, though we saw this market dominance reach as high as 80% last year. I anticipate these other services stand to take larger shares of cryptojacking revenue now that the largest player has left. We might even see a new competitor service emerge to challenge for cryptojacking dominance.
Stay tuned to the Webroot blog for future developments in cryptojacking.
Cyber News Rundown: Georgia County Pays for Ransomware Threat
Georgia County Pays Six Figure Ransom to Restore IT Systems
Following a ransomware attack earlier this month, officials in Jackson County, Georgia decided to pay a $400,000 ransom in order to obtain a decryption key and return their systems to normal operations. While it’s not normally recommended to pay ransoms, but instead to keep proper backups of critical files, the county decided that it would cost significantly more to restore the systems on their own. It is still unclear how the breach unfolded or how long the hackers had access to the network.
Michigan Healthcare Group Compromised
Sensitive information on over 600,000 patients was recently exposed after the Wolverine Solutions Group (WSG) suffered a data breach. The WSG initially suffered a ransomware attack in September of last year, and has been working to decrypt many of their systems since then. Due to Michigan’s lax laws regarding the announcement of a data breach, customers who may have been affected were contacted only within the last month.
Redirect Tags Found on Fortune 100 Sites
Hundreds of third-party redirect tags have been found hidden on the websites of Fortune 100 companies. These tags could allow attackers to access user data from any of the compromised sites and also degrade the performance of sites with multiple hidden tags. Many site owners even expressed concern over possible customer data loss, but did little to clear the tags from their sites.
Asian Gaming Companies Infiltrated by Backdoors
Several Asia-based gaming companies have discovered hidden backdoors within main executables of some games attracting tens of thousands of players. Fortunately, after identifying the malicious code two of the three companies immediately pushed updates to their software, and the command & control servers for the backdoors were taken offline soon after. The backdoors appear to have originated from a malicious Chinese hacker group that has committed these types of attacks multiple times in recent years.
Info on 1.8 Million Women Found on Unprotected Chinese Database
An unprotected database was recently found which contains extremely sensitive data for nearly 1.8 million women in China. Amongst the personally identifying information was GPS coordinates, political affiliations, and even available video of specific individuals. Unfortunately, while the owners of this one database were successfully contacted, there are still thousands of similarly unprotected databases on Chinese networks.
The Hidden Costs of ‘Free’ WiFi
The True Cost of Free WiFi
Ease-of-access is a true double-edged sword. Like all powerful technologies, WiFi (public WiFi in particular) can be easily exploited. You may have read about attacks on publicly accessible WiFi networks, yet studies show that more than 70% of participants admit to accessing their personal email through public WiFi. WiFi vulnerabilities aren’t going away anytime soon—in 2017, the WPA2 security protocol used by essentially all modern WiFi networks was found to have a critical security flaw that allowed attackers to intercept passwords, e-mails and other data.
So what are the most commonly seen attacks via free WiFi, and how can we protect ourselves and our families? We turned to Tyler Moffitt, Webroot’s Sr. Threat Research Analyst, for answers.
Common Public WiFi Threats
“Criminals are either taking over a free WiFi hotspot at the router level, or creating a fake WiFi hotspot that’s meant to look like the legitimate one,” explained Moffitt. “The purpose of these man-in-the-middle attacks is to allow attackers to see and copy all of the traffic from the devices connected to the WiFi they control.”
Basic security protocols often aren’t enough to protect users’ data.
“Even with HTTPS sites where some data is encrypted, much of it is still readable,” Moffitt said. “Beyond just seeing where you surf and all the login credentials, criminals also have access to your device and can drop malicious payloads like ransomware.”
We are now seeing these attacks evolve, with cryptojacking becoming a particularly lucrative exploitation model for public WiFi networks. Cryptojacking is seen as a “low risk” attack as an attacker siphons a victim’s computer processing power, something far less likely to be detected and tracked than a traditional malware or ransomware attack. This was particularly notable in a 2017 cryptojacking attack that targeted Starbucks customers, which went uncorrected until Noah Dinkin—a tech company CEO—noticed a delay when connecting to the shop’s WiFi. Dinkin took it upon himself to investigate
Hi @Starbucks @StarbucksAr did you know that your in-store wifi provider in Buenos Aires forces a 10 second delay when you first connect to the wifi so it can mine bitcoin using a customer's laptop? Feels a little off-brand.. cc @GMFlickinger pic.twitter.com/VkVVdSfUtT
— Noah Dinkin (@imnoah) December 2, 2017
It’s not just coffee shops that are being targeted. Airports, hotels, and convention centers are particularly prime targets due to their high traffic. To demonstrate the power of a targeted attack in a conference setting, a security experiment was conducted at the 2017 RSA Conference. Surprisingly, even at an IT security conference, white hat hackers were able to trick 4,499 attendees into connecting to their rogue WiFi access point. The targeting of high-traffic, travel-focused locations means that many frequent travelers will leave themselves exposed at some point by connecting to public WiFi options—even though they may know better.
How to Detect the Threat
What are the telltale signs of a compromised system?
“With cryptomining, you will definitely notice that your machine will start acting slow, the fans will kick on full blast, and the CPU will increase to 100 percent, usually the browser being the culprit,” Moffitt said. “But there are few signs of a man-in-the-middle attack, where wireless network traffic is spied on for credentials and financial information. You won’t notice a thing, as your computer is just connecting to the router like normal. All information is being observed by someone in control of the router.”
With one recent attack in 2018 alone affecting 500,000 WiFi routers, the need for WiFi security has never been stronger.
Protecting Yourself on the Go
You can take steps to keep your data secure; the first of which is being sure that you have a VPN installed and protecting your devices. Nothing else will as effectively encrypt and shield your traffic on a public network.
“Using a VPN is the most impactful way to combat the dangers of free WiFi,” Moffitt said. “Think of VPN as a tunnel that shelters all of your information going in and out of your device. The traffic is encrypted so there is no way that criminals can read the information you are sending.”
“I use a VPN on my phone when I’m on the go,” he continued. “It’s really easy to use and you make sure all your data is private and not visible to prying eyes.”
But be sure to research any VPN before you commit to ensure it is trustworthy. It’s important to review the vendor’s privacy policy to make sure the VPN does not monitor or retain logs of your activities. Remember that, with security software and apps, you generally get what you pay for.
While free VPN apps will shield your data from the router you are connecting to, they may still spy on you and sell your information,” Moffitt said.
What does this all mean for you? If there is no such thing as free lunch, then there is definitely no such thing as free WiFi. The true cost just might be your online security and privacy.
Stay vigilant, secure all of your web traffic behind a trusted VPN, and check back here often for the latest in cybersecurity updates
Cyber News Rundown: New Ransomware Service Offers Membership
Ransomware as-a-Service Offers Tiered Membership Benefits
Jokeroo is the latest ransomware-as-a-service (RaaS) to begin spreading through hacker forums, though it’s differentiating itself by requiring a membership fee with various package offerings. For just $90, a buyer obtains access to a ransomware variant that they can fully customize in exchange for a 15% service fee on any ransom payments received. Higher packages are also available that offer even more options that give the user a full dashboard to monitor their campaign, though no ransomware has yet to be distributed from the service.
Android Adware Apps are Increasingly Persistent
Several new apps on the Google Play store have been found to be responsible for constant pop-up ads on over 700,000 devices after being installed as phony camera apps. By creating a shortcut on the device and hiding the main icon, the apps are able to stay installed on the device for a considerable amount of time, as any user trying to remove the app would only delete the shortcut. Fortunately, many users have been writing poor reviews about their experiences in hopes of steering prospective users away from these fraudulent apps while they remain on the store.
Phone Scammers Disguising Themselves with DHS Numbers
People all across the U.S. have been receiving phone calls from scammers claiming to be from the Department of Homeland Security (DHS), with actual spoofed DHS phone numbers, requesting sensitive information. While phone scams aren’t new, this campaign has upped the stakes by threatening the victims with arrest if they don’t provide information or make a payment to the scammers. DHS officials have stated they will never attempt to contact individuals through outgoing phone calls.
Failed Ransomware Attack Leaves Thousands of Israeli Sites Defaced
A ransomware attack aiming to infect millions of Israeli users through a widget used in thousands of websites failed over the weekend. Though all sites began displaying pro-Palestine messages, the intended file download never took place due to a coding error that prevented execution immediately after the pop-up message. After dealing with the poisoned DNS records for the widget creator Nagich, the company was able to restore normal function within a few hours of the attack beginning.
Chicago Medical Center Exposes Patient Records
Nearly eight months after a Rush Medical Center employee emailed a file containing highly sensitive patient information to one of their billing vendors, the company began contacting affected patients and conducting an internal investigation. Rush has setup a call center to provide additional information to concerned patients and has offered all victims access to an identity monitoring service, while warning them to check their credit history for any fraudulent activity.
Cyber News Rundown: Botnet Hijacks Browsers
Fake Apex Legends App Spreads Malware
As the popularity of the latest free-to-play battle royale pushes ever higher, malicious Apex Legends apps have been spotted in the Google Play store with upwards of 100,000 downloads. The fake apps typically offer free in-game currency, or free downloads for an already free game, while installing malware onto devices and directing users to enter phishing domains to further compromise themselves.
Cryptocurrency Wallet Bug Checks User Passwords with Spellchecker
A new bug has been found within the Coinomi cryptocurrency wallet app that quietly submits each user password to Google’s spellchecker without encryption, leaving user accounts vulnerable to attacks if someone is monitoring the web traffic of the application. The bug was discovered by a researcher who noticed that a majority of his funds had gone missing from his Coinomi-stored cryptocurrencies, leading him to investigate the app more extensively.
Bangladeshi Embassy Site Compromised
Researchers have found that the web site for the Bangladesh Embassy in Cairo has been compromised and was pushing malicious word document downloads to any user who visited the site. Once the download is confirmed, it installs to an innocuous location within ProgramData and begins attempting to contact the command & control server to pull down additional malware. It’s likely that this issue is linked to an earlier attack on the site that left a cryptominer operating for several days and is affecting users who accessed the site during that time.
Botnet Controls Browsers Even After Being Closed
A new type of cyber attack has been found that uses normal JavaScript and HTML5 functionality to take control of a user’s browser for a number of malicious activities and can even continue operating and commandeering resources after the browser or website has closed. Through these normal capabilities, this type of attack could affect both desktop and mobile browsers and, due to its nature, can be exceedingly persistent on the system once active.
Multi-OS Ransomware Demands High Payment
The latest ransomware variant to make its rounds, Borontok, has already been spotted encrypting Linux servers and commercial websites, leaving a .rontok extension at the end of the filename. To make matters worse, the demanded ransom payment is 20 Bitcoins, or roughly $75,000, and gives directions to an actual payment site, though it does later offer the user a chance to negotiate for a lower payment.
The Ransomware Threat isn’t Over. It’s Evolving.
This is the third of a three-part report on the state of three malware categories: miners, ransomware and information stealers.
Ransomware is any malware that holds your data ransom. These days it usually involves encrypting a victim’s data before asking for cash (typically cryptocurrency) to decrypt it. Ransomware ruled the malware world since late 2013, but finally saw a decline last year. The general drop in malware numbers, along with defensive improvements by the IT world in general (such as more widespread backup adoption), were factors, but have also led this threat to become more targeted and ruthless.
Delivery methods
When ransomware first appeared, it was typically distributed via huge email and exploit kit campaigns. Consumer and business users alike were struck without much discretion.
Today, many ransomware criminals prefer to select their targets to maximise their payouts. There’s a cost to doing business when it comes to infecting people, and the larger the group of people you are trying to hit, the more it costs.
Exploit kits
Simply visiting some websites can get you infected, even if you don’t try to download anything. This is usually done by exploiting weaknesses in the software used to browse the web such as your browser, Java, or Flash. Content management and development tools like WordPress and Microsoft Silverlight, respectively, are also common sources of vulnerabilities. But there’s a lot of software and web trickery involved in delivering infections this way, so the bulk of this work is packaged into an exploit kit which can be rented out to criminals to help them spread their malware.
Renting an exploit kit can cost $1,000 a month, so this method of delivery isn’t for everyone. Only those cybercriminals who’re sufficiently motivated and funded.
“Because the cost of exploitation has risen so dramatically over the course of the last decade, we’ll continue to see a drop in the use of 0-days in the wild (as well as associated private exploit leaks). Without a doubt, state actors will continue to hoard these for use on the highest-value targets, but expect to see a stop to Shadowbrokers-esque occurrences. The mentioned leaks probably served as a powerful wake-up call internally with regards to who has access to these utilities (or, perhaps, where they’re left behind).” – Eric Klonowski, Webroot Principal Threat Research Analyst
Exploits for use in both malware and web threats are harder to come by these days and, accordingly, we are seeing a drop in the number of exploit kits and a rise in the cost of exploits in the wild. This threat isn’t going anywhere, but it is declining.
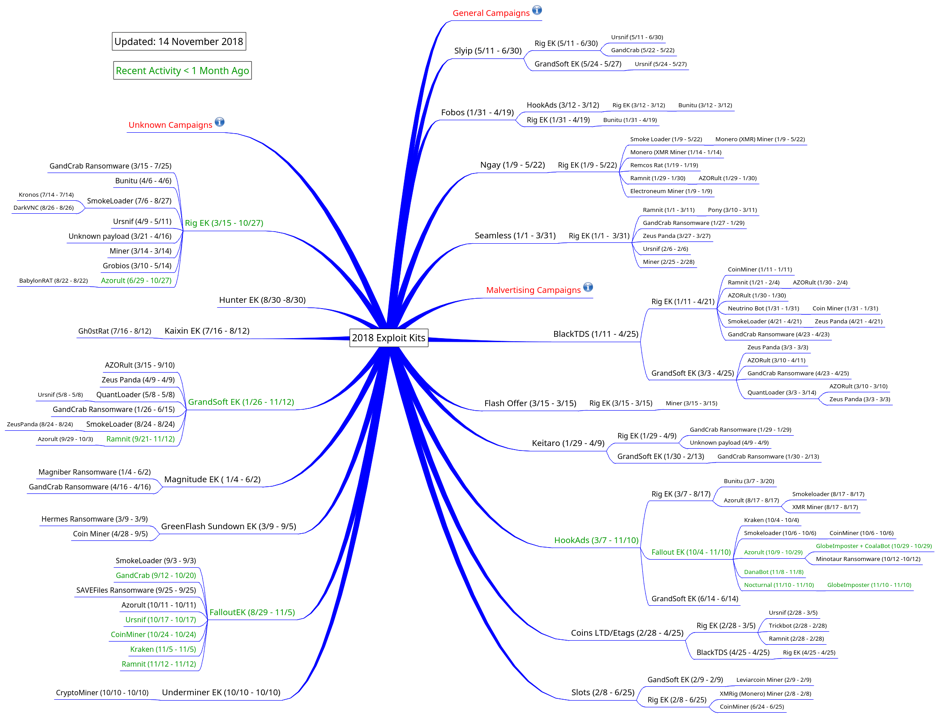
Email campaigns
Spam emails are a great way of spreading malware. They’re advantageous for criminals, as they can hit millions of victims at a time. Beating email filters, creating a convincing phishing message, crafting a dropper, and beating security in general is tough to do on a large scale, however. Running these big campaigns requires work and expertise so, much like an exploit kit, they are expensive to rent.
Targeted attacks
The likelihood of a target paying a ransom and how much that ransom is likely to be is subject to a number of factors, including:
- The country of the victim. The GDP of the victim’s home nation is correlated to a campaign’s success, as victims in richer countries are more likely to shell out for ransoms
- The importance of the data encrypted
- The costs associated with downtime
- The operating system in use. Windows 7 users are twice as likely to be hit by malware as those with Windows 10, according to Webroot data
- Whether the target is a business or a private citizen. Business customers are more likely to pay, and pay big
Since the probability of success varies based on the target’s circumstances, it’s important to note that there are ways of narrowing target selection using exploit kits or email campaigns, but they are more scattershot than other, more targeted attacks.
RDP
Remote Desktop Protocol, or RDP, is a popular Microsoft system used mainly by admins to connect remotely to servers and other endpoints. When enabled by poor setups and poor password policies, cybercriminals can easily hack them. RDP breaches are nothing new, but sadly the business world (and particularly the small business sector) has been ignoring the threat for years. Recently, government agencies in the U.S. and UK have issued warnings about this completely preventable attack. Less sophisticated cybercriminals can buy RDP access to already hacked machines on the dark web. Access to machines in major airports has been spotted on dark web marketplaces for just a few dollars.
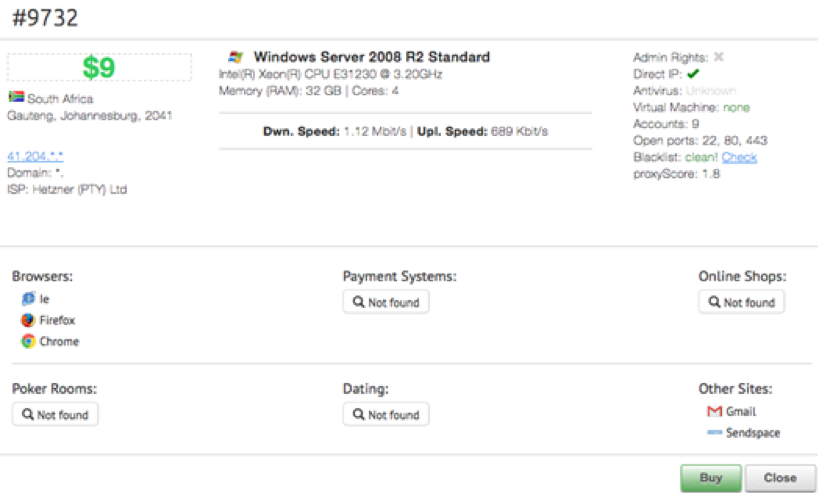
Spear phishing
If you know your target, you can tailor an email specifically to fool them. This is known as spear phishing, and it’s an extremely effective technique that’s used in a lot of headline ransomware cases.
Modular malware
Modular malware attacks a system in different stages. After running on a machine, some reconnaissance is done before the malware reinitiates its communications with its base and additional payloads are downloaded.
Trickbot
The modular banking Trojan Trickbot has also been seen dropping ransomware like Bitpaymer onto machines. Recently it’s been used to test a company’s worth before allowing attackers to deploy remote access tools and Ryuk (ransomware) to encrypt the most valuable information they have. The actors behind this Trickbot/Ryuk campaign only pursue large, lucrative targets they know they can cripple.
Trickbot itself is often dropped by another piece of modular malware, Emotet.
What are the current trends?
As we’ve noted, ransomware use may be on the decline due to heightened defences and greater awareness of the threat, but the broader, more noteworthy trend is to pursue more carefully selected targets. RDP breaches have been the largest source of ransomware calls to our support teams in the last 2 years. They are totally devastating to those hit, so ransoms are often paid.
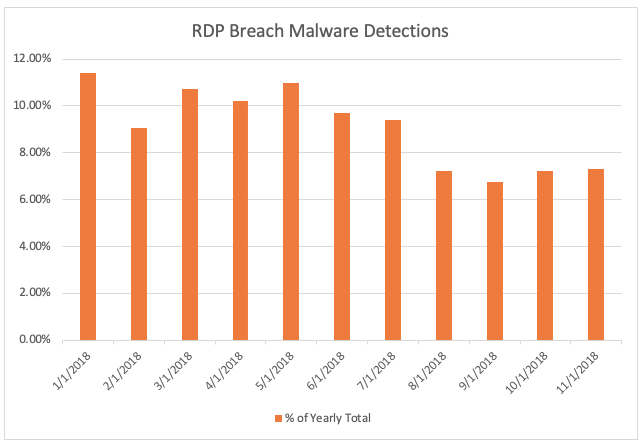
Modular malware involves researching a target before deciding if or how to execute and, as noted in our last blog on information stealers,they have been surging as a threat for the last six months.
Automation
When we talk about selecting targets, you might be inclined to assume that there is a human involved. But, wherever practical, the attack will be coded to free up manpower. Malware routinely will decide not to run if it is in a virtualised environment or if there are analysis tools installed on machines. Slick automation is used by Trickbot and Emotet to keep botnets running and to spread using stolen credentials. RDP breaches are easier than ever due to automated processes scouring the internet for targets to exploit. Expect more and more intelligent automation from ransomware and other malware in future.
What can I do?
- Secure your RDP
- Use proper password policy. This ties in with RDP ransomware threats and especially applies to admins.
- Update everything
- Back up everything. Is this backup physically connected to your environment (as in USB storage)? If so, it can easily be encrypted by malware and malicious actors. Make sure to air gap backups or back up to the cloud.
- If you feel you have been the victim of a breach, it’s possible there are decryption tools available. Despite the brilliant efforts of the researchers in decryption, this is only the case in some instances.
What can Webroot do?
- Detect and stop ransomware. Prevention is always best, and it’s what we’re best at.
- Block malicious URLs and web traffic.
- Rollback changes made by some ransomware.
- Offer support. Our support is excellent and easy to reach. As well as helping to tackle any possible ransomware attack, our team will investigate the root cause and help you secure your organisation against future attacks. Specialised security hardening tools that can be deployed from your console to your machines in a few clicks.
- For more technical details see our Ransomware Prevention Guide.
A Cybersecurity Checklist for Modern SMBs
The landscape of digital security is rapidly shifting, and even the largest tech giants are scrambling to keep up with new data regulations and cybersecurity threats. Small to medium-sized businesses (SMBs) are often left out of these important conversations, leaving themselves — and their users — vulnerable. In an effort to combat this trend, Webroot conducted a survey of more than 500 SMB IT leaders in the UK, revealing common blind spots in SMB cybersecurity practices. As businesses around the globe grapple with similar change, our Size Does Matter: Small Businesses and Cybersecurity report offers insight and guidance for companies regardless of geography.
The biggest takeaway? We turned to Webroot’s Senior Director of Product Strategy Paul Barnes for his thoughts.
“The damage from data loss or downtime often means substantial financial and reputational losses, sometimes even leading to a business no longer being viable. A key learning for all small businesses should be to stop hiding behind your size. Instead, become educated in the risks and make your security posture a differentiator and business driver.”
When you’re putting together a cybersecurity checklist, you’ll need to do one thing first: check your preconceived notions about SMB cybersecurity at the door. Your business is not too small to be targeted. The data you collect is both valuable and likely vulnerable, and a costly data breach could shutter your business. More than 70% of cyberattacks target small businesses, with 60% of those going out of business within six months following their breach. With both the threat of hackers and the looming possibility of increased GDPR-style data regulatory fines, your small business cannot afford to be underprepared.
The first step to a fully realized cybersecurity program? An unflinching look at your company’s resources and risk factors.
“Understand what you have, from a technology and people perspective, and the risks associated with loss of data or operations, whether through externally initiated attacks or inside threats,” advised Barnes. “This will allow you to plan and prioritise next steps for protecting your business from attack.”
For established SMBs, this type of internal review may seem overwhelming; with so many employees already wearing so many hats, who should champion this type of effort? Any small business that is preparing to modernize its cybersecurity protocols should consider bringing in a managed service provider (MSP) to do an internal audit of its systems and to report on the company’s weaknesses and strengths. This audit should serve as the backbone of your cybersecurity reform efforts and — depending on the MSP — may even give you a security certificate that can be used for marketing purposes to differentiate your brand from competitors.
With a strong understanding of your company’s strengths and weaknesses, you can begin to implement an actionable cybersecurity checklist that will scale as you grow, keeping your business ahead of the data security curve. Each SMB’s checklist will be unique, but these best practices will be integrated into any successful cybersecurity strategy.
Continuous Education on the Latest Threats
A majority of small to medium-sized businesses rely on software systems that are constantly evolving, closing old security gaps while potentially opening new ones. With a tech landscape in constant flux, one-off security training will never be enough to truly protect your business. Comprehensive employee training that evolves alongside cybersecurity threats and data privacy regulations are your company’s first line of cybersecurity defense. Include phishing prevention practices in these trainings as well. Although seemingly old hat, phishing attacks are also evolving and remain one of the largest causes of data breaches globally. Continuous training of employees helps build a culture of security where they feel part of the team and its success.
Regular Risk Assessment and Security Audits
Just as one-off training is not sufficient in keeping your staff informed, a one-off audit does nothing to continuously protect your company as it grows. Depending on your industry, these audits should take place at least annually, and are the best way to detect a security flaw before it is exploited. Factors such as the sensitivity of the data your business houses, and the likely impacts of a successful breach—your risk profile—should guide decisions regarding the frequency of these security audits.
Disaster Response Plan
Having a prepared disaster response plan is the most effective way to mitigate your losses during a data security breach. Backup and recovery tactics are critical components of this plan. It should also include a list of security consultants to contact in order to repair the breach, as well as a communications plan that notifies customers, staff, and the public in accordance with data protection regulations. An MSP can work with your company to provide a disaster response plan that is customized to your business’ specific needs.
Bring Your Own Device
Never scrimp on mobile security. Many companies now tolerate some degree of bring-your-own-device (BYOD) policy, giving employees increased convenience and employer accessibility. But convenience is a compromise and, whether it be from everyday theft or a malicious app, mobile devices are a weak point in many company’s security. Including mobile security guidelines like automatic device lock requirements, strong password guidelines, and failsafe remote wipe access in your BYOD policies will save your company money, time, and heartache.
Layer Your Security
Finally, ensure your business has multiple layers of defense in place. Accounting for endpoint devices is no less critical than it’s always been, but businesses are increasingly learning that networks and users need protection, too. DNS-layer security can keep employees from inviting risky sites onto your network, and security awareness training will help your users recognize signs of an attack. No one solution is a panacea, but tiered defenses make a business more resilient against cybercrime.
Survey says: We don’t have time for this
One of the largest impediments to SMBs adopting these modern cybersecurity protocols is the perceived time cost, with two-fifths of IT leaders surveyed by Webroot stating they simply do not have the time or resources to fully understand cybersecurity threats. The uncomfortable truth is that, if you can’t find the time to protect your data, a hacker whodoes have the time is likely to find and exploit your security gaps. But there is a silver-lining, the smaller size of an SMB actually allows for a certain level of agility and adaptiveness when implementing cybersecurity policies that is inaccessible to tech giants.
“SMBs can no longer consider themselves too small to be targets. They need to use their nimble size to their advantage by quickly identifying risks and educating employees on risk mitigation, because people will always be the first line of defense,” said Barnes.
You’ll find additional benefits beyond the base-level protection a comprehensive cybersecurity plan provides. As 33% of SMBs surveyed by Webroot say they prefer not to think about cybersecurity at all, demonstrating that your company is ahead of the problem can be a powerful way to distinguish your business from its competitors. With consumer data privacy concerns at an all-time high, a modern cybersecurity checklist may be one of the best marketing tools available. The best way to stay ahead of cybersecurity threats is to stay informed. Read the entire Size Does Matter: Small Businesses and Cybersecurity report for an in-depth look at how your SMB contemporaries are handling data protection, and stay up-to-date with Webroot for additional cybersecurity reports and resources.
Cyber News Rundown: Phishing through Email Filter
Email Phishers Find New Filter Bypass
Since email filters have gained popularity over the last decade, scammers have been forced to adapt their attacks. To bypass a normal URL filter that would check for malicious links, these scammers have found a way to alter the “document relationship” file (xml.rels) and continue to push out harmful links. By removing the malicious link from the relationship file, many filters simply skip over it and allow the link to remain clickable, a new tactic which relies on filters scanning only a portion of a file.
Unknown Devices Putting UK Firms at Risk
In a recent survey, nearly 3 million UK businesses have admitted to constantly monitoring dozens of unknown devices connecting to their corporate networks. With internal security flaws being the main driver for data breaches, new policies should be implemented to work with the increasing number of external IoT devices connecting with systems expected to maintain a certain level of privacy. Unfortunately, many companies still see IoT devices as a non-threat and continue to ignore the gaping security holes appearing within their walls.
Swedish Healthcare Database Left Unattended for Years
A server was recently discovered to contain millions of call records made to a Swedish Healthcare Guide service that has been left exposed for up to six years. The server itself was created, then forgotten in 2013, and has since missed dozens of patches, leaving it vulnerable to at least 23 unique security flaws. Within the call records are names, birth dates, and even social security numbers, though after hearing of the breach, the company made swift efforts to properly secure the sensitive data.
Stanford Students Exposed After URL Vulnerability Spotted
What started as a simple admissions document request has left the personal data of 93 students exposed, due to a simple flaw in the record’s URL. By easily swapping out parts of the numeric ID viewable in the document’s URL, anyone with a login to the site could view another student’s records. Within the admissions documents was personal information relating to a specific student, including non-university records like background/criminal checks and citizenship standings. Fortunately, Stanford was quick to make the necessary changes and contacting affected students.