419 advance fee fraudsters abuse CNN’s ‘Email This’ Feature, spread Syrian Crisis themed scams
Opportunistic 419 advance fee scammers are currently using CNN.com’s “Email This” feature to spamvertise Syrian Crysis themed emails, in an attempt to successfully bypass anti-spam filters. Ultimately tricking users into interacting with these fraudulent emails. The emails are just the tip of the iceberg in an ongoing attempt by multiple cybercrime gangs, looking to take advantage of the geopolitical situation (event-based social engineering attack) for fraudulent purposes, who continue spamming tens of thousands of emails impersonating internationally recognized agencies, on their way to socially engineer users into believing the legitimacy of these emails.
How to avoid unwanted software
We’ve all seen it; maybe it’s on your own computer, or that of a friend, your spouse, child, or parent. Your home page has been changed to some search engine you’ve never heard of, there’s a new, annoying toolbar in your browser. Maybe you’re getting popup ads or have a rogue security product claiming you’re infected and asking you to buy the program to remove the infection. Even worse, you don’t know how it got there! Welcome to the world of Potentially Unwanted Applications (PUAs.) Chances are that these programs were inadvertently installed while installing software from sites that use “download managers” that add additional software to otherwise free downloads.
Many of these “download managers” and the additional applications they install use a Pay Per Install business model that is often used by unscrupulous individuals that use various techniques to trick you into clicking on their sites rather than the official download site for the software you’re attempting to download. These techniques include using advertisements on search engines and various Search Engine Optimization (SEO) techniques to get their sites to show up before the official downloads in search results. We’ve even seen fake image upload sites whose sole purpose is to direct you to a page that looks like an official download page for a program but uses one of these “download managers” instead.
So how do you avoid these “download managers?” It’s actually pretty simple. Whenever possible, download software from the software company’s official page (this is not always possible since some software is only available through third-party download sites.) As mentioned earlier, some of the most popular techniques to get you to install software using these “download managers” is through ads and SEO techniques on search engines, so we’ll show you how to locate the official download links in search results from Google, Bing, and Yahoo.
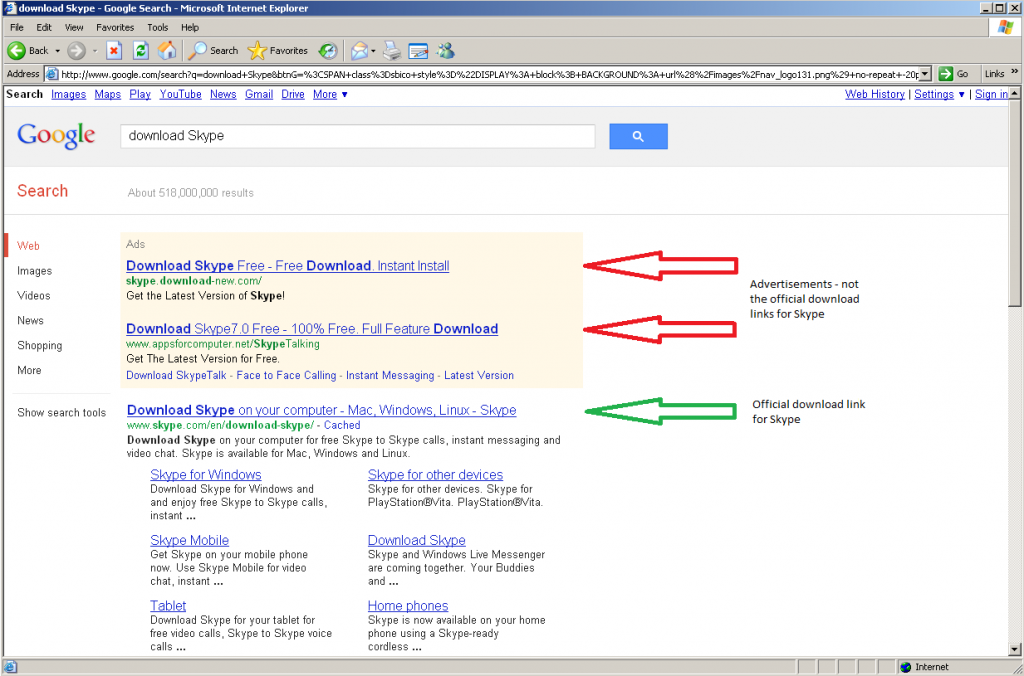
For this example we’ll search for the popular voice and video chat program Skype by searching for “download Skype.”
With Google it is rather easy to spot the official download link since the advertisements are clearly marked, and the first actual result is the official download link:
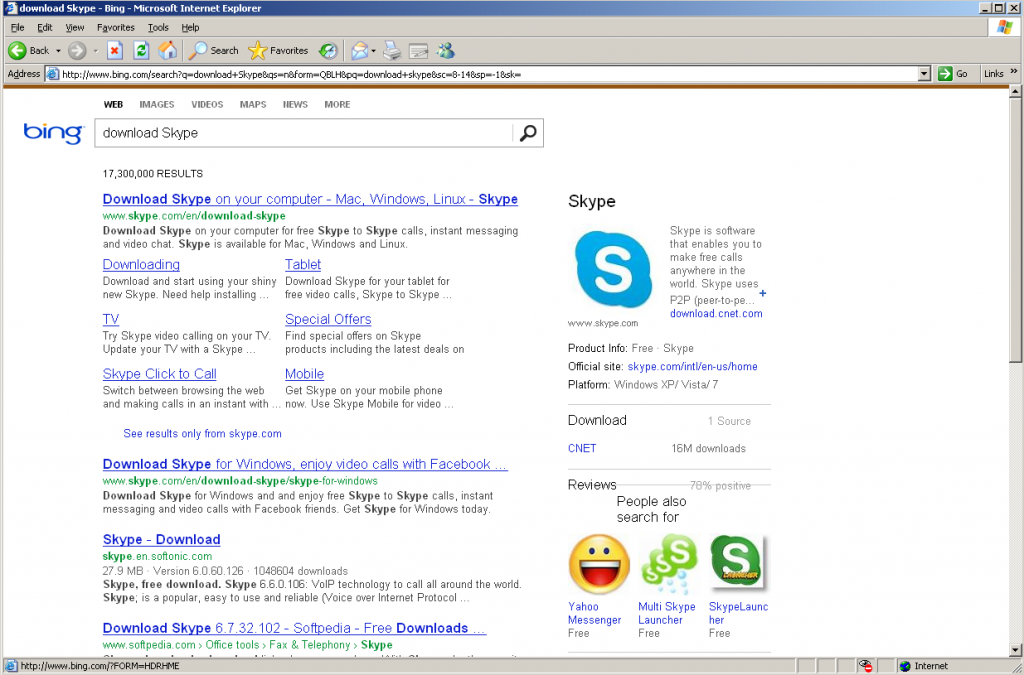
Let’s have a look at Bing next. Since both Skype and Bing are Microsoft products, the first two search results are for the official download links:
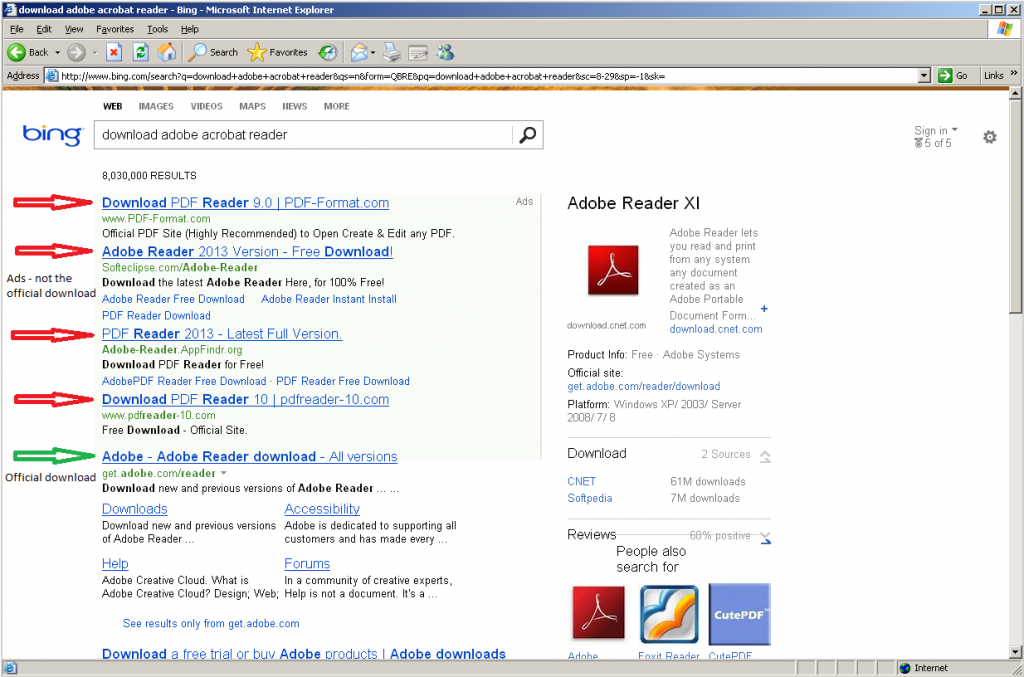
For a better example of Bing results, let’s search for Adobe Reader by searching for “download adobe acrobat reader.” This one is also pretty easy to spot since the ads are clearly marked.
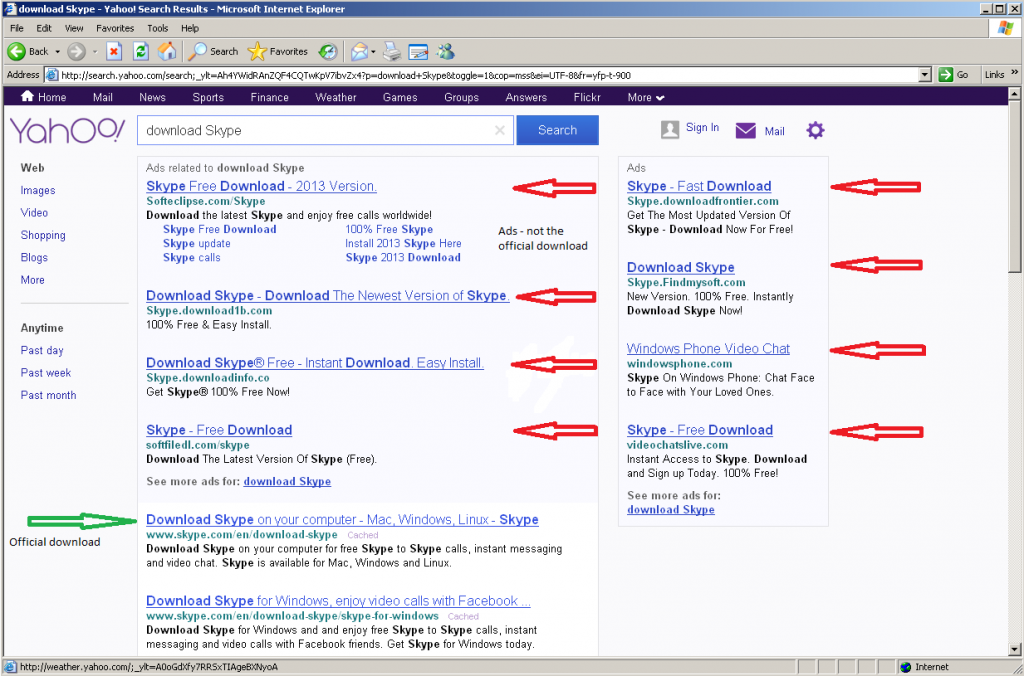
Now let’s have a look at the results for “download Skype” on Yahoo. Once again, the ads are clearly marked and the first actual result is the official download link.
Looking at these search results, you’ll notice a few things in common: The top results are all ads, and none of the ads point to the official download links, and the first actual link that is not an advertisement is the official download link. While this will not always be the case, it is common, and fortunately the three search engines we used in this example all do a very good job at identifying their advertisements. Does this mean that all ads are bad? Of course not! But when looking to download free software, the ads may not be your best choice. Also pay attention to the URLs, the official downloads are all on “skype.com” domains, while all the adds point to other domains.
Now you should have a better understanding of how some of those unwanted toolbars and search pages ended up on your computer, that clicking on the top result on a search page may not be the best way to go about downloading free software, and how to find the official download links for software on some of the most popular search engines. Pass this information onto others, and maybe you’ll save yourself a trip to a friend or family member’s house to remove an unwanted toolbar.
Affiliate network for mobile malware impersonates Google Play, tricks users into installing premium-rate SMS sending rogue apps
Affiliate networks are an inseparable part of the cybercrime ecosystem. Largely based on their win-win revenue sharing model, throughout the years, they’ve successfully established themselves as a crucial part of the cybercrime growth model, further ensuring that a cybercriminal will indeed receive a financial incentive for his fraudulent/malicious activities online.
From pharmaceutical affiliate networks, iPhone selling affiliate networks, to affiliate networks for pirated music and OEM (Original Equipment Manufacturer) software, cybercriminals continue to professionally monetize each and every aspect of the underground marketplace, on their way to harness the experience, know-how and traffic acquisitions capabilities of fellow cybercriminals.
In this post, I’ll take a peek inside a cybercrime-friendly affiliate network for premium-rate SMS based mobile malware, list its associated numbers currently in use, provide MD5s of variants known to have been pushed by it, and discuss its business model.
ThreatVlog Episode 5: Vodafone hacked, Super Hacker arrested, and bad GTAV torrents
In this episode of ThreatVlog, Tyler Moffitt talks about the 2 million user hack that Vodafone experienced last week, which investigators are saying is an inside job. He also goes into the arrest of Superhacker out of Argentina, who turned computers into zombies and was able to steal $50,000 a month from users. And in big news, Grand Theft Auto V was released today, and already torrents are being discovered packed full of malware and phishing schemes.
http://youtu.be/TALpwwBh-6g
Managed Malicious Java Applets Hosting Service Spotted in the Wild
In a series of blog posts, we’ve been profiling the tactics and DIY tools of novice cybercriminals, whose malicious campaigns tend to largely rely on social engineering techniques, on their way to trick users into thinking that they’ve been exposed to a legitimate Java applet window. These very same malicious Java applets, continue representing a popular infection vector among novice cybercriminals, who remain the primary customers of the DIY tools/attack platforms that we’ve been profiling.
In this post, I’ll discuss a popular service, that’s exclusively offering hosting services for malicious Java applets.
Web-based DNS amplification DDoS attack mode supporting PHP script spotted in the wild
The idea of controlling multiple, high-bandwidth empowered servers for launching DDoS attacks, compared to, for instance, controlling hundreds of thousands of malware-infected hosts, has always tempted cybercriminals to ‘innovate’ and seek pragmatic ‘solutions’ in order to achieve this particular objective.
Among the most recent high profile example utilizing this server-based DDoS attack tactic is Operation Ababil, or Izz ad-Din al-Qassam a.k.a Qassam Cyber Fighters attacks against major U.S financial institutions, where the use of high-bandwidth servers was utilized by the attackers. This indicates that wishful thinking often tends to materialize.
In this post, we’ll take a peek inside what appears to be a command and control PHP script in its early stages of development, which is capable of integrating multiple (compromised) servers for the purpose of launching distributed denial of service attacks (DDoS) taking advantage of their bandwidth.
More details:
ThreatVlog Episode 4: ThreatVlog SMS Fake Installer tricking Android Users
In this episode of ThreatVlog, Nathan Collier covers the old, but still around, SMS Fake Installer, a Russian based program used to trick phone users to send premium text messages, costing money to the user. Nathan talks about how these threats work, how this threat is different, and the easiest way to stay protected on your Android powered phone.
http://youtu.be/bA9B2lcPXCQ
Scammers pop up in Android’s Calendar App
Over the last couple of days, we’ve intercepted a rather interesting fraudulent approach that’s not just successfully hitting the inboxes of users internationally, but is also popping up as an event on their Android Calendar apps.
How is this possible? Fairly simple.
DIY malicious Android APK generating ‘sensitive information stealer’ spotted in the wild
Back in June, 2013, we offered a peek inside a DIY Android .apk decompiler/injector that was not only capable of ‘binding’ malicious Android malware to virtually any legitimate app, but also, was developed to work exclusively with a publicly obtainable Android-based trojan horse.
In this post, I’ll profile a similar, recently released cybercrime-friendly Windows-based tool that’s capable of generating malicious ‘sensitive information stealing’ Android .apk apps, emphasize on its core features, and most importantly, discuss in depth the implications this type of tool could have on the overall state of the Android malware market.
More details: read more…
ThreatVlog Episode 3: NYT, Twitter, and HuffPost hacked by Syrian Electronic Army
In this episode of ThreatVlog, Grayson Milbourne covers the information behind the Syrian Electronic Army’s hacking of New York Times, Twitter, and Huffington Post. Grayson includes a breakdown of the hack as well as information on how to keep your own websites protected form this malicious behavior.
http://youtu.be/9UPJjD2qwPA
Changes to the Webroot ThreatBlog
Over the next few days, you will begin to see some changes to the Webroot ThreatBlog. As the company has grown, so has the need for our threat research to be delivered in a clearer, more concise manner. We have worked long and hard on the new blog, including adding new content like the ThreatVlog, as well as highlighting the individuals behind all the great threat research done here at Webroot.
So with all that, we want to welcome you to the brand new Webroot ThreatVlog. It is more than a URL update, but a whole new look to help you better stay updated on the digital threats out there, and just how to stay protected.
To better help you, here are a few updated links to help you.
New web URL: https://www.webroot.com/blog/
RSS feed update: https://www.webroot.com/blog/feed/
Cybercrime-friendly underground traffic exchanges help facilitate fraudulent and malicious activity – part two
The list of monetization tactics a cybercriminal can take advantage of, once they manage to hijack a huge portion of Web traffic, is virtually limitless and is entirely based on his experience within the cybercrime ecosystem.
Through the utilization of blackhat SEO (search engine optimization), RFI (Remote File Inclusion), DNS cache poisoning, or direct impersonation of popular brands in spam/phishing campaigns tactics, on a daily basis, traffic is sold and resold for achieving a customer’s or a seller’s fraudulent/malicious objectives, and is then most commonly converted to malware-infected hosts.
In this post, I’ll profile two cybercrime-friendly iFrame traffic exchanges, with the second ‘vertically integrating’ by also offering spamming services, as well as services violating YouTube’s ToS (Terms of Service) such as likes, comments, views, favorites and subscribers on demand, with an emphasis on the most common ways through which a potential cybercriminal can abuse any such traffic exchange network.
More details: