Increasing Profits by Moving to the MSP Model
The benefits of adopting the managed service provider (MSP) business model are compelling. After all, predictable, recurring revenue; deeper engagement with clients; and a trusted advisor relationship that generates further business opportunities all sound like everything a successful services business could want. However, for some, it still means braving uncharted territory.
Important Considerations
IT solutions providers interested in switching to the MSP model face a number of decisions. Before you do anything else, you have to define your service offerings. There are so many companies who offer products in the primary MSP categories, so it’s important to take your time in performing a detailed analysis of the pros and cons of various products.
- Automation
Plain and simple, you need automation tools. These include professional services automation (PSA) and remote monitoring and management (RMM) software, which are the backbone of every MSP’s business. Pay close attention not to just features, but the pricing structure and integrations with the other tools you plan to use. - Timing
Another challenge can be finding the right timing to migrate existing customers. The process of transitioning current customers can be a minefield of logistical issues, particularly if those customers purchased different products on a staggered schedule. In those cases, you must consider not just what your full managed services offering will look like, but how to get existing customers onto a monthly bundle.
Differentiating Your Business
Remote monitoring is a standard part of the traditional MSP portfolio. Disaster recovery, such as a secure backup system, is also a leading service to pitch to customers, since disasters of all types can hit an organization at any time, and have the potential to cripple their business operations. So what’s going to make you stand out? You might not think so, but many MSPs are leading with another equally important service: endpoint security.
Computers, mobile devices, and servers will always need protection, but modern businesses face a variety of new challenges. Cybercriminals have only increased their efforts at causing mischief, launching new and creative ransomware with startling frequency at companies around the globe. Additionally, many organizations in the healthcare, financial, and retail segments have compliance mandates for handling sensitive data, which typically include endpoint security. In short, the time is right for starting a conversation about security.
Selecting Cybersecurity
The MSP model is about efficiency gains, so choose a provider that helps reduce your TCO. Look for a security offering that doesn’t need a local server, offers flexible monthly billing, and consider a solution that’s cloud-based so it won’t impact system performance. The security application you choose should be effective, lightweight, and have no noticeable impact when running.
Should disaster strike, it’s also very important to have a solution that can remediate systems automatically, reducing the burden on your IT staff. On the topic reducing burdens, the solution should also include PSA or RMM integration, or a management console that can automate routine tasks and give you the granular visibility you need to oversee all your customers in one place.
Making the Switch to the MSP Model
While adding managed services might seem daunting, it’s a powerful way for resellers to add new revenue streams to the business while transitioning into a hybrid or full MSP model. Keeping costs down on monthly contracts gives MSPs a big advantage today, and if the managed services model didn’t work for both customers and IT solution providers, it wouldn’t have seen the adoption and success it has experienced in recent years. Although the transition isn’t easy, it holds a lot of promise. IT solution providers in transition can rest assured that their best and most profitable years are ahead.
Read this case study to find out how SLPowers, an MSP managing 76 different companies with over 2,000 endpoints, got its start in the reseller realm, moved to managed services, and leveraged next-generation endpoint protection to improve customer satisfaction, lower costs, and increase profitability
Or, take a free, no-risk, no-conflict 30-day trial of Webroot SecureAnywhere Business Endpoint Protection with the Global Site Manager to see the solution SLPowers chose in action.
Cyber News Rundown: Edition 2/3/17
Hotel Doors Locked By Ransomware
A prestigious hotel in Austria was the target of a ransomware attack that left their electronic door locking systems inoperable for several hours. The hack only stopped hotel personnel from activating new keycards due to system is capabilities allowing the functionality without power. Unfortunately, the hotel did pay a ransom of 2 bitcoins. They now have plans to replace the electronic lock system with traditional keys to avoid any future complications.
WordPress Quietly Fixes Critical Vulnerability
Reports have surfaced that WordPress deployed an update resolving several crucial vulnerabilities allowing unauthorized users to access and modify WordPress hosted sites. REST API is the source of the vulnerability. The API was implemented in an earlier version and set to be enabled by default. Fortunately for many WordPress users, the exploit was resolved without any signs of the issue being exploited in the wild.
Ransomware Locks up Texas Police Department
A Texas police department was forced to wipe their servers ridding ransomware encrypting documents and video evidence stored on computers. Officials have stated that the infection started from a spam email link and spread through nearly 8 years worth of data before the individual computer was taken offline.
Netflix Login Generator Creates More Than Credentials
Researchers have discovered a new ransomware variant that comes bundled inside a Netflix login generator application. When users click on the “Generate Login!” button, they are met with a dropped executable that begins encrypting any file located in the main Users directory of the computer. Currently, this variant only runs in Windows 7 and 10 and demands a smaller ransom than normal ($100 or .18 bitcoins), likely in the hope of actually receiving payment.
Office Printers Susceptible to Cyber Attack
While many believe that employees are the main point of vulnerability for a typical corporation, it should be mentioned that the quietest machine in the office can also be an attack vector: the printer. With wireless access becoming ever more prevalent, it’s no surprise that cyber criminals are looking to different areas of opportunity. With nothing more than authority to use the printer, there are several ways to bring the machine to a halt or even gather data that passes through.
Webroot Attends RSAC 2017
Twitter is buzzing with chatter about the RSA Conference 2017 (RSAC). Attendees, vendors, and speakers alike are anxiously awaiting the opportunity to discuss information security and the latest technology at the largest security conference in the world. Attending RSAC? Here’s what you should know about Webroot.
What’s new with Webroot in 2017
Today, we announced the expansion of our platform with 3 new products; Webroot FlowScape® Analytics, Webroot BrightCloud® Streaming Malware Detection, and Webroot SecureAnywhere® DNS Protection leverage the security industry’s most sophisticated artificial intelligence engine to give customers greater protection against today’s most dangerous known and unknown cyber threats.
By providing deeper insight into behaviors in the web and network layers, our new products offer better protection against today’s most advanced threats—both known and unknown—no matter where users are or what devices are connected. – Chad Bacher, SVP of product strategy and technology alliances, Webroot
During RSAC, be sure to visit us in the South Expo at booth #S1307 to experience Webroot threat intelligence and security products in action.
The Webroot Briefing Center Presentation at RSAC
Identifying threats within the barrage of everyday network traffic can be difficult. During our Briefing Center Presentation Securing the Internet of Everything: How Webroot Keeps a Smart City Safe, Chad Bacher will be discussing this how smart cities and other organizations can use advanced inspection modeling, and analytics inside the network to avoid security risks.
In-Booth Presentations
Webroot is hosting multiple in-booth presentations throughout the conference. Presentation topics will include our insights into the most recent threat trends, stopping polymorphic malware, using machine learning to detect zero-day threats, and more. Be sure to set a private meeting with Webroot security experts, also.
Join leading security pros and innovators, including the Webroot team, at RSAC 2017 to learn about the current state of cybersecurity. Get our thoughts on what the future holds.
Cyber News Rundown: Edition 1/27/17
Major Dark Web Marketplace Hacked
Recently, a hacker using the alias cypher0007 reached out to AtlasBay, a large dark web market, with information on two significant vulnerabilities that allowed him to access over 200,000 private messages, names, and addresses. Along with retrieving a good amount of buyer and seller information, the hacker also revealed that the site had no encryption on its private messaging feature. For users of the online marketplace, their data has been secured in addition to AlphaBay releasing patches for both vulnerabilities.
Ransomware Victims Likely to Pay for Data Retrieval
In a recent study, it was revealed that nearly half of businesses hit with ransomware were willing to pay the ransom which often reached over $10,000. Many of the respondents believed that the loss of data was actually less costly than the overall downtime for the business, loss of customers, and the investment in new security measures. More surprisingly, 17% of the victim companies did not involve a law enforcement agency for fear of additional attacks on their infrastructure.
Latest Firefox Update Flags Insecure Logins
Following in the steps of Google, Firefox has released an update that has resolved many security flaws that have been prevalent for quite some time. The main focus appears to be on flagging HTTP login pages as insecure and giving users an additional warning if they begin typing in an insecure username or password field. Also, Firefox has begun refusing to accept SHA-1 certificates from several public companies, as a sign of lost faith.
Android Ransomware Found On Google Play
In the last week, researchers discovered a new ransomware variant embedded in a seemingly innocent app on the Google Play store. The variant, named Charger, begins by prompting the user to allow administrator access to the device. Once access is given, the user is shown a ransom lock screen and the app starts downloading user contact and SMS data while asking for a mere 0.2 bitcoins, or roughly $180. Fortunately, the app was caught early and removed from the app store with a minimal number of total downloads.
Dark Web Hacker Steals Over 1 Billion User Accounts
With corporate hacking being more profitable than ever, it comes as no surprise to see dark web vendors selling data for millions of users. Recently however, one vendor has offered access to over 1 billion unique user accounts from some of China’s largest online vendors. Alongside the initial listing for the main Chinese accounts, the hacker also offers another ~46 million email accounts from varying domains.
How F5 is Changing the Application Security Game
To address the need for application security in the digital transformation era, F5 is releasing a new host of products and services.
“The digital transformation has really changed security as a whole,” says Preston Hogue, Director of Security Marketing and Competitive Intelligence. What he means is that everything—EVERYTHING—is moving to the cloud. Think about the companies from years ago, such as Blockbuster, versus their modern counterparts, like Netflix or Hulu. Think about the fact that most of today’s twenty-somethings have never set foot in a physical bank branch, but use online banking daily. Now think about the fact that every service I’ve mentioned so far has an application, which is the primary method of interaction for users.
The application is the new perimeter and identity is the key to that perimeter. Over 70% of all data breaches occur by accessing applications. At F5, we are focused on securing our customers’ applications; both by securing access to the apps, and by securing the apps themselves where they reside.
We spoke with Preston about the newest security products F5 is launching, and how they’re using Webroot BrightCloud® IP Reputation intelligence to help power their solutions.
Webroot: Tell us a little bit about the security launch. What should we expect to see?
Preston Hogue: First, we are launching a family of dedicated security products called Herculon. The first two components of the Herculon product family are the Herculon SSL Orchestrator and the Herculon DDoS Hybrid Defender. These products are dedicated to solving the challenges of SSL/TLS encrypted traffic and ensuring application availability.
Second, we’re announcing a new service called Silverline WAF Express, which will give customers easy, self-service access to our cutting-edge web application firewall. We’ve been deploying web application firewalls on premises for some time and also offer a fully managed service. Since some customers don’t have the time or resources to install and maintain the software, or maintain the racks and stack and everything within their environment, we’re giving them a simpler self-service experience.
Our focus on securing applications means our overall threat research is geared toward application threat intelligence—really trying to get to the root cause of the 70+% of data breaches I mentioned previously—so we’re also announcing increased investment in our F5 Labs threat intelligence team.
Last but not least, we’re also announcing that the services of our security incident response team (SIRT), a dedicated team of highly trained individuals within the support organization, are now available to all F5 customers around the world. This team will be the highest level of escalation for security and service response.
Since threat intelligence is such a huge component of your offerings, what should your target customers consider when choosing threat intelligence sources for themselves?
There are a lot of companies that offer threat intelligence, but it’s challenging because they all claim a kind of broad, generic expertise. We advise that customers look for specificity; for targeted, actionable information that pertains to what they’re trying to do. Looking at a company like Webroot, you’ve taken on very specific aspects of threat intelligence and you’ve been able to master those particular areas—like the Webroot IP reputation intelligence that we integrate.
We see a lot of organizations trying to take on too much. That’s why we’re very definitive about the scope of what we’re trying to accomplish, and why we focus on leveraging our application security expertise around threats and ensuring we can provide very specific, clear, actionable threat intelligence with F5 Labs.
What do you hope your customers will gain by implementing your solutions with Webroot BrightCloud IP Reputation intelligence?
We know we have the expertise when it comes to understanding the overall threat to an application. We partner with companies like Webroot for insight into a particular aspect of threats; in Webroot’s case, it’s insight into IP addresses and additional threat information around user agents and anonymous proxies. We’re very specific in our threat intelligence, and we know we’re not always able to show the entire picture on our own. So we are able to fill in other areas of the overall threat landscape through our partnerships to ensure that we can give our customers the full picture they need.
How do you see the F5 security launch changing the security industry?
F5 has been in application security for over 20 years. From what we’ve seen, digital transformation is changing security as a whole. It has driven applications out of the data center and into the cloud. That means there are 3.2 billion users on the internet, who all potentially have access to these applications, which makes them a big target for breaches. Because of our expertise within the field, F5 is in the perfect position to provide visibility into this threat landscape, and also the control our customers need to achieve a secure application experience.
In his closing comments, Hogue had the following to say, “To secure access to applications and to secure the apps where they reside, you need a complete picture of the threats that target apps. You need a team like F5, with an ecosystem of intelligence partners like Webroot to provide that picture. And that’s how, ultimately, we can help our customers solve today’s security challenges and keep users safe.”
Learn more about Webroot BrightCloud IP Reputation intelligence. Or, for more information about F5’s security launch, read the press release.
Cyber News Rundown: Edition 1/19/17
MongoDB Hacks Spreading Fast
In the past few weeks, researchers have been monitoring the steady rise of hacked MongoDB installations, now surpassing over 28,000 individual systems. While the attacks started with ransoming back the stolen data, the attackers have now begun simply deleting the information from the database and leaving the ransom note for payment anyways. With up to 12 different attackers as well, crossover hacks have occurred on several of the databases, leaving the victim unsure of who to contact or how to retrieve their missing data.
Miami Bank Loses Millions without Notice
Recently, a major Miami Beach bank has been under heavy scrutiny after nearly $4 million USD were stolen from their accounts without any suspicion arising. According to officials, the thefts began in the summer of 2016 and continued until December, when they were given a report showing a large number of fraudulent transactions taking place in the form of automatic billing payments that were being rerouted. Amidst the scandal, several prominent financial executives were forced to resign.
Amazon Phishing Scheme Targeting User Credentials
Users of retailing giant, Amazon, have noticed some oddly suspicious behavior when attempting to purchase items with prices that are too good to be true. Items being posted for sale the fraudulent merchant are available to purchase, until you add the item to your cart and begin checking out. Once in the cart, the item mysteriously disappears and a message stating that it is no long available appears. Users are then contacted by the vendor via email with a new link to purchase the item, though this link does not direct the user back to the legitimate Amazon site, but instead one that looks similar and wants your credentials badly.
Ukraine Power Stations Still the Focus of Cyber Attacks
It’s been almost exactly one year since the major power outages that affected nearly a quarter million Ukrainians, and once again, the hackers are up to their same tricks. In the last month, officials have been working to determine if the latest power substation failure was a legitimate failure or the results of another cyberattack. With the latter being confirmed, it is still surprising how little damage the hackers have actually done, with nothing more than overwriting the firmware used in the power stations to signal a manual reset to engineers on site. Researchers believe these attacks are merely a test of their capabilities and learning what security is in place and how to bypass it.
Spora Ransomware Offering New Encryption Process
With ransomware being the highest grossing cyber-attack vector, it’s no surprise that attackers are coming up with clever new methods for causing user devastation. By adding an additional encryption step, allowing for offline encryption, the attackers are able to create a new set of AES keys on the local machine which will stop decryptors from unlocking all of the victims with one private key. Additionally, Spora has the capability to gather information about the computer itself and determine an appropriate ransom amount, whether it’s for an individual user or a large corporate network.
Satan: A new ransomware-as-a-service
Ransomware as a Service (RaaS) has been growing steadily since it made its debut in 2015 with Tox. With the new Satan service, it’s easier than ever. The idea is to use this web portal to contract threat actors to create new ransomware samples for distribution via the desired attack vector. This allows any potential cybercriminal, regardless of their skill or coding knowledge, to upgrade to an encrypting ransomware business model.
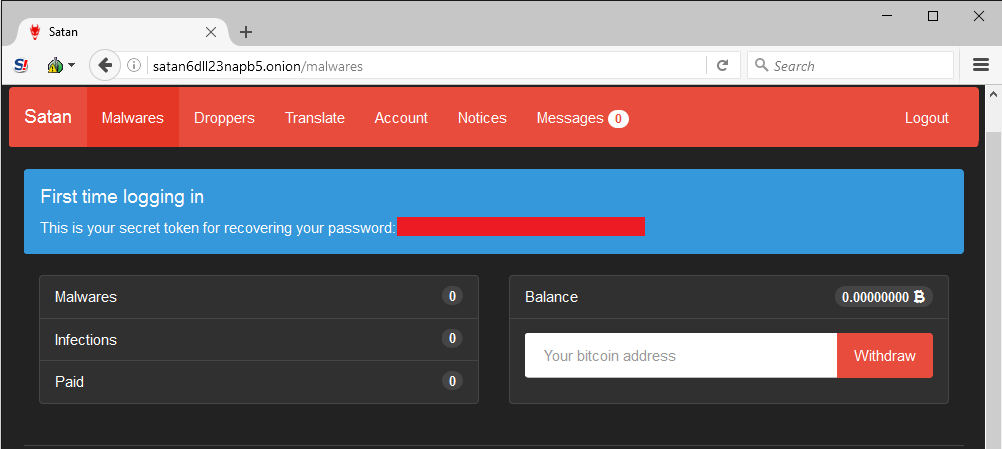
Those who join the program have a number of viewing options in the portal. The Account panel shows various stats, including how much money has been made, infection count, current share percentage, etc.
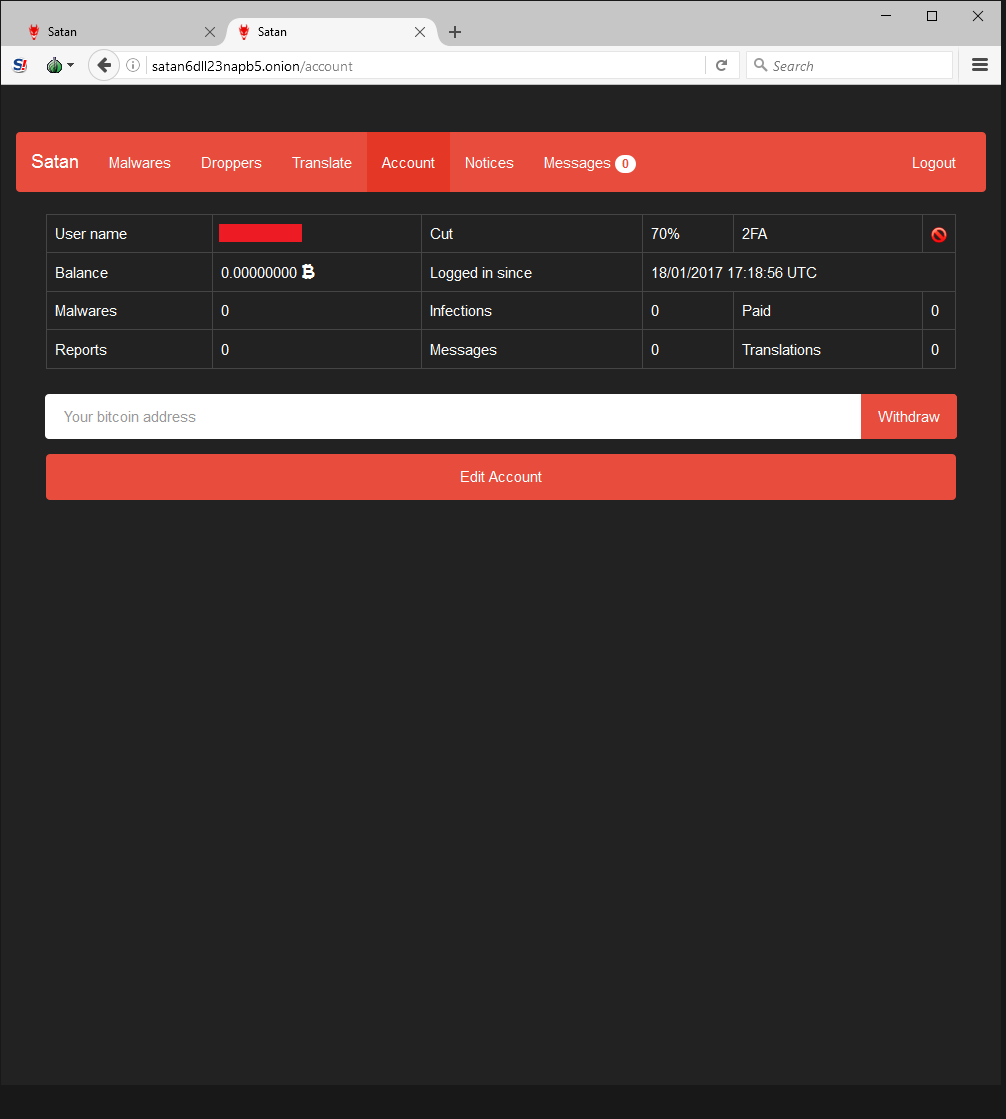
All a criminal needs to do is enter a few simple pieces of information to generate brand new malware that’s ready to infect victims. Note that the portal author specifically requests downloaded samples not be shared with VirusTotal, decreasing the likelihood that security vendors will have encountered the variant.
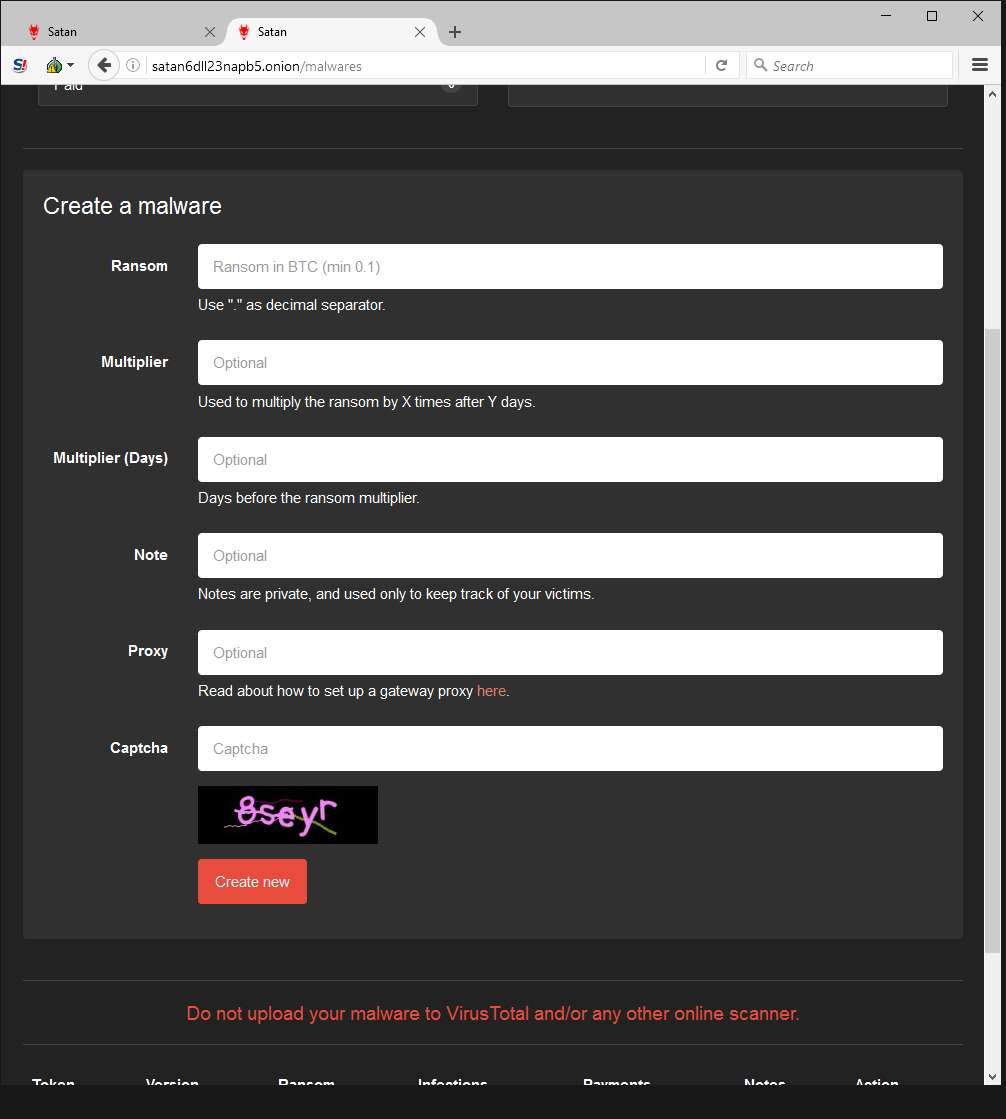
Since the darknet web portal creator takes a 30% cut of all ransoms, it’s in his best interests to make sure as many victims are infected as possible. He provides a guide with step-by-steps instructions on how to deploy malware using obfuscation techniques to avoid detection.
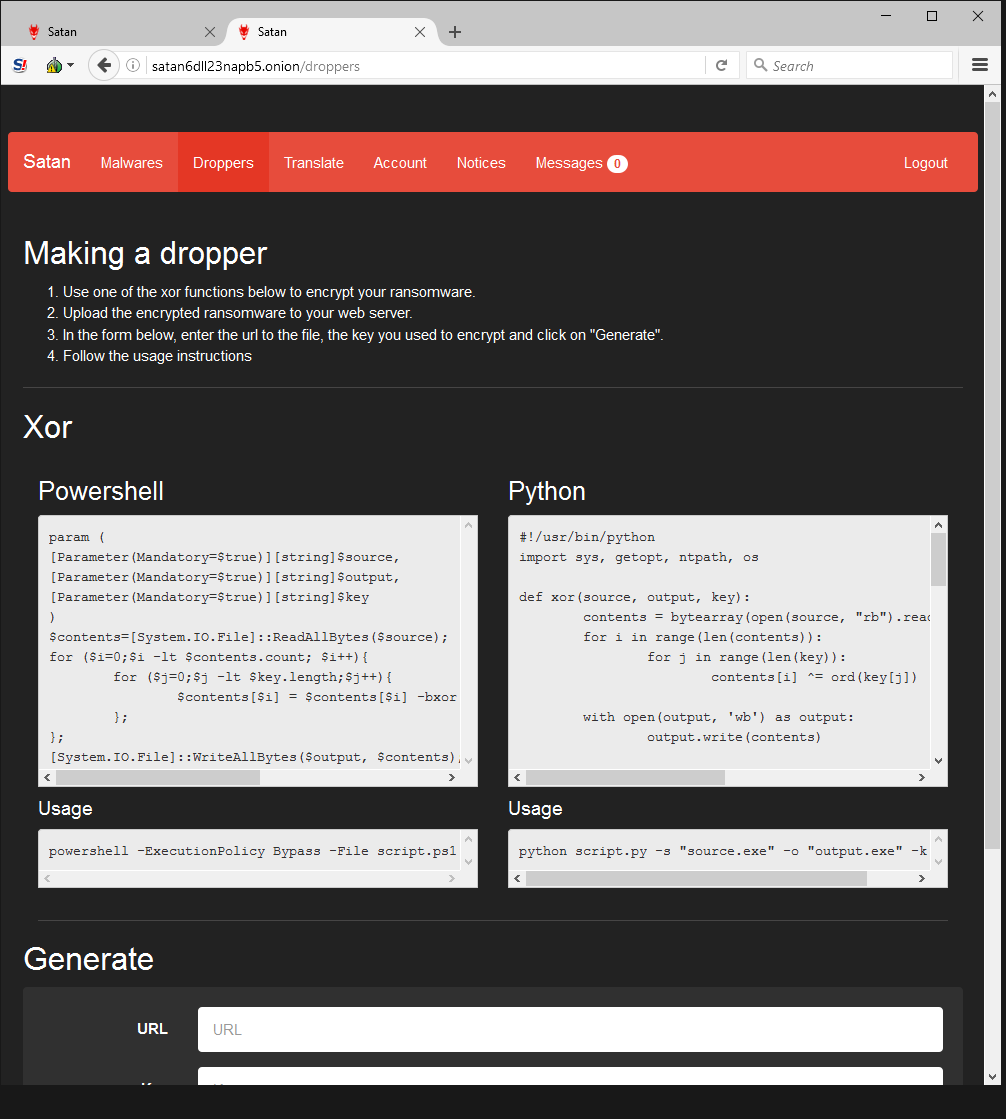
The author also advertises his web portal on underground forums, and explains the payload and the payout scheme. After all, affiliates’ success means he gets a bigger cut.
 Although Webroot will catch this specific variant of ransomware as a service in real time before any encryption takes place, don’t forget that the best protection in your anti-ransomware arsenal is a good backup solution. You can use a cloud service or offline external storage, but keeping it up to date is crucial for business continuity.
Although Webroot will catch this specific variant of ransomware as a service in real time before any encryption takes place, don’t forget that the best protection in your anti-ransomware arsenal is a good backup solution. You can use a cloud service or offline external storage, but keeping it up to date is crucial for business continuity.
For best practices for securing your environment against encrypting ransomware, see our community post.
Webroot named among the Best Software Products for IT Teams 2017
“Highest average score for ease of use, quality of support, and […] requirements in endpoint protection.” That’s how Marty Duffy, Director of Research at G2 Crowd, describes Webroot after seeing the results of this year’s G2 Crowd survey on Best Software for IT Teams 2017. We’d be lying if we said we weren’t over the moon.
Webroot Endpoint Protection’s users consistently commended the product in 2016. Mid-market users recognized the tool as a stand-out product to be used by IT teams. It received the highest average score for ease of use, quality of support, and meets requirements in endpoint protection (mid-market). – Marty Duffy, Director of Research, G2 Crowd
G2 Crowd is a peer-to-peer business software review platform. Since 2014, they’ve recognized the best software products based on reviews by professionals across numerous markets. Their awards are supported exclusively by actual user satisfaction ratings, not obscure testing methodologies or paid industry reviewers. This is important to us for a couple of reasons.
Integrity and Customer Focus
At Webroot, two of our core company values are integrity and customer focus. We believe in respect, honoring our commitments, and measuring our success by our customers’ success. Our strength as a company is defined by the people who trust us to protect their businesses, clients, homes, and families. We’re proud to repay their trust by giving them the best possible service.
Real-time Protection
Cybersecurity continues to be a topic that gets more groans than cheers. Most users, both at home and at work, consider cybersecurity to be a kind of necessary evil. Sure, it keeps you safe from malware and other attacks, but it can also slow down your computer and get in the way of your activities. But we’re in the business of changing people’s minds on the subject. We devised a smarter way to protect businesses and individuals in the connected world. Our cloud-based protection and threat intelligence stop threats using behavior and contextual data, without draining system resources. We eliminated the hassle of system-intensive updates. And when any Webroot-protected device encounters a new threat, every device connected to our advanced threat intelligence platform is protected in real time.
Being recognized for this award serves to underscore our commitments as we continue to grow and innovate throughout the coming year. And, hot on the heels of being named Most Customer Friendly Company of the Year, we’ve only got one more thing to say: Thank you!
See for yourself what all the fuss is about. Take a free 30-day trial of Webroot SecureAnywhere® Business Endpoint Protection today. It won’t conflict with your existing security, and only takes a few seconds to install.
Your 6-Step MSP Guide for Stopping Ransomware
While a lot of the hype around ransomware paints it as daunting and virtually impossible to combat, there are several very straightforward steps for managed service providers to dramatically reduce the risk that their clients’ will fall victim to ransomware.
-
Proven endpoint security backed by industry-leading threat intelligence.
Security shouldn’t just spot and quarantine threats that have already infiltrated a system. It should prevent threats from infecting the endpoint in the first place. Be sure to select a solution that protects web browsing in real time, secures system settings, controls outbound traffic, provides proactive anti-phishing, and continuously monitors and reports on individual endpoints.
-
Get your house in order with backup and business continuity.
If any of your clients do become ransomware victims, the only real course of action is to restore their data as quickly as possible to minimize business downtime. These days, there are a fair number of automated, on-premises and cloud-based business continuity solutions that will back up data and get your clients’ business back on track after a breach.
-
Implement strong Windows policies.
As part of your ransomware defense strategy, you can use Windows policies to block certain paths and file extensions from running. If you need varying levels of access, you can set up policies in groups. Some useful policies include blocking executables in temp or temp+appdata and the creation of startup entries. For instance, .SCR, .PIF, and .CPL file types should not be run in the following in users’ temp, program data, or desktop directories.
-
Block volume shadow copy service.
Windows uses the VSS copy service to create local copies of files. CryptoLocker and other ransomware variants will encrypt this area because it holds VSS copies for the local (C:) drive. By setting Windows policies to block access to the service, you can help stop ransomware like CryptoLocker from erasing local drive file backups. Make sure that policies point to the VSSAdmin executable. Attempts to access or stop the service will be blocked.
-
Get rid of macros and autorun.
Numerous kinds of ransomware use macros to infect systems, but you can easily disable them in the Trust Center of every version of Microsoft Office. You can also enable individual macros, if they’re necessary for a particular task, while disabling all others. Additionally, autorun might be a handy feature, but many types of malware use it to propagate. As an example, a USB stick uses autorun, but so do Visual Basic Script (VBS) malware and worms. As a general rule, we recommend disabling autorun.
-
Keep clients in the know about ransomware.
It’s no secret that human error is a large part of successful cybercrime. As long as staff members remain relatively unaware and undereducated about the risks of the internet, malware will continue to be a viable business. Make sure clients understand the basics and what to watch out for so they stay safe both at home and in the office.
The first step to securing endpoints against ransomware is deploying a next-generation security solution. Take a free 30-day Webroot trial, no risk, no obligation to buy. In less than five minutes you can install Webroot SecureAnywhere® Business Endpoint Protection with Global Site Manager and see first-hand how it delivers superior malware protection while lowering your costs and boosting your bottom line—without conflicting with your existing security.
Cyber News Rundown: Edition 1/6/17
FireCrypt Ransomware Builder Found in Wild
Researchers have discovered a new ransomware variant that uses “.firecrypt” as its amended extension once encryption has taken place. FireCrypt is compiled using a command line builder software that allows varying inputs and outputs to be determined by the author for a unique hash, as this allows for better disguise by enabling the author to change the icon and executable name. Along with the usual encryption, FireCrypt also connects to the Pakistan Telecom Authority website and begins downloading all of the available content, thus filling the victims hard drive with thousands of junk files.
Los Angeles College Hit with Cyberattack
While many students are preparing to return to classes after their winter break, employees at Los Angeles Valley College are working to determine the severity of a cyberattack. It is still unclear how the systems were breached or to what extent any sensitive information has been access, though officials are working with law enforcement.
Philippine Army Website Vandalized By Hackers
In the past week, the official Philippine Army website was compromised by a hacker going by the alias, Shin0bi H4x0r. The site itself displayed several messages to any visitors, boasting about the weak security and taunting the site admins. Though the site has since been taken offline, it is still undecided how the site was breached.
Experts Doubtful of Russia’s Part in Recent Hacking
With so many recent stories surrounding Russia’s involvement with the recent utility grid breach in Vermont and the implied connection to the hacks that took place during the election, many security researchers are unsure how involved Russia actually is. Flaws found in the US utility services are not a secret, and officials have been working to resolve them for quite some time. While public outcry over Russia hacking the election has been very pro-America, it stands as a bit hypocritical, as the US is assuredly involved in similar tactics all across the globe.
Malicious Super Mario Run Apps Found on Android
While Super Mario Run was released for iOS in the early part of December, it has yet to hit the official Android app store for sale. Due to the release gap, many cybercriminals have been cashing in by creating at least 9,000 known malicious versions of the app and distributing them through third-party app stores. Users are warned to avoid downloading any Super Mario Run-related apps until the official version has been released by Nintendo on the Google Play Store.
Four Rising Stars on the Ransomware Stage
By now, everybody has probably heard of CryptoLocker. It makes sense that CryptoLocker would get a fair amount of media attention, since it’s been involved in several high-profile hacks, but there are a number of other players on the ransomware stage that deserve a place of distinction among the list of players. Managed service providers (MSPs) like you know the value of staying up to date on the variety of different types of threats—in addition to their individual stats and characteristics—to keep clients safe.
Cast of Ransomare Players
-
CryptoWall 4.0
A bit like the Barrymores, the Sheens, the Coppolas, (the Kardashians?), the CryptoWall family gets more media coverage with every generation. Following in the family tradition, CryptoWall 4.0 uses phishing emails for distribution. This is hardly a surprise, since phishing is still the single most effective way to drop a malware payload. But CryptoWall 4.0 marches to the beat of its own drum; not only are the victim’s files encrypted, this ransomware randomizes the filenames so the victim can no longer tell which file is which. By fanning the flames to create confusion around how much file damage there actually is, the new CryptoWall increases its chances that victims will pay up.
Additionally, CryptoWall 4.0 includes a free decrypt video to convince victims that the decryption steps they need to get their files back is effortless, and that handing over the ransom will get them their files back.
- Phishing email attachment is source of payload
- Randomizes victim’s filenames to create confusion
- Offers free decrypt demo to add credibility
-
PadCrypt
Rather than hiding out and concealing its plans, what makes PadCrypt different from its contemporaries is its willingness to interact with the public. Embedded into the “product”, PadCrypt includes a chat interface. The ransom process of setting up a Bitcoin wallet, filling it with bitcoins, and sending payment can be complicated. By offering this chat feature, PadCrypt lends a more human support element to the ransomware process, providing so-called support to its victims. (How sweet!)
- First ransomware with chat support
- Communicates via Darknet to avoid being traced
- “Helps” even less savvy victims pay up
-
TeslaCrypt
Because it targeted gamers specifically and encrypted the files they need for their games, TeslaCrypt is more of what you’d call a cult fave. The files it takes hostage included saves, mods, and profiles. But since TeslaCrypt was being sold by non-authors on the Darknet, the original authors leaked the master decryption key to the public to permanently diffuse the threat. While it’s laying low for now, we wouldn’t be surprised if TeslaCrypt showed up again next season.
- Accounted for ~11% of distributed ransomware
- Attacked over 200 extensions on newer variants
- Targeted gamers (Valve, Bethesda, Unreal Engine files)
- Circumvented 3rd party defense to deliver polymorphic payloads at root level
-
RaaS (Ransomware-as-a-Service)
Not an actor, per se, but RaaS is more like a local theater company that encourages audience participation. Created for criminals by criminals, it opens up the ransomware stage to hackers of all skill levels. Thanks to RaaS, almost anyone can distribute encrypting ransomware payloads of their own design. In return, hackers pay for the service by sharing a cut of their spoils with the original author.
- Enables almost anyone to make ransomware
- Portal for malware generation is exclusively in Darknet (typically invite-only)
- Intended for less-skilled cybercriminals who rent botnets
- The malware author who created the portal takes a commission
Conclusion
Even though the number of ransomware stars keeps growing, and their methods keep getting more diverse and advanced, managed service providers (MSPs) can take steps to maximize defense and help clients stay ahead. Keeping yourself and your customers in the know about the latest tactics and types of exploits favored by today’s ransomware is vital—as well as putting together an all-star cast with next-generation endpoint protection that utilizes collective threat intelligence to proactively protect against the rising stars of malware.
Next Steps: Want to find out if Webroot has what it takes to protect your customers? See for yourself with a no-risk FREE trial. You don’t even have to uninstall existing security. Want to learn more about how Webroot partners with MSPs to delight customers, lower costs, and boost profits? Learn more.
5 Totally Achievable Resolutions
If you’re anything like me, you probably make a bunch of lofty resolutions every year that you probably won’t, or even can’t, achieve. (For instance, I’ve been promising to hit the gym a little harder for about 6 years now.)
But enough is enough. Here are 5 completely achievable resolutions to help keep you and your identity safe in the New Year. Best of all, they’re not too hard and don’t take long, so you get the satisfaction of checking things off your list right away!
1. Layer Your Wi-Fi Security
Remember over the holidays, when you had to read your super long and complicated router password to everyone in your family so they could connect to the Wi-Fi? Wouldn’t it have been great if they’d taken a seat and listened all at once so you wouldn’t have to repeat it 50 times in between trips to the kitchen to baste your bird or check a timer? Wouldn’t it be even better if you could have your own guest network with a friendly password that the whole family can remember?
Well… you can.
These days, continuing technological advances have given most routers dual-band technology. The “dual” part means you have a 5 GHz band for devices that are centrally located and more or less stationary near your router, giving you the best possible speeds, while there’s a 2.4 GHz connection for devices that are more mobile and need a longer range.
If you activate Guest Networking for both your 5GHz and 2.4GHz bands within your router’s settings, you can create separate passwords for residents and guests. That way, you can manage who gets access to your secure network, and then your connection won’t get bogged down the next time you want to stream the football game while your 3-year-old niece is glued to the Disney Holiday Special.
Be sure to enable WPA2 security on both networks to protect your houseguests and to keep holiday opportunists from leeching off of your connection.
2. Enable Biometric Screening or a PIN on your New Device
Did you get a new toy over the holidays? Make sure to enable two-factor authentication and either a security PIN or biometric access to your devices whenever possible. Although it might add another second or two to the time it takes to unlock your devices, it’ll be worth it when you realize your mom won’t casually stumble across those pictures from so-and-so’s bachelor/ette party.
3. Avoid Opening Emails On the Go
This one might be the easiest of all, and a lot of recent studies have suggested that ignoring your email a bit more often can have incredible benefits for your stress levels and overall mental health. And, let’s face it, who couldn’t use a little help de-stressing after the holidays?
Unsecured Wi-Fi in coffee shops and the like is a prime spot for cybercriminals to take advantage. If you absolutely have to open your emails while you’re out and about, we recommend staying connected to your mobile data plan. And if you’re worried about data rates, try to wait until you’re connected to a secure Wi-Fi network that you trust, and one that you know has encryption in place. Besides, if you really take stock of it all, those emails can probably wait.
4. Activate Automatic Updates
You’d be amazed how many breaches could be avoided by keeping software/firmware up to date. Hackers often exploit known vulnerabilities that companies like Adobe and Microsoft have already patched or are close to patching, figuring that the numbers game will still come out in their favor. After all, there are a lot of people out there who ignore updates or may not realize how important they can be. If you don’t have time to stay on top of every update, enabling automatic updates on your devices is an easy way to close the window of opportunity for cyber thieves and other hackers.
5. Install a Unified Threat Management Appliance (UTM)
Think of a UTM as a souped-up firewall. The average family has at least 4 connected devices in their home, and many have more than double that amount. For larger families, not to mention people who run a business from their home, a Unified Threat Management appliance will add another layer of network protection for your highly connected gateway.
In all seriousness, you could probably complete most—if not all—of these tasks in the span of a Sunday afternoon, and they could save you from spending countless hours on the phone with banks and creditors as you try to retrieve a stolen identity or dispute fraudulent charges. How many of your other resolutions have that going for them?
So what are you waiting for? Take the initiative in 2017 and follow these tips to protect your family, your home, your identity, and your privacy from modern cyberattacks.