Fake ‘DHL Delivery Report’ themed emails lead to malware
Over the past couple of days, cybercriminals have launched two consecutive malware campaigns impersonating DHL in an attempt to trick users into thinking that they’ve received a parcel delivery notification. The first campaign comes with a malicious attachment, whereas in the second, the actual malicious archive is located on a compromised domain.
More details: read more…
Historical OSINT – The ‘Boston Marathon explosion’ and ‘Fertilizer plant explosion in Texas’ themed malware campaigns
Following the recent events, opportunistic cybercriminals have been spamvertising tens of thousands of malicious emails in an attempt to capitalize on on the latest breaking news.
We’re currently aware of two “Boston marathon explosion” themed campaigns that took place last week, one of which is impersonating CNN, and another is using the “fertilizer plant exposion in Texas” theme, both of which redirect to either the RedKit or the market leading Black Hole Exploit Kit.
Let’s profile the campaigns that took place last week, with the idea to assist in the ongoing attack attribution process.
More details:
CAPTCHA-solving Russian email account registration tool helps facilitate cybercrime
By Dancho Danchev
Just how challenged are cybercriminals when they’re being exposed to CAPTCHAs in 2013?
Not even bothering to “solve the problem” by themselves anymore, thanks to the cost-efficient, effective, and fully working process of outsourcing the CAPTCHA solving process to humans thereby allowing the cybercriminals to abuse any given Web property, as if it were multiple humans actually performing the actions.
In this post I’ll profile an automatic CAPTCHA-solving (Russian) email account registration tool which undermines the credibility of Russia’s major free email service providers by allowing cybercriminals to register tens of thousands of bogus email accounts.
More details:
DIY SIP-based TDoS tool/number validity checker offered for sale
By Dancho Danchev
Over the past year, we observed an increase in publicly available managed TDoS (Telephony Denial of Service) services. We attribute this increase to the achieved ‘malicious economies of scale’ on behalf of the cybercriminals operating them, as well as the overall availability of proprietary/public DIY phone ring/SMS-based TDoS tools.
What are cybercriminals up to in terms of TDoS attack tools? Let’s take a peek inside a recently released DIY SIP-based (Session Initiation Protocol) flood tool, which also has the capacity to validate any given set of phone numbers.
More details: read more…
DIY Russian mobile number harvesting tool spotted in the wild
By Dancho Danchev
Earlier this year we profiled a newly released mobile/phone number harvesting application, a common tool in the arsenal of mobile spammers, as well as vendors of mobile spam services. Since the practice is an inseparable part of the mobile spamming process, cybercriminals continue periodically releasing new mobile number harvesting applications, update their features, but most interestingly, continue exclusively targeting Russian users.
In this post, I’ll profile yet another DIY mobile number harvesting tool available on the underground marketplace since 2011, and emphasize on its most recent (2013) updated feature, namely, the use of proxies.
More details: read more…
A peek inside a (cracked) commercially available RAT (Remote Access Tool)
By Dancho Danchev
In an attempt to add an additional layer of legitimacy to their malicious software, cybercriminals sometimes simply reposition them as Remote Access Tools, also known as R.A.Ts. What they seem to be forgetting is that no legitimate Remote Access Tool would possess any spreading capabilities, plus, has the capacity to handle tens of thousands of hosts at the same time, or possesses built-in password stealing capabilities. Due to the nature of these programs, they have also become known as Remote Access (or Admin) Trojans.
Pitched by its author as a Remote Access Tool, the DIY (do it yourself) malware that I’ll profile in this post is currently cracked, and available for both novice, and experienced cybercriminals to take advantage of at selected cybercrime-friendly communities.
More details:
The first time we came across the underground market ad promoting the availability of the DIY malware was in June 2012 and offered for sale for $1,000. Then in October 2012, a cracked and fully working version of the DIY malware leaked on multiple cybercrime-friendly communities, potentially undermining the monetization attempted by its author.
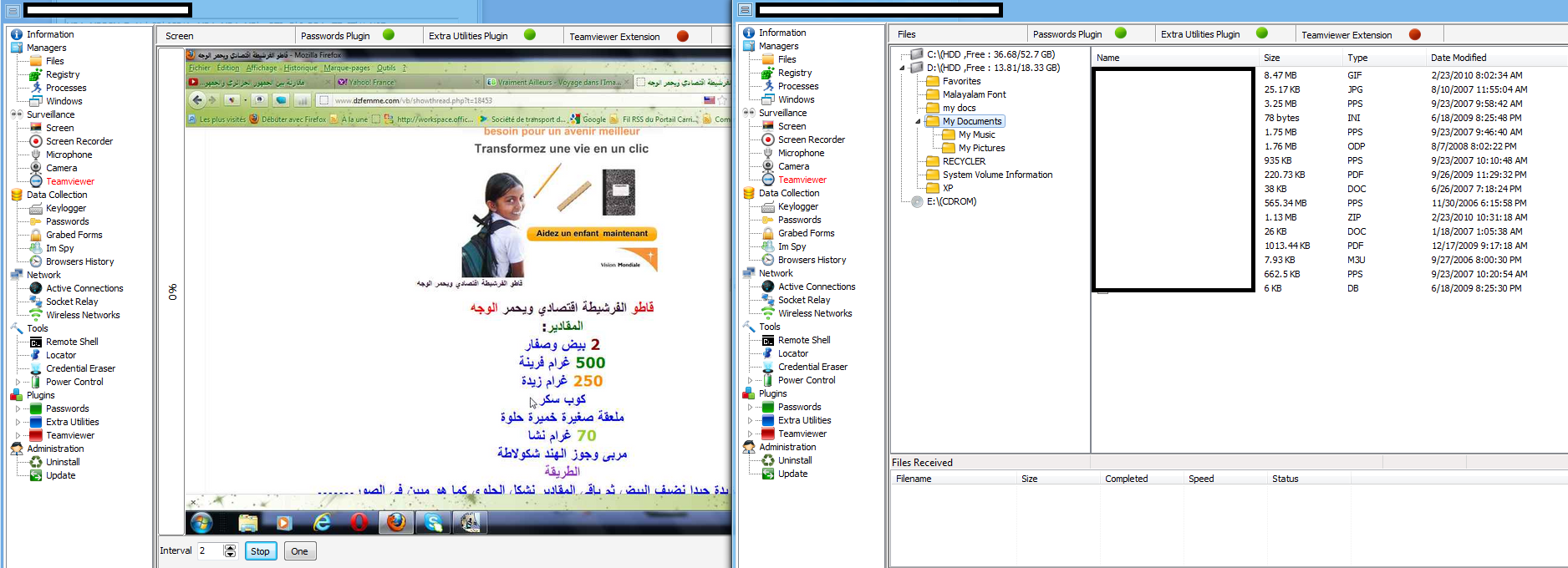
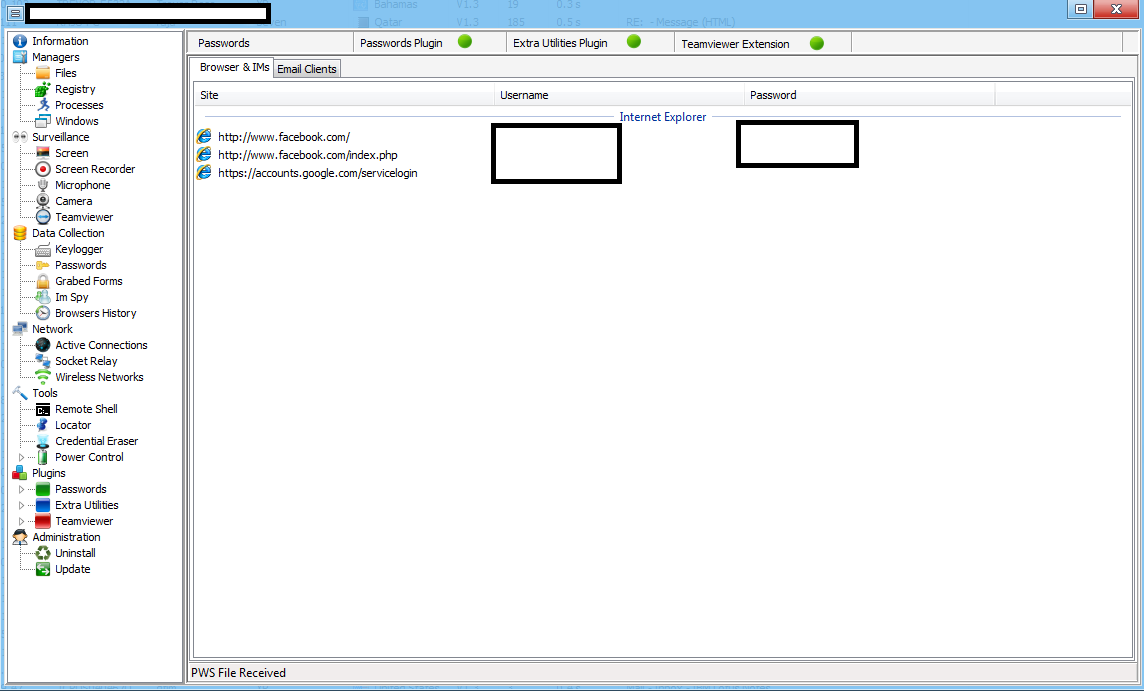
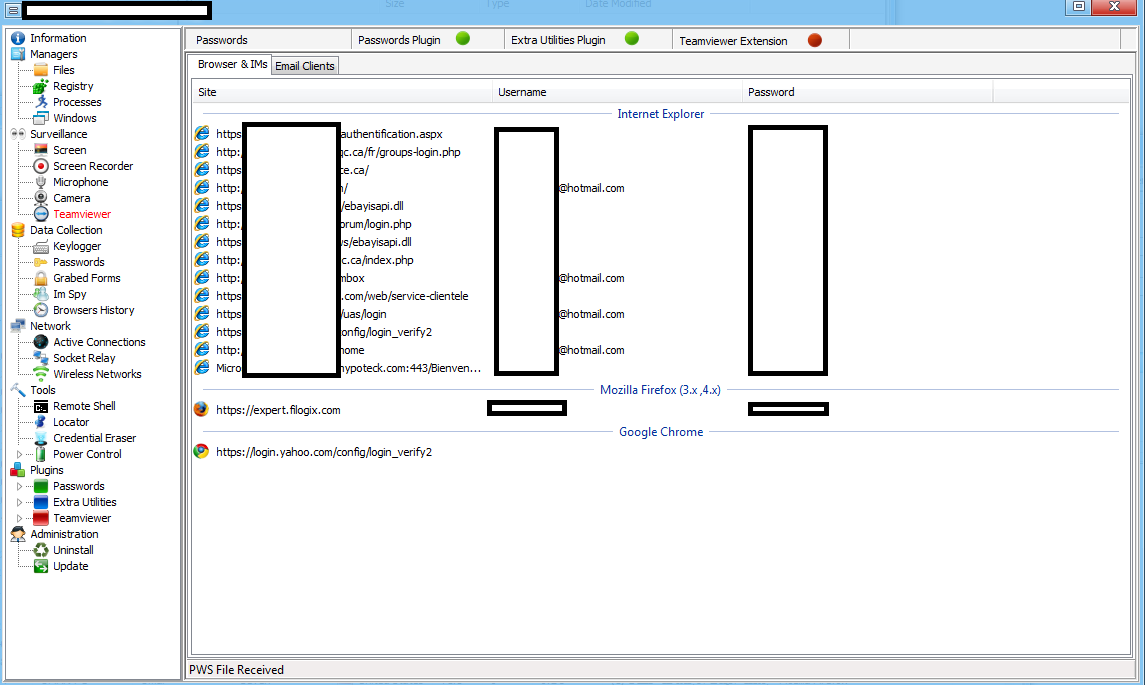
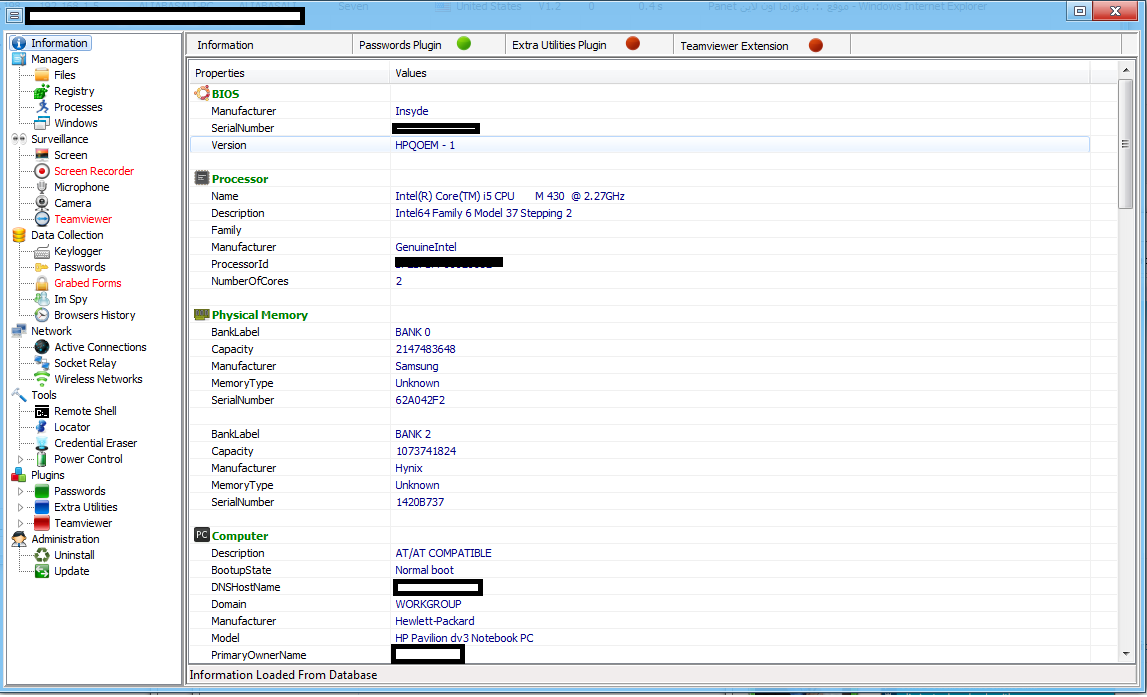
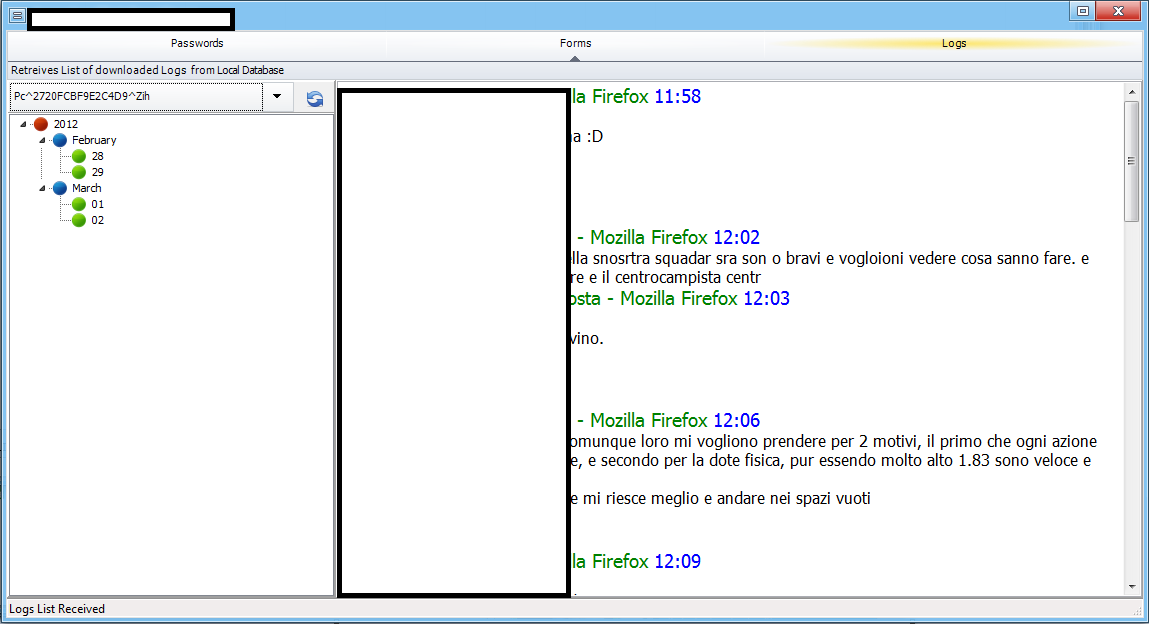
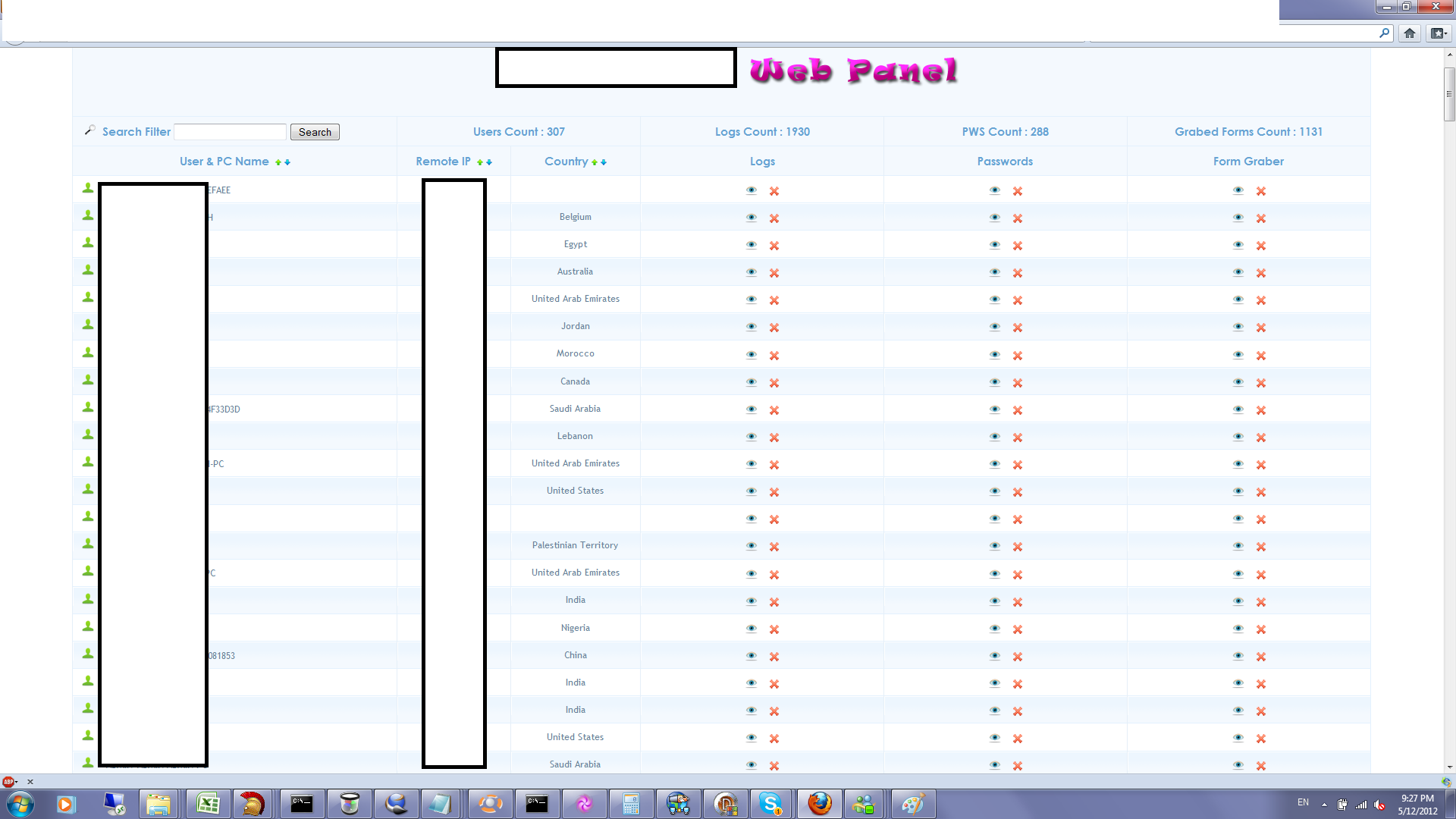
The Web/Client based release has numerous features, presented in a point-and-click fashion, potentially empowering novice cybercriminals with a versatile set of online spying capabilities. Let’s go through some screenshots to demonstrate the capabilities of this particular (cracked) underground market release.
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Sample screenshot of the DIY Web/Client based malware:
Cracked malware releases either cease to exist since the cybercriminal behind them has failed to monetize his release in the initial phrase, continue being developed as private releases, or become adopted by novice cybercriminals taking advantage of today’s managed malware crypting services to ensure that the actual payload remains undetected before it is distributed to the intended target(s).
We’ll continue monitoring the development of this RAT software/DIY malware, in particular, whether or not its developer will continue working on it, now that there are leaked versions of it available online.
You can find more about Dancho Danchev at his LinkedIn Profile. You can also follow him on Twitter.
How mobile spammers verify the validity of harvested phone numbers – part two
Just as we anticipated earlier this year in our “How mobile spammers verify the validity of harvested phone number” post, mobile spammers and cybercriminals in general will continue ensuring that QA (Quality Assurance) is applied to their upcoming campaigns. This is done in an attempt to both successfully reach a wider audience and to charge a higher price for a verified database of mobile numbers.
In this post I’ll profile yet another commercially available phone/mobile number verification tool that’s exclusively supporting Huawei 3G USB modems.
More details: read more…
Cybercriminals offer spam-friendly SMTP servers for rent
In times when modern cybercriminals take advantage of the built-in SMTP engines in their malware platforms, as well as efficient and systematic abuse of Web-based email service providers for mass mailing fraudulent or malicious campaigns, others seem to be interested in the resurrection of an outdated, but still highly effective way to send spam, namely, through spam-friendly SMTP servers.
In this post, I’ll profile a recently posted underground market ad for spam-friendly SMTP servers, offered for sale for $30 on a monthly basis.
More details: read more…
American Airlines ‘You can download your ticket’ themed emails lead to malware
By Dancho Danchev
Cybercriminals are currently spamvertising tens of thousands of emails impersonating American Airlines in an attempt to trick its customers into thinking that they’ve received a download link for their E-ticket. Once they download and execute the malicious attachment, their PCs automatically join the botnet operated by the cybercriminal/gang of cybercriminals behind the campaign.
More details:
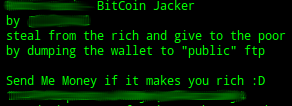
BitCoin Jackers Ask: “What’s in Your Wallet?”
By Adam McNeil
With all the recent media coverage and extreme changes of the BitCoin value, it should come as no surprise that malware authors are trying to capitalize on the trends. These people attempt to make money on all sorts of digital transactions and it’s probably a safe bet to expect their rapid expansion into the up-and-coming Digital Currency market.
The Webroot Threat Research Department has already seen many malware campaigns targeting BitCoin users. The recent explosion (and subsequent implosion) of the BitCoin value has expedited the need for custom compiled BitCoin harvesters and the malware authors are happy to abide.
More details: read more…
A peek inside a ‘life cycle aware’ underground market ad for a private keylogger
By Dancho Danchev
What’s greed to some cybercriminals, is profit maximization to others, especially in times when we’re witnessing the maturing state of the modern cybercrime ‘enterprise’. Many enter this vibrant marketplace as vendors without really realizing that, thanks to the increasing transparency within the cybercrime ecosystem, their basic and valued added services will be directly benchmarked against a competing vendor, sometime rendering their unique value proposition completely irrelevant. Others will take a different approach by releasing a ‘life cycle aware’ underground market ad and will still manage to generate some revenue, as well as secure a decent number of customers in the long-term.
In this post, I’ll profile a ‘life cycle aware’ underground market ad for a private keylogger, relying on a limited number of licenses for its business model.
More details:
Spamvertised ‘Your order for helicopter for the weekend’ themed emails lead to malware
Cybercriminals are currently mass mailing tens of thousands of emails, in an attempt to trick users into thinking that the order for their “air transportation services has been accepted and processed”. In reality though, once users execute the malicious attachments, their PCs will automatically become part of the botnet managed by the malicious actors.
More details: read more…