Cyber News Rundown: 2017 Year in Review
As 2017 comes to a close, we’re looking back at the 10 most significant (or simply the most devastating) cybersecurity stories of the year. Read through the list below to see which attacks, data breaches, and other events left a lasting impact on both the security industry and the global online community overall.
Which story meant the most to you or your business? Let us know in the comments below!

MongoDB Hacks
In January of this year, MongoDB suffered a severe hack that left thousands of installations at the mercy of a ransomware attack that transformed into a destructive force, by deleting thousands of data entries while still leaving a ransom note behind to taunt the victims. At its peak, this specific attack was being played out by up to 12 unique attackers, all leaving their own ransomware variant and encryption information on the systems, making it exceedingly difficult for remediation.

WikiLeaks Release CIA Vault 7
By March, an enormous national security hole was revealed thanks to a release on WikiLeaks dubbed “Vault 7”, which exposed information on CIA hacking, zero-day exploits that they had used, and finally that the lead security organization in the country is not invulnerable to security flaws. While consumer data has become less and less secure due to retail data breaches, it’s shocking that such a trove of information could be heisted from right under the noses of those whose job it is to protect some of the nation’s greatest secrets.

Shadow Brokers Divulge NSA Exploits
Just a short month after the WikiLeaks dump came the sudden flood of software exploits, all from the National Security Agency’s systems. Most of these were initially labeled as zero-day exploits that focused on older Windows operating systems that hadn’t received security updates, something which many large organizations had yet to implement. While Microsoft was quick to push out patches for these vulnerabilities, some of which were available for nearly a month prior to the actual Shadow Broker’s reveal, these exploits were later used for some of the largest ransomware attacks to date.

WannaCry Ransomware Tackles Globe
Within weeks of the last Shadow Brokers dump, organizations in over 150 different countries were dealing with the WannaCry ransomware that spread like wildfire across at least 150,000 individual endpoint devices. By propagating like a worm, the infection was able to spread quickly, exploiting several largely unpatched vulnerabilities in several Windows operating systems. While a patch for un-updated systems has been publicly available since March, many organizations struggled to roll it out to their endpoints, or couldn’t do so without rendering their proprietary software unusable. Months after the initial WannaCry campaign was launched, systems across the globe were still getting infected, including a Honda production plant in Japan, and an entire network of traffic cameras in Australia.

NotPetya Causes Global Chaos
Following closely behind the WannaCry campaign was a new variant of an older ransomware, dubbed NotPetya. The variant used similar tactics to the original Petya ransomware, though it had an entirely different agenda. By using the EternalBlue exploit made available by the Shadow Brokers back in March to attack unprotected Windows systems, NotPetya encrypted thousands of systems by booting to a fake ChkDsk to cover its actions, and then leaving the victims without a method to pay the ransom or make any attempts to retrieve their destroyed data.

NHS Database Exposes Over 1 Million Patient Records
By August, a breach had been discovered in a patient booking system known as SwiftQueue, which is widely used by several National Health Service facilities across the UK. The database in question contained patient information for nearly 1.2 million citizens, and to makes matters even worse, the attackers also claimed to have found additional vulnerabilities within SwiftQueue’s software and possessed of all 11 million records stored by the company. The breach comes just 2 months after the NHS fell victim to the WannaCry attacks that affected hundreds of industries around the world.

Equifax Sees Largest Data Breach to Date
In early September, Equifax announced that it had been compromised, leaving over 145 million Americans social security numbers and other highly sensitive information both vulnerable and likely for sale. The original point of access would seem to be their main Argentinian employee portal page which, through simple HTML viewing, could show both the username and password for nearly 14,000 customers who had filed a complaint, along with their social security number-equivalent, all stored in plain text.

Big Four Accounting Firm Breached
Using an administrative account without 2-factor authentication to gain access to their email system is the likely entry point for the September breach involving Deloitte, one of the world’s largest accounting firms. The attack appears to have only affected a limited number of the firm’s clients, though actual figures have remained quiet. In addition to the improperly managed client data, it was also revealed that the company’s entire email database, including administrative accounts, had been accessed by the attackers for an unknown amount of time. While the scale of this attack appears relatively small in comparison to Equifax, it should be known that Deloitte works with some of the largest organizations currently in operation and the sensitive nature of their information could be catastrophic if placed in the wrong hands.

Yahoo Breach Expands to All 3 Billion Users
In a mid-September statement, Yahoo announced that the initial breach that occurred in 2013 and took nearly 4 years of investigation, has impacted all the company’s 3 billion unique users. Along with this recent update, the company is still reeling from yet another data breach that happened in 2014, but pushes Yahoo into the podium as the largest data breach in current history. This update to the total affected users comes as little surprise, as the original breach left questions as to why some accounts were compromised quickly, while others remained untouched and showed no signs of malicious activity for several years.

IoT Takes Major Hit with Krack Attacks
To round off a high-profile year, a vulnerability was found within the Wi-Fi encryption currently in use by hundreds of millions of IoT devices around the world. The vulnerability has fortunately been patched by dozens of vendors for quite some time now. However, there are still some devices that won’t likely receive an update in the near future: security cameras, routers, and other household wirelessly connected ‘things’ due to the complexity and sheer quantity of devices that even one vendor can bring to market, let alone the dozens of vendors who are currently working with their partners to decide on the best methods for tackling this enormous vulnerability.
Cyber News Rundown: Edition 12/08/17
The Cyber News Rundown brings you the latest happenings in cyber news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst, and a guy with a passion for all things security. Any questions? Just ask.
PayPal Plagued by Phishing Emails
Recently, many PayPal users have received emails about a fake transaction failure that request the user verify their login credentials. While many users were quick to notice the illegitimate sender email address, they also noticed that the email didn’t call them by name or username. Anyone who did follow the verification link would land on a fake site that asks the user to reenter their payment information and security questions.
Satori Botnet Emerges with 280,000 Infected Devices
Closely following worm behavior, the Satori variant of Mirai is able to spread quickly by using exploits to remotely connect to devices with unsecured ports, specifically ports 37215 and 52869. While exact methods are still unclear, Satori appears to be using a zero-day exploit for Huawei routers that received some attention in late November for allowing unauthorized code execution on affected devices. Use of Mirai variants has continued to rise in prevalence following the initial Mirai botnet discovery, which received worldwide attention for being the largest active botnet to date.
Virtual Keyboard App Leaves Data Exposed
With over 40 million users worldwide, you might expect a popular virtual keyboard app company would use strong data protection, rather than hosting the information on a simple server without so much as a password. Although the company secured their server shortly after learning of the vulnerability, 577 gigabytes worth of sensitive user data were available for an unknown period of time. The data included names and email addresses, along with user locations by city. Even worse, any keystrokes entered via the app were recorded and stored; this data was also on the unencrypted server.
Phishing Sites Now Use HTTPS to Appear Legitimate
In the past few years, security measures for websites have gotten significantly stronger, but cybercriminals are managing to close the gap. By implementing HTTPS for phishing sites, scammers can trick victims into divulging their information even more easily. After all, many users have been trained to look for the HTTPS protocol to ensure a website’s security. In a recent sample collected over a 24-hour period, nearly 200 unique phishing pages were found using HTTPS, even though it isn’t necessary for anything beyond user deception.
Apple Root Bug Resurfaces After Update
As a follow-up to last week’s new regarding a bug that allowed anyone with access to the device to gain “root” or administrative privileges, the bug appears to have resurfaced on systems that received the update after the patch was released. In addition to the bug’s return, the security update also managed to break Apple’s file sharing functionality. They have since pushed out yet another update that appears to patch all the recent issues.
How to Outsmart Mobile Threats
As the holiday season kicks into high gear, keep in mind that shoppers are at an even higher risk of cyberattacks during this time of year. Salesforce projects that mobile users will account for 60 percent of traffic to retail sites around the globe this year. With the increased popularity of shopping on the go, more and more cybercriminals will move to prey on unsuspecting shoppers. Here are a few tips to minimize your chances of falling victim to cybercriminals this holiday season (and all year long).
Sophisticated attacks on smartphones
The fact is, mobile threats are on the rise. The Webroot 2017 Threat Report revealed a spike in malicious mobile apps, noting that almost half of new and updated mobile apps analyzed over the previous year were classified as malicious or suspicious. That’s nearly 10 million apps, up from a little more than two million such apps in 2015.
Given the rising frequency of cyberattacks and data breaches year over year, it’s no surprise that we’ve continued to see more sophisticated smartphone attacks. Some of the most common mobile threats users face are mobile web browser-based hacking, adware, remote device hijacking and eavesdropping, and breaches of mobile payment services.
Why you need a mobile security app
To avoid becoming a hacker’s next victim, protect your device with a mobile security app. A trusted security app can block infected or malicious apps and file downloads. It can also help protect your identity and personal information if your mobile device is lost or stolen.
It’s worth pointing out that all mobile security services are not created equal. In October, independent testing firm AV-TEST found that Google’s Play Protect service, which is designed to safeguard Android apps, was found to be “significantly less reliable” than third-party security apps, according to The Next Web.
Outside of a solid mobile security app, Webroot Chief Information Security Officer Gary Hayslip recommends making sure mobile devices are up to date:
“I recommend getting in the habit of periodically checking for updates and, if any are available, installing them. Updates that are waiting to be installed are accidents waiting to happen; they are doorways that can be exploited to access your devices or steal or encrypt your information. Don’t make it easier for your device to be compromised, keep it updated with the latest patches.”
Safety measures
In addition to a mobile security app and frequent updates, you should also be protective of your mobile device’s connections. Follow these two tips to double-down on your mobile safety:
- Turn off your Bluetooth: Bluetooth is a resurgent way for cyber deviants to gain access to your devices and personal information, so be sure to keep your Bluetooth off while out and about doing holiday shopping.
- Data over WiFi: Public WiFi networks are notorious hotbeds for digital attacks. If you have to do your holiday shopping online in public, use your cellular connection instead. If you’d rather not use data, a virtual private network (VPN) is a great way to protect yourself while connected to a public network on your mobile device.
New Cryptojacking Tactic May Be Stealing Your CPU Power
What if cybercriminals could generate money from victims without ever delivering malware to their systems? That’s exactly what a new phenomenon called “cryptojacking” entails, and it’s been gaining momentum since CoinHive first debuted the mining JavaScript a few months ago.
The intended purpose: whenever a user visits a site that is running this script, the user’s CPU will mine the cryptocurrency Monero for the site owner. This isn’t money out of thin air, though. Users are still on the hook for CPU usage, the cost of which shows up in their electric bill. While it might not be a noticeable amount on your bill (consumer CPU mining is very inefficient), the cryptocurrency adds up fast for site owners who have a lot of visitors. CoinHive’s website claims this is an ad-free way for website owners to generate enough income to pay for the servers. All altruistic excuses aside, it’s clear threat actors are abusing the tactic at the victims’ expense.
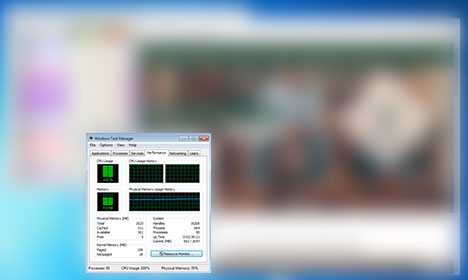
In the image above, we can see that visiting this Portuguese clothing website causes my CPU to spike up to 100%, and the browser process will use as much CPU power as it can. If you’re on a brand new computer and not doing anything beyond browsing the web, a spike like this might not even be noticeable. But if you’re using a slower computer, just navigating the site will become very sluggish.
Cybercriminals using vulnerable websites to host malware isn’t new, but injecting sites with JavaScript to mine Monero is. In case you’re wondering why this script uses Monero instead of Bitcoin, it’s because Monero has the best hash rate on consumer CPUs and has a private blockchain ledger that prevents you from tracking transactions. It’s completely anonymous. Criminals will likely trade their Monero for Bitcoin regularly to make the most of this scam.
CoinHive’s JavaScript can be seen in this website’s HTML:
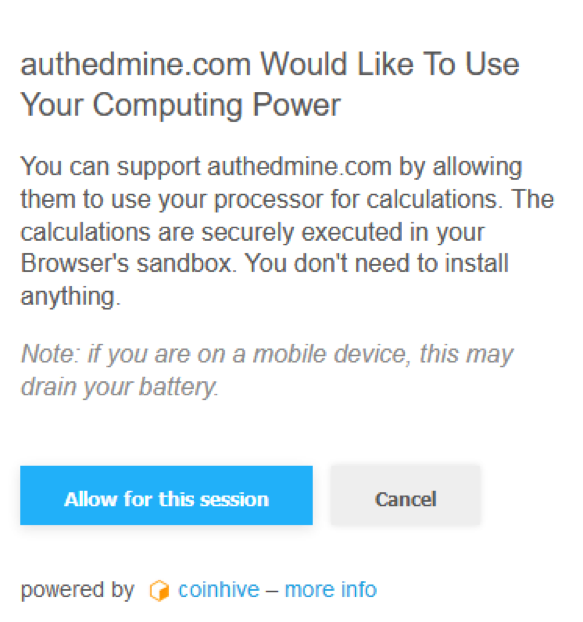
CoinHive maintains that there is no need block their scripts because of “mandatory” opt-ins:
“This miner will only ever run after an explicit opt-in from the user. The miner never starts without this opt-in. We implemented a secure token to enforce this opt-in on our servers. It is not circumventable by any means and we pledge that it will stay this way. The opt-in token is only valid for the current browser session (at max 24 hours) and the current domain. The user will need to opt-in again in the next session or on a different domain. The opt-in notice is hosted on our servers and cannot be changed by website owners. There is no sneaky way to force users into accepting this opt-in.”
For reference, here’s what an opt-in looks like (assuming you ever do see one):
Why Webroot blocks cryptojacking sites
Unfortunately, criminals seem to have found methods to suppress or circumvent the opt-in—the compromised sites we’ve evaluated have never prompted us to accept these terms. Since CoinHive receives a 30% cut of all mining profits, they may not be too concerned with how their scripts are being used (or abused). This is very similar to the pay-per-install wrappers we saw a few years ago that were allegedly intended for legitimate use with user consent, but were easily abused by cybercriminals. Meanwhile, the authors who originated the wrapper code made money according to the number of installs, so the nature of usage—benign or malicious—wasn’t too important to them.
To protect our users from being exploited without their consent, we at Webroot have chosen to block websites that run these scripts. Webroot will also block pages that use scripts from any CoinHive copycats, such as the nearly identical Crypto-Loot service.
There are a few other ways to block these sites. You can use browser extensions like Adblock Plus and add your own filters (see the complete walkthrough here.) If you’re looking for more advanced control, extensions like uMatrix will allow you to pick and choose which scripts, iframes, and ads you want to block.
Update 12/13/17:
CoinHive scripts running rampant
If there was ever any doubt around the severity of this emerging threat and the overall nefarious use of CoinHive’s scripts, it can be put to rest. CoinHive engineers have now essentially admitted that they’ve “invented a whole new breed of malware,” according to a report in the German newspaper Süddeutsche Zeitung.
With the continued price surges in Monero, and the cryptocurrecy market as a whole, it seems cryptojacking becomes a more lucrative opportunity for cybercriminals with each passing day. And recent revelations have shown even more surreptitious methods being used by cryptojacking sites to evade user detection. One website was seen hiding a popup window underneath the Window’s task bar in order to continue mining after users believe they have closed their web browser, according to Bleeping Computer.
CoinHive’s cryptojacking script was even spotted on public WiFi at a Starbucks in Buenos Aires, according to BBC News.
Cyber News Rundown: Edition 12/01/17
The Cyber News Rundown brings you the latest happenings in cyber news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst, and a guy with a passion for all things security. Any questions? Just ask.
US Military Files Found on Publicly Available Server
In the past week, researchers have discovered several publicly available Amazon S3 servers belonging to the US Army and the NSA. Of the numerous sensitive files that were exposed, one was a virtual machine that contained thousands of files, many of which were labeled “Top Secret”, though these were inaccessible without the aid of other internal resources. Along with the virtual machine, researchers also discovered a portion of an outdated cloud computing service used to access the aggregate information on an Army intelligence network, though the program has been out of use since 2014.
Latest MacOS Leaves Root Access Exposed
With the latest iteration of MacOS, dubbed High Sierra, comes an unusual problem: it allows anyone with local access to a machine to log in as a “root” user (which has powerful system permissions) without entering a password. Fortunately for many users, simply adding a root password was a quick method to solve the security issue, though Apple promptly released a patch which provided the fix.
Healthcare Industry Takes Firmer Stance on Security
A new report revealed that most healthcare domains do little to protect their email users, as a staggering 57% of all emails that come from the healthcare industry have been found to be fraudulent. In addition, at least 92% of all healthcare domains have been victims of phishing or scam emails within the past 6 months. Hopefully, with the implementation of stricter security measures, customers can begin to have more trust in the emails they receive from healthcare providers.
Facebook Flaw Allows Polls to Delete Other Users’ Data
Recently, a researcher found a flaw in Facebook’s polling feature that would have allowed him to connect this poll with any other user’s images and subsequently delete the images when he deleted the poll. By finding a workaround to user authentication, he could attach the image ID of any picture that was posted to the site to a Facebook poll he created. Luckily, the researcher quickly contacted Facebook, who have since fixed the flaw and paid a tidy bounty for the find.
Uber Waits Entire Year to Reveal Data Breach
Last week, Uber announced they suffered a data breach in late 2016 that could affect 2.7 million users in the UK. Reportedly, Uber knew of the breach and paid the hackers $100,000 to delete the stolen data and keep quiet. While the breach appears to only contain names, email addresses, and phone numbers, the National Cyber Security Centre (NCSC) encourages all Uber users to change their login credentials immediately, as the full extent of the breach remains unclear. This breach and its handling are yet another strike against the ride-sharing service, after a long year of controversies that have majorly affected their business.
Why You Should Use a VPN on Public WiFi
Working remotely? It only takes a moment on a free WiFi connection for a hacker to access your personal accounts. While complimentary WiFi is convenient, protecting your connection with a VPN is the best way to stay safe on public networks, keeping your data and browsing history secure.
Are you prepared for today’s attacks? Discover the year’s biggest cyber threats with the annual Webroot Threat Report.
What is a VPN?
VPN stands for “virtual private network” and is a technology that can be used to add privacy and security while online. It’s specifically recommended when using public WiFi which is often less secure and is often not password protected.
VPN’s act as a bulletproof vest for your internet connection. In addition to encrypting the data exchanged through that connection, they help safeguard your data and can enable private and anonymous web browsing. However, even if you’re using a VPN, you must still be careful about clicking on suspicious links and downloading files that may infect your computer with a virus. Protecting yourself with antivirus software is still necessary.
When and why should you use a VPN?
When checking into your hotel, connecting to the WiFi is often one of the first things you do once settling in. While it may sound like a tempting offer, logging in to an unsecured connection without a VPN is a very bad idea. In July, ZDNet reported the return of hacker group DarkHotel which aims to target hotel guest’s computers after they have logged on to the building’s WiFi. Once compromising a guest’s WiFi, the hacker group can then leverage a series of phishing and social engineering techniques to infect targeted computers.
Traveling and lodging is just one example of when you can use a VPN to help stay secure and avoid potential attacks, however anyone can benefit from using a VPN.
From checking Facebook on an airport hotspot, accessing your company files while working remotely or using an open network at your local coffee shop, regardless of the scenario, using a public WiFi can potentially put the data you’re sending over the internet at risk. For business looking to secure their guest WiFi, click to learn more about our DNS protection solution.
Ready to take back control of your privacy? Webroot WiFi Security is compatible with devices running iOS®, Android™, macOS® and Windows® operating systems, and is now available to download on the Apple App Store, Google Play™ store, and Webroot.com.

Cyber News Rundown: Edition 11/16/17
The Cyber News Rundown brings you the latest happenings in cyber news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst, and a guy with a passion for all things security. Any more questions? Just ask.
Brothers Printers Vulnerable to Major Exploit
Researchers have discovered an exploit in several Brothers printer models that would allow attackers to issue a continuing DDoS attack against the printer, rendering it unusable. By sending a fraudulent HTTP request to the device, the attackers could then use the printer against itself by forcing a cycle of printer errors, followed swiftly by another phony HTTP request. Although this exploit only affects printer models with a web interface, its discovery sheds light on much more basic security flaws, such as not changing the default password or allowing unrestricted remote access.
Password Hackers Have Reached New Heights
As cybercriminals and their tools get more and more advanced, it’s no surprise that the use of traditional passwords may have finally met its end. Password cracking software has gone from taking years to days to hours to complete, so human-created passwords may now leave many institutions less secure than they could be, and have contributed to numerous data breaches in the last few years.
Ride-Hailing Service Leaves Servers Unsecured
In the least week or so, a server belonging to Fasten, a Boston-based ride-hailing service, was found to be publicly accessible for at least 48 hours; the timeframe may have been longer. The server in question contained personal data for both passengers and drivers, along with data about customer devices and the vehicles used. Fortunately for many users, the company worked quickly to secure the server and improve their data security policies.
Pro-ISIS Hacking Group Targets U.S. School Websites
Recently, the primary websites for at least 800 schools across the U.S. were hacked by a Pro-ISIS group to redirect site visitors to an Arabic YouTube propaganda video. The hacked sites were all linked through an academic website building service called SchoolDesk. SchoolDesk claims no personal information was exposed during the breach, though this news is difficult to confirm. This attack isn’t the worst one perpetrated by the hacking group, but it is the most recent, and the hackers have stated each of their victims has had limited security protocols.
IcedID Banking Trojan Spreads to US
Over the last several days, researchers have been tracking a new banking Trojan that has swiftly spread across the US. IcedID employs both redirection attacks and browser injection, which is fairly unusual. Previously, these tactics have only been combined by Dridex, a highly advanced banking Trojan. By using the botnet built by the Emotet Trojan, IcedID can deploy onto previously infected systems, causing even more damage.
Cyber News Rundown: Edition 11/10/17
The Cyber News Rundown brings you the latest happenings in cyber news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst, and a guy with a passion for all things security. Any more questions? Just ask.
UK-Based Cryptocurrency Hit By Cyberattack
Prior to the official launch of Electroneum, a UK-based cryptocurrency that uses smartphones for its mining process, was targeted by a DDoS attack that shut down both the website and the app for several days. The attack effectively blocked all users from accessing their accounts, as the entire network was forced offline, to ensure the safety of investors’ funds.
Canadian University Held for Ransom
In the past week, officials have been working with affected students to secure their personal information after hackers breached the university’s systems and gained access to student records. The university has since taken its email system offline, as the hackers were spreading the leaked information throughout the email lists. Along with the data circulation, the hackers also demanded the university pay a large ransom of roughly 23,000 USD within 48 hours, though officials are still uncertain when the breach itself occurred.
WaterMiner Cryptocurrency Mod for GTA 5
As more cryptocurrency miners are embedded in software, one Russian hacker has gone a step further by exploiting a mod for the popular game Grand Theft Auto 5. The exploit silently uses a computer’s power to mine digital currency and, with the help of a modified version of the XMRig miner, can hide itself if it suspects monitoring software is active.
Paradise Papers Expose Latest Offshore Dealings
A sizable data dump from offshore law firm Appleby was released and quickly distributed across the globe in the last week. Initial reports reveal that nearly 1.4TB of data was included in the dump, which contained private investment figures belonging to large corporations and prominent political figures. While the perpetrator of the leak has not yet been identified, this event brings to light the unconscionable lack of security that such firms employ, even when dealing with the most sensitive of client data.
Parity Bug Freezes $300 Million in Cryptocurrency
Although the full impact has not yet been quantified, a user bug caused at least 70 Ethereum accounts to completely deactivate, leaving approximately $300 million worth of cryptocurrency completely inaccessible. The bug stems from a recent patch that Parity developers implemented after a previous breach led to the theft of over $30 million in cryptocurrency. At this time, the future of the locked funds is still undecided. Developers are considering a radical change (termed a “hard fork”) to the currency to unlock affected accounts, but this solution isn’t appealing to many investors.
Two-Factor Authentication: Why & How You Should Use it
Conventional wisdom about passwords is shifting, as they are increasingly seen as a less-than-ideal security measure for securing digital accounts. Even the recommended rules for creating strong passwords were recently thrown out the window. Average users are just too unreliable to regularly create secure passwords that are different across all accounts, so using technology to augment this traditional security is imperative.
From online banking to email to cloud-based file storage, much of our high-value information is in danger if a hacker gains access to our most frequently visited sites and accounts. That’s where two-factor authentication comes in.
Two-factor authentication (2FA) adds an extra layer of security to your basic login procedure. When logging into an account, the password is a single factor of authentication, and requiring a second factor to prove you are who you say you are is an added layer of security. Each layer of security that you add, exponentially increases protection from unauthorized access.
Three categories of two-factor authentication:
- Something you know, such as a password.
- Something you have, such as an ID card, or a mobile phone.
- Something you are, a biometric factor such as a fingerprint.
The two factors required should come from two different categories. Often, the second factor after entering a password is a requirement to enter an auto-generated PIN code that has been texted to your mobile phone. This combines two different types of knowledge: something you know (your password) and something you have (your mobile phone to receive a code in SMS text or code from a 2FA app).
Protect accounts with an extra layer of security
Popular social media sites, including Twitter, Facebook, Instagram and Pinterest, have added 2FA to help protect users. In addition, you may have noticed that services from companies such as Apple, Google and Amazon will notify you via email each time you log in from a different device or location.
While 2FA from an SMS text message is popular and much more secure than a password alone, it is one of the weaker types of 2FA. This is because it’s relatively easy for an attacker to gain access to your SMS texts. When you log in to your account and it prompts for a SMS code, the website then sends the code to a service provider and then that goes to your phone.
This is not as secure as everyone thinks, because the phone number is the weakest link in the process. If a criminal wanted to steal your phone number and transfer it to a different SIM card, they would only need to provide an address, the last four digits of your social security number, and maybe a credit card number.
This is exactly the type of data that is leaked in large database breaches, a tactic to which most Americans have fallen victim at some point or another. Once the attacker has changed your phone number to their SIM card, they essentially have your number and receive all your texts, thus compromising the SMS 2FA.
Ready to protect your home setup? Explore and compare Webroot’s home cybersecurity solutions here.
Many people are guilty of using weak passwords or the same login information across several accounts, and if this sounds like you, we recommend that you use authenticator apps such as Google Authenticator and Authy. These apps are widely supported and easy to setup.
Simply go to the “account settings” section on the site you want to enable. There should be an option for 2FA if it is supported. Use the app on your phone to scan the QR code and, just like that, it’s configured to give you easy six-digit encrypted passwords that expire every 30 seconds.
What happens when you’re not using sites that have 2FA enabled? Quite simply, security is not as tight and there’s a higher risk of a hacker gaining access to your accounts. Depending on what is stored, your credit card information, home address, or other sensitive data could be stolen and used to commit fraud or sold on the DarkWeb.
Learn how to enable 2FA on your Webroot SecureAnywhere in our Community Knowledge Base.
Cyber News Rundown: Edition 11/03/17
The Cyber News Rundown brings you the latest happenings in cyber news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst, and a guy with a passion for all things security. Any more questions? Just ask.
DoubleLocker Takes Android Ransomware to Next Level
While the concept of ransomware is nothing new, DoubleLocker takes encryption a step further by not only locking down the device’s files, but also locking the device itself. Once installed, DoubleLocker takes control of the Home button functionality, implementing a randomly generated PIN for the device the first time the user taps Home. This makes it extremely difficult to unlock the device without performing a complete factory reset.
Heathrow Security Documents Found on Lost USB Drive
In the last week, officials at Heathrow Airport in London have been working to determine how a USB drive containing a large quantity of security details about the airport was found on an inconspicuous London street. The USB contained information on the airport’s security measures, as well as details on how the Queen is ushered through the facility. Fortunately, the man who found the drive turned it in to the proper authorities after discovering the data it contained.
Firefox Fights Canvas Fingerprinting
The newest Firefox browser version will take a sterner approach to canvas fingerprinting, a nearly silent method of tracking users’ browsing activity. Canvas fingerprinting tracks the browser instead of storing cookies on the system. Although it has legitimate uses, the canvas element allows companies to track users without their consent. Unlike cookies, fingerprints cannot be deleted by the user. While canvas fingerprinting won’t be going away, Firefox is taking a step in the right direction: their new browser version will give users the choice of opting in, rather than being unwitting subjects.
Mobile Facebook Users Targeted By Phishing Scheme
Recently, Facebook users from continental Europe have seen a sizeable increase in phishing campaigns focused on mobile users. The campaigns start with an already-hacked Facebook account that posts fake “YouTube” links. These links direct anyone who clicks to a fake login page that attempts to steal their credentials. The phished credentials are then used to continue propagating the campaign from the compromised user accounts.
ONI Ransomware Favors Japanese Systems
For the last several months, researchers have been tracking the ONI ransomware variant as it works its way through Japan’s corporate sector. Focusing solely on Japanese companies, ONI and MBR-ONI have been spotted encrypting numerous computers and also wiping others clean, likely in an attempt to cover up other hacking operations. Researchers report the attackers may have used the EternalBlue exploit to move through networks more easily, as the computers involved had not yet received the Microsoft update that would have patched that vulnerability.
Top 10 Nastiest Ransomware Attacks of 2017
We’re revealing the top 10 nastiest ransomware attacks from the past year. NotPetya came in on our list as the most destructive ransomware attack of 2017, followed closely by WannaCry and Locky in the number two and three spots, respectively. NotPetya took number one because of its intent to damage a country’s infrastructure. Unlike most ransomware attacks, NotPetya’s code wasn’t designed to extort money from its victims, but to destroy everything in its path.
While NotPetya and WannaCry were first uncovered in 2017, the other ransomware attacks on our top 10 list made their debuts last year. These attacks either continued into 2017 or returned with a vengeance.
This top 10 list underscores the reality of our increasingly connected world—cybercriminals will continue to develop new infections and will capitalize on reliable, successful attack methods.
To view our Top 10 Nastiest Ransomware infographic, click here.
Not sure how to protect yourself online? Read our safety tips.
Cyber News Rundown: Edition 10/27/17
The Cyber News Rundown brings you the latest happenings in cyber news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst, and a guy with a passion for all things security. Any more questions? Just ask.
Fake Crypto Exchange Apps Found on Google Play Store
After being available on the Google Play store for nearly a month, several phishing apps that were spoofing cryptocurrency exchanges have been removed. Unfortunately, they had been installed up to 5000 unique times by unwitting users. While this isn’t the first time we’ve seen phony crypto exchange apps in an app store, they are becoming more regular, and increasingly difficult to identify.
Reaper Botnet on Track to Be Largest in History
A new botnet called Reaper has been spotted controlling nearly two million unique IoT devices, and is continuing to grow. The infection spreads relatively quietly, like a worm, and uses known vulnerabilities within internet-connected devices to increase its reach. The botnet has yet to be used for any known DDoS attacks, and it appears to be more concerned with growth than high-profile attacks.
Microsoft Office Vulnerability Leaves Users Defenseless
As more and more attention is focused on infections from malicious email attachments, an exploit has been found in a decades-old data exchange system used in all Microsoft Office programs that could allow similar attacks to remain unnoticed. The exploit is based on the data exchange protocols used to send data between Office apps and could be used to trigger malware without user interaction. Unfortunately, Microsoft is unlikely to perform any major patches to resolve the issue, since they could break the data protocols needed by each app.
Customer Info Breach at Major Cosmetics Company
Recently, a security firm found two publicly accessible databases containing sensitive information for nearly 2 million Tarte Cosmetics customers. The data consisted mostly of payment and other sensitive information for any online customers from the last decade, and may have also fallen victim to a ransomware attack during the period that it was unsecured. Fortunately, Tarte was quick to take both databases offline after being informed of the indiscretion.
Bad Rabbit Ransomware Invades Media Outlets
Over the past week, multiple media outlets from Eastern Europe to Japan have been experiencing a ransomware attack, dubbed Bad Rabbit by researchers. The variant shares some of its code with Petya, the ransomware that caused widespread damage earlier this year. Bad Rabbit seems to propagate through fake Flash updates and uses Mimikatz to obtain credentials from infected devices.