Introducing Webroot BrightCloud® Streaming Malware Detection
We’re not telling you anything new when we say that malware continues to pose a major challenge for businesses of all sizes. Polymorphism, in particular, is especially dangerous. Polymorphic executables constantly mutate without changing their original algorithm, meaning the code can change itself each time it replicates, even though its function never changes at all. That’s why it’s so problematic; organizations that rely on traditional endpoint protection methods have little hope of detecting and blocking all the variants that might hit their network, even if they combine their antivirus technologies with network sandboxing.
How BrightCloud® Streaming Malware Detection Works
With all this in mind, we’ve developed Webroot BrightCloud Streaming Malware Detection. This brand new, innovative technology detects malicious files in transit, in real time, at the network perimeter. It can be integrated into perimeter network security devices to complement existing functionality by identifying and eliminating malicious files before they enter the network or have the chance to spread or mutate internally.
In most cases, Streaming Malware Detection can make determinations without requiring the entire file to be downloaded. It scans files in real time to make determinations after only a small portion of the file has streamed through a network perimeter device. Streaming Malware Detection determines quickly whether files are benign or malicious, enabling the device itself to block, drop, or route the file for further investigation, depending on how the technology partner or end customer chooses has configured the appliance.
For partners, Streaming Malware Detection…
- Adds malware detection functionality to your network device and enhances your ability to detect and block known and never-before-seen malware
- Makes determinations on a high percentage of previously unknown, zero-day, and malicious files at the network level
- Processes files at a rate of 5,700 files/min (over 500 times faster than a typical sandbox at 11 files/min)
- Continuously improves its own capabilities via self-learning
- Provides the flexibility to tune and adjust thresholds to minimize false positive rate
- Integrates quickly and efficiently in network edge security devices via precompiled SDK
- Provides an incremental revenue opportunity
How To Get Streaming Malware Detection
We’re currently planning to make this extra layer of protection against polymorphic malware, and targeted malware in general, available for GA in the second calendar quarter of 2017. For the time being, we’re pleased to invite existing and prospective Webroot technology partners to join our beta program. Contact your Webroot account representative to participate.
For more info about Streaming Malware Detection and other new Webroot services, read our press release.
Cyber News Rundown: Edition 2/10/17
Macros Turn Focus Towards MacOS
Researchers have discovered a trend of malicious Microsoft Word documents for MacOS that behave similar to Windows macro infections. The culprits download and execute a malicious payload to a user’s computer. While not particularly sophisticated, the macro-based infections focus on exploiting the users of the computer, rather than a software vulnerability, as macros can also be used for legitimate applications.
Phishing and Tax Season Go Hand in Hand
It’s tax season and criminals are working on new and clever ways to gain access to sensitive documents, and other available assets. This year brings the usual spear phishing campaigns that spoof an executive requesting tax forms, but arrive with a follow-up email requesting a wire transfer to a listed account. The best defense against these types of attacks is caution on the recipient of any suspicious emails, and using two-factor authentication where available.
Android Malware Triada Takes Top Spot
The reigning Android malware family has changed from Hummingbad, a rootkit downloader that remains persistent on devices and downloads fraudulent apps for ad revenue, to Triada, a malicious backdoor that grants super-user privileges to the malicious payloads that are downloaded according to a recent announcement. This switch comes after nearly a year as the most widespread infection for Android devices.
Teen Hacks 150,000 IoT Devices Overnight
It’s been revealed that a teenager from the UK, in the span of an evening, successfully hacked over 150,000 printers across the world. He created a simple program that sent printer protocol requests to various IoT devices and was able to get responses from and send jobs to different printers. The teen claims he did so to bring attention to the major lack in security for IoT devices that are connected to an insecure network.
Unpatched WordPress Sites Defaced
Thousands of WordPress sites have been defaced by hackers exploiting a bug patched nearly two weeks ago. Sites that haven’t been updated to the latest version were susceptible to a vulnerability in the REST API allowing unauthorized changes to be made to the title and any visible content. Due to the defacements, Google has begun categorizing affected sites by the hacker group’s names.
What’s new from Webroot in early 2017?
Throughout 2016, many of the attacks and risks in the world of cybercrime followed “analog” crime: holding something for ransom/extortion, propaganda, theft, and identity scams. You might expect a cybersecurity vendor to see these trends as good for business, but in fact it’s the opposite. The modern world relies heavily on the internet and web applications for all types of transactions. For these technologies to continue advancing, users have to feel safe when they conduct those transactions online. That means those of us in the cybersecurity field are dealing with trust as our most valuable commodity. Erode the trust too deeply and many internet users will either take their business elsewhere, or try to avoid online transactions altogether.
Maintaining customers’ trust should always be the core of any cybersecurity provider’s strategy. In 2017, we plan to continue coming up with new ways to use our threat intelligence and cloud-based security platform to do just that. Here’s a look at what’s in store.
Webroot SecureAnywhere® DNS Protection
To kick off the year, we’ve introduced our new Webroot SecureAnywhere® DNS Protection service. By redirecting users’ internet traffic through the Webroot DNS cloud, businesses now get enhanced visibility, control, and peace of mind. Web requests are checked in real time to ensure they are not malware connecting to a Command and Control server, or requests to visit high risk sites. SecureAnywhere DNS Protection also lets businesses fine-tune web access policies by IP address or IP range, and limit access to websites based on their category—with 82 URL categories to choose from. This simple, domain layer security improves productivity, provides great visibility, and is a smart and cost-effective way to dramatically reduce web risks.
Webroot FlowScape®
The second new offering is a state-of-the-art approach to early threat detection that works by analyzing all the traffic taking place within your network; not just communications to and from the internet, but also those that occur between network-connected devices. Using supervised and unsupervised machine learning and behavioral analytics, the Webroot FlowScape® solution cuts through everyday network noise to reveal network anomalies and threats that other security technologies miss, and does so early enough for security administrators to prevent those threats from compromising the network. The FlowScape solution is designed for MSSPs and other IT security professionals who need to identify all the adversarial anomalies and risks within their networks.
Webroot BrightCloud® Streaming Malware Detection
Last, but not least, we are releasing Webroot BrightCloud® Streaming Malware Detection for polymorphic malware protection. This technology detects malicious files as they stream through the network perimeter in real time, without having to download the entire file, and without causing undue network latency. Streaming Malware Detection is designed to be integrated into network security devices to help identify and eliminate malicious files before they enter the network.
2017 will bring many new security challenges, but with these new solutions in place and other innovations on the Webroot drawing board, we plan to keep building our customers’ safety, security and trust.
Increasing Profits by Moving to the MSP Model
The benefits of adopting the managed service provider (MSP) business model are compelling. After all, predictable, recurring revenue; deeper engagement with clients; and a trusted advisor relationship that generates further business opportunities all sound like everything a successful services business could want. However, for some, it still means braving uncharted territory.
Important Considerations
IT solutions providers interested in switching to the MSP model face a number of decisions. Before you do anything else, you have to define your service offerings. There are so many companies who offer products in the primary MSP categories, so it’s important to take your time in performing a detailed analysis of the pros and cons of various products.
- Automation
Plain and simple, you need automation tools. These include professional services automation (PSA) and remote monitoring and management (RMM) software, which are the backbone of every MSP’s business. Pay close attention not to just features, but the pricing structure and integrations with the other tools you plan to use. - Timing
Another challenge can be finding the right timing to migrate existing customers. The process of transitioning current customers can be a minefield of logistical issues, particularly if those customers purchased different products on a staggered schedule. In those cases, you must consider not just what your full managed services offering will look like, but how to get existing customers onto a monthly bundle.
Differentiating Your Business
Remote monitoring is a standard part of the traditional MSP portfolio. Disaster recovery, such as a secure backup system, is also a leading service to pitch to customers, since disasters of all types can hit an organization at any time, and have the potential to cripple their business operations. So what’s going to make you stand out? You might not think so, but many MSPs are leading with another equally important service: endpoint security.
Computers, mobile devices, and servers will always need protection, but modern businesses face a variety of new challenges. Cybercriminals have only increased their efforts at causing mischief, launching new and creative ransomware with startling frequency at companies around the globe. Additionally, many organizations in the healthcare, financial, and retail segments have compliance mandates for handling sensitive data, which typically include endpoint security. In short, the time is right for starting a conversation about security.
Selecting Cybersecurity
The MSP model is about efficiency gains, so choose a provider that helps reduce your TCO. Look for a security offering that doesn’t need a local server, offers flexible monthly billing, and consider a solution that’s cloud-based so it won’t impact system performance. The security application you choose should be effective, lightweight, and have no noticeable impact when running.
Should disaster strike, it’s also very important to have a solution that can remediate systems automatically, reducing the burden on your IT staff. On the topic reducing burdens, the solution should also include PSA or RMM integration, or a management console that can automate routine tasks and give you the granular visibility you need to oversee all your customers in one place.
Making the Switch to the MSP Model
While adding managed services might seem daunting, it’s a powerful way for resellers to add new revenue streams to the business while transitioning into a hybrid or full MSP model. Keeping costs down on monthly contracts gives MSPs a big advantage today, and if the managed services model didn’t work for both customers and IT solution providers, it wouldn’t have seen the adoption and success it has experienced in recent years. Although the transition isn’t easy, it holds a lot of promise. IT solution providers in transition can rest assured that their best and most profitable years are ahead.
Read this case study to find out how SLPowers, an MSP managing 76 different companies with over 2,000 endpoints, got its start in the reseller realm, moved to managed services, and leveraged next-generation endpoint protection to improve customer satisfaction, lower costs, and increase profitability
Or, take a free, no-risk, no-conflict 30-day trial of Webroot SecureAnywhere Business Endpoint Protection with the Global Site Manager to see the solution SLPowers chose in action.
Cyber News Rundown: Edition 2/3/17
Hotel Doors Locked By Ransomware
A prestigious hotel in Austria was the target of a ransomware attack that left their electronic door locking systems inoperable for several hours. The hack only stopped hotel personnel from activating new keycards due to system is capabilities allowing the functionality without power. Unfortunately, the hotel did pay a ransom of 2 bitcoins. They now have plans to replace the electronic lock system with traditional keys to avoid any future complications.
WordPress Quietly Fixes Critical Vulnerability
Reports have surfaced that WordPress deployed an update resolving several crucial vulnerabilities allowing unauthorized users to access and modify WordPress hosted sites. REST API is the source of the vulnerability. The API was implemented in an earlier version and set to be enabled by default. Fortunately for many WordPress users, the exploit was resolved without any signs of the issue being exploited in the wild.
Ransomware Locks up Texas Police Department
A Texas police department was forced to wipe their servers ridding ransomware encrypting documents and video evidence stored on computers. Officials have stated that the infection started from a spam email link and spread through nearly 8 years worth of data before the individual computer was taken offline.
Netflix Login Generator Creates More Than Credentials
Researchers have discovered a new ransomware variant that comes bundled inside a Netflix login generator application. When users click on the “Generate Login!” button, they are met with a dropped executable that begins encrypting any file located in the main Users directory of the computer. Currently, this variant only runs in Windows 7 and 10 and demands a smaller ransom than normal ($100 or .18 bitcoins), likely in the hope of actually receiving payment.
Office Printers Susceptible to Cyber Attack
While many believe that employees are the main point of vulnerability for a typical corporation, it should be mentioned that the quietest machine in the office can also be an attack vector: the printer. With wireless access becoming ever more prevalent, it’s no surprise that cyber criminals are looking to different areas of opportunity. With nothing more than authority to use the printer, there are several ways to bring the machine to a halt or even gather data that passes through.
Webroot Attends RSAC 2017
Twitter is buzzing with chatter about the RSA Conference 2017 (RSAC). Attendees, vendors, and speakers alike are anxiously awaiting the opportunity to discuss information security and the latest technology at the largest security conference in the world. Attending RSAC? Here’s what you should know about Webroot.
What’s new with Webroot in 2017
Today, we announced the expansion of our platform with 3 new products; Webroot FlowScape® Analytics, Webroot BrightCloud® Streaming Malware Detection, and Webroot SecureAnywhere® DNS Protection leverage the security industry’s most sophisticated artificial intelligence engine to give customers greater protection against today’s most dangerous known and unknown cyber threats.
By providing deeper insight into behaviors in the web and network layers, our new products offer better protection against today’s most advanced threats—both known and unknown—no matter where users are or what devices are connected. – Chad Bacher, SVP of product strategy and technology alliances, Webroot
During RSAC, be sure to visit us in the South Expo at booth #S1307 to experience Webroot threat intelligence and security products in action.
The Webroot Briefing Center Presentation at RSAC
Identifying threats within the barrage of everyday network traffic can be difficult. During our Briefing Center Presentation Securing the Internet of Everything: How Webroot Keeps a Smart City Safe, Chad Bacher will be discussing this how smart cities and other organizations can use advanced inspection modeling, and analytics inside the network to avoid security risks.
In-Booth Presentations
Webroot is hosting multiple in-booth presentations throughout the conference. Presentation topics will include our insights into the most recent threat trends, stopping polymorphic malware, using machine learning to detect zero-day threats, and more. Be sure to set a private meeting with Webroot security experts, also.
Join leading security pros and innovators, including the Webroot team, at RSAC 2017 to learn about the current state of cybersecurity. Get our thoughts on what the future holds.
Cyber News Rundown: Edition 1/27/17
Major Dark Web Marketplace Hacked
Recently, a hacker using the alias cypher0007 reached out to AtlasBay, a large dark web market, with information on two significant vulnerabilities that allowed him to access over 200,000 private messages, names, and addresses. Along with retrieving a good amount of buyer and seller information, the hacker also revealed that the site had no encryption on its private messaging feature. For users of the online marketplace, their data has been secured in addition to AlphaBay releasing patches for both vulnerabilities.
Ransomware Victims Likely to Pay for Data Retrieval
In a recent study, it was revealed that nearly half of businesses hit with ransomware were willing to pay the ransom which often reached over $10,000. Many of the respondents believed that the loss of data was actually less costly than the overall downtime for the business, loss of customers, and the investment in new security measures. More surprisingly, 17% of the victim companies did not involve a law enforcement agency for fear of additional attacks on their infrastructure.
Latest Firefox Update Flags Insecure Logins
Following in the steps of Google, Firefox has released an update that has resolved many security flaws that have been prevalent for quite some time. The main focus appears to be on flagging HTTP login pages as insecure and giving users an additional warning if they begin typing in an insecure username or password field. Also, Firefox has begun refusing to accept SHA-1 certificates from several public companies, as a sign of lost faith.
Android Ransomware Found On Google Play
In the last week, researchers discovered a new ransomware variant embedded in a seemingly innocent app on the Google Play store. The variant, named Charger, begins by prompting the user to allow administrator access to the device. Once access is given, the user is shown a ransom lock screen and the app starts downloading user contact and SMS data while asking for a mere 0.2 bitcoins, or roughly $180. Fortunately, the app was caught early and removed from the app store with a minimal number of total downloads.
Dark Web Hacker Steals Over 1 Billion User Accounts
With corporate hacking being more profitable than ever, it comes as no surprise to see dark web vendors selling data for millions of users. Recently however, one vendor has offered access to over 1 billion unique user accounts from some of China’s largest online vendors. Alongside the initial listing for the main Chinese accounts, the hacker also offers another ~46 million email accounts from varying domains.
How F5 is Changing the Application Security Game
To address the need for application security in the digital transformation era, F5 is releasing a new host of products and services.
“The digital transformation has really changed security as a whole,” says Preston Hogue, Director of Security Marketing and Competitive Intelligence. What he means is that everything—EVERYTHING—is moving to the cloud. Think about the companies from years ago, such as Blockbuster, versus their modern counterparts, like Netflix or Hulu. Think about the fact that most of today’s twenty-somethings have never set foot in a physical bank branch, but use online banking daily. Now think about the fact that every service I’ve mentioned so far has an application, which is the primary method of interaction for users.
The application is the new perimeter and identity is the key to that perimeter. Over 70% of all data breaches occur by accessing applications. At F5, we are focused on securing our customers’ applications; both by securing access to the apps, and by securing the apps themselves where they reside.
We spoke with Preston about the newest security products F5 is launching, and how they’re using Webroot BrightCloud® IP Reputation intelligence to help power their solutions.
Webroot: Tell us a little bit about the security launch. What should we expect to see?
Preston Hogue: First, we are launching a family of dedicated security products called Herculon. The first two components of the Herculon product family are the Herculon SSL Orchestrator and the Herculon DDoS Hybrid Defender. These products are dedicated to solving the challenges of SSL/TLS encrypted traffic and ensuring application availability.
Second, we’re announcing a new service called Silverline WAF Express, which will give customers easy, self-service access to our cutting-edge web application firewall. We’ve been deploying web application firewalls on premises for some time and also offer a fully managed service. Since some customers don’t have the time or resources to install and maintain the software, or maintain the racks and stack and everything within their environment, we’re giving them a simpler self-service experience.
Our focus on securing applications means our overall threat research is geared toward application threat intelligence—really trying to get to the root cause of the 70+% of data breaches I mentioned previously—so we’re also announcing increased investment in our F5 Labs threat intelligence team.
Last but not least, we’re also announcing that the services of our security incident response team (SIRT), a dedicated team of highly trained individuals within the support organization, are now available to all F5 customers around the world. This team will be the highest level of escalation for security and service response.
Since threat intelligence is such a huge component of your offerings, what should your target customers consider when choosing threat intelligence sources for themselves?
There are a lot of companies that offer threat intelligence, but it’s challenging because they all claim a kind of broad, generic expertise. We advise that customers look for specificity; for targeted, actionable information that pertains to what they’re trying to do. Looking at a company like Webroot, you’ve taken on very specific aspects of threat intelligence and you’ve been able to master those particular areas—like the Webroot IP reputation intelligence that we integrate.
We see a lot of organizations trying to take on too much. That’s why we’re very definitive about the scope of what we’re trying to accomplish, and why we focus on leveraging our application security expertise around threats and ensuring we can provide very specific, clear, actionable threat intelligence with F5 Labs.
What do you hope your customers will gain by implementing your solutions with Webroot BrightCloud IP Reputation intelligence?
We know we have the expertise when it comes to understanding the overall threat to an application. We partner with companies like Webroot for insight into a particular aspect of threats; in Webroot’s case, it’s insight into IP addresses and additional threat information around user agents and anonymous proxies. We’re very specific in our threat intelligence, and we know we’re not always able to show the entire picture on our own. So we are able to fill in other areas of the overall threat landscape through our partnerships to ensure that we can give our customers the full picture they need.
How do you see the F5 security launch changing the security industry?
F5 has been in application security for over 20 years. From what we’ve seen, digital transformation is changing security as a whole. It has driven applications out of the data center and into the cloud. That means there are 3.2 billion users on the internet, who all potentially have access to these applications, which makes them a big target for breaches. Because of our expertise within the field, F5 is in the perfect position to provide visibility into this threat landscape, and also the control our customers need to achieve a secure application experience.
In his closing comments, Hogue had the following to say, “To secure access to applications and to secure the apps where they reside, you need a complete picture of the threats that target apps. You need a team like F5, with an ecosystem of intelligence partners like Webroot to provide that picture. And that’s how, ultimately, we can help our customers solve today’s security challenges and keep users safe.”
Learn more about Webroot BrightCloud IP Reputation intelligence. Or, for more information about F5’s security launch, read the press release.
Cyber News Rundown: Edition 1/19/17
MongoDB Hacks Spreading Fast
In the past few weeks, researchers have been monitoring the steady rise of hacked MongoDB installations, now surpassing over 28,000 individual systems. While the attacks started with ransoming back the stolen data, the attackers have now begun simply deleting the information from the database and leaving the ransom note for payment anyways. With up to 12 different attackers as well, crossover hacks have occurred on several of the databases, leaving the victim unsure of who to contact or how to retrieve their missing data.
Miami Bank Loses Millions without Notice
Recently, a major Miami Beach bank has been under heavy scrutiny after nearly $4 million USD were stolen from their accounts without any suspicion arising. According to officials, the thefts began in the summer of 2016 and continued until December, when they were given a report showing a large number of fraudulent transactions taking place in the form of automatic billing payments that were being rerouted. Amidst the scandal, several prominent financial executives were forced to resign.
Amazon Phishing Scheme Targeting User Credentials
Users of retailing giant, Amazon, have noticed some oddly suspicious behavior when attempting to purchase items with prices that are too good to be true. Items being posted for sale the fraudulent merchant are available to purchase, until you add the item to your cart and begin checking out. Once in the cart, the item mysteriously disappears and a message stating that it is no long available appears. Users are then contacted by the vendor via email with a new link to purchase the item, though this link does not direct the user back to the legitimate Amazon site, but instead one that looks similar and wants your credentials badly.
Ukraine Power Stations Still the Focus of Cyber Attacks
It’s been almost exactly one year since the major power outages that affected nearly a quarter million Ukrainians, and once again, the hackers are up to their same tricks. In the last month, officials have been working to determine if the latest power substation failure was a legitimate failure or the results of another cyberattack. With the latter being confirmed, it is still surprising how little damage the hackers have actually done, with nothing more than overwriting the firmware used in the power stations to signal a manual reset to engineers on site. Researchers believe these attacks are merely a test of their capabilities and learning what security is in place and how to bypass it.
Spora Ransomware Offering New Encryption Process
With ransomware being the highest grossing cyber-attack vector, it’s no surprise that attackers are coming up with clever new methods for causing user devastation. By adding an additional encryption step, allowing for offline encryption, the attackers are able to create a new set of AES keys on the local machine which will stop decryptors from unlocking all of the victims with one private key. Additionally, Spora has the capability to gather information about the computer itself and determine an appropriate ransom amount, whether it’s for an individual user or a large corporate network.
Satan: A new ransomware-as-a-service
Ransomware as a Service (RaaS) has been growing steadily since it made its debut in 2015 with Tox. With the new Satan service, it’s easier than ever. The idea is to use this web portal to contract threat actors to create new ransomware samples for distribution via the desired attack vector. This allows any potential cybercriminal, regardless of their skill or coding knowledge, to upgrade to an encrypting ransomware business model.
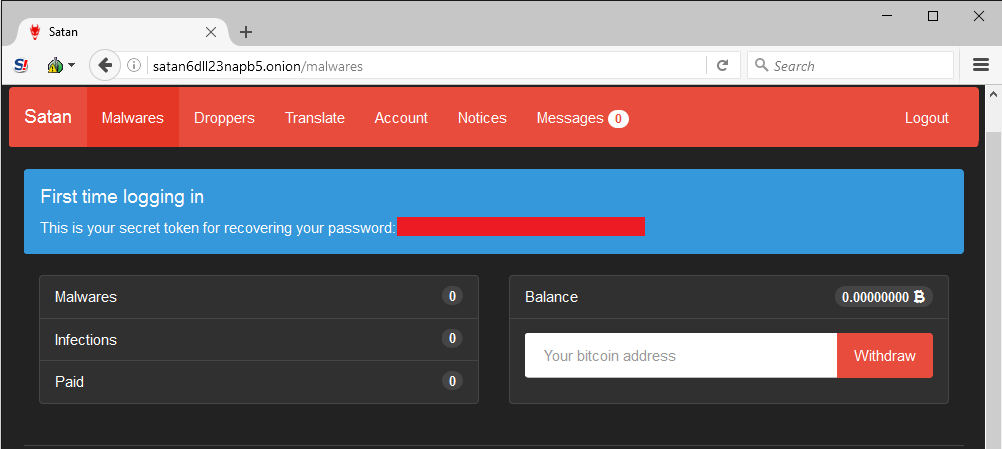
Those who join the program have a number of viewing options in the portal. The Account panel shows various stats, including how much money has been made, infection count, current share percentage, etc.
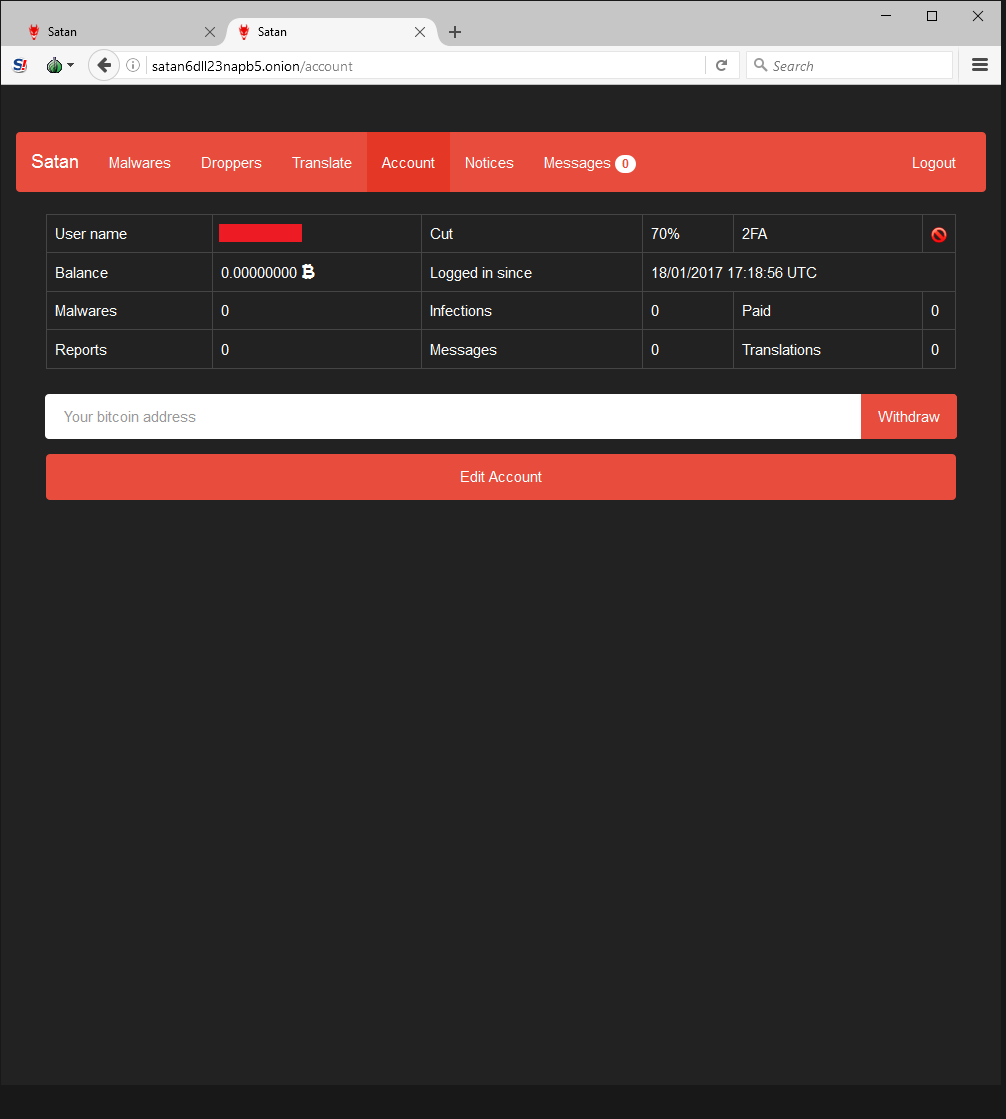
All a criminal needs to do is enter a few simple pieces of information to generate brand new malware that’s ready to infect victims. Note that the portal author specifically requests downloaded samples not be shared with VirusTotal, decreasing the likelihood that security vendors will have encountered the variant.
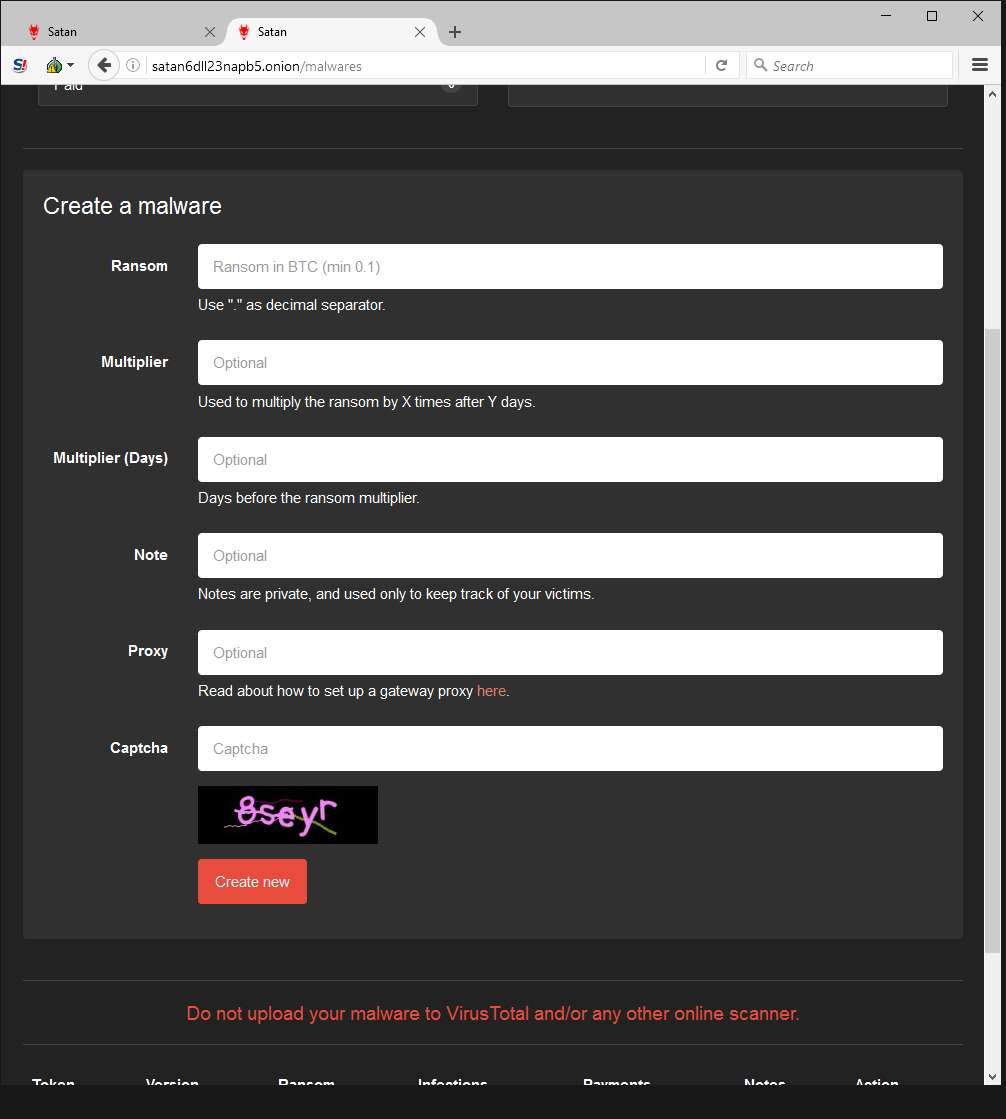
Since the darknet web portal creator takes a 30% cut of all ransoms, it’s in his best interests to make sure as many victims are infected as possible. He provides a guide with step-by-steps instructions on how to deploy malware using obfuscation techniques to avoid detection.
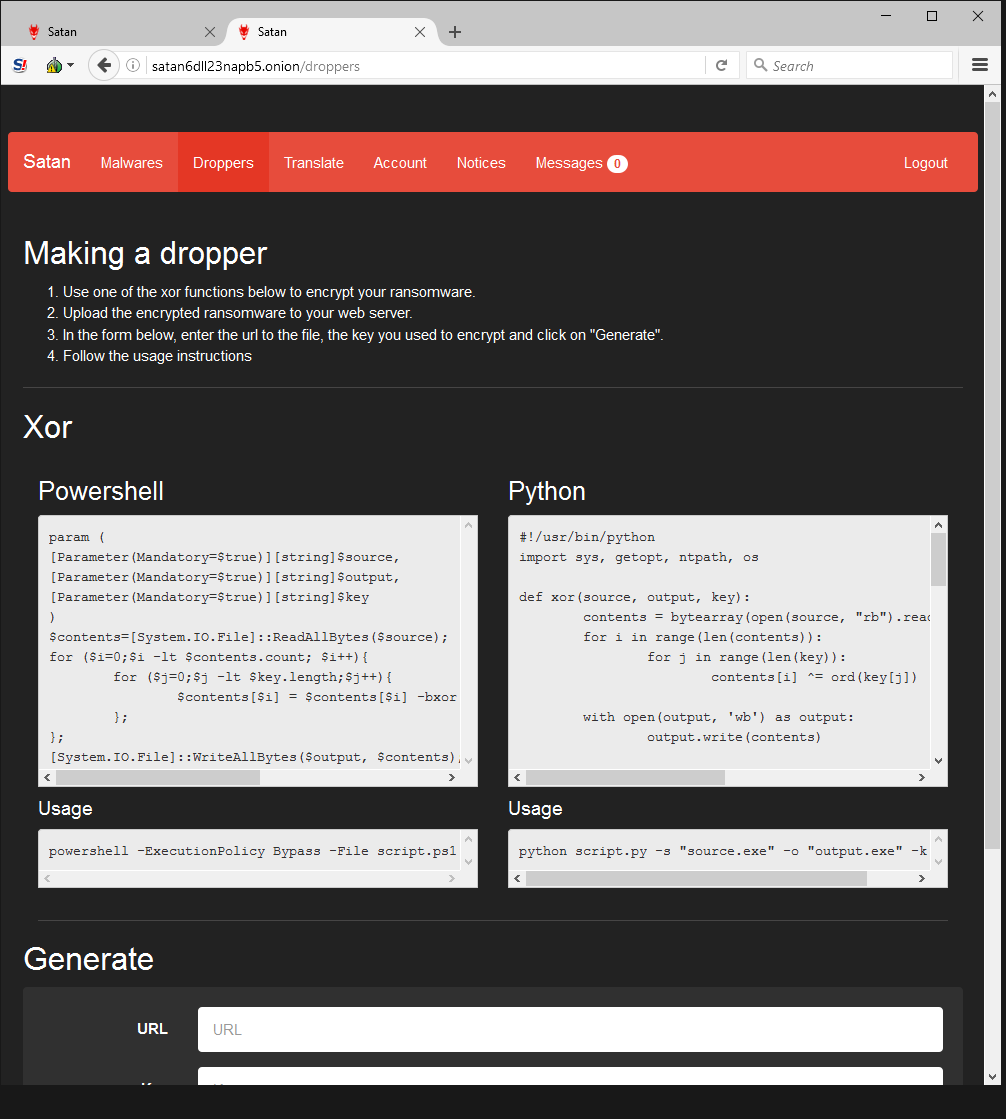
The author also advertises his web portal on underground forums, and explains the payload and the payout scheme. After all, affiliates’ success means he gets a bigger cut.
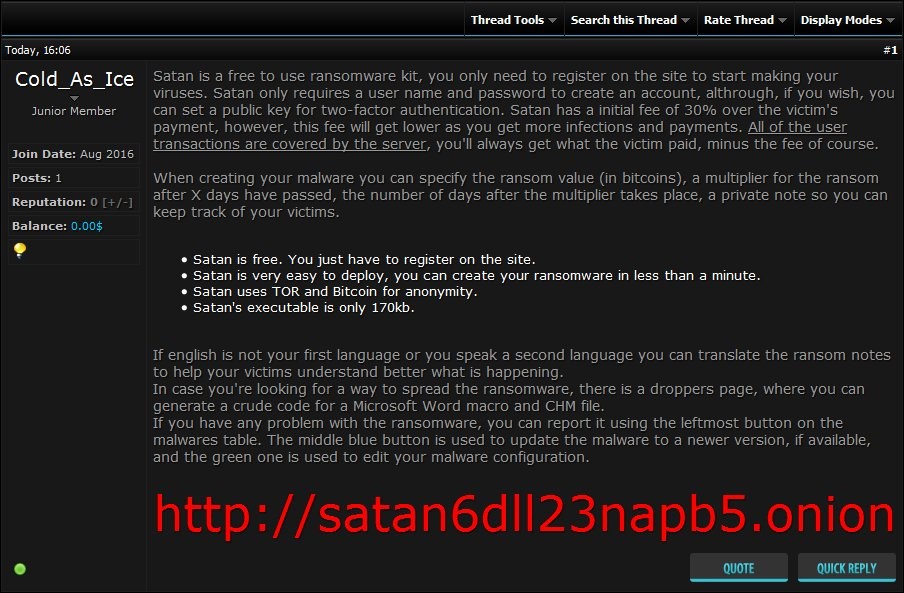 Although Webroot will catch this specific variant of ransomware as a service in real time before any encryption takes place, don’t forget that the best protection in your anti-ransomware arsenal is a good backup solution. You can use a cloud service or offline external storage, but keeping it up to date is crucial for business continuity.
Although Webroot will catch this specific variant of ransomware as a service in real time before any encryption takes place, don’t forget that the best protection in your anti-ransomware arsenal is a good backup solution. You can use a cloud service or offline external storage, but keeping it up to date is crucial for business continuity.
For best practices for securing your environment against encrypting ransomware, see our community post.
Webroot named among the Best Software Products for IT Teams 2017
“Highest average score for ease of use, quality of support, and […] requirements in endpoint protection.” That’s how Marty Duffy, Director of Research at G2 Crowd, describes Webroot after seeing the results of this year’s G2 Crowd survey on Best Software for IT Teams 2017. We’d be lying if we said we weren’t over the moon.
Webroot Endpoint Protection’s users consistently commended the product in 2016. Mid-market users recognized the tool as a stand-out product to be used by IT teams. It received the highest average score for ease of use, quality of support, and meets requirements in endpoint protection (mid-market). – Marty Duffy, Director of Research, G2 Crowd
G2 Crowd is a peer-to-peer business software review platform. Since 2014, they’ve recognized the best software products based on reviews by professionals across numerous markets. Their awards are supported exclusively by actual user satisfaction ratings, not obscure testing methodologies or paid industry reviewers. This is important to us for a couple of reasons.
Integrity and Customer Focus
At Webroot, two of our core company values are integrity and customer focus. We believe in respect, honoring our commitments, and measuring our success by our customers’ success. Our strength as a company is defined by the people who trust us to protect their businesses, clients, homes, and families. We’re proud to repay their trust by giving them the best possible service.
Real-time Protection
Cybersecurity continues to be a topic that gets more groans than cheers. Most users, both at home and at work, consider cybersecurity to be a kind of necessary evil. Sure, it keeps you safe from malware and other attacks, but it can also slow down your computer and get in the way of your activities. But we’re in the business of changing people’s minds on the subject. We devised a smarter way to protect businesses and individuals in the connected world. Our cloud-based protection and threat intelligence stop threats using behavior and contextual data, without draining system resources. We eliminated the hassle of system-intensive updates. And when any Webroot-protected device encounters a new threat, every device connected to our advanced threat intelligence platform is protected in real time.
Being recognized for this award serves to underscore our commitments as we continue to grow and innovate throughout the coming year. And, hot on the heels of being named Most Customer Friendly Company of the Year, we’ve only got one more thing to say: Thank you!
See for yourself what all the fuss is about. Take a free 30-day trial of Webroot SecureAnywhere® Business Endpoint Protection today. It won’t conflict with your existing security, and only takes a few seconds to install.
Your 6-Step MSP Guide for Stopping Ransomware
While a lot of the hype around ransomware paints it as daunting and virtually impossible to combat, there are several very straightforward steps for managed service providers to dramatically reduce the risk that their clients’ will fall victim to ransomware.
-
Proven endpoint security backed by industry-leading threat intelligence.
Security shouldn’t just spot and quarantine threats that have already infiltrated a system. It should prevent threats from infecting the endpoint in the first place. Be sure to select a solution that protects web browsing in real time, secures system settings, controls outbound traffic, provides proactive anti-phishing, and continuously monitors and reports on individual endpoints.
-
Get your house in order with backup and business continuity.
If any of your clients do become ransomware victims, the only real course of action is to restore their data as quickly as possible to minimize business downtime. These days, there are a fair number of automated, on-premises and cloud-based business continuity solutions that will back up data and get your clients’ business back on track after a breach.
-
Implement strong Windows policies.
As part of your ransomware defense strategy, you can use Windows policies to block certain paths and file extensions from running. If you need varying levels of access, you can set up policies in groups. Some useful policies include blocking executables in temp or temp+appdata and the creation of startup entries. For instance, .SCR, .PIF, and .CPL file types should not be run in the following in users’ temp, program data, or desktop directories.
-
Block volume shadow copy service.
Windows uses the VSS copy service to create local copies of files. CryptoLocker and other ransomware variants will encrypt this area because it holds VSS copies for the local (C:) drive. By setting Windows policies to block access to the service, you can help stop ransomware like CryptoLocker from erasing local drive file backups. Make sure that policies point to the VSSAdmin executable. Attempts to access or stop the service will be blocked.
-
Get rid of macros and autorun.
Numerous kinds of ransomware use macros to infect systems, but you can easily disable them in the Trust Center of every version of Microsoft Office. You can also enable individual macros, if they’re necessary for a particular task, while disabling all others. Additionally, autorun might be a handy feature, but many types of malware use it to propagate. As an example, a USB stick uses autorun, but so do Visual Basic Script (VBS) malware and worms. As a general rule, we recommend disabling autorun.
-
Keep clients in the know about ransomware.
It’s no secret that human error is a large part of successful cybercrime. As long as staff members remain relatively unaware and undereducated about the risks of the internet, malware will continue to be a viable business. Make sure clients understand the basics and what to watch out for so they stay safe both at home and in the office.
The first step to securing endpoints against ransomware is deploying a next-generation security solution. Take a free 30-day Webroot trial, no risk, no obligation to buy. In less than five minutes you can install Webroot SecureAnywhere® Business Endpoint Protection with Global Site Manager and see first-hand how it delivers superior malware protection while lowering your costs and boosting your bottom line—without conflicting with your existing security.