Cyber News Rundown: Edition 12/2/16
Between a handful of high profile network hacks and the steady stream of ransomware attacks, the last week of November didn’t pull any punches in the constant sparring match that is cybersecurity. In the wake of headlines about a US Navy breach, large scale network outages across Germany, and more, internet users across the globe must stay watchful and wary of their next click.
US Navy Sees Massive System Compromise
Officials in the US Navy have been notified of a security breach stemming from a Hewlett Packard Enterprise contractor whose laptop had been compromised. Currently, the Navy is contacting those who may be a part of the nearly 140,000 names and social security numbers that were affected, though it is still unclear on exactly how the breach occurred. With the steady rise in cyberattacks, the stress on IT departments of all sizes is mounting to defend against future attacks.
Tech Support Scammers Using Ransomware to Boost Income
Researchers have discovered an unsettling evolution to the traditional cold-calling tech support scams: executing ransomware on their victims’ computers to ensure payment for their “cleaning services”. While typical scammers will attempt nearly anything to get personal information, the use of ransomware takes the threat one step further by maliciously forcing payment regardless of any services rendered. Even worse for victims of VindowsLocker—as the ransomware is dubbed–the authors failed to properly setup the ransom transactions and thus, users may be unable to regain their files even if the ransom is paid.
UK National Lottery User Accounts Hacked
Major website hacks are occurring regularly due to reused login credentials, and it’s still a shock when a large site operator has to begin notifying tens of thousands of users about a possible data breach. Now we’re adding the UK National Lottery to the list. Only a small fraction of the National Lottery’s users were compromised, but Camelot, the operator for the lottery, has been forcing password resets for any potentially compromised individuals. While password re-use is the likely cause of the breach, it is still uncertain why the Lottery didn’t offer any additional authentication prior to the user accounts that were taken over.
San Francisco Train System Brought Down By Ransomware
In recent days, it has been discovered that the San Francisco Municipal Transit Agency was taken offline with only a poorly worded ransom message displaying for customers and employees alike. The attack led to the SFMTA providing free rides to customers while the issue was being resolved. In a surprising stance, the excessive ransom demanded–100 bitcoins totaling over $70,000 USD—was not paid to the attackers. For many public utilities and services, having the capability to promptly return to normal functions after such an attack is extremely important, and fortunately the SFMTA have announced that no customer information was compromised.
German Telecom Provider Hit with Mirai Variant
There is no doubt the world is now more attentive after the last Mirai botnet attack that took down several prominent sites. Yet, a similar variant has been deployed keeping DSL customers in Germany disconnected. Recently, nearly 900,000 telecom customers have been unable to access anything reliant on their DSL routers, which have been under attack for several days. By scanning for commonly open ports on routers, the attackers are able to remotely execute code resulting in a widespread DDoS attack.
Top 10 Most Infected States
The sheer number of cyberattacks lately led us to this question: which states are at the greatest risk of a cyberattack? Naturally, we took it a step further. We looked into data on population and population density in an effort to find correlations.

Which are the most infected states?
Opening up our list in the top three spots are California, Texas, and Florida. These three states were both the top three most populated and the top three most infected. This immediately led us to some questions: is the only correlation between states and the number of infections population? Based on these top three, that might be a safe guess.
Pulling up the rear of the top 10 are North Carolina and Wisconsin. North Carolina held strong at #9 for the Census’ most populated state and as Webroot’s 9th most infected state. The only major difference we noted is the fact that Wisconsin made it onto the list of the most infected states, while Georgia, 8th for most populous, doesn’t even rank.
Wait a second, Georgia doesn’t even rank? For the record, Wisconsin is the 21st most populous state, which puts them way outside the range of the top 10. What’s even more surprising about this discrepancy is that Georgia’s population is at 10,214,860 and Wisconsin’s is about half that at 5,771,337.
So, I think that safely puts our “more people equals more infections” theory to bed.
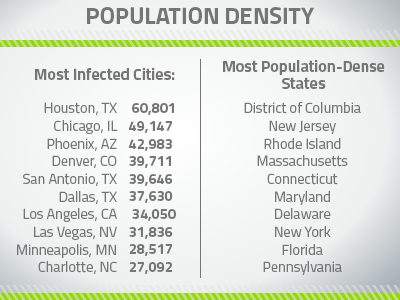
How do the most infected cities stack up?
The most infected cities in the U.S. compared to a list of the most populous cities proved even more surprising. Since we noticed that there wasn’t a strong correlation at the state level, we wondered about the city level instead, and took a side-by-side analysis of the most infected cities and most population dense areas of the U.S.
The first thing we noticed in the above is how little correlation there seems to be between population density and the number of infected devices in the city, which we expected would have some impact. In fact, a quick glance at the list shows that none of the most infected cities are in any of the most population-dense states.
Additionally, even though Texas is 2nd on our list of most-infected states, it has its infections more localized in its larger cities. As a point of comparison, consider that NYC is one of the most population-dense cities in the U.S., but it conversely doesn’t even make it into the top ten for the number of infected devices.
Another example of an apparent contradiction to our hypothesis is that Arizona, which doesn’t even make it into the top ten for most infected devices or for population, but look how many infected devices reside in Phoenix:
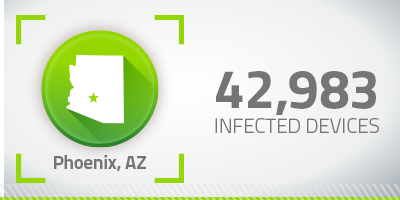
Although Phoenix is right behind Chicago and Houston in the number of infected devices, it’s a significantly smaller city. The same goes for Denver. Even though Colorado is at #23 for population and infected devices, Denver itself nonetheless makes its way into our top ten. Maybe Webroot users have some hometown pride?
Cybercriminals have no geographical bias. Whether you live in a big city or small town, east or west coast, you’re susceptible to being a victim of cybercrime. Protect yourself with award-winning security.
RDP Attacks: What You Need to Know and How to Protect Yourself
For many years now, Microsoft has offered a system with Windows that allows you to take control of another machine. This has been invaluable for system admins that need to control servers and other Windows machines, without having to run around from office to office or site to site. Easy takeover of machines does come with risks. The protocol known as Remote Desktop Protocol (RDP) and the Remote Desktop Connection software that relies on it are often victims of simple attacks. These attacks have been on the rise in recent years and are extremely popular at the moment, as they are enticing for cyber criminals that seek to compromise the admins and machines that control whole organizations.
How is Remote Desktop Protocol a security risk?
RDP often uses a particular port that is easy to locate in a scan. And unfortunately, the default account username for an admin is often Administrator. While it’s no secret that having a poor password policy is not ideal for server security, it’s worth reiterating here it can mean that hackers can try huge amounts of passwords before anyone is alerted or an account is locked out.
Once an intruder gets admin access, they can deliver specialized malware or remote access tools that can often be almost impossible for any security solution to detect. With admin privileges and route access to the desktop, maximum damage can be done. This stresses the importance of endpoint protection, as well as policies, monitoring, logging, backups and incident response.
How to protect & secure your organization from Remote Desktop attacks
Preventing such brute force attacks isn’t as complicated as it may seem. You can employ a few easy actions to keep your organization safe:
Prevent scanning for an open port
- Change default RDP port from 3389 to another unused port
- Block RDP (port 3389) via firewall
- Restrict RDP to a whitelisted IP range
Prevent attackers from gaining access if RDP is enabled
- Create a Group Policy Object (GPO) to enforce strong password policy (GPOs are important and should be common practice for your organization)
Optional
- Require two-factor authentication
Getting to the bottom of suspicious activity is vitally important and our team is here to help. Contact us today or learn more about our full suite of business cybersecurity solutions.
Cyber News Rundown: Edition 11/18/16
Alarming Number of Sites Still Using SHA-1 Certificates
The January deadline for switching over to SHA-2 rapidly approaching. For the vendors that are still lagging behind, they will begin to see browser warnings to their customers stating the site is untrustworthy for processing sensitive information. Surprisingly, 1/3 of all worldwide sites are still using the insecure algorithm. Unfortunately for many of these vendors, switching to SHA-2 could take quite a bit of work, as they have to locate and identify their current SHA-1 certificates before the migration can start.
PoisonTap Tool Navigates Around Password-Protected Computers
Recently, a new tool has been making its name by allowing an attacker to gain access to a computer, even while locked, by simply plugging in a malicious USB. The tool, dubbed PoisonTap, gains access to any unencrypted internet traffic and captures cookies used to login to sensitive accounts. Once the information is captured, the tool installs a backdoor to allow the attacker further access to the computer, then transfers all data back to the attacker’s server.
Ransomware Steps Up Blackmailing Methods
Ransomware is still on a steady path of destruction, and one variant has gone the extra step to better ensure the ransom gets paid. By scanning the system for any trace of child exploitation or pirated content, the ransomware is able to display a directed warning message about any files found that it could then expose to the public. By threatening the user with releasing any incriminating files, the attackers hope for a higher number of victims paying the ransom, as it now holds leverage against the payment.
Adult Friend Finder Hack, Possibly Largest Ever
Recently, the adult dating site Adult Friend Finder, and its network of other sites, has fallen victim to one of the biggest data hacks on record. With nearly 412 million users accounts compromised, the network’s security is coming under scrutiny as nearly a third of the passwords found were stored as plain text files or relied on the long-outdated SHA-1 algorithm. Even more worrying, many of the passwords appear to be extremely simple words or number sequences that are likely being re-used alongside the same email address for other websites.
Corporation Chains Hit with Customer Service Malware Attack
In the past few weeks, many vendors have complained about receiving fake customer service emails that contain malicious attachments. These attacks begin by impersonating a customer trying to provide sensitive information via email, and coercing the company representative into opening said attachment. Once opened, the malware begins downloading additional tools for collecting and transferring sensitive information back to the attackers. This method of stealing consumer data is not new, but the approach of remaining on the phone for the duration of the attack is something few researchers have seen before.
Cyber News Rundown: Edition 11/11/2016
Your online identity is at risk now more than ever. This week’s cyber news update covers the growing threat of online banking attacks and phishing scams across the globe.
Tesco Bank Hacked For Millions
Tesco’s banking services released a statement earlier this week announcing that several thousand bank accounts had been hacked, resulting in the theft of nearly $3 million USD. At present, this attack is the largest hack to target a western bank. While Tesco Bank is still looking into the breach, they have already compensated customers whose accounts were affected, and have stated that no confidential customer information was exposed.
Google Safe Browsing Gets More Persistent
Ever since Google launched Safe Browsing over a decade ago, hundreds of millions of users have been prevented from being drawn into malicious websites through fake warning notifications. With the latest updates to Google’s security policies, Google will show additional full-page warnings for any offenders who violate policies repeatedly until the site can be verified. With the addition of the Repeat Offenders policy, sites that attempt to use any coverage gap to revert to harmful activity after the safety verification will be shut down for a period of 30 days.
TrickBot Banking Trojan Spreading Rapidly
A new trojan has risen and is targeting banking customers across the globe. Having started in the UK and spread into continental Europe, TrickBot uses redirection attacks and server-side injection to compromise user login credentials. Using spam emails as their delivery method, attackers have been able to hit a wider range of victims with a very high success rate.
PlayStation Hacks Target UK Gamers
Recently, dozens of PlayStation Network users have reported their accounts had been compromised and used to make fraudulent charges. While it is still unclear how the accounts are being compromised, it likely stems from reusing passwords, or possibly another Sony breach. Due to the increase in attacks, Sony recently released two-factor authentication to provide enhanced security for its users.
Nigerian Prince Scammers Upping Their Tactics
In the early days of the internet and email, scammers took advantage of ignorant users by pretending to be someone of great importance who simply needed help transferring funds. Today, these types of scammers have evolved their strategy by targeting victim computers and stealing login credentials to sensitive sites. Another change in their strategy has been to focus on big businesses, rather than individual consumers, to increase profitability.
Cyber News Rundown: Edition 11/4/2016
Computer safety has never been more of a necessity, regardless of your location in the world. This week’s cyber news recap spans from Western Europe to Australia, with a variety of threats that everyday users may face themselves.
UK Hospital System Hit with Malware
In the last few days, a hospital network in the UK was infected with what is likely ransomware. This incident has lead officials of the affected hospitals to temporarily shut down all hospital operations until the infection is isolated and removed. While current patients will still receive care, all emergency cases are being transferred to other area locations. It comes as no surprise to see yet another hospital fall victim to cybercriminals due to the lack due to lack of security that’s systematic across the industry.
Flash Player Android App Actually Banking Trojan
Recently, many smartphone users may have noticed an increase in popups requesting payment card information. While initially unsuspecting, upon installation, the app will request administrative rights for the device and begin gathering data from over 90 different banking apps and other social media apps. Consumers using third-party app stores should be extremely cautious as the trojan uses fake overlays to appear as a legitimate application.
Converse Online Store Hacked
In the weeks following the largest data breach in Australia’s history, the country’s online retail site for Converse shoes was hacked. The prime target was payment card information, as is the norm for many of the recent online-retailer cyberattacks. However, the figures for any compromised information are still unknown. Fortunately for any customers that made purchases during that period of time, the site was able to remediate the incident quickly.
CEO Phishing Scam Targets New Zealand Nurses
With email scams always changing and evolving, the weakest point in an organization’s security is still the employees. Earlier in the week, an email coming from the alleged CEO of the New Zealand Nurses Organization requested the email addresses of all 47,000 employees. The recipient swiftly responded with the full list. Unfortunately for the victim, the email wasn’t from a legitimate source or even a company email domain, as the sender was noted to be a Yahoo address.
Google Discloses Windows Vulnerability, Receives Backlash from Microsoft
In the past week, Google released information regarding a zero-day vulnerability in a Windows OS kernel that was actively being exploited in the wild. After disclosing the information to Microsoft to get the issue resolved, they announced a simplified statement about the vulnerability. As some might suspect, Microsoft took offense as they require a more unified public disclosure. Microsoft has also announced a coordinated effort with Google and Adobe to mitigate any negative outcomes of the recent exploits and that a patch will be released in the coming days.
Cyber Threat Halloween Prank
Happy Halloween! To commemorate this annual night of fright, our team wanted to accentuate the unpredictability of cyber threats. What they came up with was not only funny and entertaining, but also serves as a reminder to stay vigilant when online.
This Halloween and beyond, remember these sage words of advice. Files that used to be benign can turn malicious over time. An email from your closest friend could be phishing in the end. This Halloween, use common sense. Defend yourself with confidence. Before you go to trick or treat, get protection that can’t be beat.
Cyber News Rundown: Edition 10/28/2016
Fake BSOD Lock Screens Popping Up Again
In a nod to screen-locking malware from past years, a new variant has arrived that now requests a simple call to support for assistance. Rather than demand a ransom to remove the fake screen, it provides a number to a fake tech support line and suggests calling them. Fortunately for many users of Windows 8.1 or higher, the malware is disguised as Microsoft Security Essentials, a security software bundle that was removed and replaced by Windows Defender after Windows 7, which would be suspicious to see on any newer OS.
Surprising Value of Personal Records
The value placed on compromised data has a varied range with cyberattacks becoming the norm in many highly lucrative industries. Due to the high return on investment of financial records, they draw some of the highest price tags—$14 to $25 per record. However, data that may take more effort or time to analyze, such as medical records, can demand only a fraction of that for the sensitive information contained within. Because the medical industry is so low-tech in terms of securing patient information, they are a prime target for attacks, as we have seen in recent months.
Adobe Pushes Emergency Patch after Flaw Exploited
Recently, Adobe Systems was forced to issue an emergency patch to stop a flaw that could allow unauthorized code execution through Flash Player. The move came after reports of the vulnerability being exploited were announced. For most users, simply ensuring they are on the latest versions of any Adobe products in use will protect them from this vulnerability. Additionally, many users who have Flash Player through their browser will have the update installed automatically.
Ontario Schools Hit with DDoS Attack
In the same week as the major DDoS attack that affected the East Coast of the US, students preparing for their Grade 10 literacy test were unable to write the exam as the district’s computer systems were targeted with a similar attack. With this year’s exam being the pilot for future online testing, it was a major setback for officials looking to determine its viability, but also a disappointment for students who had been working hard in preparation for the test.
Russian Cybercriminals Taking Bank Attacks Worldwide
After spending the last couple years attacking local banks with cyberattacks, Russian criminals are now expanding their successful attack techniques to other countries. The largest factor contributing to this expansion is likely the value of the Ruble to other international currencies, as local attacks net a lower profit than foreign attacks on countries with a stronger currency. While the group behind the attacks is still unknown, it is likely they are spread through various countries to avoid detection.
DDoS attack on Dyn cripples the internet
A portion of the internet went down after suffering a crippling blow from a series of global attacks on a cloud-based Internet Performance Management (IPM) company, called Dyn. Major websites including Twitter, Reddit, Spotify and even game servers for Battle Field 1 have been affected.
This was all made possible by an unknown group of malicious actors that targeted a DDoS attack on a company called Dyn. Dyn provides an internet DNS system which allows users to connect to websites by routing a human readable internet address to their corresponding IP addresses. For example, http://webroot.com becomes: 66.35.53.194.
Dyn was being overloaded by requests from tens of millions of IP addresses all at once, causing their service to go down. Imagine a one-lane highway designed to handle the traffic flow of about 100 cars per hour. Then imagine that the same highway was suddenly riddled with over 10,000 cars. This would cause a bottleneck so severe, that the traffic would just stop. That’s essentially what happened Friday morning with Dyn.
The internet is a superhighway with destinations to a number of IP addresses rather than the actual domains of the websites. The issue is that there has to be a record of what websites and domains translate to what IP addresses. A Top Level Domain (TLD) provides that service, and they are the answer to the question of which name belongs to each IP address.
In this case, it’s been confirmed that an Internet of Things botnet, called Mirai, has been identified as a participant in the well planned and sophisticated attacks. The motive for this attack is only being speculated, given that the actual actors for the attacks have not yet surfaced or explained their intent.
Dyn has released an update on the DDoS event here, and you can subscribe for real-time updates on the status of the attack.
Cyber News Rundown: Edition 10/21/2016
DDoS Attack on Dyn Crippled the Internet
A portion of the internet went down after suffering a crippling blow from a series of global attacks on a cloud-based Internet Performance Management (IPM) company, called Dyn. Major websites including Twitter, Reddit, Spotify and even game servers for Battle Field 1 have been affected.
Malware Using Trump’s Name to Entice Users
With the election swiftly approaching, have you started to see an influx in Donald Trump-themed articles and email spam lately? Beware! Malware authors are in full swing creating threats aimed solely to infect users. They are counting on the polarized emotions to leave users disarmed. Take caution this election season and stay safe online.
School District Has Data Breach via Third-Party Vendor
The value of data is remaining higher than ever, and compulsory schools are finding out the hard way. Recently, a third-party data management vendor used by Katy ISD in Katy, TX, was exposed. The vendor in question, SunGard K-12, considers the incident low risk. Fortunately for the students and their families, the data breach was quickly noticed.
Axis Bank Discovers Unknown Login on Internal Servers
In yet another announcement of a bank becoming a victim of cybercrime, Axis Bank in India has made an official claim to the Royal Bank of India that its servers were compromised. Since the discovery, Axis has launched a full investigation, which has reported no unauthorized monetary transfers or signs of customer data loss.
Android Malware Still Affecting Non-Updated Users
In the past few weeks, the Android Trojan known as Ghost Push has continued to spread across older versions of the Android OS. By rooting itself to a device, the trojan is exceedingly difficult to remove, as even a factory reset will prove unhelpful. By displaying a steady stream of ads, the creators are able to profit from the clicks generated. There is a solution–upgrading your device to either Android 6.0 or 7.0 will stop the malware from propagating, as it is unable to root either of these operating systems.
CryPy Ransomware Using Python-Based Encryption
Ransomware authors have taken to new methods of targeting users and improving their profit odds. A a new variant called CryPy ransomware—written using Python—is being used to retrieve multiple RSA key tokens and encrypt a variety of files while allowing some “free” unlocks to the user. I wouldn’t say this is particularly useful, but being able to unlock specific files gives the victim a feeling of hope to recover the remaining and may increase the chances of the ransom being paid.
Threat Recap: Week of October 10th
French TV Network Brought Down By Hacker Group
Earlier this year, it was reported that TV5Monde fell victim to a cyberattack that nearly caused the demise of the network. Rather than gain access to retrieve sensitive information, the attack was aimed at simply destroying any and all network systems. While the reasoning behind the attack is still unknown, it has allowed TV5 to greatly improve its employee security measures and methods for operating safely.
Card Breach at Vera Bradley Retail Stores
Recently, Vera Bradley issued a statement regarding a card-processing breach that occurred over the past several months. The company has since resolved the breach but is still urging customers to monitor their credit card accounts for any fraudulent charges. Currently, only three stores located around Detroit seem to have been affected.
Amazon Pushes out Password Resets for Millions
In the past week, Amazon has started forcing password resets to customers that may have reused their credentials on possibly compromised sites. Along with changing passwords, users are also encouraged to enable two-step authentication to further protect their accounts. While the data leaks aren’t directly related to Amazon’s customers, researchers from Amazon have determined that credentials may have been used for multiple sites.
Ransomware Now Displaying Legal Notice for Victims
In the last month, the new ransomware variant DXXD has been hitting a large number of users. DXXD has made a change in that it displays the ransom note and a legal notification prior to users logging into their windows machine. The legal note explains that the user’s information has been compromised and gives multiple ways to contact the attackers to resolve the encryption.
UK Police Websites Susceptible to Attacks
Nearly 25% of UK police related sites have no form of secure connection according to a recent study. Even more troublesome, the majority of these sites ask for user information to identify case information without ensuring a properly secured network connection or encryption when transferring sensitive data. While many municipalities have improved their online security measures, it’s surprising to see so many still lacking, with new data breaches occurring almost weekly.
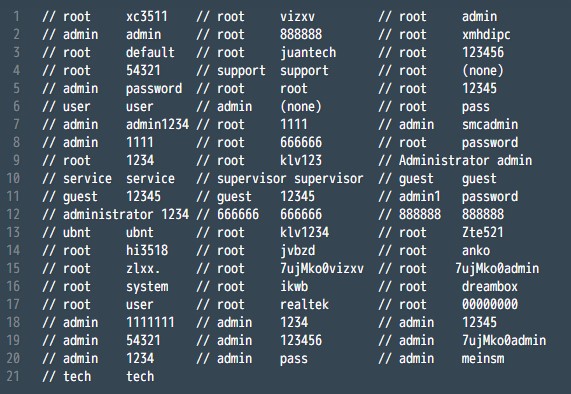
Source Code for Mirai IoT Malware Released
Recently, source code for the Internet of Things (IoT) botnet malware, Mirai, was released on hack forums. This type of malware was used last month in an historic distributed-denial-of-service (DDoS) attack against KrebsOnSecurity, which was estimated to have sent 650 gigabits per second of traffic from unsecured routers, IP cameras, DVRs and more to shut down the domain. Thanks to DDoS prevention measures by engineers at Akamai, the company protecting Krebs, the attack was unsuccessful; however, they report that this attack was nearly double the size of the largest one they’d previously seen.
Now that this malware is released publicly, we can expect to see more DDOS attacks coming from botnets such as unsecured routers and other IoT devices. For those wondering who would leave the default firmware username and password on their devices, the answer is “millions of people.” In fact, using Telnet alone (TCP/IP protocol for remote access), Mirai-author, Anna-senpai, reported “I usually pull max 380k bots.” It’s worth noting that many are saying Mirai wasn’t the only malware variant involved in the attack. Level 3 Communications reported that the Bashlight botnet may have played a part, as well.
How the Mirai attack worked
Mirai continuously scans the internet for IoT devices and logs into them using the factory default or hard-coded usernames and passwords.
Once infected, the devices connect to command and control servers to gather details of the attack and target. They then produce large amounts of network traffic—spoofed to look legitimate—at the target servers. With hundreds of thousands of these running in tandem, it’s not hard to shut down most sites. These devices-turned-botnet will still function correctly for the unsuspecting owner, apart from the occasional sluggish bandwidth, and their botnet behavior may go unnoticed indefinitely.
Infected systems can be cleaned by rebooting them, but since scanning for these devices happens at a constant rate, it’s possible for them to be reinfected within minutes of a reboot. This means users have to change the default password immediately after rebooting, or prevent the device from accessing the internet until they can reset the firmware and change the password locally. If you’re taking these steps, make sure to no longer use Telnet, FTP, or HTTP, and instead use their encrypted counterparts SSH, SFTP, and HTTPS.
The underlying problem is that IoT manufacturers are only designing the devices for functionality and aren’t investing in proper security testing. Right now, it’s up to the consumer to scrutinize the security on any devices they use. In the future, some kind of vendor regulation may be necessary.
Hack forums have removed the published code, but it’s still available here.