Cyber News Rundown: Hackable Mercedes
The Cyber News Rundown brings you the latest happenings in cybersecurity news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst and a guy with a passion for all things security. Any questions? Just ask.
Mercedes Keyless Entry Leads to Car Theft
It was discovered this week that criminals are using an unusual technique to steal late-model that are equipped with keyless entry. By using a frequency relay box, the criminals can boost the signal from keys, often still within the home, to trick the car into thinking they are nearby and unlocking or starting the vehicle remotely. Unfortunately, this trick is also capable of deactivating pre-installed tracking systems, leaving the owner unable to locate the stolen vehicle.
Former Employee Cause of Coca-Cola Data Breach
Coca-Cola officials announced this week that a breach had taken place that could affect the personal data of at least 8,000 employees. The breach was discovered after law enforcement contacted the company regarding a mishandled hard drive. The drive itself was removed from the company by a former employee before he left, though it is still unclear if the information was used maliciously.
Honda India Leaves Unsecure Data on Thousands of Customers Online
It was recently revealed that two Amazon S3 buckets were left publicly exposed, leaving the sensitive information on over 50,000 customers widely accessible. The buckets, originally created for users of the Honda Connect app, contain everything from names and addresses to specific car details such as the VIN and Honda Connect login credentials. Additionally, the researcher who reported the exposed S3 servers also found a note from another researcher who discovered the leak and attempted to inform the owners nearly three months prior.
VPNFilter Botnet Nearing 500,000 Units Strong
Researchers have been monitoring a new botnet as it gains significant strength across the globe, currently affecting upwards of 500,000 unique devices. Using a multi-step process, VPNFilter can access the command and control server to begin gathering and sending data, along with allowing remote code execution. Unfortunately, it is nearly impossible to detect VPNFilter, as it remains relatively hidden while running its processes.
Major Canadian Banks Faced with $1 Million Ransom
Recently, officials from two of Canada’s largest banks announced that the financial information for almost 100,000 customers had been compromised and hackers are demanding $1 million to stop its public release. To make matters worse, neither bank was aware their client’s information had been stolen until the hackers demanded ransom payment, which raises concerns about what, if any, security measures they had in place.
Cyber News Rundown: Comcast Router Bug
The Cyber News Rundown brings you the latest happenings in cybersecurity news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst and a guy with a passion for all things security. Any questions? Just ask.
Comcast Router Bug Leaves Credentials Unsecured
Researchers recently found a flaw in the Comcast user authentication process that would allow anyone with an account number and partial address to illicitly access WiFi networks and alter any credentials found there. Fortunately, Comcast was quick to take down the entire site and make the necessary changes so such detailed information can no longer be gathered without proper verification.
Scam Email Warns Users of Other Scammers
A new phishing campaign is gaining traction throughout the US, with users receiving emails regarding a bank transfer of several million dollars currently being held by the Bank of England. The email itself continues by listing off a respectable number of other “scammers,” warning the victim of potential fraud linked to the listed names. While bank transfers are relatively common, it should be clear that a suspiciously large amount of money offered without context should always be approached with caution.
Teen Monitoring Software Left Available Online
Recently, a mobile app that allows parents to monitor their child’s internet browsing has left two internal servers completely accessible to the internet. While the contained information did not include any payment data, it did have email addresses and passwords for nearly all the app’s clients. TeenSafe has since taken both servers offline, though the Amazon cloud buckets were available for an undocumented amount of time with no mention of unauthorized access during that period.
Fraudulent Fortnite Apps Preceding Official Launch
As Fortnite continues its steady rise in popularity following its latest release on iOS, hundreds of phony apps have already flooded the Google Play store in advance of the Android release. One specific was downloaded over 5,000 times before researchers reported the app to the Google Security team. By promising in-game currency for downloading and rating fake apps, the spyware-laden apps quickly begin gathering call and message logs from the device while simply displaying a Fortnite icon.
Sensitive Information Found on 200 Million Japanese Citizens
Likely accumulated from several data breaches over the last few years, a dataset has been found containing the personal information of at least 200 million individuals living in Japan. The data appears to have been gathered from dozens of websites with login credentials for up to 50 unique sites and stems back to 2013. While the source of the information is still unclear, researchers have found several previous attempts to sell smaller datasets on Chinese dark web pages.
Cyber News Rundown: Chili’s PoS Breached
Chili’s Restaurant Reveals Payment Card Breach
In the last week, officials have discovered a data breach that affects an unknown number of the chain’s 1,600 restaurants across the country. It is believed that the breach could affect customers who visited the restaurant between March and April of this year, and likely includes all payment information, though Chili’s doesn’t retain any additional customer data.
StalinLocker Requires Puzzle Code to Stop Deletion
A new screen-locking malware has been spotted that avoids the ransom and moves quickly to locking the entire screen. Once the lock screen is in place, a 10-minute countdown begins, and requests the user enter a specific code or it will begin deleting the contents of every mapped drive on the computer. Along with running a countdown timer, a picture of Joseph Stalin is displayed across the screen and the USSR anthem plays in the background.
Mexican Bank Funds Transferred Illicitly
Within the past month, the Interbank payment systems of the Mexican Central Bank were compromised, leaving millions of dollars unaccounted for. Abusing the interbank payment system allowed the attackers to immediately make the transfers and withdraw in cash. Even though some of the transfers were stopped for being suspicious, the final estimate rests at over $20 million. Fortunately for the bank’s customers, it appears that the stolen funds were from the bank’s accounts, not their clients.
Latest Dharma Ransomware Variant Uses .bip Extension
The most recent variant of the Dharma/Crysis ransomware has made some subtle changes since its previous iteration. Using a compromised RDP service, attackers are able to manually install the Dharma variant, which begins encrypting all files, including mapped and unmapped network drives with a .bip extension. Even though decryption hasn’t yet been made freely available, victims are still encouraged to attempt restoring from an external backup, as this variant will completely remove all shadow copies from the system.
Danish Train Network Hit with DDoS Attack
Thousands of Danish passengers found themselves unable to purchase train tickets from multiple sources after a DDoS attack took down the purchasing system. Some were fortunate enough to be able to purchase tickets directly from train officials, as even their staff was having difficulties communicating both internally and externally regarding the issue. Luckily, the systems were quickly restored to normal operation with no residual problems.
Bad Apps: Protect Your Smartphone from Mobile Malware
Smartphone apps make life easier, more productive, and more entertaining. But can you trust every app you come across? Malicious mobile apps create easy access to your devices for Android and iOS malware to wreak havoc. And there are many untrusted and potentially dangerous apps lurking around in app stores determined to outsmart your smartphone. With the average user having 35 apps installed on their phone, according to Google, it’s easy to see why smartphones can be such a easy target.
But my iPhone is safe, right?
Both Apple iOS and Android devices are targeted by hackers, and while the latter is a more popular target, both platforms are both susceptible to various types of cyberattacks. After all, Apple’s latest version of iOS 11 was cracked just one day after its release via vulnerabilities in the Safari web browser, according to ZDNet.
Protect yourself from bad apps:
All of this means that unprotected smartphones are soft targets for cybercriminals, with weaknesses that hackers can ultimately exploit to generate revenue. The first defense is knowing that you can’t trust all apps. These tips will also help you stay protected as you search for the good ones:
- Download apps from reputable stores. The major, reliable providers are Galaxy Apps (Samsung), the App Store (iOS), Amazon App Store, and Google Play (Android).
Google Play, for example, scans 50 billion apps daily to detect malware before publishing new ones. - Disable “Unknown Sources” for Android devices, which prevents installing apps from sources other than the Google Play Store. So, if you use Amazon App Store, you’ll need to enable “Unknown Sources”. In that case, be mindful before allowing any other app or website to install something on your phone. It should also be noted that changes to this functionality are coming with the latest update to Android’s Oreo operating system.
- Keep Android USB debugging off. It can prevent outside malware from accessing your phone through corded connections, such as from a public charging station.
- Don’t jailbreak your iPhone. Allowing access and changes to your phone’s software can allows outsider apps that may not be trustworthy.
- Beware of any website, text, email, or anything asking you to install an app. Search for your own apps at the store and research all apps before installing.
- Beware of granting excessive permissions. Apps that perform basic functions, such as a flashlight, don’t need to access your personal information, for example.
- Read app reviews before installing, and review and report sinister apps. Users working together as a community can help alert unsuspecting victims to phony apps.
- Be cautious about providing your credit card or banking information. Avoid making transactions over apps that are not well known to you or the user community and be careful about hidden charges such as microtransactions.
- Install OS and other software updates. It always recommended to keep your OS and apps updated with the latest patches. It’s also smart to consider phones from vendors that release prompt security patches. Many software updates are designed to defend against malware and other emergent threats.
- Use trusted internet security software. No matter how careful you are, it is wise to employ a reputable layer of online security.
Prevention, prevention, prevention.
Sometimes free mobile apps, including free security software apps from unknown providers, are suspect. The convenience of a quick download and excessive trust are not worth saving a few seconds or cents. Do your research, follow these 10 tips, and protect your well-being on any mobile device.
Cyber News Rundown: Excel JavaScript Support May Open Door to Exploits
Crypto Mining Makes the Jump to Excel
With the recent Microsoft release supporting JavaScript within Excel, it was only a matter of time before the scripting service was manipulated to mine cryptocurrency. Mere hours after the release, the first proof of concept appeared, with easy-to-replicate steps to get CoinHive functioning. While this proof of concept does require an Office Insider build to accomplish, it will likely be just as feasible when JavaScript is introduced into the publicly available version of Excel.
SynAck Ransomware Employs Unique Evasion Tactics
A relatively new ransomware variant, known as SynAck, has recently been spotted using an uncommon method for evading security measures. Using a procedure called Process Doppelganging, the malware can create a copy of a legitimate process and inject malicious code to be executed without running anything suspicious. Additionally, the malware is heavily obfuscated and targets numerous programs before encryption to shut down any running processes or tasks that may be necessary to encrypt.
Japanese Security Cameras Defaced
Over the past several weeks, Japanese officials have been dealing with complaints from victims whose security cameras have been hacked. These attacks arose due to negligence on the part of the camera owners, who disregarded proper security practices and failed to update the default passwords on the devices. To make matters worse, the frequency of these attacks has been steadily climbing in the last couple days, and have begun to include government-owned devices on secured networks.
Facebook Exploit Used for Crypto Mining
Researchers have recently discovered a malicious Chrome browser extension that attempts to steal account credentials for any cryptocurrency trading platform it finds on the system. By spreading through Facebook Messenger, FacexWorm can propagate quickly and begin any data gathering or cryptocurrency mining with relative ease. While most of its victims have been located in Southeast Asia, numerous occurrences have been spotted in Western European countries as well, demonstrating the extension’s reach and speed.
Phishing is Still Leading Mobile Infection Rates
In a recent report based on phishing statistics over the past year, officials found that Apple iOS® users had a significantly higher chance of receiving a phishing attempt than downloading malware. With over 4000 new phishing sites being created daily and over half of all internet usage occurring on mobile devices, it’s no surprise that attackers have shifted their focus to this immense group of users, who typically lack security software for their devices and typically don’t consider mobile security necessary.
Tech Support Scams: From Bad to Worse
Fake tech support scams aren’t going anywhere. In fact, recent data shows this type of social engineering attack is on the rise—with phony tech support calls, emails, and pop-ups peddling the digital equivalent of snake oil to unsuspecting internet users around the world.
While many people have grown wise enough to spot the warning signs of the typical tech support scam, a significant percentage fall victim, and exploiting their naivety can prove quite profitable for cybercriminals. A recent report from Microsoft describes a growing global problem: 153,000 reports were received from Microsoft customers involved in tech support scams in 2017, leading to a 24 percent rise in tech scams reported by Microsoft from the previous year. Those who lost money forked over an average of $200 and $400.
“It doesn’t require a great deal of technical knowledge to carry out a support scam, so it’s easy to see why criminals are choosing to jump into this field,” said Marcus Moreno, Supervisor of Threat Research at Webroot. “All that’s is needed is gaining the user’s trust and knowing more than they do about their computer. Whether criminals pay websites to host their fake support banners, or they proactively reach out to you, it doesn’t take much expertise.”
Due to the lucrative nature and relative success rate of these social engineering tactics, tech support fraud continues to propagate. The FBI’s Internet Crime Complaint Center (IC3) received around 11,000 cases of tech support scams in 2017, with victims claiming nearly $15 million in losses. That’s a shocking 86 percent increase from 2016!
The IC3 report also noted new variations of the typical tech support scam, with attackers resorting to posing as law enforcement to re-target previous victims by offering phony recovery assistance in exchange for a fee. Tech support scams are also turning to target cryptocurrency users, where the stakes can be higher, netting potentially thousands of dollars from a single victim.
Cold calls? Hold the phone!
The number one thing to keep in mind is that major tech companies—whether that’s Microsoft, your security software provider, or your device manufacturer—will never call you out of the blue. Beyond attempting to dupe a victim out of a fee for fake support services, cybercriminals can also try to gain remote access to your computer to steal personal information and install malware that can carry on the attack after the phone call has ended.
It’s also important to know that tech support scams also appear in the form of malvertising, such as pop-ups that can be found even on legitimate websites. These scam ads try to trick users with various fake system errors or malware infection warnings. Thousands of websites were recently discovered to be infected with malicious ads that lock users’ browsers and display a fake infection warning, according to SC Magazine. Web-based threats like this highlight the importance of keeping your devices updated and secure, as well as practicing safe browsing habits.
Visit our Cybersecurity Education Resources to understand more about common tech support scams and how to avoid falling victim. There you can also find blacklists of URLs and phone numbers known to impersonate Webroot and target our customers.
Cyber News Rundown: GDPR Edition
As the EU’s General Data Protection Regulation (GDPR) edges closer, we’re looking back on the five most significant stories during the lead up to its implementation. Read about GDPR’s impact on data security and find out how to get prepared with five steps to compliance.
What aspect of GDPR will have the biggest impact on you or your business? Let us know in the comments below!
GDPR Myths
On April 14, 2016, the EU received its final legislative approval for GDPR, making the changes official as of May 25, 2018. Many myths surround the legislation, stirring confusion among those affected. One major myth is that GDPR compliance is focused on a fixed point in time, similar to the Y2K bug. However, GDPR will be an ongoing journey that requires a complete change to many company procedures. The regulation will begin in May 2018, so businesses may not be pleased to discover they are currently in the “grace period,” and there will not be another one after the implementation date.
Data Breached
We discovered in 2017 that many corporations are far too negligent when it comes to securely storing sensitive consumer data. It seemed like hardly a week passed without another major data breach making headlines. The year saw Equifax fall victim to the largest data breach in corporate history, Uber conceal a breach affecting 57 million users for over a year, and more than a million patients’ records stolen from the NHS’s database, to name just a few high profile cases. GDPR will not stop data breaches entirely, but the introduction of fines as high as €20 million, or 4% of annual turnover, for noncompliance should force companies to take their data responsibilities more serious.
Brexit
Britain’s decision to exit the European Union has added confusion concerning GDPR compliance for companies within the UK. In September, however, the UK updated their data protection legislation, which brings GDPR wholesale into UK law. This confirms that the UK also recognises the importance of data protection and suggests UK companies will need to be at least as careful as their EU peers. Also, any company dealing with EU citizen data (even those located outside of the EU), will be expected to comply with these standards.
Google and the Right to be Forgotten
Google received 2.4 million takedown requests under the EU’s updated ‘right to be forgotten’ laws, which have been in place for search engines since 2014. GDPR will now expand on this right to certain data subjects- giving people more control over deletion of their data once it’s no longer necessary for a company to have. Data subject rights have been enhanced, so companies that process personal data will be expected to have procedures in place to act on requests in the proscribed timeframes.
Facebook have been in the news a lot over data rights, most recently for allegedly allowing Cambridge Analytica to harvest the data of more than 50 million Facebook users. Previously, the ICO had gotten WhatsApp to sign an undertaking in which it committed publicly to not share personal data with its parent company Facebook until the two services could do it in a GDPR-compliant way. GDPR is clearly bearing down on big companies that have been negligent with customer data previously.
How to get prepared
Are you prepared for GDPR? A company can take the following steps to help become GDPR-ready:
- Know the facts: GDPR is coming, so make sure everyone in your company is aware of the important components and are fully trained to comply. Examine what data your company has and who you share it with. Auditing your data will help you to understand how you can meet the terms.
- Privacy Information: Revisit the procedures governing how you inform individuals about personal data your company may be holding. Make amendments to those procedures as necessary to meet GDPR requirements.
- Individuals Rights: Verify your procedures cover the rights of individuals, including your processes for deleting or responding to a subject access request.
- Enforcement and Sanctions: It should be noted that GDPR will simplify enforcement for supervisory authorities and significantly increase fines.
- Consent: Data must be processed lawfully. There are many legitimate bases for processing personal data. However, most companies will use consent, contractual necessity, or legitimate interest as a basis for doing so.
Did You Know?
Webroot Security Awareness Training offers GDPR-specific compliance training modules to help ensure your employees are up to speed with the new regulations, in addition to industry-specific compliance courses. Learn more at webroot.com/awareness.
Cyber News Rundown: Facebook Reveals “Clear History” Feature
The Cyber News Rundown brings you the latest happenings in cybersecurity news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst and a guy with a passion for all things security. Any questions? Just ask.
Cyberattack Shuts Down Mexico Central Bank
Within the past week, several payment systems associated with Mexico’s central bank were compromised for an unspecified amount of time. The impacted systems led to delays with money transfers and processing of transactions for central bank customers, but officials claim no funds or data were stolen. It is still unclear how the attackers accessed the systems, though the issue has heightened awareness of possible security flaws.
Facebook Implementing History Removal Tool
In the wake of the data mishandling scandal that tarnished Facebook’s privacy standards, the company announced it’s working on a new tool that will allow users to clear browsing history and cookies from within Facebook, along with opting out of allowing Facebook to gather future browsing data. While this tool is still being created, Mark Zuckerberg has said Facebook hopes to give more privacy controls back to the users who trust the site.
Fitbit Adopts Google Healthcare API
Recently, Fitbit announced they will be integrating their current systems to incorporate the Cloud Healthcare API from Google in order to give healthcare providers better access to important data. Fitbit has been working towards this for some time by constantly improving their data analysis and providing better feedback to users and their health professionals. The partnership with Google’s API allows them to use an industry-compliant system, without the trouble of creating one from the ground up.
Northeast School District Pays Hefty Ransom
Following the April 14 cyberattack that encrypted much of a Massachusetts school district’s computer systems, local police recommended the district pay the $10,000 ransom to restore the system. While it paying ransoms is normally suggested only as a last resort, it would appear that the district wasn’t capable to restoring the systems on their own. In the end, it opted to pay the requested amount in hopes the criminals stay true to their word.
DVRs Being Compromised
A researcher recently released a tool that would allow anyone access to several brands of DVRs and illicitly obtain both device credentials and live video recordings. Using Shodan, the researcher was able to identify nearly 55,000 unique, accessible DVR devices that could be exploited with his tool using a previously discovered flaw for DVR devices.
DNS Protection Gets Major Updates
Our most recent release of the DNS Protection agent provided customers with added features and enhancements designed to improve the overall product experience and its capabilities delivered to end users. We revamped the network detection functionality to improve accuracy and speed for roaming and off-site clients who frequently change networks.
We also addressed a variety of small bug fixes and performance improvements, such as SSL certification installation on Firefox Quantum and improvements to the agent update process.
VPN & TCP support
The Webroot DNS Protection agent now supports Juno Pulse Secure v 3.5 and Private Internet Access (client version 7.5) VPN types. This new feature enables roaming clients to access intranet assets and ensure clients benefit from DNS Protection while using a VPN.
Additionally, we added TCP Traffic support filtering. While the majority of DNS traffic is handled via UDP, certain domains and applications only use TCP. This update allows the agent to filter both UDP and TCP traffic.
Policy Configuration
We have also enhanced policy configuration with more granular policy control. Custom policy configurations can now be applied to groups, sites, individual devices or network IP. We’re also working to improve internet usage visibility, and are excited to make our Top Active Report available for .csv export so it can be easily integrated into other reporting tools in use.
Finally, we’re updating the GSM console to give users the availability to initiate trials and/or purchase products directly within the console.
‘Smishing’: An Emerging Trend of Phishing Scams via Text Messages
Text messages are now a common way for people to engage with brands and services, with many now preferring texts over email. But today’s scammers have taken a liking to text messages or smishing, too, and are now targeting victims with text message scams sent via shortcodes instead of traditional email-based phishing attacks.
What do we mean by shortcodes
Businesses typically use shortcodes to send and receive text messages with customers. You’ve probably used them before—for instance, you may have received shipping information from FedEx via the shortcode ‘46339’. Other shortcode uses include airline flight confirmations, identity verification, and routine account alerts. Shortcodes are typically four to six digits in the United States, but different countries have different formats and number designations.
The benefits of shortcodes are fairly obvious. Texts can be more immediate and convenient, making it easier for customers to access links and interact with their favorite brands and services. One major drawback, however, is the potential to be scammed by a SMS-based phishing attack, or ‘Smishing’ attack. (Not surprisingly given the cybersecurity field’s fondness for combining words, smishing is a combination of SMS and phishing.)
All the Dangers of Phishing Attacks, Little of the Awareness
The most obvious example of a smishing attack is a text message containing a link to mobile malware. Mistakenly clicking on this type of link can lead to a malicious app being installed on your smartphone. Once installed, mobile malware can be used to log your keystrokes, steal your identity, or hold your valuable files for ransom. Many of the traditional dangers in opening emails and attachments from unknown senders are the same in smishing attacks, but many people are far less familiar with this type of attack and therefore less likely to be on guard against it.
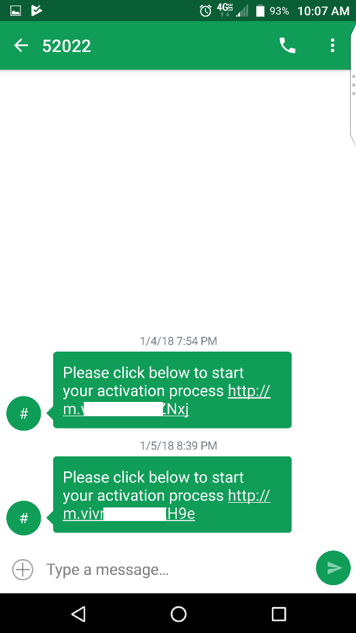
Text messages from shortcodes can contain links to malware and other dangers.
Smishing for Aid Dollars
Another possible risk in shortcodes is that sending a one-word response can trigger a transaction, allowing a charge to appear on your mobile carrier’s bill. When a natural disaster strikes, it is common for charities to use shortcodes to make it incredibly easy to donate money to support relief efforts. For instance, if you text “PREVENT” to the shortcode 90999, you will donate $10 USD to the American Red Cross Disaster Relief Fund.
But this also makes it incredibly easy for a scammer to tell you to text “MONSOON” to a shortcode number while posing as a legitimate organization. These types of smishing scams can lead to costly fraudulent charges on your phone bill, not to mention erode aid agencies ability to solicit legitimate donations from a wary public.
Another common smishing technique happens during tax-filing season and involves IRS-themed requests for the taxpayer to update personal and financial information. An uptick in these scams after the pandemic prompted the FBI to post public warnings.
Protect yourself from Smishing Attacks
While a trusted mobile security app can help you stay protected from a variety of mobile threats, avoiding smishing attacks demands a healthy dose of cyber awareness. Be skeptical of any text messages you receive from unknown senders and assume messages are risky until you are sure you know the sender or are expecting the message. Context is also very important. If a contact’s phone is lost or stolen, that contact can be impersonated. Make sure the message makes sense coming from that contact.
Related Resources:
Webroot blog: Smishing Explained: What It Is and How to Prevent It
Webroot blog: What’s Behind the Surge in Phishing Sites? Three Theories
RSAC 2018: “Clearing A Path for More Conversation and Context”
Two big trends stood out at RSAC 2018. Many organizations that once thought all threat intelligence was created equal have gained appreciation for quality data feeds that deliver real-time information vs. crowdsourced or static lists. Endless alerts and flashy numbers are no longer enough. Companies want to know the “why?” and “what actions they can take?”
“What this tells me is that Webroot is in the right place at the right time with the best solution, and that is a great place to be,” said Michael Neiswender, vice president, embedded security sales.
The subtle messages of small-to-medium businesses (SMBs) and managed service providers (MSPs) demanding a certain focus didn’t fall on deaf ears. The question asked over and over was “how do you get into the SMB space?” There was a clear understanding that it’s a hot market, hard to penetrate, and has specific needs. SMBs require solutions architected from the ground up for multitenancy, high efficiency, and ease of use—customer experience cannot be neglected.
David Dufour, vice president, engineering said, “MSPs are a big business. A lot of people are aware of it, but they don’t know how to attract that market. We’re in a really good position as a company because we understand them.”
Big Conversations
As Webroot spoke with industry peers during the four-day cybersecurity conference, the conversations led to a few more themes.
Real Threat Intelligence is King
Security professionals have a desire for real-time, quality threat intelligence. They are looking for insights that draw from multi-geo, -device, and -businesses. How the updates are delivered to the customer is also of importance. The reality is the scale of threats and the associated risks facing organizations is increasing at a rate companies are finding difficult to manage.
Security is Everyone’s Responsibility
The idea of inherent security will become more mainstream. All companies will have to start thinking and acting like security companies, putting user education first. Loosely handling personal data is no longer an option. GDPR will make sure of that. Simple: your weakest link can be your strongest defense if properly trained.
Getting Back to Basics
Fundamental concepts of cybersecurity are as relevant as ever. The basics at their core address security as a requirement for businesses today in our connected environment. To be effective using cybersecurity start by following the basic fundamental concepts of protect, detect, respond, recover, and user training.
Into the Future
Threat intelligence will continue to offer a powerful position for those who choose to listen to the industry. As Webroot prepares for greater growth in the coming months and years, we are uniquely positioned for the future. You can expect more threat intelligence insights via our Annual Threat Report and Quarterly Threat Trends; continued investigation into our partners’ needs; and solutions that will meet partners where they are.
More companies will realize their customers want them to look at them in a new light. They will also begin to ask the right questions to provide solutions that uniquely address the concerns security professionals have when building their own internal security programs.
“There were companies that I could tell had methodically built out platforms to address specific threats,” said Gary Hayslip, chief information security officer. “These vendors differed from their competitors, because they knew what issues to solve and their technologies were uniquely focused on providing value by integrating with broader platforms to manage risk.”
Cyber News Rundown: Amazon DNS Service Hijacked
The Cyber News Rundown brings you the latest happenings in cybersecurity news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst and a guy with a passion for all things security. Any questions? Just ask.
Amazon IPs Rerouted for Several Hours
Early Tuesday morning attackers compromised an ISP that allowed them to reroute 1,300 IP addresses belonging to Amazon’s Route 53 DNS service. Amazon quickly released a statement on the issue and clarified that it was a specific vendor’s domain that was sharing the traffic across multiple peer networks. In doing so, the attackers were able to masquerade as MyEtherWallet.com, which netted them over $150,000 in cryptocurrency.
Middle East Ride-Hailing App Compromised
In an announcement at the beginning of this week, the ride-hailing app Careem addressed a data breach that occurred in mid-January. The breach could affect nearly 14 million customers, though officials have stated that no payment information was amongst the compromised data, as it is stored off-site. Fortunately, the breach shouldn’t affect anyone who signed up for the app after January 14.
Complaints of Tech Support Scams on the Rise
Over the course of 2017, Microsoft saw a 24% rise in the number of complaints regarding tech support scams their customers fell victim to. This increase is similar to the findings of the FBI’s Internet Crime Complaint Center, which saw an 86% change from the previous year. While the tactics used have not varied much, the number of scam calls have gone up significantly and have branched out to include both Mac and Linux users.
City of Atlanta Closing in on $3 Million Mark for Ransomware Recovery
It was recently revealed the City of Atlanta has spent close to $3 million to recover from a ransomware attack nearly a month ago. Though the original ransom was set at $51,000, paying it would not guarantee a swift resolution. Even now, Atlanta is still working on returning its systems to full working order. The delay may have been lengthened by the unknown amount of time the hackers had access to its system.
Malicious Crypto-miner Disables System Security
The newly dubbed PyRoMine, a cryptocurrency miner, which uses the EternalRomance NSA exploit to propagate, has been spotted in the wild over the past month. By disabling any security services it encounters, as well as Windows Updates, the malicious VBScript is able to compromise RDP to allow consistent traffic through port 3389. Even though it hasn’t spread widely, the number of unpatched machines still accessible to malware authors is a goldmine just waiting to be found.

















