Avoid Unsecure IoT: Smart Device Shopping Tips
“Internet of things” (IoT) is a term that’s becoming increasingly commonplace in our daily lives. Internet-connected devices are being designed and implemented at a rapid clip, especially in our own homes. The internet is not just at our fingertips anymore, but also at our beck and call with smart speakers and digital assistants.
It’s easy to see why we are drawn to these cool new devices. They promise to make our lives easier and the convenience associated with some of these devices is undeniable.
But at what point are we sacrificing security for convenience?
A Brave New World of IoT Devices
Internet-connected doorbells can beam a video feed to your phone so you can see who is at your door before deciding whether or not to open it. A smart refrigerator will alert you when supplies are running low or approaching expiration while you shop at the grocery store. Smart thermostats boost efficiency and deliver monthly savings on utilities. These functions have obvious appeal for consumers.
However, some devices on the market stretch their advertised utility and convenience. Smart salt shakers, for instance, deliver voice-controlled sodium so you can avoid the hassle of salting your food the old fashioned way. Smart toasters will burn the date and weather into your bread, lest you forget an umbrella and what day it is. But with each new “convenience” promised by smart devices comes the danger of ceding some of your security.
Image source: Screenshot from Toasteroid YouTube.
The underlying issue with the new and accelerating trend of buying more and more IoT devices is that the average consumer has little to no education about security when shopping for these devices. Even manufacturers can be blind to or willfully negligent of the security issues inherent to their IoT devices. It’s all about coolness and convenience—and that’s the trap.
Be wary of Unsecure IoT
Many IoT devices have little to no embedded security, and there’s little incentive for designers to consider it. One reason for that is a lack of third-party standards for evaluating IoT security. Until now, the focus has been on producing a viable product that’s functional enough to get consumers to purchase it at the right price. The “right price” is usually as inexpensive as possible, and so some quality is sacrificed.
With IoT devices, that sacrifice usually comes at the expense of security vetting in the design process. As a result, one of the biggest trends we see with cheap IoT devices is a complete and total lack of security. It’s just not something that stands out in marketing materials, so manufacturers don’t promise it and consumers don’t demand it.
That’s why care is required when shopping for new IoT devices—especially cheap ones. IoT devices like smart thermostats, smart doorbells, et cetera, usually feature competing products with varying functionalities and prices. It’s common to peruse the fanciest, most expensive devices, and then purchase an off-brand device that offers similar functionality at a much lower price.
Vendors have flooded the IoT market with devices that have so-called “hardcoded passwords.” This means that, when setting up your device, the password given to you in the instructions is the same password for every device of that model and can’t be changed. Even if the device allows you to setup a custom password, the hardcoded password will still work to log into the device.
This is basically the opposite of security. It served as the principal attack vector for the infamous Mirai botnet attack a couple years ago. It’s also how hundreds of thousands of routers have been hacked to mine cryptocurrency. Even premium IoT devices like Google’s Nest are subject to attacks, but when properly set up and used—as in by setting up two-factor authentication and not reusing their compromised credentials—they tend to be safer than their knock-off counterparts.
It’s clear now that internet-connected devices will be a part of our lives for the foreseeable future. They will help run our cities, power our grids, and yes, manage our homes. But we must be aware of what we are connecting in our home and the security of each device. Vendor regulation will also need to play its part, something already underway in California, but there is plenty more ground to cover and no time to wait. For now, it’s on the consumer to scrutinize the IoT products they bring into their home, and security should be high on their checklist.
Make sure that any internet-connected devices you buy allow you to create custom passwords, as a start. It’s also wise to only shop from reputable vendors.
Taking caution will help ensure that your smart home isn’t an easy target for cybercriminals.
Cyber News Rundown: Photography Site Breached
Popular Photography Site Breached
A major photography site, 500px, recently discovered they had suffered a data breach in July of last year. Data ranging from name and email addresses, to birthdates and user locations, were comprised. While the company did confirm no customer payment data is stored on their servers, all 15+ million users are receiving a forced password reset to ensure no further accounts can be compromised.
Nigerian Scammers Target ‘Lonely’ Victims
A recent email campaign by a criminal organization known as Scarlet Widow has been focusing on matchmaking sites for people they consider to be lonelier, elderly, or divorced. By creating fake profiles and gaining the trust of these individuals, the scammers are not only attempting to profit financially, but also causing emotional harm to already vulnerable people. In some cases these victims have been tricked into sending thousands of dollars in response to false claims of needing financial assistance, with one victim sending over $500,000 in a single year.
VFEmail Taken Down by Hackers
The founder of VFEmail watched as nearly 20 years-worth of data was destroyed by hackers in an attack that began Monday morning. Just a few hours after servers initially went down, a Tweet from a company account announced that all of the servers and backups had been formatted by a hacker traced back to Bulgarian hosting services. The motivation for the attack is still unclear, though given the numerous security measures the hacker successfully bypassed, it appears to have been a significant effort.
Urban Electric Scooters Vulnerable to Attacks
With the introduction of electric scooters to many major cities, some are curious about the security measures keeping customers safe. One researcher was able to wirelessly hack into a scooter from up to 100 yards and use his control to brake or accelerate the scooter at will, leaving the victim in a potentially dangerous situation. Without a proper password authentication system for both the scooter and the corresponding application, anyone can take control of the scooter without needing a password.
Phishing Campaign Stuffs URL Links with Excessive Characters
The latest phishing campaign to gain popularity has brought with it a warning about accounts being blacklisted and a confirmation link containing anywhere from 400 to 1,000 characters. Fortunately for observant recipients, the link should immediately look suspicious and serve as an example of the importance of checking a URL before clicking on any links.
Cyber News Rundown: Phishing British Parliament
Members of British Parliament Targeted by Phishing Attack
Dozens of MPs from the UK were recently subjected to malicious spam and unauthorized solicitations via their mobile devices. Fortunately, as this wasn’t the first phishing attempt on MPs, many were quick to delete any unusual messages and quickly warned others to do the same. Due to the ease of mounting such an attack, phishing campaigns can be extremely effective, especially when deploying social engineering tactics to increase the victim pool.
Major African Utility Company Breached
One of the largest energy providers on the African continent suffered a data breach this week, brought on by an employee downloading a game onto a corporate device. Along with introducing a fairly sophisticated banking Trojan onto the system, the employee also allowed for a database containing sensitive customer information to be made available to the attackers. Even more worrisome, the utility company was only made aware of the breach after an independent security researcher attempted to contact them about the stolen data via Twitter.
Cryptocurrency Exchange Collapses After CEO Death
A Canadian-based cryptocurrency exchange was recently faced with a major dilemma after the untimely death of their CEO and only person to have access to the offline coin storage wallet. With more than $100 million worth of cryptocurrency current tied up in the exchange, many customers quickly found themselves without access to their funds, possibly indefinitely. Having a single point of failure is a critical, and easily avoidable, issue for any digital company.
Fast Food POS Breach
A new breach has been discovered that could affect any customers who paid with a credit card at any Huddle House fast-food locations over the past two years. While the specific malware variant is still unknown, there were obvious signs of credential stealing and other information gathering tactics. Huddle House has since been working with law enforcement and credit companies to help potential victims with credit monitoring.
Google Play Removes Porn Apps
In another wave of cleaning up the Google Play store, the company recently removed 29 apps that were disguised as photo or camera apps but would instead steal user photos and display a steady stream of pornographic advertisements. The apps had all been downloaded between 100,000 and 1 million time each, and were often extremely difficult to remove, even hiding the app icon entirely. Additionally, some of the apps would display as a photo editor, encouraging users to upload any extra pictures that weren’t already stolen.
Carbonite to Acquire Webroot
I’m excited to share that Webroot has entered into an agreement to be acquired by Carbonite, a leader in cloud-based data protection for consumers and businesses.
Why do I think this is such good news for customers, partners and our employees?
For customers and partners, the combined Webroot and Carbonite will create an integrated solution for their top security needs today and a platform for us to build upon in the future. When surveyed, SMBs and MSPs consistently name endpoint security and backup and data recovery services among their top priorities.
For our threat intelligence partners, the addition of new data sources will make our threat intelligence services even more powerful.
We see great opportunities ahead building on the solutions you trust—endpoint and network protection, security awareness training and threat intelligence services—and extending them to backup and data recovery and beyond.
For employees, we see a great future of growth for a team with a shared culture. Both Webroot and Carbonite have tremendously talented team members who together will bring even more innovative solutions to market. But, just as important, both companies have a culture of customer focus, where customer success is the ultimate proof of company success.
Until the transaction closes, we must operate as separate companies. After close, which we expect to happen in the first calendar quarter of 2019, I look forward to sharing more information about our plans.
In the meantime, customers and partners can expect:
- The same commitment to customer care and support. You will have access to your same account reps and award-winning customer support team.
- Future solutions that combine Webroot’s threat intelligence driven portfolio with Carbonite’s data protection solutions.
- Extended sales channels and partner ecosystems. Carbonite partners will provide additional channels for Webroot to reach new customers and partners worldwide.
The most important point I want to underline is that our commitment to you will not change, and we are just expanding the family of people dedicated to building great solutions to protect you and your customers.
Mike Potts
President & CEO, Webroot
The Reality of Passphrase Token Attacks
In my blog, Password Constraints and Their Unintended Security Consequences, I advocate for the use of passphrases. Embedded in the comments section, one of our readers Ben makes a very astute observation:
What happens when attackers start guessing by the word instead of by the letter? Then a four-word passphrase effectively becomes a four-character password.
What Ben is describing is called a “passphrase token attack,” and it’s real. With a good passphrase, the attack is not much of a threat though. First, a definition, then I’ll explain why.
What’s a token?
In the context of a passphrase token attack, a token is a grouping of letters, AKA a word. The passphrase made famous by the comic xkcd, “correct horse battery staple,” is 28 characters long. But, in a passphrase token attack, I wouldn’t try to guess all possible combinations of 28 letters. I would guess combinations of entire words, or tokens, each representing a group of characters.
The math behind passphrases
One might assume, as Ben did, that a four-word password is the same as a four-character password. But that’s a math error. Specifically, 95≠1,000,000.
Here’s why: There are 95 letters, numbers, and symbols that can be used for each character in a password. However, there are over a million words in the English language. For simplicity’s sake, let’s call it an even million words. If I’m thinking of a single character, then at most you have to try 95 characters to guess it. But if I ask you to guess which word I am thinking of, then you may need to guess a million words before you have guessed the word that I am thinking of.
So while there are 95^4 possible combinations of characters for a four-character password, there are over 1,000,000^4 combinations of words for a four-word password.
You might be thinking “But nobody knows a million words,” and you are correct. According to some research, the average person uses no more than 10,000. So, as an attacker, I’d try combinations of only the most common words. Actually, I may be able to get by with a dictionary as small as 5,000 words. But 5,000^4 is still a whole lot more combinations than 95^4.
Here is one list of 5,000 of the most commonly used words in the English language, and another of the 10,000 most commonly used words. Choosing an uncommon word is great, but even words in the top 5,000 are still far better than a complex nine-character password.
Why and how to use a passphrase
There are two major strengths of passphrases:
- Passphrases allow for longer, more secure passwords. It’s length that makes a passphrase a killer password. A password/passphrase that’s 20 lowercase characters long is stronger than a 14 character password that uses uppercase letters, lowercase letters, numbers, and symbols.
- Passphrases can be easy to remember, making creating and using passwords a lot less painful. “Aardvarks eat at the diner” is easy to remember and, at 26 characters long and including uppercase and lowercase letters, is more than 9 trillion times stronger than the password “eR$48tx!53&(oPZe”, or any other complex, 16-character password, and potentially uncrackable.
Why potentially uncrackable? Because “aardvark” is not one of the 10,000 most frequently used words and, if a word is not in the attacker’s dictionary, then you win. This is why it helps to use foreign-language words. Even common foreign words require an attacker to increase the size of their dictionary, the very factor that makes passphrase token attacks impractical. Learning a word in an obscure foreign language can be fun and pretty much assures a passphrase won’t be cracked.
As we’ve seen, cracking a passphrase can be far more difficult than cracking a password, unless you make one of two common mistakes. The first is choosing a combination of words without enough characters. “I am a cat,” for example. Although it’s four words, it’s only 10 characters long and an attacker can use a conventional brute force attack, even for a passphrase. Spaces between words can be used to increase the length and complexity of passphrases.
The second most common mistake is using a common phrase as a passphrase. I can create a dictionary of the top 1,000,000 common phrases and, if you’re using one, then it only takes at most 1,000,000 guesses to crack (about the same as a complex three-character password).
So create your own unique passphrases and you’re all set. Most experts recommend passphrases be at least 20 characters long. But if you only go from eight characters to 16 upper and lower case letters, you’ll already be 430 trillion times better off. And if you’re creating a passphrase for a site requiring a number or symbol, it’s fine to add the same number and symbol to the end of your phrase, provided the passphrase is long to begin with.
As a side note, according to math, a five word passphrase is generally stronger than a four word passphrase, but don’t get too hung up on that.
So Ben, you are 100% right about the reality of passphrase token attacks. But, with a strong passphrase, the math says it doesn’t matter. Note: If this stuff fascinates you, or you suffer from insomnia, you might enjoy “Linguistic Cracking of Passphrases using Markov Chains.” You can download the PDF or watch this riveting thriller on YouTube. Sweet dreams.
Common WordPress Vulnerabilities & How to Protect Against Them
The WordPress website platform is a vital part of the small business economy, dominating the content management system industry with a 60% market share. It gives businesses the ability to run easily-maintained and customizable websites, but that convenience comes at a price. The easy-to-use interface has given even users who are not particularly cybersecurity-savvy a presence on the web, drawing cyber-criminals out of the woodwork to look for easy prey through WordPress vulnerabilities in the process.
Here are some of these common vulnerabilities, and how can you prepare your website to protect against them.
WordPress Plugins
The WordPress Plugin Directory is a treasure trove of helpful website widgets that unlock a variety of convenient functions. The breadth of its offerings is thanks to an open submission policy, meaning anyone with the skill to develop a plugin can submit it to the directory. WordPress reviews every plugin before listing it, but clever hackers have been known to exploit flaws in approved widgets.
The problem is so prevalent that, of the known 3,010 unique WordPress vulnerabilities, 1,691 are from WordPress plugins. You can do a few things to impede your site from being exploited through a plugin. Only download plugins from reputable sources, and be sure to clean out any extraneous plugins you are no longer using. It’s also important to keep your WordPress plugins up-to-date, as outdated code is the best way for a hacker to inject malware into your site.
Phishing Attacks
Phishing remains a favored attack form for hackers across all platforms, and WordPress is no exception. Keep your eyes out for phishing attacks in the comments section, and only click on links from trusted sources. In particular, WordPress admins need to be on alert for attackers looking to gain administrative access to the site. These phishing attacks may appear to be legitimate emails from WordPress prompting you to click a link, as was seen with a recent attack targeting admins to update their WordPress database. If you receive an email prompting you to update your WordPress version, do a quick Google search to check that the update is legitimate. Even then, it’s best to use the update link from the WordPress website itself, not an email.
Weak Administrative Practices
An often overlooked fact about WordPress security: Your account is only as secure as your administrator’s. In the hubbub of getting a website started, it can be easy to create an account and immediately get busy populating content. But hastily creating administrator credentials are a weak link in your cybersecurity, and something an opportunistic hacker will seize upon quickly. Implementing administrative best practices is the best way to increase your WordPress security.
WordPress automatically creates an administrator with the username of “admin” whenever a new account is created. Never leave this default in place; it’s the equivalent of using “password” as your password. Instead, create a new account and grant it administrative privileges before deleting the default administrator account. You’ll also need to change the easily-located and often-targeted administrator url from the default of “wp-admin” to something more ambiguous of your own choosing.
One of the most important practices for any WordPress administrator is keeping the WordPress version up-to-date. An ignored version update can easily become a weak point for hackers to exploit. The more out-of-date your version, the more likely you are to be targeted by an attack. According to WordPress, 42.6% of users are using outdated versions. Don’t be one of them.
Additional Security Practices
The use of reputable security plugins like WordFence or Sucuri Security can add an additional layer of protection to your site, especially against SQL injections and malware attacks. Research any security plugins before you install them, as we’ve previously seen malware masquerading as WordPress security plugins. If your security plugin doesn’t offer two-factor authentication, you’ll still need to install a secure two-factor authentication plugin to stop brute force attacks. Keeping your data safe and encrypted behind a trusted VPN is also key to WordPress security, especially for those who find themselves working on their WordPress site from public WiFi networks.
WordPress is a powerful platform, but it’s only as secure as you keep it. Keep your website and your users secure with these tips on enhancing WordPress security, and check back here often for updates on all things cybersecurity.
Cyber News Rundown: Apple Removes Facebook Research App
Facebook Research App Removed from App Store
After seeing their Onavo VPN application removed from the Apple App Store last year, Facebook has re-branded the service as a “research” app and made it available through non-Apple testing services. The app itself requires users download and install a Facebook Enterprise Developer Certificate and essentially allow the company complete access to the device. While many users seem to be in it only for the monthly gift cards, they remain unaware of the extreme levels of surveillance the app is capable of conducting, including accessing all social media messages, sent and received SMS messages and images, and more. Apple has since completely removed Facebook’s iOS developer certificate after seeing how they collect data on their customers.
Japan Overwhelmed by Love Letter Malware Campaign
Following the discovery of the Love Letter malware a couple weeks ago, the campaign has been determined to be responsible for a massive spike in malicious emails. Hidden amongst the contents of the suspiciously-titled attachments are several harmful elements, ranging from cryptocurrency miners to the latest version of the GandCrab ransomware. Unfortunately for users outside of the origin country of Japan, the initial payload is able to determine the system’s location and download additional malicious payloads based on the specific country.
Apple FaceTime Bug Leads to Lawsuit
With the recent announcement of a critical vulnerability for Apple’s FaceTime app, the manufacturer has been forced to take the application offline. Unfortunately, prior to the shutdown, one Houston lawyer filed a case alleging that the vulnerability allowed for unauthorized callers to eavesdrop on a private deposition without any consent. By simply adding a user to a group FaceTime call, callers were able to listen through the other device’s microphone without that user answering the call.
Authorities Seize Servers for Dark Online Marketplace
Authorities from the US and Europe announced this week that, through their combined efforts, they had successfully located and seized servers belonging to an illicit online marketplace known as xDedic. While this was only one of many such server sites, administrators could have used it to facilitate over $68 million in fraudulent ad revenue and other malicious activities. Hopefully, this seizure will help law enforcement gain an understanding of how such marketplaces operate and assist with uncovering larger operations.
French Engineering Firm Hit with Ransomware
Late last week the French engineering firm Altran Technologies was forced to take its central network and supported applications offline after suffering a ransomware attack. While not yet confirmed, the malware used in the attack has likely been traced to a LockerGoga ransomware sample uploaded to a malware engine detection site the very same day. Along with appending extensions to “.locked”, LockerGoga has been spotted in multiple European countries and seems to spread via an initial phishing campaign, and then through compromised internal networks.
The Rise of Information Stealers
This is the second of a three-part report on the state of three malware categories: miners, ransomware, and information stealers.
As noted in the last blog, mining malware is on a decline, partly due to turmoil affecting cryptocurrencies. Ransomware is also on a decline (albeit a slower one). These dips are at least partly the result of the current criminal focus on information theft.
Banking Trojans, hacks, leaks, and data-dealing are huge criminal enterprises. In addition to suffering a breach, companies might now be contravening regulations like GDPR if they didn’t take the proper precautions to secure their data. The ways in which stolen data is being used is seeing constant innovation.
Motivations for data theft
Currency
The most obvious way to profit from data theft is by stealing data directly related to money. Examples of malware that accomplishes this could include:
- Banking Trojans. These steal online banking credentials, cryptocurrency private keys, credit card details, etc. Originally for bank theft specialists, this malware group now encompasses all manner of data theft. Current examples include Trickbot, Ursnif, Dridex.
- Point of Sale (POS). These attacks scrape or skim card information from sales terminals and devices.
- Information stealing malware for hijacking other valuables including Steam keys, microtransactional or in-game items
Trade
Data that isn’t instantly lucrative to a thief can be fenced on the dark web and elsewhere. Medical records can be worth ten times more than credit cards on dark web marketplaces. A credit card can be cancelled and changed, but that’s not so easy with identity. Examples of currently traded information include:
- Credit cards. When cards are skimmed or stolen, they’re usually taken by the thousands. It’s easier to sell these on at a reduced cost and leave the actual fraud to other crooks.
- Personal information. It can be used for identity theft or extortion, including credentials, children’s data, social security information, passport details, medical records that can be used to order drugs and for identity theft, and sensitive government (or police) data
Espionage
Classified trade, research, military, and political information are constant targets of hacks and malware, for obvious reasons. The criminal, political, and intelligence worlds sometimes collide in clandestine ways in cybercrime.
As a means of attack
While gold and gemstones are worth money, the codes to a safe or blueprints to a jewellery store are also worth a lot, despite not having much intrinsic value. Similarly, malware can be used to case an organisation and identify weaknesses in its security setup. This is usually the first step in an attack, before the real damage is done by malware or other means.
“In late 2013, an A.T.M. in Kiev started dispensing cash at seemingly random times of day. No one had put in a card or touched a button. Cameras showed that the piles of money had been swept up by customers who appeared lucky to be there at the right moment.” –From a story that appeared in the New York Times
Just another day in the Cobalt/Carbanak Heists
Some examples of “reconnaissance” malware include:
- Carbanak. This was the spear-tip of an attack in an infamous campaign that stole over €1 billion ($1.24 billion) from European banks, particularly in Eastern Europe. The Trojan was emailed to hundreds of bank employees. Once executed, it used keylogging and data theft to learn passwords, personnel details, and bank procedures before the main attacks were carried out, often using remote access tools. ATMs were hacked to spill out cash to waiting gang members and money was transferred to fraudulent accounts.
- Mimikatz, PsExec, and other tools. These tools are freely available and can help admins with legitimate issues like missing product keys or passwords. They can also indicate that a hacker has been on your network snooping. These software capabilities can be baked into other malware.
- Emotet. Probably the most successful botnet malware campaign of the last few years, this modular Trojan steals information to help it spread before dropping other malware. It usually arrives by phishing email before spreading like wildfire through an organisation with stolen/brute-forced credentials and exploits. Once it has delivered its payload (often banking Trojans), it uses stolen email credentials to mail itself to another victim. It’s been exfiltrating the actual contents of millions of emails for unknown purposes, and has been dropping Trickbot recently, but the crew behind the campaign can change the payload depending what’s most profitable.
“Emotet is an advanced, modular banking Trojan that primarily functions as a downloader or dropper of other banking Trojans. Emotet continues to be among the most costly and destructive malware affecting state, local, tribal, and territorial (SLTT) governments, and the private and public sectors.”- An August 2018 warning from the American DHS
- Trickbot/Ryuk. Trickbot is a banking Trojan capable of stealing a huge array of data. In addition to banking details and cryptocurrency, it also steals data that enables other attacks, including detailed information about infected devices and networks, saved online account passwords, cookies, and web histories, and login credentials. Trickbot has been seen dropping ransomware like Bitpaymer onto machines, but recently its stolen data is used to test a company’s worth before allowing attackers to deploy remote access tools and Ryuk (ransomware) to encrypt the most valuable information they have. The people behind this Trickbot/Ryuk campaign are only going after big lucrative targets that they know they can cripple.
What are the current trends?
Emotet is hammering the business world and, according to our data, has surged in the last six months of 2018:
Data recorded between 1 July and December 31, 2018. Webroot SecureAnywhere client data.
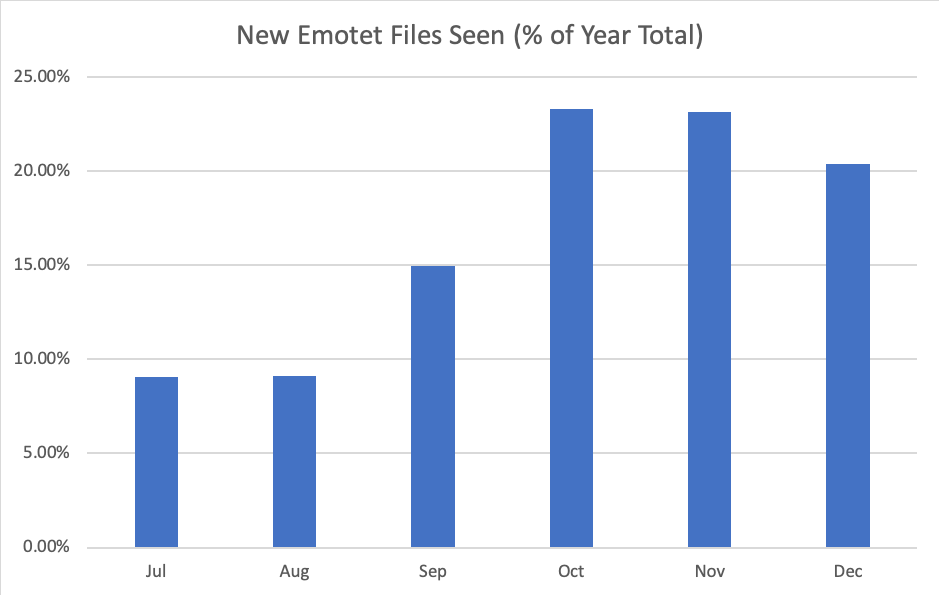
Detection of related malware surged alongside these detections. Almost 20% of Webroot support cases since the start of December have been related to this “family” of infections (Emotet, Dridex, Ursnif, Trickbot, Ryuk, Icedid).
What can I do?
- Update everything! The success of infections such as WannaMine proved that updates to many operating systems still lag years behind. Emotet abuses similar SMB exploits to WannMine, which updates can eliminate.
- Make sure all users, and especially admins, adhere to proper password practices.
- Disable autoruns and admin shares, and limit privileges where possible.
- Don’t keep sensitive information in plain text.
What can Webroot do?
- Webroot SecureAnywherehome security products detect and remove information stealers including Emotet, Trickbot, Ursnif, Heodo, and Mimikatz, as well as any other resultant malware.
- Our Identity and Privacy Shield stops keylogging and clipboard theft, even if malware isn’t detected.
- Ongoing cybersecurity education and trainingfor end users is a must for businesses to stay secure. Remember: phishing and email tend to be the top delivery methods for this malware.
- As well as helping you clean machines, Webroot’s support (in the case of infections such as Emotet) will help you plug security holes. Our specialised security hardening tools can be deployed through our console to all endpoints in a few clicks.
Information theft can be a very complicated business, but to tackle it, the basics have to be done. Criminals will always go for the low hanging fruit, so lifting your organisation’s data out of this category should be your first priority.But proper device protection and knowledge of good cyber hygiene are also essential to protecting your data. Stay tuned to the Webroot blog for the latest information on the newest threats.
Building a Cybersecurity Talent Pipeline One Coding Challenge at a Time
Like many technology companies, Webroot is constantly on the hunt for a diverse pool of engineering and technical cybersecurity talent. According to Jon Oltsik, senior principal analyst with Enterprise Security Group, a cybersecurity skills deficit holds the top position for problematic skills in ESG’s annual survey of IT professionals. In fact, the percentage of organizations reporting this problem has jumped more than 10 percent in just three years.
Here are the results from the last 4 years’ surveys:
- 2018-2019: 53% of organizations report a problematic shortage of cybersecurity skills
- 2017-2018: 51% of organizations report a problematic shortage of cybersecurity skills
- 2016-2017: 45% of organizations report a problematic shortage of cybersecurity skills
- 2015-2016: 42% of organizations report a problematic shortage of cybersecurity skills
The time has come for the private sector to take action to help develop the talent pipeline.
Start with real-world simulations
At Webroot, this need for more cybersecurity talent sprouted a partnership with the University of California San Diego Jacobs School of Engineering, which has culminated in an annual Coding Challenge.
The Challenge—presented in the form of a game—is a way for Webroot to impart real-world skills like problem solving, coding, and creative technical thinking onto the students.
The goal of the game is to be the best in the room. For the competitive students, that translated to beating everyone above them on the leaderboard. To do so, the students had to write code to control three characters to capture ghosts:
- A hunter, who worked to reduce ghost stamina,
- A ghost catcher, who trapped and released ghosts,
- A support character who focused on stunning the competition and observing the playing field as a whole.
But, as Daniel Kusper, senior QA engineer at Webroot points out, “it also provides an amazing opportunity for students to ask [industry experts] any and all questions they may have about cybersecurity and software engineering.”
In addition to honing skills like creative thinking and problem solving, students get a glimpse of real-world life for engineers and developers.
Xingyao Wu, a computer science student, said that this type of problem doesn’t have a single, specific right answer. You need creativity to come up with a solution.
“I learned how to solve this problem by thinking outside the box to create new rules or algorithms instead of just following the normal ideas.”
The advantage of real-world practice was not lost on Chris Mayton, another computer science major, either. Chris shared,“In my opinion, what you learn in class is more isolated from the real world; the data is clean and the environment is ready for you to start coding. With hackathons or coding challenges, you have to apply the concepts learned in class—which are big-picture—to real-world situations.”
Ryan Willett, a current Webroot engineering intern, may have put it best. “You need room for personal growth in the computer science field. Few classes give you the liberty to try to fail boundlessly. And there is a lot to be learned in failing. Events like the Coding Challenge help students realize that, sometimes, you’ll start down a route on a project that is very bad. You may have to throw away all your code and start again. Sometimes that’s just what you have to do to get to a workable solution.”
Given the large range and variety of technical employees that volunteered their time, the students got a diverse overview of a day-in-the-life of an engineer. Some students already had a good idea of why they’re interested in the field. Computer science and mathematics double major Guanxin Li said she“joined computer science because [she] felt like it’s really cool to build something with a couple lines of code. That’s so powerful.”

Value in internships
The winners of the event are invited to apply for internship positions at Webroot’s San Diego office. Some of the rock star students from past events have even become full-time employees. These internships provide valuable experience for those who are still figuring out where they want to focus, or what industries to explore further.
Fred Yip, manager of software development and intern manager at Webroot, challenges his interns “to solve real-world problems, and to join the team by participating in the scrum and developer sprints just like full-time employees.”
Will one Coding Challenge solve the industry’s skills shortage? No. But it is a start. And I see many other cybersecurity and tech companies taking small steps that will have an impact on our future workforce. Webroot is also seeking more partnership opportunities with other universities to host learning events, and is even looking to extend its internship program globally.
We should all be excited about the next generation of talent and what they will bring to the industry. Who knows; one of the Coding Challenge participants might someday solve a present-day cybersecurity conundrum.
Advice to students from students
“I learned you really have to focus on small ideas first before implementing something more advanced. When we started, we tried to think about implementing everything at once. But then, where do we start? Think about it as a layer by layer at a time. Build it up.” – Leo Sack, computer science major
“Design what you want to implement before you start implementing. Thinking through the strategies of what each of your ghostbusters should do. Work through each problem step by step. And be patient, definitely be patient.” – Edward Chen, computer science major
Would You Like To Know My Social Security Number?
It’ll cost you a buck. Just like everyone else’s. The use of a Social Security Number (SSN) as unique identifiers has long been a contentious subject. SSNs were never intended to be used for identification, and their ubiquitous abuse for identification and authentication has lead me to call them “Social Insecurity Numbers,” or SINs.
There was a time when my response to a breach that leaked SSNs was “the horror, the horror.” Now my cynical reaction is “big deal, they stole my public information… again.” Yes, I know it’s improper for a security expert to feel this way, but an improper response is sometimes still the correct response.
Let me walk you through both sides of the issue: the horror and the dispassion.
The Horror
When aliens visit our lifeless planet in 2525, they will run DNA tests on our remains and they will catalog or index us by our SINs. That’s one of the things that makes the theft of SSNs worrisome. SSNs do not expire. A person may expire, their SSN does not. Social security numbers are not reused. They just stop being used. Funds may be paid to surviving spouses and children, but after that the SSNs are a permanent entry in a database.
Let’s put this into perspective. Of all of the credit cards issued between 1946 and 2012, virtually none are valid. Of all of the compromised credit cards issued between 2012 and 2018, very few remain valid. Sometimes the cards are replaced before they’re fraudulently used, and other times fraudulent use results in the cancellation of the cards. In either case, the cards are simply replaced with new account numbers.
Compare this to SSNs. Of all of the SSNs issued since 1934, well… Have you ever see an expiration date on a Social Security card? You can change your credit card number. You can change bank. You can change your career, your doctor, your vet, your clothes, or your mind. But unless you enter the United States Federal Witness Protection Program, your SSN isn’t changing. (Actually, that’s a bit overstated. Under certain circumstances you can get a new SSN, but your SSN simply being compromised does not qualify you to change SSNs.)
According to a study published by Javelin, more social security numbers were involved in breaches in 2017 than credit cards. Think about that for a moment. Do you know anyone who has had a fraudulent purchase made on their credit card? Here’s where the problem becomes insidious. Credit card fraud is loud. You can hear it coming. I have alerts set up on my bank accounts so that I know each time a charge is made. I am alerted through text and email. One fraudulent charge and I know. I can act.
But SSNs are quiet. Multiple applications for credit cards can be made simultaneously, but you’re not likely to find out very quickly. Pair this with a compromised email account, and you could be in big trouble. For me, it’s of serious concern.
The Dispassion
Why don’t I worry about my SSN being leaked? Because it’s already been leaked multiple times in multiple breaches.
How do I know that?
I don’t, I just assume it has been. Why? Because my SSN has been vulnerable to theft for decades, and there are so many compromised SSNs stocking the dark web that they’re a cheap commodity. You might even expect to encounter a “buy five credit card numbers get two SSNs free” deal, or to see them sold by the dozen, like Kleenex at Costo.
According to Brian Stack, the Vice President of Dark Web Intelligence at Experian, Social Security numbers sell for only $1 on the dark web. In the massive Marriot breach, it wasn’t my SSN I was worried about, it was my loyalty program information. My loyalty program information is worth 20 times more than my SSN on the dark web. Loyalty program points can be used to buy travel or merchandise in airline shopping malls.
For several years, “assume the breach” has been the mindset of many security professionals, meaning that we should assume a company will be breached, or already has been breached, and we should be clear-eyed about it. It is a call to action. Put mitigations and remediation processes in place. Have an action plan.
For the public, and I cannot emphasize this enough, this means you should assume it was your data that was compromised in the breach, and put a remediation plan in place. If the businesses holding your data assumes your data is toast, then you should too.
What You Can Do
So, if we’re adopting the fatalist position on SSN theft, but still want to protect ourselves, what’s a person to do?
- Credit freezes and fraud alerts. Both are good proactive defenses. The Federal Trade Commission (FTC) is a good place to start if you don’t know how. For information about credit freezes, check here. For information about fraud alerts and extended fraud alerts, take a look here and here.
- Use two-factor authentication. Gmail, Facebook, Twitter, and other sites offer two-factor authentication. Typically, this means you’ll need to respond to a text or email in order to log into your account. This makes it harder for the bad guys to hijack it. Not impossible, but significantly more difficult.
- Take advantage of alerts offered by financial institutions. If someone tries to log into my bank account or make a charge on my credit or debit card, I will know it immediately.
- Be Prepared for Identity Theft. Once again, the FTC consumer information page on identity theft is a great resource for consumers, security evangelists, and businesses alike on how to build a strong defensive posture.
Identity theft is real, it can be devastating, and you need to be prepared for it. But reports of breaches that include SSNs tell me what I already know; my SSN is in the hands of cybercriminals. It has been for years.
So no, I’m not going to tell you my SSN. You’ll have to pay your dollar for it, just like everyone else.
A Miner Decline: The Slowdown of a Once-Surging Threat
This is the first of a three-part report on the state of three malware categories: miners, ransomware and information stealers.
In Webroot’s 2018 mid-term threat report, we outlined how cryptomining, and particularly cryptojacking, had become popular criminal tactics over the first six months of last year. This relatively novel method of cybercrime gained favour for being less resource-intensive and overtly criminal when compared to tactics involving ransomware. But mining cases and instances of mining malware seem to have dropped off significantly in the six months since this report, both anecdotally and in terms of calls to our support queue.
The crytpo world has gone through significant turmoil in this time, so it’s possible the reduced use of malicious cryptojacking scripts is the result of tanking cryptocurrency values. It’s also possible users are benefitting from heightened awareness of the threat and taking measures to prevent their use, such as browser extensions purpose-built to stop these scripts from running.
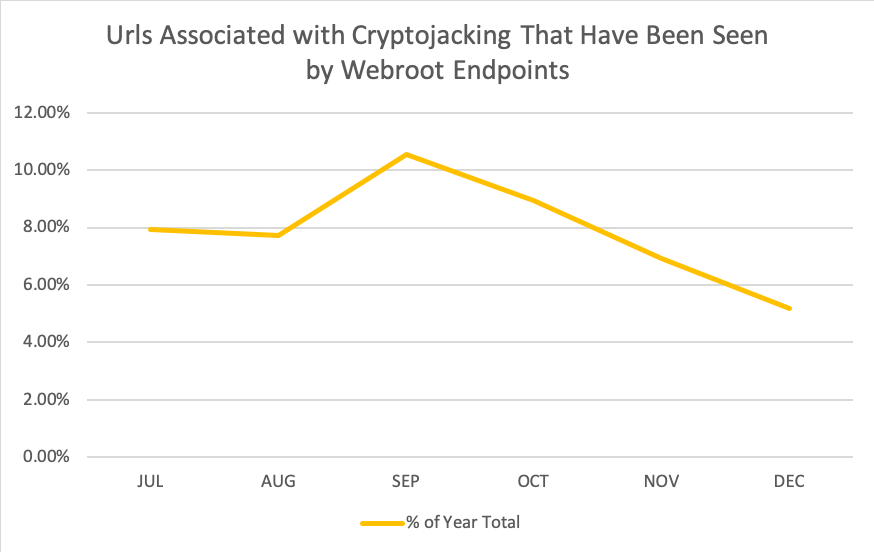
Setting aside the question of why for a moment, let’s take a look at some stats illustrating that decline during that time period.
Cryptojacking URLs seen by Webroot over six months beginning 1 July through 31 December, 2018, Webroot SecureAnywhere client data.
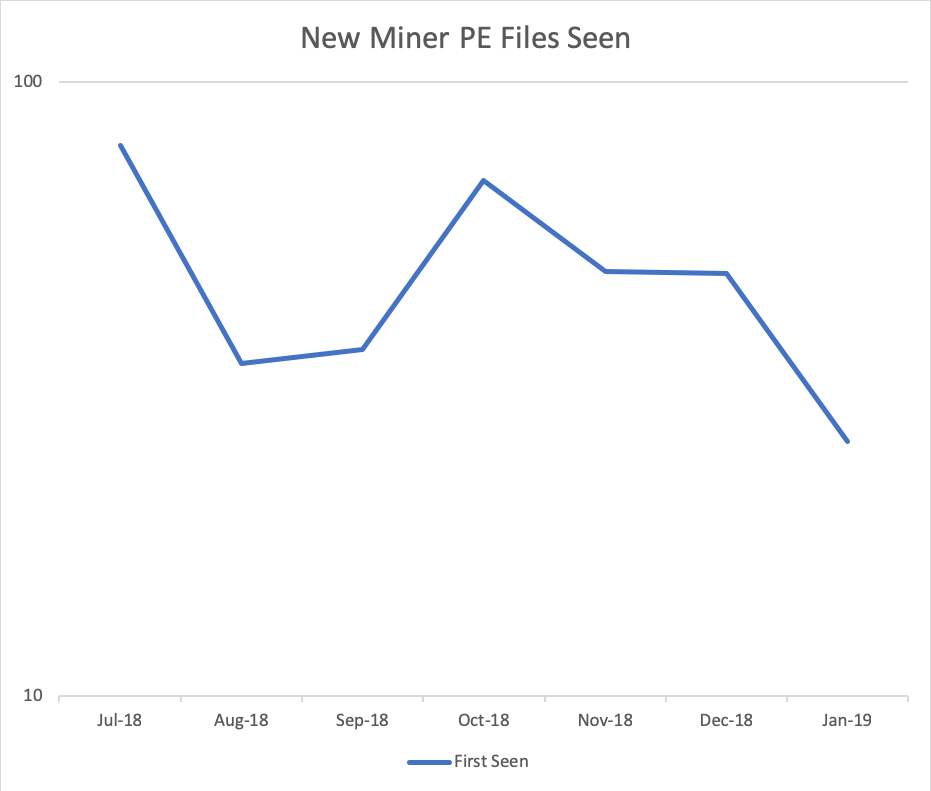
New miner malware seen by Webroot
Data from six months beginning 12 July through 9 Jan, 2019, Webroot data, units logarithmic.
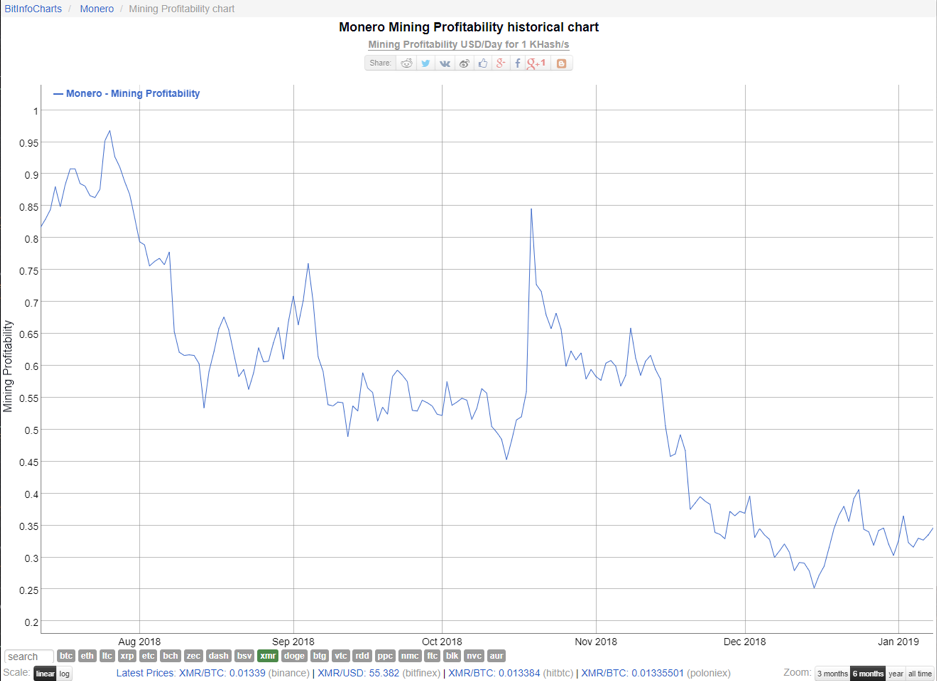
Monero mining profitability ($)
Data covering six months from 12 July – 9 Jan, 2019, Bit Info Charts, units logarithmic
Monero price ($)
Data covering six months from 12 July through 9 Jan, 2019, World Coin Index
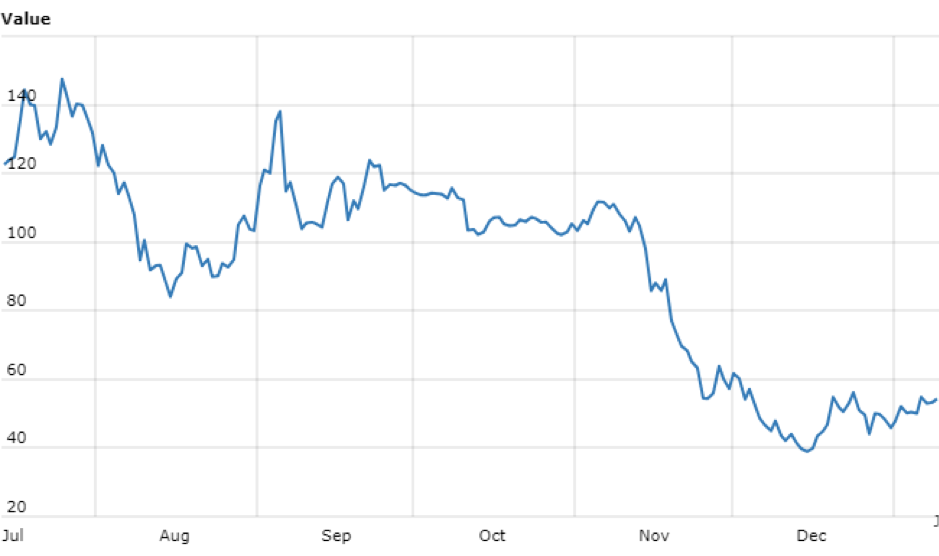
Interpreting the data
None of the graphs are identical, but without too much statistical comparison, I think a broad trend can be seen: malicious mining is on the decline alongside a general decline in coin value and coin mining profitability.
Profitability affecting criminal tactics is of course not surprising. The flexibility of exploit kits and modern malware campaigns like Emotet mean that cybercriminals can change tactics and payloads quickly when they feel their malware isn’t netting as much as it should.
Thanks to the dark web, criminal code has never been easier to buy or rent than in recent years, and cryptocurrencies themselves make it easy to swap infection tactics while keeping the cash flowing. Buying or renting malicious code and malware delivery services online is easy, so the next time the threat landscape changes, expect criminals to quickly change with it.
Should I still care about miners?
Yes, absolutely.
Cryptocurrency, cryptomining, and malicious cryptomining aren’t disappearing. Even with this dip, 2018 was definitely a year of overall cryptocrime growth. Our advanced malware removals teams often spot miner malware on machines infected by other malware, and it can be an indication of security holes in need of patching. And any illegal mining is still capable of constantly driving up power bills and frustrating users.
Where are cybercriminals focused now?
Information theftis the current criminal undertaking of choice, a scary development with potentially long-lasting consequences for its victims that are sometimes unpredictable even to thieves. The theft, trade, and use for extortion of personal data will be the focus of our next report.
What can I do?
Cryptojacking may only be on the decline because defences against them have improved. To up your chances of turning aside this particular threat, consider doing the following:
- Update everything. Even routers can be affected by cryptojacking, so patch/update everything you can.
- Is your browser using up lots of processor? Even after a reset/reinstall? This could be a sign of cryptojacking.
- Are you seeing weird spikes in your processor? You may want to scan for miner infections.
- Don’t ignore repeated miner detections. Get onto your antivirus’ support team for assistance. This could be only the tip of the iceberg.
- Secure your RDP.
What can Webroot do?
Webroot SecureAnywhere®antivirus products detect and remove miner infections, and the web threat shield blocks malicious cryptojacking sites from springing their code on home office users. For businesses, however, the single best way to stop cryptojacking, is with DNS-level protection. DNS is particularly good at blocking cryptojacking services, no matter how many sites they try to hide behind.
Persistent mining detections might point to other security issues, such as out-of-date software or advanced persistence methods, that will need extra work to fix. Webroot’s support is quick and easy to reach.
In the end, cryptomining and cryptojacking aren’t making the same stir in the cybersecurity community they were some months ago. But they’ve far from disappeared. More users than ever are aware of the threat they pose, and developers are reacting. Fluctuations in cryptocurrency value have perhaps aided the decline, but as long as these currencies have any value cryprojackers will be worth the limited effort they require from criminals.
Watch for the use of cryptominers to be closely related to the value of various cryptocurrencies and remain on the lookout for suspicious or inexplicable CPU usage, as these may be signs that you’re being targeted by these threats.
And of course, stay tuned to the Webroot blog for information on the latest threat trends.
Cyber News Rundown: Anatova Ransomware Infects the Globe
Anatova Ransomware Reaches Global Market
A new ransomware family, dubbed Anatova by researchers, has been infecting machines across the globe. During encryption, Anatova appears to focus on small files to speed up overall encryption times, but doesn’t append the encrypted files with a new extension. Unexpectedly, this variant demands DASH crypto coins, rather than using a currency with a less visible transaction ledger. It also uses several tactics to prevent analysis in both real-world and virtual environments.
Android Malware Remains Dormant until it Detects Motion
On the Google Play store, researchers have discovered several malicious apps that rely on an unusual trigger to install a banking Trojan: motion sensors. By monitoring the motion sensor in a specific mobile device, the malware can determine if it is a real victim device or a research emulator (which would likely remain stationary during analysis.) In particular, one of these insidious apps was downloading the Anubis banking Trojan, which launched a fake Android update screen to start keylogging in hopes of capturing banking credentials.
Google Faces First Major GDPR Fine
Regulators in France have issued a fine against Google for two separate complaints, the first being the company’s misuse of their users’ data, the second being the legal use of that data without providing the user enough details to give fully-informed consent. This fine is the first issued by the CNIL, the official regulator for France, and could cost Google up to $57 million.
ElasticSearch Database Exposes Online Gambling Bets
In the last couple days, security researchers have discovered a database holding sensitive information on dozens of online casino sites’ bettors. After contacting the hosting provider, researchers verified that the database, which contained over 100 million bet entries, had finally been secured. However, it’s still unclear whether the database’s owner or the ISP was responsible.
Chinese Crypto Farms Get Unique Ransomware Strain
Since China houses most of the world’s cryptocurrency mining farms, it comes as little surprise that malware authors are beginning to focus on this lucrative market. By infecting Antminer devices, which mine Litecoin and Bitcoin, this variant can quickly shut down the device and prevent further mining operations. Victims must choose between paying an extremely high ransom and allowing the infection to spread to thousands of other devices. For victims who do not pay, this variant also threatens to shut down devices’ fans, causing them to overheat and eventually destroy themselves.