Rogue ‘Free Mozilla Firefox Download’ ads lead to ‘InstallCore’ Potentially Unwanted Application (PUA)
Our sensors continue detecting rogue ads that expose users to bogus propositions in an attempt to install privacy-invading Potentially Unwanted Applications (PUAs) on their PCs. The most recent campaign consists of a successful brand-jacking abuse of Mozilla’s Firefox browser, supposedly offered for free, while in reality, the rogue download manager entices users into installing multiple rogue toolbars, most commonly known as InstallCore.
More details:
Adobe Flash spoof leads to infectious audio ads
By Tyler Moffitt
We’ve seen quite a few audio ads infecting users recently. We think it’s a good idea to go over an in-depth look at how they infect your computer and how to remediation them.
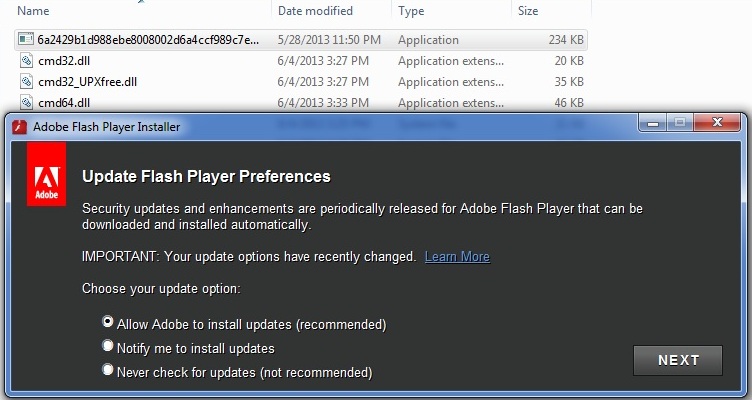
As you can see in this first picture, this is another Adobe Flash spoof that launches its signature update window.
You might not be able to see, but the “f” is a little off on the tiny icon at the top left. Either way it looks quite legitimate. It doesn’t matter what option you check; once you click “NEXT” you’ll get this next window.
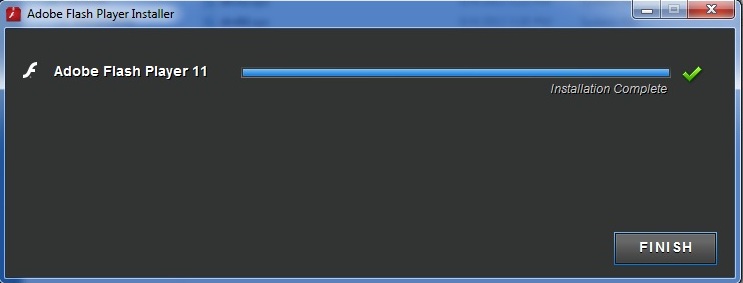
So far this seems completely official and harmless. It even takes it’s time progressing the loading bar. However, once you click “Finish” everything closes down and the computer reboots. The command force quits all applications so you won’t have time to save anything or cancel the shutdown. Once the computer reboots there is no final closing message from “Adobe”, but everything seems normal for a few minutes. After about three to five minutes the computer slows down to a crawl and Audio ads start playing in the background. By now users start to worry about foul play with their computer so here’s a look at what’s going on at this point.
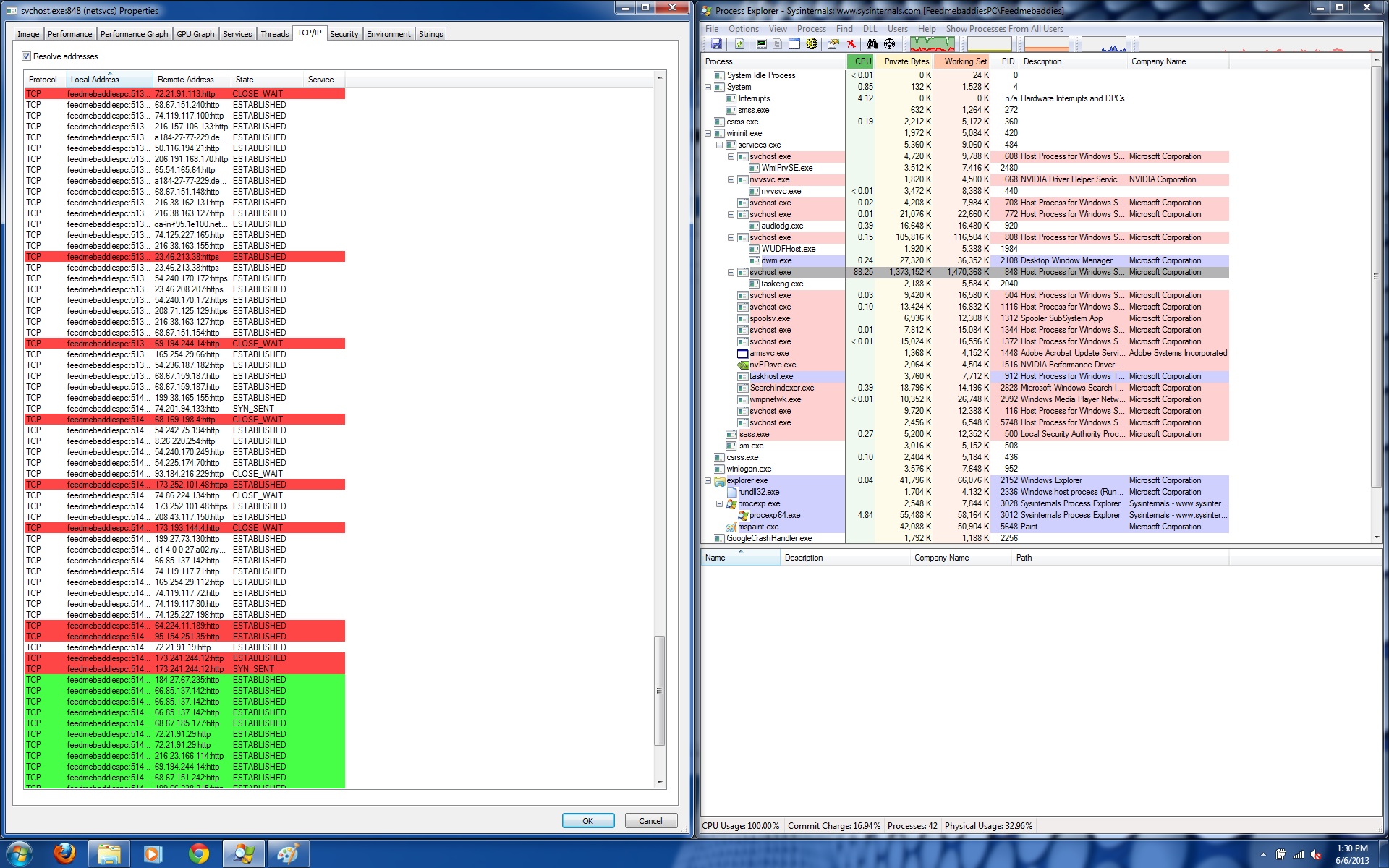
The audio streams are not being run by an audio application or an internet browser session, but instead a hijacked “svchost.exe” that’s using 88.25% CPU. If we take a look at its network communication we find that it’s establishing and closing over a hundred different connections at once. This is why the audio ads aren’t coherent and are basically just multiple advertisement streams all at once which makes for quite an annoying sound. You can give it a listen by clicking below.
[soundcloud url=”http://api.soundcloud.com/playlists/6977174″ params=”” width=” 100%” height=”300″ iframe=”true” /]
The motivation is for this virus, other than being very obnoxious, is that the hundreds of IP addresses being resolved from the PC will generate a tick on the visit counter and generate ad revenue.
To remove this sample is actually quite simple. Since this starts as soon as the computer starts if you take a look at the startup entries you should find something similar to this.
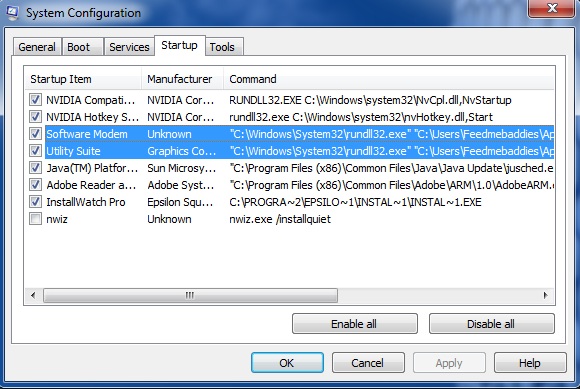
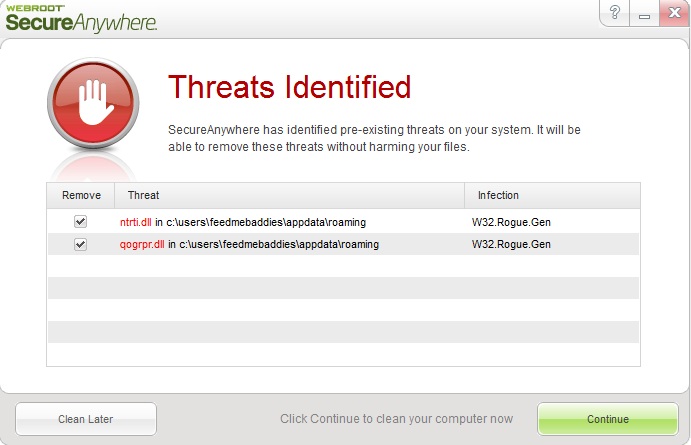
Software Modem and Utility Suite are the culprit. If you read the full command they are located in appdata and point to two randomly named DLLs called “qogrpr.dll” and “ntrti.dll” This is extremely suspicious.
All you need to do is delete the files in appdata and then remove the run keys from startup. The full registry key and directory location from are below.
[HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun]
“qogrpr”=””C:\Windows\System32\rundll32.exe” “C:\Users\”youruserfolder”\AppData\Roaming\qogrpr.dll”,GetGlobals”
“ntrti”=””C:\Windows\System32\rundll32.exe” “C:\Users\”youruserfolder”\AppData\Roaming\ntrti.dll”,NewMember”
As always, you can install Webroot SecureAnywhere and we’ll remove it with ease.
That’s it for this variant of the Audio ads. There are also other variants that use rootkits to infect the MBR. Please contact Webroot Support if additional assistance is needed in remediating this infection.
New subscription-based SHA256/Scrypt supporting stealth DIY Bitcoin mining tool spotted in the wild
A recently released subscription-based SHA256/Scrypt supporting stealth DIY Bitcoin mining tool is poised to empower cybercriminals with advanced Bitcoin mining capabilities to be used on the malware-infected hosts that they have direct access to, or have purchased through a boutique cybercrime-friendly E-shop selling access to hacked PCs.
Let’s take a peek at the DIY Bitcoin mining tool, and discuss some of its core features.
New E-Shop sells access to thousands of malware-infected hosts, accepts Bitcoin
Thanks to the buzz generated over the widespread adoption of the decentralized P2P based E-currency, Bitcoin, we continue to observe an overall increase in international underground market propositions that accept it as means for fellow cybercriminals to pay for the goods/services that they want to acquire.
In this post, I’ll profile yet another recently launched E-shop selling access to thousands of malware-infected hosts, which compared to the previous E-shops that we’ve profiled, is directly promoting the use of ransomware, click fraud facilitating bots and bitcoin mining tools on the malware-infected hosts purchased through the service.
More details:
Rogue ‘Oops Video Player’ attempts to visually social engineer users, mimicks Adobe Flash Player’s installation process
Our sensors have just detected yet another rogue advertisement served through the Yieldmanager ad network, this one enticing users into downloading a rogue video player known as the ‘Oops Video Player’. What’s particularly interesting about this rogue ad campaign is that the PUA (Potentially Unwanted Application) attempts to visually trick users by mimicking Adobe Flash Player’s installation process.
More details:
New boutique iFrame crypting service spotted in the wild
In a series of blog posts shedding more light into the emergence of the boutique cybercrime ‘enterprise’, we’ve been profiling underground market propositions that continue populating the cybercrime ecosystem on a daily basis, but fail to result in any widespread damage or introduce potential ecosystem disrupting features. Despite these observations, the novice cybercriminals behind them continue earning revenue from fellow cybercriminals, continue generating and maintaining their botnets, and, just like small businesses in a legitimate economy model, continue to collectively occupy a significant market share within the cybercrime ecosystem.
In this post, I’ll profile a self-service type of boutique iFrame crypting cybercrime-friendly operation and discuss why its perceived short product/service life cycle is still a profitable cybercrime ecosystem monetization tactic, despite these services’/products’ inability to differentiate their proposition from the market leading competitors whose ‘releases’ remain a major driving force behind the mature state of the underground market in 2013.
More details:
Rogue ads target EU users, expose them to Win32/Toolbar.SearchSuite through the KingTranslate PUA
By Dancho Danchev
Who would need a virtually unknown, but supposedly free, desktop based application in order to translate texts between multiple languages? Tens of thousands of socially engineered European ads, who continue getting exposed to the rogue ads served through Yieldmanager’s network, are promoting more Potentially Unwanted Applications (PUAs) courtesy of Bandoo Media Inc and their subsidiary Koyote-Lab Inc.
More details:
How cybercriminals apply Quality Assurance (QA) to their malware campaigns before launching them
By Dancho Danchev
In 2013, the use of basic Quality Assurance (QA) practices has become standard practice for cybercriminals when launching a new campaign. In an attempt to increase the probability of a successful outcome for their campaigns — think malware infection, increased visitor-to-malware infected conversion, improved conversion of blackhat SEO acquired traffic leading to the purchase of counterfeit pharmaceutical items etc. — it has become a common event to observe the bad guys applying QA tactics, before, during, and after a malicious/fraudulent campaign has reached its maturity state, all for the sake of earning as much money as possible, naturally, through fraudulent means.
In this post we’ll profile a recently released desktop based multi-antivirus scanning application. It utilizes the infrastructure of one of the (cybercrime) market leading services used exclusively by cybercriminals who want to ensure that their malicious executables aren’t detected and that their submitted samples aren’t shared between the vendors before actually launching the campaign.
More details:
Rogue ads lead to SafeMonitorApp Potentially Unwanted Application (PUA)
By Dancho Danchev
Our sensors just picked up yet another rogue ad enticing users into installing the SafeMonitorApp, a potentially unwanted application (PUA) that socially engineers users into giving away their privacy through deceptive advertising of the rogue application’s “features”.
More details:
Tens of thousands of spamvertised emails lead to W32/Casonline
By Dancho Danchev
Fraudsters are currently spamvertising tens of thousands of emails enticing users into installing rogue, potentially unwanted (PUAs) casino software. Most commonly known as W32/Casonline, this scam earns revenue through the rogue online gambling software’s affiliate network.
More details:
How not to install Adobe Flash Player
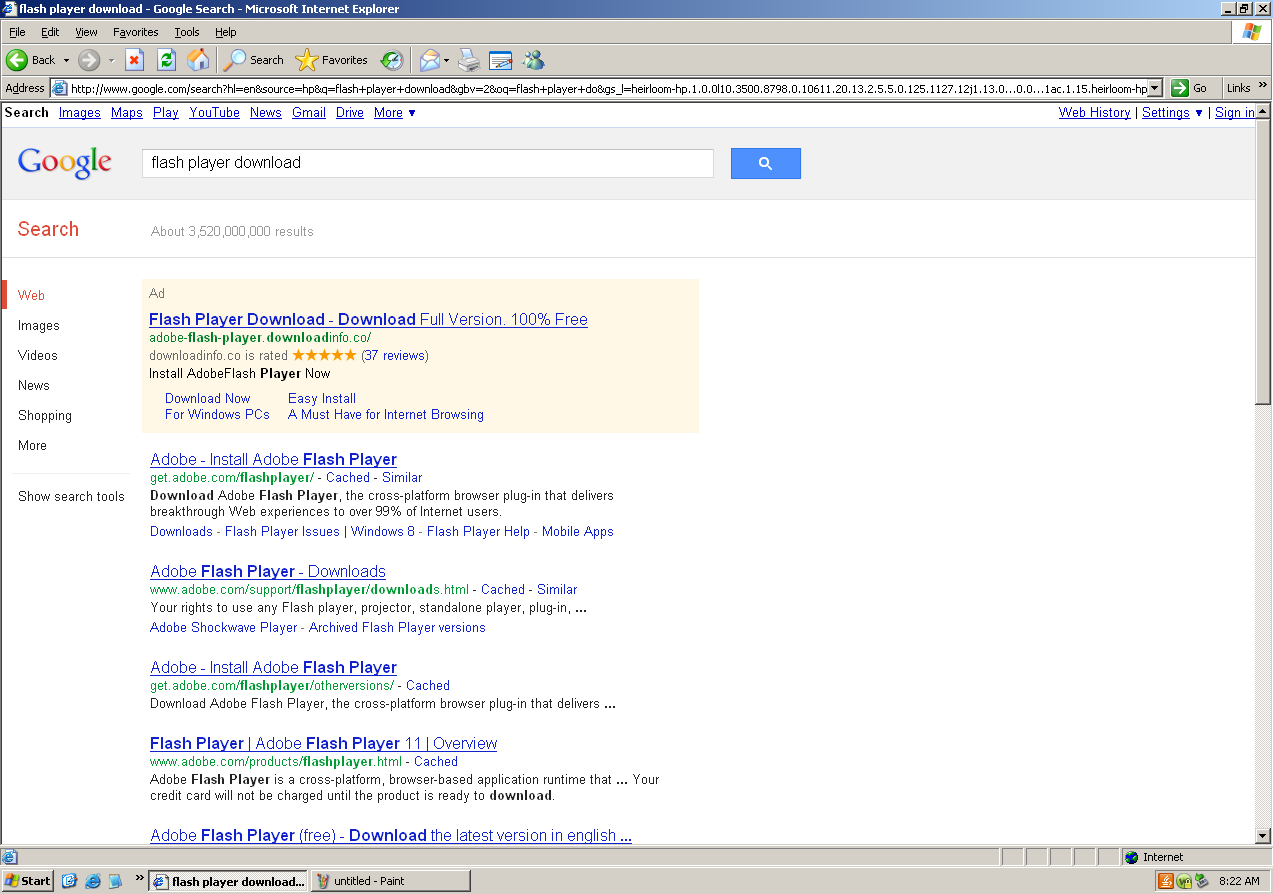
It seems simple enough, I want to install Adobe Flash Player so I search for “flash player download and click on the first result, right?
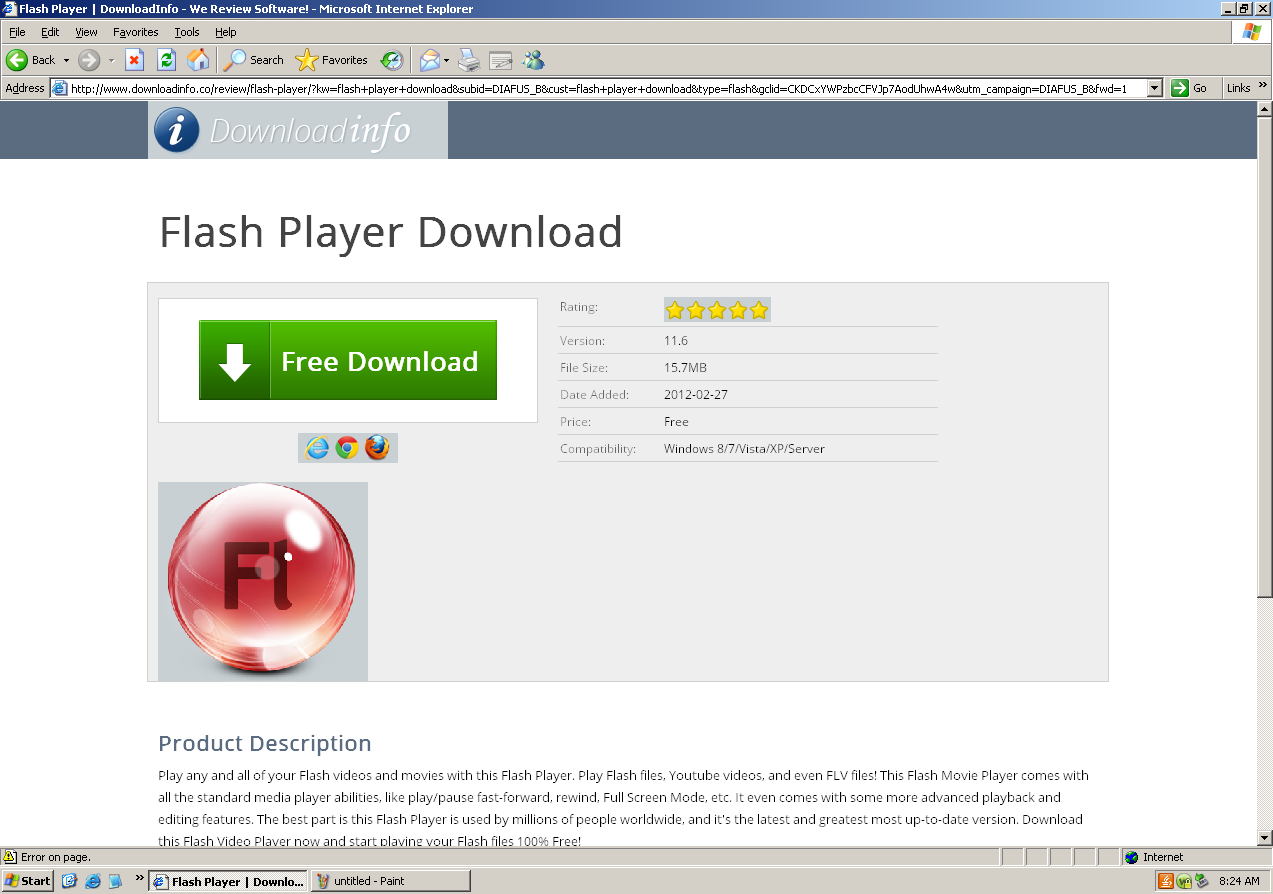
Ignoring the second link which doesn’t have a five star rating and 37 reviews, I’m brought to a page called downloadinfo.com.
I click the download button, click through the download dialog box and run dialog box, come to the Optimum Download screen for my Free Flash Player. Click.
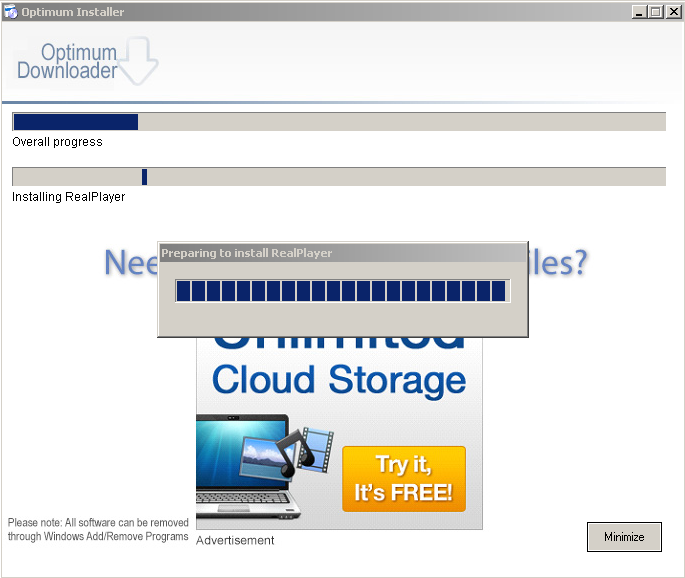
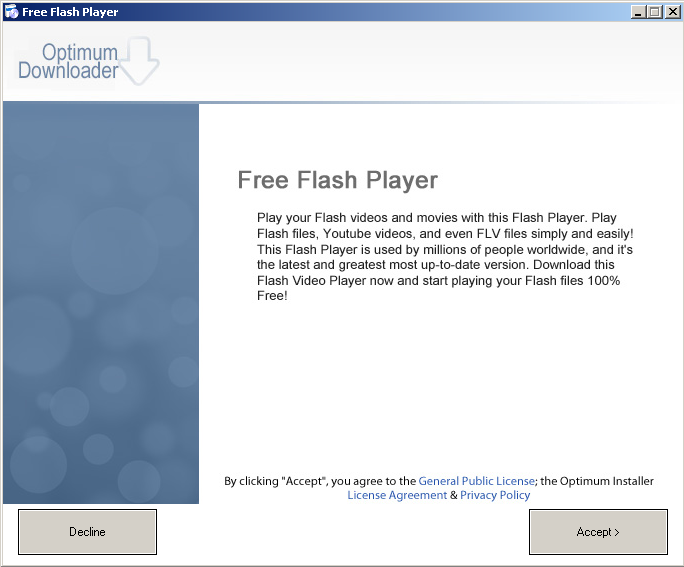 Let’s see what this installs. First up is RealPlayer. Click.
Let’s see what this installs. First up is RealPlayer. Click.
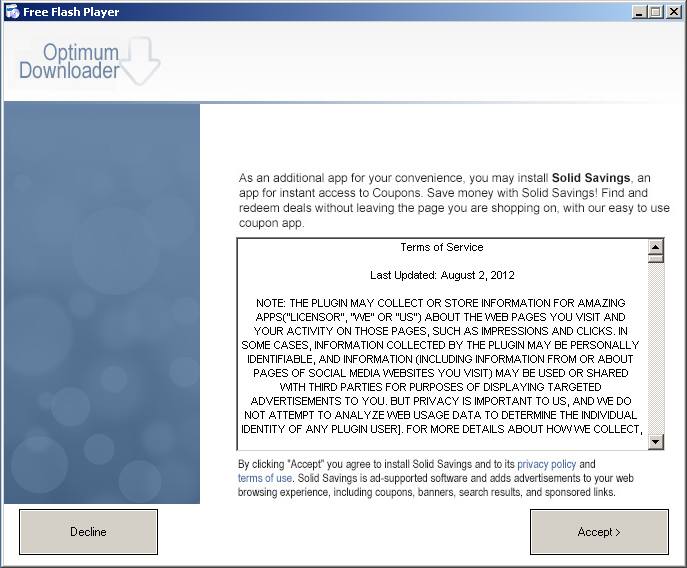
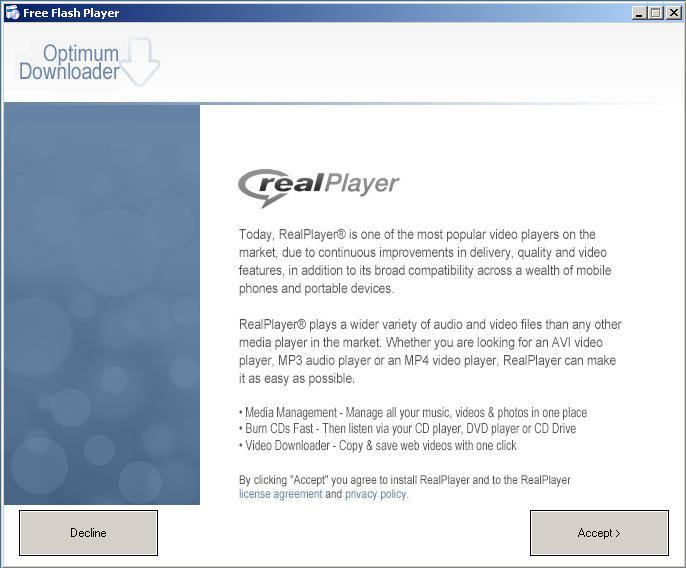 Next up is some program called Solid Savings. Click.
Next up is some program called Solid Savings. Click.
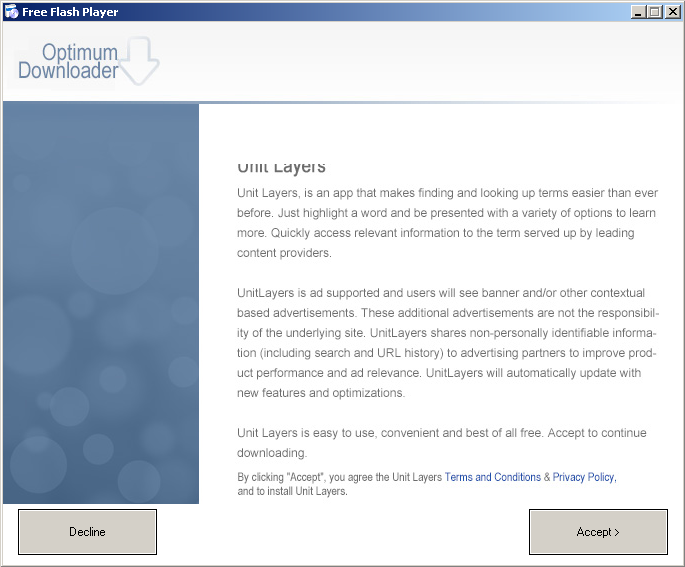
Then something called Unit Layers. Click.
That seems like a lot of software to install in order to get my Adobe Flash Player, but we’re not done yet, here’s something called Optimizer Pro. Click.
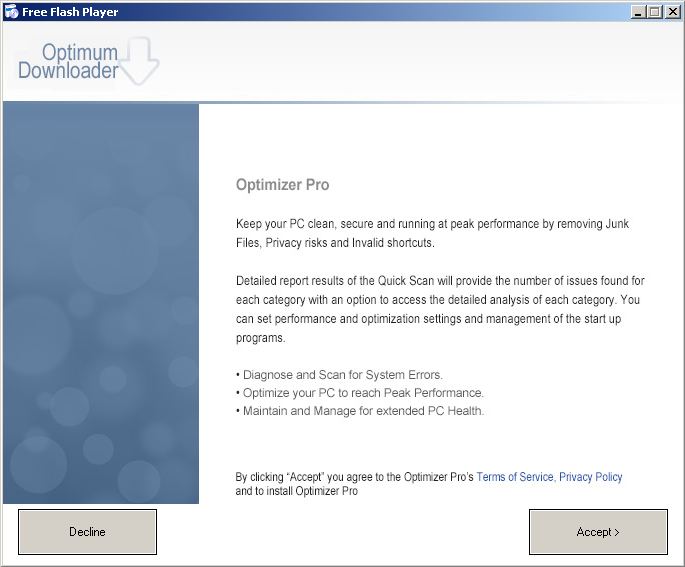
Okay, now we’re finally installing…
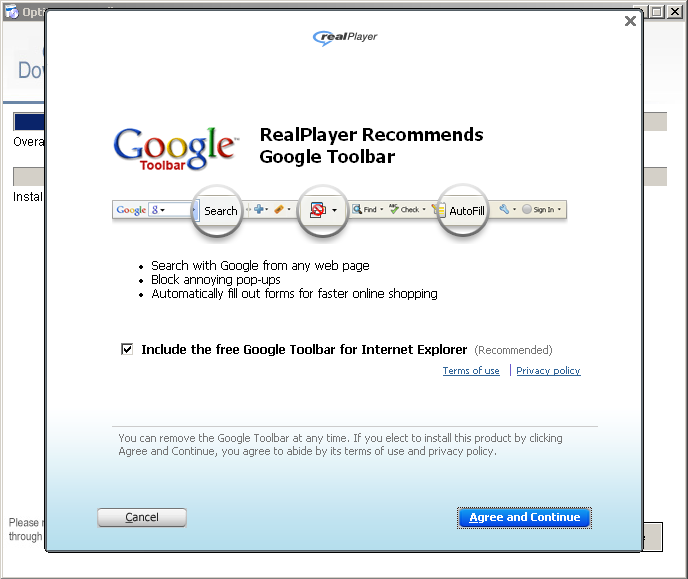
Now RealPlayer, which was bundled with Flash Player wants to install the Google Toolbar? A bundle within a bundle? Okay… Click.
I should have my Flash Player any moment now… Wait a minute. VLC media player? Where’s the Adobe Flash Player I started out downloading?
Okay, VLC media player will play flash files, but I really expected to be getting Adobe Flash Player (Seriously, while I was doing this I was hoping this was one of the “download managers” that actually downloads and installs the actual Adobe Flash Player along with all of this other software. I was surprised and disappointed to get VLC media player instead.) The link I had clicked on initially displayed it’s URL as adobe-flash-player.downloadinfo.co/ and included the text “Install AdobeFlash Player Now” so you would think that link would get you Adobe Flash Player, but no, it was just a misleading ad that appeared as the top result on the search page that led to a “download manager” which bundled a bunch of additional software along with VLC media player, which can be downloaded for free. The downloadinfo.com website even had fine print stating that “This software may be available free elsewhere” which was hyperlinked to the download page for VLC media player!
So how should you install Adobe Flash Player? Or any other software for that matter? In this case I could have clicked on the second link which would have brought me directly to the download page for Adobe Flash Player (and unchecked the box to opt-out of installing McAfee Security Scan Plus of course.) In general we recommend downloading software directly from the software company’s website whenever possible, otherwise you could end up installing all sorts of additional, potentially unwanted software along with the free software that you wanted to download – or even a completely different program like I just did.
Fake ‘Unsuccessful Fax Transmission’ themed emails lead to malware
Have you sent an eFax recently? Watch out for an ongoing malicious spam campaign that tries to convince you that there’s been an unsuccessful fax transmission. Once socially engineered users execute the malicious attachment found in the fake emails, their PCs automatically join the botnet of the cybercriminals behind the campaign.
More details: