New commercially available DIY invisible Bitcoin miner spotted in the wild
By Dancho Danchev
Just as we anticipated in our previous analysis of a commercially available Bitcoin miner, cybercriminals continue “innovating” on this front by releasing more advanced and customizable invisible Bitcoin miners for fellow cybercriminals to take advantage of.
In this post, we’ll profile yet another invisible Bitcoin miner, once again available for purchase on the international cybercrime-friendly marketplace, emphasize on its key differentiation features, as well as provide MD5s of known miner variants.
More details:
CVs and sensitive info soliciting email campaign impersonates NATO
By Dancho Danchev
Want to join the North Atlantic Treaty Organization (NATO)? You may want to skip the CVs/personally identifiable information soliciting campaign that I’m about to profile in this post, as you’d be involuntarily sharing your information with what looks like an intelligence gathering operation.
More details: read more…
DIY malware cryptor as a Web service spotted in the wild – part two
By Dancho Danchev
With more Web-based DIY malware crypters continuing to pop up online, both novice and experienced cybercriminals can easily obfuscate any malicious sample into an undetected — through signatures based scanning not behavioral detection — piece of malware, successfully bypassing perimeter based defenses currently in place.
In this post I’ll profile a recently launched service, empowering virtually everyone using it, with the capability to generate undetected malware. I’ll emphasize on its key differentiation factors and provide sample MD5s known to have been crypted using the service.
More details:
Commercial ‘form grabbing’ rootkit spotted in the wild
By Dancho Danchev
Trust is vital. It’s also the cornerstone for the growth of E-commerce in general, largely thanks to the mass acceptable of a trusted model for processing financial data and personally identifiable information. For years, the acceptance and mass implementation of PKI (Public Key Infrastructure) has been a driving force that resulted in a pseudo-secure B2C, B2B, and B2G electronic marketplace, connecting the world’s economies in a 24/7/365 operating global ecosystem.
The bad news? Once the integrity of a host or a mobile device has been compromised, SSL, next to virtually every two-factor authentication mechanism gets bypassed by the cybercriminals that compromised the host/device, leading to a situation where users are left with a ‘false feeling of security‘.
In this post, I’ll profile a recently advertised commercial ‘form grabbing’ rootkit, that’s capable of ‘”grabbing” virtually any form of communication transmitted over SSL
More details: read more…
Newly launched ‘Magic Malware’ spam campaign relies on bogus ‘New MMS’ messages
By Dancho Danchev
The gang of cybercriminals behind the ‘Magic Malware‘ has launched yet another malicious spam campaign, attempting to trick U.K users into thinking they’ve received a notification for a “New MMS” message. In reality, once users execute the malicious attachment, it will download and drop additional malware on the affected hosts, giving the cybercriminals behind the campaign complete access to the affected host.
More details: read more…
Android.RoidSec: This app is an info stealing “sync-hole”!
Android.RoidSec has the package name “cn.phoneSync”, but an application name of “wifi signal Fix”. From a ‘Malware 101’ standpoint, you would think the creators would have a descriptive package name that matches the application name. Not so, in this case. So what is Android.RoidSec? It’s a nasty, malicious app that sits in the background (and avoids installing any launcher icon) while collecting all sorts of info-stealing goodness. read more…
New versatile and remote-controlled “Android.MouaBot” malware found in the wild
By Cameron Palan and Nathan Collier
Recently, we discovered a new malicious Android application called Android.MouaBot. This malicious software is a bot contained within another basic app; in this case, a Chinese calculator application. Behind the scenes, it automatically sends an SMS message to an auto-reply number which replies back to the phone with a set of commands/keywords. This message is then parsed and the various plugins within the malicious packages are run or enabled.
Fake ‘Free Media Player’ distributed via rogue ‘Adobe Flash Player HD’ advertisement
Our sensors just picked up a rogue advertisement served through the Yieldmanager ad network, which exposes users to fake Adobe Flash Player HD ads, ultimately dropping a copy of the potentially unwanted application (PUA)/adware, known as Somoto Better Installer.
More details:
New subscription-based ‘stealth Bitcoin miner’ spotted in the wild
By Dancho Danchev
Bitcoin, the digital peer-to-peer based currency, is an attractive target for cybercriminals, who persistently look for new monetization tactics to apply to their massive, but easily generated botnets. Not surprisingly, thanks to the buzz surrounding it, fraudulent Internet actors have begun to look for efficient ways to take advantage of the momentum. A logical question emerges – how are market oriented cybercriminals capitalizing on the digital currency?
Instead of having to personally infect tens of thousands of hosts, some take advantage of basic pricing schemes such subscription-based pricing, and have others do all the infecting, with them securing a decent revenue stream based on a monthly subscription model.
Let’s profile the international underground market proposition, detailing the commercial availability of a stealth Bitcoin miner, feature screenshots of the actual DIY miner generating tool, screenshots provided by happy customers, and perhaps most importantly, MD5s of known miner modifications ‘pushed’ since its first commercial release.
More details:
Newly launched E-shop for hacked PCs charges based on malware ‘executions’
By Dancho Danchev
On the majority of occasions, Cybercrime-as-a-Service vendors will sell access to malware-infected hosts to virtually anyone who pays for them, without bothering to know what happens once the transaction takes place.
A newly launched E-shop for malware-infected hosts, however, has introduced a novel approach for calculating the going rate for the hacked PCs. Basically, they’re selling actual malicious binary “executions” on the hosts that the vendor is managing, instead of just selling access to them.
A diversified international underground market proposition? Check. A novel approach to monetize malware-infected hosts? Not at all. Let’s profile the actual market proposition, and discuss in-depth why its model is flawed by design.
More details:
Cybercriminals offer HTTP-based keylogger for sale, accept Bitcoin
By Dancho Danchev
In 2013, Liberty Reserve and Web Money remain the payment method of choice for the majority of Russian/Eastern European cybercriminals. Cybercrime-as-a-Service underground market propositions, malware crypters, R.A.Ts (Remote Access Trojans), brute-forcing tools etc. virtually every underground market product/service is available for purchase through the use of these ubiquitous virtual currencies.
What’s the situation on the international underground market? Next to accepting PayPal and consequently all major credit cards, we’ve been observing an increase in market propositions starting to accept Bitcoins. Is this a trend or a fad, and does the currency’s P2P model about to be embraced ecosystem-wide due to its (current) pseudo-anonymous model?
Let’s find out.
More details:
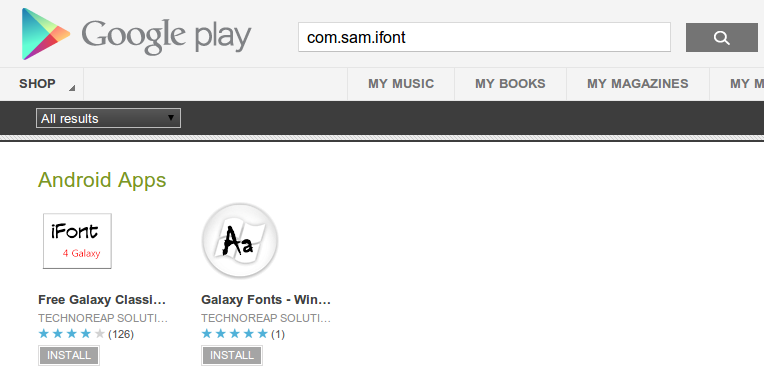
Android.TechnoReaper Downloader Found on Google Play
We have found a new threat we are calling Android.TechnoReaper. This malware has two parts: a downloader available on the Google Play Market and the spyware app it downloads. The downloaders are disguised as font installing apps, as seen below: