Key Insights from the OpenText 2024 Threat Perspective
As we navigate through 2024, the cyber threat landscape continues to evolve, bringing new challenges for both businesses and individual consumers. The latest OpenText Threat Report provides insight into these changes, offering vital insights that help us prepare and protect ourselves against emerging threats. Here’s what you need to know:
The resilience of ransomware
Ransomware remains a formidable adversary, with groups like LockBit demonstrating an uncanny ability to bounce back even after significant law enforcement actions. Despite a recent crackdown that saw authorities dismantle its infrastructure, LockBit swiftly resumed operations, even taunting law enforcement agencies in the process. This adaptability highlights how resourceful ransomware groups have become, enabling them to evade detection and persistently challenge defenders.
For businesses, this means implementing a comprehensive incident response plan that includes secure, immutable backups and regular testing to ensure rapid recovery in the event of an attack. Consumers should also take measures like frequently backing up their data to an external drive or cloud solution. This resilience requires ongoing vigilance and robust security measures for everyone involved.
Malware infections on the rise
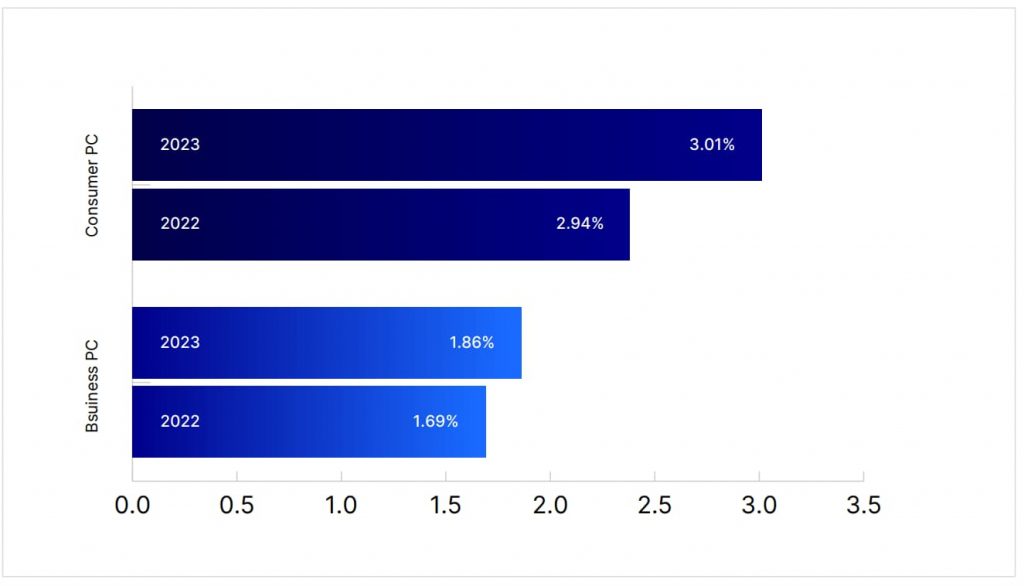
For the first time in years, malware infection rates are rising among both businesses and consumers. The uptick is primarily attributed to attackers leveraging advanced tools like generative artificial intelligence (AI), which helps them craft malware that’s more sophisticated and adaptive. Malware variants are becoming more difficult to detect, and infection methods are increasingly creative, such as using enticing email attachments or redirecting users to malicious sites via QR codes.
This new wave of malware infections serves as a stark reminder for businesses and individuals to strengthen their cyber defenses. Keep all devices updated with the latest security patches, and use reputable antivirus solutions that can block suspicious downloads and identify malicious software. Additionally, be wary of unexpected attachments or links and avoid clicking on anything that looks suspicious.
Phishing gets personal
Phishing attacks are becoming more sophisticated, thanks to tools like generative AI, which enable attackers to personalize their campaigns for maximum impact. What was once a clear distinction between mass phishing emails and more targeted spear-phishing attempts is now blurring, making it harder to distinguish between the two. Attackers can craft convincing emails that mimic legitimate brands, logos, and domains to trick unsuspecting victims into providing sensitive information or clicking malicious links.
For both businesses and consumers, this trend emphasizes the need for increased vigilance and cybersecurity awareness. Educate yourself on common phishing tactics and train employees to recognize fraudulent emails. Multi-factor authentication (MFA) can add a vital layer of protection, and carefully inspect email addresses and links before taking any action.
The critical role of cyber resilience
The report underscores the importance of adopting a multi-layered defense strategy to mitigate the impact of these evolving threats. Cyber resilience involves proactive measures to prevent attacks while also ensuring you can quickly recover if a breach occurs. For businesses, this means implementing strong antivirus software, endpoint protection solutions, and regular software updates. For consumers, being alert to suspicious emails, using secure passwords, and frequently backing up data is crucial.
A multi-layered approach integrates different layers of defense, making it much harder for an attacker to compromise all systems simultaneously. Combine antivirus tools with DNS protection, endpoint monitoring, and user training for comprehensive protection.
Regional disparities in cyber threats
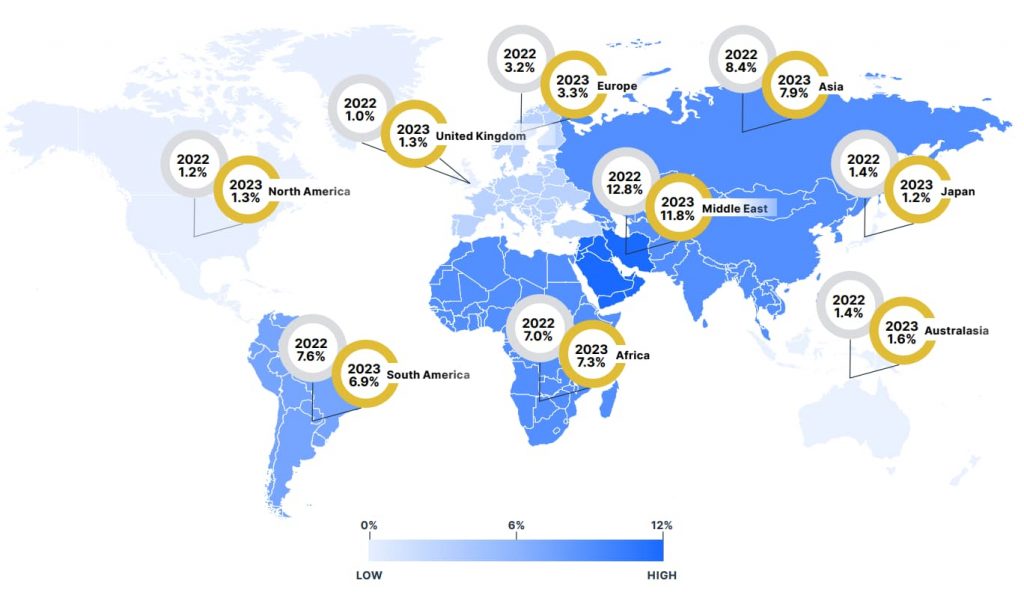
Geographical factors significantly influence the prevalence and nature of cyber threats. The report identifies regions like Asia, Africa, and South America facing higher infection rates than North America and Europe, partly due to differing economic conditions, cybersecurity maturity, and regulatory environments. Malware campaigns are often tailored to exploit regional nuances, such as the availability of local payment methods or common software vulnerabilities.
Businesses operating globally should adapt their cybersecurity strategies to account for these disparities, ensuring protections are tailored to local risks. Similarly, consumers should stay updated on the regional trends to better prepare for prevalent scams and threats in their area.
Industry-specific risks
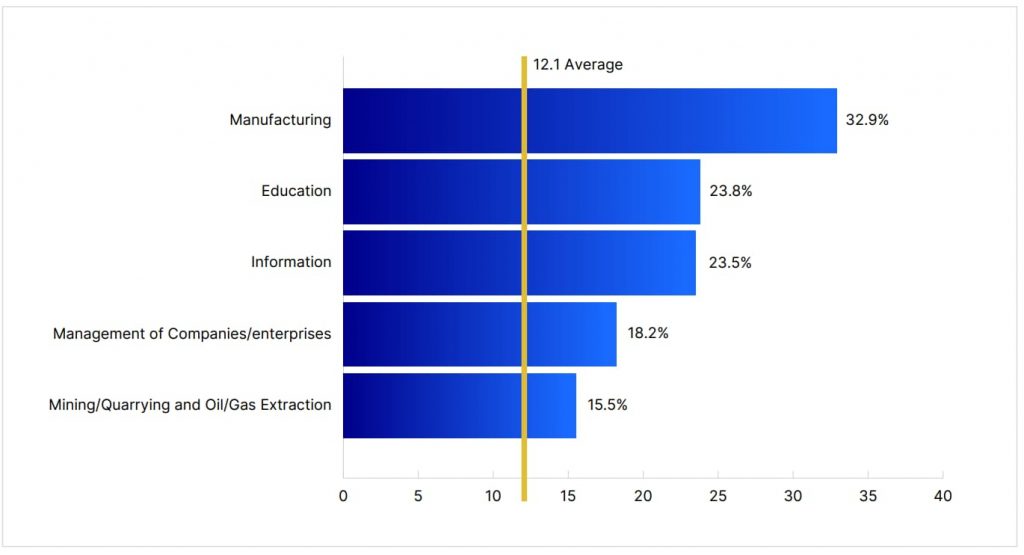
Specific industries like manufacturing, education, and healthcare are frequently targeted due to the valuable data they hold and the potential disruption caused by successful attacks. Manufacturing is particularly vulnerable to ransomware due to the high cost of production stoppages, which can prompt quicker ransom payments. Educational institutions, on the other hand, often have limited cybersecurity budgets, leaving them vulnerable to malware and phishing attacks that can compromise student and faculty data.
While businesses in these industries must enhance their cyber defenses and train staff accordingly, consumers should also be aware of how these attacks could indirectly impact them. For instance, a ransomware attack on a healthcare provider could lead to data breaches exposing patient information.
Recommendations for enhancing cybersecurity
The 2024 OpenText Threat Perspective serves as a crucial resource, offering insights that are essential for both businesses and consumers aiming to navigate the complexities of today’s cyber threat landscape. By understanding these threats and implementing a multi-layered defense strategy, we can significantly enhance our collective cyber resilience.
3 healthcare organizations that are building cyber resilience
From 2018 to 2023, healthcare data breaches have increased by 93 percent. And ransomware attacks have grown by 278 percent over the same period. Healthcare organizations can’t afford to let preventable breaches slip by. Globally, the average cost of a healthcare data breach has reached $10.93 million.
The situation for healthcare organizations may seem bleak. But there is hope. Focus on layering your security posture to focus on threat prevention, protection, and recovery.
Check out three healthcare organizations that are strengthening their cyber resilience with layered security tools.
1. Memorial Hermann balances user experience with encryption
Email encryption keeps sensitive medical data safe and organizations compliant. Unfortunately, providers will skip it if the encryption tool is difficult to use. Memorial Hermann ran into this exact issue.
Juggling compliance requirements with productivity needs, the organization worried about the user experience for email encryption. Webroot™ Email Encryption powered by Zix™ provides the solution. Nearly 75 percent of Memorial Hermann’s encrypted emails go to customers who share Webroot. Now more than 1,750 outside organizations can access encrypted email right from their inbox, with no extra steps or passwords.
2. Allergy, Asthma and Sinus Center safeguards email
The center needed to protect electronic medical records (EMR). But its old software solution required technical oversight that was difficult to manage.
Webroot™ Email Threat Protection by OpenText™ gives the healthcare organization an easy way to keep EMR secure. OpenText’s in-house research team is continually monitoring new and emerging threats to ensure the center’s threat protection is always up to date. With high-quality protection and a low-maintenance design, the IT team can focus on other projects. When patient data is at stake, the center knows it can trust Webroot.
3. Radiology Associates avoid downtime with fast recovery
Radiologists need to read and interpret patient reports so they can quickly share them with doctors. Their patients’ health can’t afford for them to have downtime.
After an unexpected server crash corrupted its database, Radiology Associates needed a way to avoid workflow interruptions. Carbonite™ Recover by OpenText™ helps the organization get back to business quickly in the event of a data breach or natural disaster. Plus, the price of the solution and ease of use gave Radiology Associates good reasons to choose our solution.
Conclusion
As ransomware becomes more sophisticated and data breaches occur more frequently, healthcare organizations must stay vigilant. Strong cyber resilience should be a priority so that you can protect patient privacy and maintain trust within the healthcare industry.
And you don’t have to do it alone. We’re ready to help out as your trusted cybersecurity partner. Together, we can prevent data breaches, protect sensitive data, and help you recover when disaster strikes.
Contact us to learn more about our cybersecurity solutions.
Read more about cyber attacks in the healthcare sector:
The Catastrophic Cyberattack That Shook Healthcare to Its Core
The Change Healthcare Cyberattack: A Wake-Up Call for Healthcare Cybersecurity
5 ways to strengthen healthcare cybersecurity
Ransomware attacks are targeting healthcare organizations more frequently. The number of costly cyberattacks on US hospitals has doubled. So how do you prevent these attacks? Keep reading to learn five ways you can strengthen security at your organization. But first, let’s find out what’s at stake.
Why healthcare needs better cybersecurity
Healthcare organizations are especially vulnerable to data breaches because of how much data they hold. And when a breach happens, it creates financial burdens and affects regulatory compliance. On average, the cost of a healthcare data breach globally is $10.93 million. Noncompliance not only incurs more costs but also hurts patient trust. Once that trust is lost, it’s difficult to regain it, which can impact your business and standing within the industry.
Adopting a layered security approach will help your organization prevent these attacks. Here are five ways to strengthen your cybersecurity:
1. Use preventive security technology
Prevention, as the saying goes, prevention is better than the cure. With the right systems and the right methodology, it’s possible to detect and intercept most cyberthreats before they lead to a data breach, a loss of service, or a deterioration in patient care.
Examples of prevention-layer technologies include:
- Endpoint protection keeps out malicious files, scripts, URLs, and exploits via a cloud-based architecture.
- Email encryption makes it hard for attackers to intercept sensitive medical data—just make sure the encryption tool is easy to manage and use.
- Email threat protection and continuity safeguards electronic medical records by monitoring emerging threats.
2. Provide cybersecurity training
According to Verizon, 82 percent of all breaches involve a human element. Sometimes malicious insiders create security vulnerabilities. Other times, well-intentioned employees fall victim to attacks like phishing, legitimate-looking emails that trick employees into giving attackers their credentials or other sensitive information—like patient data. In fact, 16 percent of breaches start with phishing.
When your employees receive basic cybersecurity training, they are more likely to recognize bad actors, report suspicious activity, and avoid risky behavior. You can outsource cybersecurity training or find an automated security training solution that you manage.
3. Ensure regulatory compliance
Healthcare providers are subject to strict data privacy regulations like HIPPA and GDPR. If an avoidable data breach occurs, organizations face hefty fines from state and federal authorities. The email and endpoint protection tools described above help you stay compliant with these regulations.
But sometimes a breach is out of your control. So regulators have provided guidelines for how to respond, including investigation, notification, and recovery.
4. Build business recovery plans
Adding a recovery plan to your multilayered security approach is crucial to achieving and maintaining cyber resilient healthcare. Ideally, you’ll catch most incoming threats before they become an issue. However, the recovery layer is critical when threats do get through or disasters occur.
You might think that your cloud-based applications back up and secure your data. But SaaS vendors explicitly state that data protection and backup is the customer’s responsibility of the customer. Some SaaS applications have recovery options, but they’re limited and ineffective. A separate backup system is necessary to ensure business continuity.
Reasons for implementing a solid recovery strategy include:
- Re-establishing patient trust.
- Avoiding disruptions to patient care.
- Remaining compliant with HIPPA and GDPR requirements.
Remember, lives depend on getting your systems back up quickly. That’s why your healthcare organization needs a secure, continuously updated backup and recovery solution for local and cloud servers.
5. Monitor and improve continuously
Once you have your multilayered security approach in place, you’ll need a centralized management console to help you monitor and control all your security services. This single-pane-of-glass gives you real-time cyber intelligence and all the tools you need to protect your healthcare organization, your reputation, and your investment in digital transformation. You can also spot gaps in your approach and find ways to improve.
Conclusion
Cybersecurity can seem daunting at times. Just remember that every step you take toward cyber resilience helps you protect patient privacy and maintain your credibility within the healthcare industry.
So when you’re feeling overwhelmed or stuck, remember the five ways you can strengthen your layered cybersecurity approach:
- Use preventive technology like endpoint protection and email encryption.
- Train your employees to recognize malicious activities like phishing.
- Ensure that you’re compliant with HIPPA, GDPR, and any other regulation standards.
- Retrieve your data from breaches with backup and recovery tools.
- Monitor your data and improve your approach when necessary.
Read more about cyber attacks in the healthcare sector:
The Catastrophic Cyberattack That Shook Healthcare to Its Core
The Change Healthcare Cyberattack: A Wake-Up Call for Healthcare Cybersecurity
Protecting your digital identity: Celebrating Identity Management Day
Mark your calendars for April 9, 2024
The second Tuesday of April marks Identity Management Day — a day dedicated to raising awareness about the importance of safeguarding your digital identity. But what exactly is identity management, and why do we need a whole day for it? In a world where our lives are increasingly navigated through digital apps and online accounts, understanding and managing our online identities has become paramount.
What is identity management?
So, what is identity management? Simply put, it’s the practice of ensuring that only authorized individuals have access to your sensitive information and online accounts. This encompasses everything from protecting your passwords to being vigilant against phishing scams and online fraud. But why dedicate an entire day to this? The answer lies in the ever-evolving landscape of cybersecurity threats. Cybercriminals are constantly devising new ways to steal personal information and exploit vulnerabilities in our digital lives. Identity Management Day serves as a reminder that protecting our identities isn’t just a one-time task — it’s an ongoing commitment that requires vigilance and proactive measures all year round.
10 tips to keep your identity safe online
Here are some practical tips to help you keep your identity safe online:
- Get the latest anti-virus software
Investing in reliable anti-virus software is like putting a protective shield around your devices, such as your PCs, Macs, mobile devices, Chromebooks, and tablets. Make sure to keep it updated to guard against the latest threats. - Update your Internet browser
Browser updates often contain security patches that address known vulnerabilities. Don’t ignore those update prompts — they could be the key to keeping your identity and online activities secure. - Create strong passwords and use different ones for each account
This may seem like a hassle, but it’s one of the most effective ways to thwart cyberattacks. Use a combination of letters, numbers, and special characters, and consider using a reputable password manager to securely keep track of them. - Be careful about using public Wi-Fi
Public Wi-Fi networks — hotspots in coffee shops, malls, airports, hotels, and other places — are convenient. But they can also be a breeding ground for hackers. Make sure your connection is encrypted by looking for the padlock symbol or “https” in the address bar to the left of the website address. And avoid accessing sensitive information or making financial transactions while connected to public Wi-Fi. - Use a VPN to browse privately
A virtual private network (VPN) enhances your online privacy and helps keep your identity safe. By encrypting your internet connection and masking your IP address, a good VPN shields your online activities from prying eyes, hackers, and nosy advertisers. - Don’t let your browser remember your login details
While convenient, allowing your browser to remember passwords puts your accounts at risk if your device falls into the wrong hands. Instead, enter your credentials each time for added security. - Learn to spot fake emails and websites
Fake emails like phishing scams are a common tactic used by cybercriminals to trick unsuspecting individuals into divulging sensitive information. Be wary of unsolicited emails or unfamiliar websites, and never click on suspicious links or attachments. For SMBs, fostering a culture where your employees become your strongest security allies is essential. Offer security awareness training to help them recognize and avoid potential threats. - Avoid online fraud and con tricks
If something seems too good to be true, it probably is. Exercise caution when sharing personal or financial information online and be skeptical of offers that promise unrealistic rewards or benefits. You should also be cautious about the personal information you share on social media. Remember, fraudsters can potentially exploit your posts to compromise your identity. Read 7 Cyber Safety Tips for more guidance on how to spot these fake offers.
For small businesses, you’ll want to safeguard your own data and that of your customers. In addition to ensuring that your employees adopt to the above eight tips, here are two important tips for you to advance your company’s identity management efforts:
- Prioritize vulnerability assessments
Conduct regular vulnerability assessments to identify potential weaknesses in your company’s security infrastructure, including endpoints such as your computers, laptops, and mobile devices. By proactively addressing these vulnerabilities and implementing robust endpoint protection and policies, you can significantly reduce the risk of unauthorized access to sensitive information. - Get to know what data you have, what’s sensitive, and protect it
Understanding the types of data your business collects, stores, and processes is essential for effective identity management. Identify sensitive information such as customer payment details or personal identifiers and implement appropriate safeguards to protect it from unauthorized access or misuse. Doing so is a sound business practice and also aids in meeting regulatory standards, if applicable to your business.
By staying informed, adopting best practices, and leveraging available resources, we can all play a part in creating a safer online environment for ourselves and others.
For those looking for additional support in managing their digital identities, consider exploring reputable cybersecurity solutions such as Webroot, which offers a range of products designed to keep your information secure. You can also check out the National Cybersecurity Alliance for ways you can get involved in Identity Management Day. Remember, protecting your identity is not just a one-day affair — it’s a continuous effort that requires diligence and awareness.
Understanding brute force attacks: The persistent threat in cybersecurity
Brute force attacks illustrate how persistence can pay off. Unfortunately, in this context, it’s for bad actors. Let’s dive into the mechanics of brute force attacks, unraveling their methodology, and focusing on their application. Whether it’s Remote Desktop Protocol (RDP), or direct finance theft, brute force attacks are a prime tactic in the current cybersecurity landscape.
What is a brute force attack?
A brute force attack is a cyber attack where the attacker attempts to gain unauthorized access to a system or data by systematically trying every possible combination of passwords or keys. This method relies on the sheer power of repetition and the computational capacity to try thousands, if not millions, of combinations in a short time span. Think of it as trying every key on a keyring until finding the one that unlocks a door.
Types of brute force attacks
- Simple brute force attacks: This basic approach involves trying all possible combinations of characters until the correct one is found.
- Dictionary attacks: A more refined method that uses a list of pre-existing passwords, phrases, or commonly used combinations instead of random permutations. There are many already leaked password lists that are commonly used, and they grow after every breach.
- Hybrid attacks: Combining elements of both the simple and dictionary approaches, often tweaking common passwords slightly to guess more complex passwords.
The role of GPUs in brute force attacks
Graphic Processing Units (GPUs) have revolutionized not just gaming and graphic design, but also the world of cybersecurity. Their powerful parallel processing capabilities make them particularly adept at handling the computational demands of brute force attacks. Unlike Central Processing Units (CPUs) that process tasks sequentially, GPUs can perform thousands of operations simultaneously, drastically reducing the time required to crack passwords or encryption keys.
Accelerating brute borce techniques
Cybercriminals exploit GPUs to accelerate the brute force process, enabling them to try billions of password combinations in seconds. This brute force capability poses a significant threat to systems protected by weak or commonly used passwords. It underscores the necessity for robust password policies and advanced security measures like Multi-Factor Authentication (MFA) and encryption methods resilient against GPU-powered attacks.
Financial applications of brute force attacks
The financial implications of brute force attacks can be profound, ranging from direct financial theft to substantial reputational damage leading to loss of business.
Direct Financial Theft
In some cases, attackers aim to gain unauthorized access to financial systems or payment platforms. By cracking login credentials through brute force, they can transfer funds, manipulate transactions, or steal sensitive financial information, leading to direct monetary losses.
The role of RDP in brute force attacks
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft that allows a user to connect to another computer over a network connection with a graphical interface. While RDP is a powerful tool for remote administration and support, it has also become a favored vector for brute force attacks for several reasons:
- Widespread use: RDP is commonly used in businesses to enable remote work and system administration.
- Open ports: RDP typically requires port 3389 to be open, making it a visible entry point for attackers scanning for vulnerabilities.
- Direct access: Successfully breaching an RDP session can give attackers direct control over a victim’s computer, allowing for the deployment of malware, ransomware, or theft of sensitive information.
Real-world examples of brute force attacks via RDP
- Ransomware deployment: One of the most nefarious uses of brute force attacks on RDP is for the deployment of ransomware. Once access is gained, attackers can encrypt the victim’s files, demanding a ransom for their release. The WannaCry and Ryuk ransomware attacks are notable examples where such tactics were likely utilized.
- Credential stuffing: In some cases, attackers use brute force tactics to validate stolen username and password combinations against accessible RDP servers. This method relies on the assumption that many users reuse their credentials across different services.
- Network infiltration: Upon gaining access via RDP, cybercriminals can use the compromised system as a foothold to explore and exploit further vulnerabilities within a network, aiming for more valuable data or systems.
Mitigating the Risk
Protecting against brute force attacks, especially on RDP, involves a multi-faceted approach:
- Strong password policies: Enforce complex, unique passwords and consider the use of multi-factor authentication (MFA) to add an extra layer of security.
- Account lockout policies: Implement policies that lock user accounts after a certain number of failed login attempts to hinder brute force efforts.
- Network level authentication (NLA): NLA requires users to authenticate before establishing an RDP session, significantly reducing the risk of brute force attacks.
- VPN usage: Restrict RDP access to users connected through a Virtual Private Network (VPN), reducing the exposure of RDP to the open internet.
- Monitoring and alerts: Use security tools to monitor for repeated failed login attempts and configure alerts to notify administrators of potential brute force activities.
The Marvels and Challenges of AI
Let’s delve into the fascinating world of Artificial intelligence (AI), unpacking its concepts, implications, and real-world applications. Brace yourself for an extended journey through the marvels and challenges of artificial intelligence.
Part 1: Unleashing marvels in our digital lives
Generative AI and chatbots
AI has transcended its sci-fi origins to become an integral part of our daily existence. Let’s explore both the light and the dark sides of this transformative force.
1. Generative AI: fueling creativity
Generative AI is a subset of AI, empowering machines to create human-like content. These models learn patterns from vast amounts of data and then generate new, original content.
Here are just some of the ways they’re shaping our world.
A. Text generation
Generative models like OpenAI’s GPT-3 have garnered attention with their creative prowess. Imagine a poet AI composing thought-provoking verses or an author AI writing entire novels. These algorithms analyze existing text and generate coherent, context-aware responses. From automated customer service chats to personalized email drafts, generative text models enhance efficiency and convenience.
Example:
Chatbot: “Dear John, I hope this email finds you well. I wanted to discuss the upcoming project deadline. Could we possibly extend it by a week? Your prompt response would be greatly appreciated.”
B. Art and music creation
Beyond text, generative AI ventures into the realms of art and music. AI artists create digital works, mimicking famous styles or inventing entirely new ones. Music composition algorithms generate enchanting melodies, experimenting with genres and instruments. The fusion of human creativity and machine learning opens up uncharted creative territories.
Examples:
Art AI: “Behold ‘digital Impressionism’—a canvas painted by an algorithm. Inspired by Monet, it captures the play of light on water, blending pixels into ethereal strokes.”
Sora: An AI model that can create realistic and imaginative scenes from text instructions, Sora allows users to create short videos based on simple text prompts.
2. Chatbots: Your digital companions
Chatbots, such as the renowned ChatGPT, engage in natural conversations with users. They’re not mere rule-based question-answer systems; they understand context, learn from interactions, and adapt their responses.
Here’s how chatbots are transforming our lives:
A. Virtual assistants
Chatbots act as tireless virtual assistants, handling tasks like setting reminders, booking appointments, and providing weather updates. They’re available 24/7, ensuring productivity and convenience.
Example:
User: “Hey chatbot, remind me to buy groceries tomorrow.” Chatbot: “Certainly! I’ll set a reminder for tomorrow at 10:00 am.”
B. Customer support
In the business world, chatbots assist customers round the clock. They resolve queries, guide users through troubleshooting steps, and even process transactions. Their efficiency reduces wait times and improves customer satisfaction.
Example:
Customer: “My order hasn’t arrived yet. Can you check its status?” Chatbot: “I apologize for the delay. Let me track your order. It should arrive by Friday.”
C. Virtual partners / AI romance
AI has developed beyond the simple “swipe right/left” paradigm of modern dating apps and now even eclipsed the human-machine relationship depicted in the Spike Jonze movie, Her (2013). Loosely based on and extrapolated from chatbots such as Apple’s Siri or Google’s Alexa, Scarlett Johannsen’s character interacts with the man played by Joaquim Phoenix in ways that were not truly possible at the time.
Example:
Today, apps like Candy.ai promise users “realistic yet fantasy-fueled relationships” using advanced artificial intelligence technology to create the ideal AI girl/boyfriend according to the user’s preferences.
D. Content creation
Chatbots can compose emails, articles, and reports. Imagine a chatbot helping you draft that important client email or summarizing a lengthy document. As they learn from user interactions, their writing style adapts, making them valuable co-authors.
Example:
Chatbot: “Here’s a concise summary of the quarterly report. Key takeaways: revenue growth, cost optimization, and increased customer engagement.”
Medical breakthroughs and personalization
1. AI in healthcare
A. Diagnosis and prediction
AI analyzes medical data, aiding in disease diagnosis and predicting patient outcomes. Imagine an AI-powered system detecting early signs of cancer or suggesting personalized treatment plans based on genetic profiles. Precision medicine becomes a reality, optimizing recovery and minimizing side effects.
Example:
AI system: “Based on your genomic markers, we recommend a tailored treatment plan for your rheumatoid arthritis, including targeted therapies and lifestyle adjustments.”
B. Drug discovery
AI accelerates drug discovery by sifting through vast chemical databases. It identifies potential candidates, predicts their efficacy, and expedites research. These breakthroughs hold the promise of saving lives and improving global health.
Example:
Researcher: “Our AI model identified a novel compound with anti-viral properties. Let’s test it in vitro.”
4. Personalization algorithms
AI algorithms can personalize our experiences across platforms in several ways, here are two we encounter in our daily lives:
A. Lifestyle recommendations
From Netflix to social media, AI analyzes our preferences and behavior. It recommends movies, articles, and products tailored to our tastes. Imagine a world where your news feed aligns perfectly with your interests, introducing you to relevant content. But this is only the tip of the iceberg.
When AI is combined with big data and personal data (gleaned from biometric sensors in wearable devices—the step counter in the Apple Watch or iPhone being one of the simplest examples) it can recommend diet and health options, tailor optimal workouts, create psychological profiles, even help users explore career choices, assist with dating and partner match recommendations, and so much more.
Example:
Smart watch: “Based on your height, weight, BMI, and fitness level, here is a diet and exercise regime designed to help you achieve your fitness goals.”
B. Targeted advertising
E-commerce platforms use AI to display ads relevant to individual users. These algorithms consider browsing history, demographics, and purchase behavior. While sometimes controversial, personalized ads can enhance user engagement and drive sales—especially when they get their timing and targeting right!
Example:
Online retailer: “Looking for running shoes? Check out our latest collection!”
Transforming industries
1. Finance, manufacturing, and logistics
A. Process automation
AI streamlines repetitive tasks, reducing human error. In finance, algorithms handle stock trading, fraud detection, and credit risk assessment. In manufacturing, robots assemble products with precision. Logistics companies optimize routes and delivery schedules, minimizing costs.
Example:
Algorithm: “Sell 100 shares of XYZ stock if it drops below $50. Execute.”
B. Data-driven decisions
AI analyzes vast data sets, providing insights for strategic decisions. Manufacturers optimize supply chains, predicting demand fluctuations. Financial institutions assess investment risks, adapting to market dynamics. Data-driven decision-making becomes the norm.
Example:
Supply chain manager: “Our AI model recommends adjusting inventory levels based on seasonal trends. Let’s implement it.”
2. Smart cities
A. Traffic management
AI monitors traffic flow, adjusts signal timings, and predicts congestion. Smart cities optimize transportation networks, reducing commute times and environmental impact.
Soon, self-driving cars equipped with advanced AI will communicate with each other to optimize traffic flow, adjusting speeds, merging seamlessly, and avoiding bottlenecks. In this future network, vehicles cooperatively navigate intersections without the need for traffic lights or stop signs.
Road accidents caused by human error are set to become a thing of the past. Self-driving cars, relying on sensors, cameras, and AI algorithms, react faster and more accurately than humans. Unlike humans, algorithms don’t get distracted, fatigued, or impaired which drastically reduces accidents.
In this AI EV future, our roads will transform into safer, more efficient spaces, where traffic snarls and collisions are relegated to history.
Example:
Traffic control center: “Route traffic away from downtown during rush hour. Optimize traffic light cycles for smoother flow.”
B. Energy efficiency
Smart grids balance energy supply and demand, minimizing wastage. AI algorithms predict peak usage hours, ensuring efficient distribution. Renewable energy sources integrate seamlessly into the grid.
Example:
Smart meter: “Solar panels are generating excess energy. Divert it to the grid or store it in batteries?”
C. Waste management
AI helps optimize waste collection routes, reducing landfill overflow. Sensors can be used to detect fill levels, alerting sanitation crews when bins need emptying. These and other innovations are helping us build cleaner, more sustainable cities.
Example:
Garbage truck dispatcher: “Route adjustment: prioritize areas with overflowing bins.”
Part 2: AI and the need for vigilance in our digital lives
The rise of AI scams
1. Deepfakes: Deception in high definition
The rapid ascent of generative AI has sparked both fascination and apprehension. Deepfakes, a byproduct of this technology, represent the downside of its dual nature. These hyper-realistic manipulations allow cybercriminals to impersonate trustworthy figures, including celebrities, politicians, and even family members. Here’s how deepfakes impact our digital landscape:
A. Impersonation of trustworthy figures:
Cybercriminals exploit deepfakes to create eerily accurate impersonations. Imagine receiving a phone call from a seemingly genuine bank manager, requesting sensitive account details for “security verification.” What the victim doesn’t know is they’re interacting with an AI-generated persona. Financial losses and reputational damage follow. Victims trust these deceptive voices, unaware of the illusion.
Example:
Deepfake Voice: “Hello, this is your bank manager. We need your account details for security verification.”
Or : “Hey Granny, could you please transfer me some money? I need to buy a new computer for school?”
B. Luring victims into fraudulent schemes:
Scammers craft persuasive narratives using deepfakes. These narratives promise quick riches, job opportunities, or romantic connections. Victims, enticed by the illusion, fall prey to these schemes.
The line between reality and deception blurs, leaving individuals vulnerable to financial exploitation.
Example:
Scammer: “Invest in this AI-powered cryptocurrency—watch this celebrity testimonial!”
Deepfakes challenge our ability to discern truth from fiction, emphasizing the need for vigilance and awareness in an AI-driven world.
Example 2:
In February 2024, an unsuspecting finance worker, attending an online meeting, interacted with entirely AI-fabricated colleagues who convinced him to confirm a false transaction resulting in a staggering $25 million loss for the company.
Algorithmic bias and privacy violations
1. Discrimination amplified
AI algorithms inherit biases from their training data. Unfortunately, facial recognition systems often misidentify people of color due to skewed data sets. These errors perpetuate societal prejudices, leading to real-world consequences.
Imagine being denied access or services because an AI system fails to verify your identity correctly.
Example:
Facial recognition system: “Sorry, we cannot verify your identity. Please try again.”
2. The erosion of privacy
AI’s insatiable appetite for personal information raises ethical concerns. Algorithms analyze sensitive data without explicit consent, eroding privacy boundaries.
Our digital identities hang in the balance as AI-driven ad targeting systems comb through browsing histories, serving personalized ads. Imagine receiving tailored advertisements based on your most intimate online activities.
Example:
AI ad targeting: “Based on your browsing history, here are personalized ads just for you!”
As we navigate the AI landscape, addressing bias and safeguarding privacy become critical imperatives.
The strange life of chatbots
1. Emotional connections with machines
As we forge connections with AI, we grapple with the paradox of intimacy and artifice. Chatbots straddle the line between utility and emotional impact. Users can form genuine bonds with these AI companions, despite their artificial nature.
While AI dating sites and chatbots as virtual companions offer convenience and novelty, there are significant downsides to consider. In our quest for digital companionship, we risk losing genuine human connections. AI chatbots lack empathy, intuition, and the emotional depth that only real-life interactions provide.
Virtual boyfriends and girlfriends shield us from the complexities of real-world relationships, which can involve disagreements, struggle, and the need for compromise. By opting for AI companions, we miss out on the growth that comes from navigating challenges together.
Another AI chatbot drawback is a tendency to reinforce traditional gender roles. Female-voiced assistants often play subservient roles, perpetuating stereotypes, and reinforcing negative perceptions of gender dynamics in real life. Additionally, there have been cases of AI chatbots behaving inappropriately, including sexual harassment.
2. Disinformation and national security
Deepfakes, a menacing offspring of AI, pose significant threats to society. These hyper-realistic manipulations undermine election outcomes, social stability, and national security.
By manipulating public opinion or spreading fabricated news, deepfakes create distrust and confusion. Educating the public about their existence and potential impact is crucial.
Example:
Disinformation campaign: “Watch this video showing how Candidate X was caught in a scandal—spread the word!”
Human psychology and confirmation bias—the tendency to seek out and prefer information that supports our preexisting beliefs—which is already amplified by social media, becomes even more dangerous when powered by AI and fake content.
This process of actively looking for evidence that aligns with what we already think or know, while ignoring or dismissing information that contradicts our beliefs, is arguably helping to fuel some of the divisions we are seeing in democratic society today.
Balancing marvels and vigilance
Moving forward, it is essential that we understand the nuances of AI. Its marvels are reshaping our world, but vigilance is crucial. As we embrace the innovations, we must also safeguard against the dark shadows of deepfakes and misinformation. We must navigate this evolving landscape with curiosity, responsibility, and a commitment to ethical AI.
What can I do at my level?
Embrace technology’s benefits but be aware of the pitfalls. Here’s how to protect yourself and your loved ones:
Exercise Judgment and Due Diligence:
- Question what you encounter online.
- Verify information before sharing or acting upon it.
Fortify Your Digital Armor:
- Use security software, VPNs, strong passwords, and two-factor authentication.
- Regularly update your software.
Mind Your Digital Footprints:
- Be mindful of what you share online.
- Adjust privacy settings and periodically review your digital footprint.
Remember, common sense is your secret weapon against misinformation and AI-driven threats.
7 cyber safety tips to outsmart scammers
Welcome to the wild west of the digital world where cyber scammers lurk around every pixelated corner. Cybercrime isn’t just a futuristic Hollywood plotline, it’s a real threat that targets everyone—from wide-eyed kids to seasoned adults and wise grandparents.
And guess what? It’s on the rise faster than your Wi-Fi connection during peak hours (okay, maybe not that fast, but you get the gist). So, hoist the sails as we cruise through the seven seas of cyber safety.
Identifying scams
Before we dive headfirst into the cyber safety tips, let’s equip ourselves with the ultimate weapon: knowledge. Scams are the digital equivalent of a snake oil salesperson peddling miracle cures. They come in all shapes and sizes, lurking in the shadowy corners of the internet.
Let’s embrace the golden rule of scam detection: skepticism.
Whether it’s a promise of untold riches, a once-in-a-lifetime opportunity, or a free Caribbean cruise courtesy of a Nigerian prince, approach with caution and a healthy dose of skepticism.
Now, let’s take a quick tour through the terrain of common cyber scams:
- Phishing scams
Ah, phishing scams, the bane of our digital existence. These sneaky scams involve fake emails posing as messages from familiar faces or reputable companies. They’ll try to sweet-talk you into clicking on suspicious links or divulging sensitive information like passwords or credit card details. Remember: real companies don’t ask for your personal data via email. - Sweepstakes and awards scams
Congratulations! You’ve just won a brand new car, a tropical vacation, and a lifetime supply of unicorn-shaped cookies—all you need to do is pay a small processing fee. Sound too good to be true? That’s because it is! These scams offer you instant wealth but are really just clever ruses to empty your wallet faster than you can say “jackpot.” - Investment scams
Picture this: a golden opportunity to double your money with zero risk. Investment scams lure unsuspecting victims with the promise of sky-high profits. Don’t let these offers cloud your judgment. Always do your due diligence before investing your hard-earned cash. - Lawsuit or tax scams
Lawsuit and tax scams thrive on instilling fear and panic, claiming you owe urgent payments. When in doubt, verify the legitimacy of any claims before reaching for your wallet. - Romance scams
Romance scams prey on the trusting hearts of hopeful romantics, weaving elaborate tales of love and devotion before swooping in for the financial kill. Remember: anyone who asks for money online is more likely to break your heart than mend it. - Tech support scams
These imposters offer remote assistance to fix nonexistent problems with your laptop or devices while gaining access to your sensitive data. Remember: legitimate tech support doesn’t come knocking unsolicited. If in doubt, just delete the email and seek help from trusted sources.
Equipped with this knowledge, you’re ready to navigate the digital minefield with confidence. You can also be a good internet citizen by forwarding these scams to the U.S. government’s Cybersecurity & Infrastructure Security Agency (CISA) at phishing-report@us-cert.gov.
Your 7 tips to stay safe online
- Use strong passwords
Let’s kick things off with the basics. Your password is the digital key to your castle, so make sure it’s not something as flimsy as ‘123456’ or ‘password.’ Get creative! Mix uppercase, lowercase, numbers, and special characters like a mad scientist concocting a secret potion. And don’t reuse passwords across multiple accounts unless you want to throw a welcome party for cybercriminals. - Keep your devices updated
Newsflash: Cybercriminals love exploiting vulnerabilities in outdated software like it’s Black Friday at the cybercrime emporium. Stay one step ahead by keeping your devices and applications updated. Those pesky software updates aren’t just about adding a new emoji, they often contain vital updates to fix security issues. - Lockdown your privacy settings
Your online profiles are like open books to cyber snoops unless you lock them down. Take a few minutes to review and adjust your privacy settings on platforms like Facebook, Instagram, and YouTube. Limit who can see your posts, tag you in photos, or slide into your DMs without an invitation. - Safeguard your privacy with a trustworthy VPN
In the digital-verse, protecting your online privacy is paramount, like guarding the secret recipe to your grandma’s famous carrot cake. That’s where a virtual private network (VPN) swoops in like a digital superhero to save the day. By encrypting your internet connection and masking your IP address, a good VPN shields your online activities from prying eyes, hackers, and nosy advertisers. - Use two-factor authentication
Two-factor authentication (2FA) adds an extra layer of security for your account logins by having you not only enter your password but also provide a second form of verification, such as a one-time code texted to your phone. It’s like having two bouncers screening out any shady characters trying to hack into your accounts. - Backup your data
Picture this nightmare scenario: Your laptop is suddenly hijacked by a malware infection or a ransomware attack encrypting all your files and holding them hostage. But fear not! By regularly backing up your data to the cloud or an external hard drive, you can rest easy knowing that your digital treasures are safe and sound. - Safeguard your loved ones
Internet scams can be devastatingly effective when targeting vulnerable groups such as the elderly, children, or those less tech savvy. So it’s crucial to designate someone as the cybersecurity leader within your family. One of your top priorities should be to ensure that everyone’s devices are equipped with robust identity protection and antivirus software. Think of it as fortifying your digital fortress, shielding your loved ones from the threats lurking in the internet world.
Congratulations, you’ve just leveled up your digital defense game! By implementing these seven cyber safety tips, you can protect yourself and your loved ones from cyber scammers. Stay safe out there!
| Need help deciding which Webroot product is right for you? Take our short quiz to discover the ideal plan for safeguarding your devices, privacy, and identity—whether it’s for you or your entire family. |
9 tips to protect your family against identity theft and credit and bank fraud
Did you know that more than nine million Americans have their identity stolen each year?
Your data is stored across countless databases for various purposes, making it a prime target for criminals. With access to your personal information, bad actors can drain your bank account and damage your credit—or worse.
But that doesn’t mean you and your family have to become victims. By taking the right steps, you and your loved ones can enjoy the peace of mind that comes from identity protection.
Check out the nine tips below to discover how you can enable family protection and help prevent identity theft and credit and bank fraud.
1. Be protective of your personal information
If criminals get ahold of your personal information—such as your name, address, date of birth, and social security number—they can use it to commit identity theft. This can impact your credit score, your savings, and your reputation—or even result in criminal records. Protect yourself by shredding documents with any personal information, and, when possible, avoid sharing this information over the phone or via email.
2. Use strong and unique passwords
Passwords are your first line of defense to protecting your online accounts from hackers. That’s why your passwords should be strong: at least eight characters long with a combination of uppercase and lowercase letters, numbers, and symbols.
But it’s just as important you don’t use the same password for multiple accounts. If you’ve been compromised in a data breach, hackers can use your stolen email and password to try and enter thousands of other sites—and if you keep using the same credentials, they’ll be successful.
Instead, use a password manager to easily generate and use strong passwords without having to recall them all. They’ll be stored in a secure vault, so you only need to remember the main password to the password manager app.
3. Monitor your accounts regularly
Detect unauthorized transactions early by regularly checking your bank and credit card statements. If you notice any unauthorized transactions, immediately report them to your bank or credit card company.
4. Be wary of phishing scams
Many criminals will send emails or text messages that appear to be from a legitimate source, like your bank or credit card company. Known as phishing scams, these messages will typically ask you to provide personal information or click on a malicious link. To avoid falling victim, always double-check the source of any message and never click on links or provide personal information unless you’re certain the message is legitimate.
5. Use two-factor authentication
Two-factor authentication adds an extra layer of security to your online accounts. With two-factor authentication, you’ll need to provide a second form of identification—such as a code sent to your phone—in addition to your password. Even if your account information is compromised, bad actors won’t be able to access your account without this secondary identification.
6. Secure your devices and connections
Without the right precautions, your computers, smartphone, and other devices can be easily hacked or compromised. To secure them, make sure your devices are up to date with antivirus software and are password-protected. Avoid using public Wi-Fi to access sensitive information—as these networks are often unsecured—or use a VPN to hide your identity and stay anonymous.
7. Keep an eye on your credit reports
Did you know you’re entitled to a free credit report once a year from each of the three major credit bureaus? Check your credit report regularly to help detect any suspicious activity, such as accounts you didn’t open or loans that you didn’t apply for. You can also use a reputable credit monitoring service—which often includes SSN monitoring—for real-time alerts and protection.
8. Stay on top of the latest scams (especially with the rise of AI)
Criminals are adopting new AI-powered scam tactics as the technology becomes more accessible. For example, it’s now possible to impersonate a friend or family member, even over the phone or by a video call. Keep informed of the latest scam techniques by following reputable cybersecurity experts and checking reputable news outlets. Because new tactics can pop up faster than they can be reported, be extra vigilant—be wary of unsolicited emails and messages and always verify a person’s identity before you share personal information.
9. Get your family covered with an identity protection package
For the best identity protection, you should invest in a comprehensive protection plan. Webroot™ Premium with Allstate™ Identity Protection, for example, includes:
- Protection against viruses, malware, scams, and other cyber threats.
- Password management to keep your credentials safe.
- Protection for 10 family members, including you and your partner, your children, and seniors aged 65+ you wish to protect.
- Identity, credit, and financial accounts monitoring and alerts if potential fraud is detected.
- Advanced dark web monitoring that notifies you if your personal data is found in a data breach or your credentials are compromised.
- 24/7 US-based support with remediation experts that help you restore your stolen identity or mitigate fraud on your accounts.
- Up to $1M reimbursement1 for:
- Fraud expenses like out-of-pocket costs associated with identity restoration, including legal fees, lost wages, child or elderly care, replacement of identification cards, driver licenses, and passports.
- Stolen funds in case identity fraud led to fraud on your saving accounts—including up to $150,000 for 401 (k)/HSA.
Get family protection today
To protect yourself and your family against identity theft and bank fraud, you need to be vigilant and commit to good security practices. By following the nine tips, you can help reduce your likelihood of becoming a victim and safeguard your personal and financial information.
Do you want to make identity protection even easier?
| Need help deciding which Webroot product is right for you? Take our short quiz to discover the ideal plan for safeguarding your devices, privacy, and identity—whether it’s for you or your entire family. |
1Identity theft insurance covering expense and stolen funds reimbursement is underwritten by American Bankers Insurance Company of Florida, an Assurant company. The description herein is a summary and intended for informational purposes only and does not include all terms, conditions, and exclusions of the policies described. Please refer to the actual policies for terms, conditions, and exclusions of coverage. Coverage may not be available in all jurisdictions. Product may be updated or modified. Certain features require additional activation. The aggregate limit for an individual or family plan is $1,000,000 in one year.
Navigating the Web of Romance Scams: A Guide for Businesses and Consumers
In the digital age, the quest for love has moved online, but so have the fraudsters, with romance scams reaching record highs. These scams don’t just harm individuals financially and emotionally; they can also pose significant risks to businesses. Let’s explore how these scams work, their impact, and how both businesses and consumers can protect themselves.
Understanding Romance Scams
Romance scams involve fraudsters creating fake profiles on dating sites, social media platforms, or apps to establish relationships with victims, gain their trust, and eventually, scam them out of money. In 2022, nearly 70,000 people reported such scams, with losses totaling a staggering $1.3 billion. The median loss per victim was around $4,400, highlighting the severe impact on individuals.
Key Trends to Watch
The reported losses to romance scams were up nearly 80% year over year, showing a rapid increase in both the frequency and effectiveness of these scams. This trend underscores the evolving threat landscape and the importance of continuous awareness and education on cybersecurity threats, including those that initially appear to be personal in nature.
- Rise in Cryptocurrency Payments: Fraudsters are increasingly asking for payments in cryptocurrency, exploiting its semi-anonymous nature. In 2021, losses to romance scams involving cryptocurrency were reported at $139 million. Expect this to avenue of fraud to consistently escalate as crypto prices and adoption increase.
- Social Media as a Starting Point: Around 40% of romance scam victims in 2022 reported that the scam started on social media, a significant increase that highlights the broadening tactics of scammers.
- Increased Use of Gift Cards: Despite the high losses associated with cryptocurrency, gift cards remain a preferred method for scammers, given their ease of use and difficulty in tracing.
The Business Angle
When employees fall victim to these scams, the emotional and financial distress can lead to decreased productivity and increased susceptibility to further scams, including those targeting the workplace. Fraudsters may use personal relationships to extract sensitive information or gain access to company networks. Thus, an employee compromised by a romance scam can inadvertently become a weak link in the company’s cybersecurity defenses.
How Romance Scams Affect the Workplace
- Distraction and Distress: Victims of romance scams often experience significant emotional and financial distress. This state of mind can lead to increased susceptibility to other types of scams or malicious attacks. When employees are distracted or stressed, they’re more likely to make mistakes, such as inadvertently clicking on phishing links or downloading malicious attachments.
- Credential Compromise: In some cases, romance scammers may directly target individuals to gain access to their professional credentials. A seemingly innocuous request for information from a “trusted” romantic partner could actually be a ploy to infiltrate company networks.
- First Line of Defense: Employees are often considered the first line of defense against cyber threats. When their judgment is clouded by personal issues, such as those stemming from a romance scam, this line of defense can weaken, exposing the organization to increased risk.
Protecting Yourself and Your Business
- Educate and Train Employees: Awareness is the first step in prevention. Businesses should include the risks of social engineering scams, like romance scams, in their cybersecurity training programs, highlighting how personal security practices impact professional security.
- Encourage Open Communication: Create an environment where employees can report personal security breaches without fear of judgment. This transparency can be crucial in preventing security risks to the business.
- Encourage Healthy Skepticism: Teach employees to question unexpected requests for information or money, whether from strangers, online acquaintances, or even romantic partners they have not met in person.
- Regular Security Assessments: Continuously evaluate and improve security practices to safeguard against evolving threats. This includes ensuring that personal devices used for work purposes are also secure.
- Monitor Financial Transactions: Look out for unusual financial requests or transactions, especially those involving cryptocurrency or gift cards.
- Verify and Validate: Encourage employees to verify the identities of individuals they interact with online and to use reverse image searches to check the authenticity of profile pictures.
Romance scams are a multifaceted problem with both personal and professional ramifications. By staying informed, fostering open communication, and implementing robust security measures, businesses and consumers alike can better protect themselves from these emotionally and financially devastating schemes. Remember, cybersecurity is not just about technology; it’s about understanding human behavior and the various ways it can be manipulated.
For more detailed information on how to protect yourself from romance scams, visit the Federal Trade Commission’s website.
Need help deciding which Webroot product is right for you? Take our short quiz to discover the ideal plan for safeguarding your devices, privacy, and identity—whether it’s for you or your entire family. |
Tax season alert: Common scams and cracked software
OpenText is committed to providing you with the latest intelligence and tips to safeguard your digital life, especially during high-risk periods like tax season. Our threat analysts are constantly monitor the ebb and flow of various threats. One trend that has recently caught our attention is the notable spike in malware-infected cracked software, particularly as we enter tax season. This post aims to shed light on the dangers of using cracked software, share best practices for a secure tax season, and highlight our latest intelligence on the surge in cracked tax software threats.
The bidden cost of cracked software
Cracked software, often touted as a cost-free way to access games and expensive software, carries a significant risk far beyond legal and ethical concerns. These unauthorized versions are frequently loaded with malware, from trojans and keyloggers to ransomware. The allure of free access blinds users to the dangers, turning their devices into gateways for cybercriminals to steal sensitive information, encrypt files for ransom, or enlist computers into botnets.
Tax season: A cybercriminal’s playground
Tax season is inherently stressful, with individuals and businesses rushing to meet filing deadlines. It’s also a golden opportunity for cybercriminals to exploit vulnerabilities through phishing scams, identity theft, and malicious software. Our best practices for a secure tax season include:
- Use legitimate tax software: Always download tax preparation software directly from the official provider or authorized resellers.
- Enable multi-factor authentication (MFA): Adding an extra layer of security can significantly reduce the risk of unauthorized access.
- Beware of phishing attempts: Be skeptical of emails, messages, or phone calls claiming to be from the IRS or tax preparation services, especially those urging immediate action or asking for personal information.
- Seriously, the IRS will NOT email/text/call you for money: They will send you a letter to your mailbox.
- Keep software updated: Ensure that your operating system and all applications are up to date with the latest security patches.
- Secure your personal information: Store sensitive documents securely and only share personal information over encrypted connections. This especially means tax return forms.
The rise of cracked tax software threats
Our threat intelligence team has observed an increase in malware-infected cracked tax software. As tax season approaches, cybercriminals capitalize on the demand for tax preparation solutions, disguising malware as cracked versions of popular tax software. These malicious versions can steal personal and financial information, leaving users vulnerable to identity theft, financial loss, and potential legal consequences.
This trend underscores the importance of vigilance during tax season. The risks associated with using cracked software, especially for something as sensitive as tax preparation, cannot be overstated. Not only does this expose individuals to malware, but it also jeopardizes the integrity of personal and financial data.
The convergence of cracked software and tax season scams highlights a broader trend in cyber security threats. As cybercriminals become more sophisticated, the importance of adhering to best practices and using legitimate software cannot be overstated. Remember, the cost of using cracked software can far exceed the price of legitimate software, not just in dollars but in the potential for irreversible damage to your digital and financial well-being. Stay informed, stay secure, and let’s navigate the digital landscape safely together.
| Need help deciding which Webroot product is right for you? Take our short quiz to discover the ideal plan for safeguarding your devices, privacy, and identity—whether it’s for you or your entire family. |
Uncover the nastiest malware of 2023
Our annual analysis of the most notorious malware has arrived. As always, it covers the trends, malware groups, and tips for how to protect yourself and your organization.
This post covers highlights of our analysis, including the rise of ransomware as a service (RaaS), the six nastiest malware groups, and the role of artificial intelligence in both cybersecurity and cyberthreats.
Malware shifts to RaaS
To say cybercriminals have come a long way since their humble beginnings—when floppy disks were used to spread malware infections—is an understatement. Their tactics have evolved significantly over the years, with ransomware now the malware of choice for cybercriminals.
The allure of ransomware is not surprising given the combination of financial gains and potential for anonymity. Never satisfied in their quest to scale operations and increase revenue potential, criminal actors have shifted their focus to a relatively new “business model” that is proving very successful—ransomware-as-a-service (RaaS). By removing the technical barriers for prospective affiliates, RaaS makes it easy for big players to grow their “enterprise.”
Who made this year’s malware list?
Topping this year’s nastiest malware is CI0p. This ransomware group made a name for itself with the MOVEit campaign, which drove up the average ransom payment to nearly three-quarters of a million dollars. To date, this campaign is known to have impacted more than 1,150 organizations and over 60 million individuals, putting its global cost at close to $11 billion.
Also on the list are four new ransomware gangs—Black Cat, Akira, Royal, and Black Basta—believed to be the next generations of previous big players. They join a familiar name on the list, Lockbit.
We ranked these six malware groups accordingly:
- Cl0p, a RaaS platform, became famous following a series of cyberattacks that exploited a zero-day vulnerability in the MOVEit file transfer software developed by Progress Software.
- Black Cat, believed to be the successor to the REvil ransomware group, built its RaaS platform on the Rust programming language. Black Cat made headlines for taking down MGM Casino Resorts.
- Akira, presumed to be a descendant of Conti, primarily targets small- to medium-sized businesses. Most notably, Akira ransomware targeted Cisco virtual private network (VPN) products to breach corporate networks, steal data, and encrypt it.
- Royal, suspected heir to Ryuk, uses whitehat penetration testing tools to move laterally in an environment and gain control of the entire network. A unique partial encryption approach allows the threat actor to choose a specific percentage of data in a file to encrypt.
- Lockbit 3.0, a main stain on the list and last year’s winner, continues to wreak havoc. Now in its third epoch, Lockbit 3.0 is more modular and evasive than its predecessors.
- Black Basta, one of the most active RaaS threat actors, is considered to be yet another descendant of the Conti ransomware group. It has gained a reputation for targeting all types of industries.
An intelligent future: artificial intelligence and machine learning
For six years, the OpenText™ Cybersecurity threat intelligence team has witnessed a steady increase in the number and sophistication of malware attacks—which show no signs of slowing down. Threat actors are creative and resourceful in their attempts to trick users and exploit software and computer vulnerabilities. And while the use of artificial intelligence (AI) and machine learning (ML) in cybersecurity is still in its early stages, it is rapidly evolving. This is good and bad news.
AI and ML have the potential to make the world a safer place, but they could also be used for malicious purposes. Rather than taking a wait-and-see approach, businesses of every size must take steps to protect themselves and mitigate the risks.
For a more detailed analysis of the 2023 malware landscape and tips from OpenText Cybersecurity threat experts on how to protect against ransomware attacks, visit: Ask your question | Webroot Community
Building a cyber resilient business: The protection layer
Cybercrime is on the rise. The number of ransomware attacks has increased by 18%, while the worldwide volume of phishing attacks doubled to 500 million in 2022. Depending on the size of the business, one-third to two-thirds of businesses suffer malware attacks in any given year.
And those attacks are costing companies a lot of money. In 2022, American businesses lost $10.3 billion to data breaches and cybercrime.
This is all happening while companies are spending trillions digitizing their business operations and trying to obtain secure cyber insurance while keeping up with regulatory changes in GDPR, HIPAA, and Sarbanes-Oxley.
The best way to weather these challenges is to become a cyber resilient business. That means implementing a layered security and data management strategy that encompasses prevention, protection, and recovery so that your data, your bottom line, and your reputation remain secure.
In this article, we’ll discuss the importance of data security and protection.
How to protect your data
A sophisticated, layered security strategy will already have prevention tools like endpoint and DNS protection in place as well as security awareness training to stop threats before they reach your network.
Unfortunately, that’s not enough. Attacks are becoming increasingly sophisticated and complex, and that first line of defense may not catch them all.
If a threat can penetrate the prevention layer, protection-layer tools kick in to neutralize the threat or minimize the damage of an attack.
Here are two tools that can protect your data:
1. Email threat protection and email continuity
Email is one of the most common entry points for attacks, from phishing links to ransomware and business email compromise (BEC) to malicious attachments. Cyber criminals can mimic trustworthy senders so you need a tool that helps you tell the difference between a safe email and suspicious one.
Tools like Webroot’s Advanced Email Threat Protection analyze the links and attachments in messages to detect malware and keep your systems secure against threats. Webroot Email Continuity can continue to send and receive emails for up to 30 days even if the infrastructure is down.
2. Email encryption
Companies rely on email to distribute important information, but when that information is confidential and sensitive, you need an encryption tool to protect it. If a cyber criminal gets access to emails, they won’t be able to access that sensitive data if it’s encrypted.
Webroot Advanced Email Encryption powered by Zix is an industry-grade encryption tool that runs in the background, without disrupting workflows or requiring any input from the user. It’s invisible to the user and requires no extra training, while keeping your communications confidential. Also, default and customizable Data Loss Prevention (DLP) policies are available at no additional cost to prevent unauthorized users from emailing sensitive data to parties outside the organization.
Customer stories
When Spitzer Automotive’s new Chief Information Officer joined the company in 2019, he realized there was a big problem that affected the company’s security and employee productivity: employees were spending too much time reviewing emails for spam. One phishing attack slipping through human review could cause big problems for the company in downtime, financial loss, and reputational damage.
Spitzer chose Webroot’s Advanced Email Threat Protection and Email Continuity as a cloud-based solution to pair with Microsoft 365. Not only were they able to save money by bundling the two together, but it also allowed the company to automate email protection by reducing the number of email threats and quarantining malicious emails.
Allery, Asthma, and Sinus Center had a different reason for using Webroot Email Threat Protection and Email Continuity. As a healthcare group, they had sensitive patient data to protect and a ransomware attack from malicious emails could put that at risk.
Once they put the Webroot system in place, they were able to focus on other IT matters while knowing that patient data was safe. It also allowed them to be HIPAA compliant.
To learn more about building cyber resilience with layered security, download our guide.

















