Segmented Russian “spam leads” offered for sale
What is the Russian underground up to when it comes to ‘spear phishing’ attacks? How prevalent is the tactic among Russian cybercriminals? What “data acquisition tactics” do they rely on, and just how sophisticated are their “data mining” capabilities?
Let’s find out by emphasizing on a recent underground market advertisement offering access to data which can greatly improve the click-through rate for a spear phishing campaign. The irony? It’s being pitched as “spam leads”.
More details:
Cybercriminals release new Java exploits centered exploit kit
Yesterday, a relatively unknown group of cybercriminals publicly announced the availability of a new Web malware exploitation kit. What’s so special about it is the fact that its current version is entirely based on Java exploits (CVE-2012-1723 and CVE-2013-0431), naturally, with “more exploits to be introduced any time soon”.
Let’s take a peek at the statistics and infection rates produced by this kit, as well as discuss its potential, or lack thereof, to cause widespread damage to endpoints internationally.
More details:
New DIY IRC-based DDoS bot spotted in the wild
Thanks to basic disruptive factors like standardization, DIY (do it yourself) underground market releases, Cybercrime-as-a-Service “value added” propositions, efficiency-centered client-side exploitation process, QA (Quality Assurance), and adaptation to the ubiquitous endpoint protection mechanisms, such as for instance, signatures-based antivirus scanning, the cybercrime ecosystem is currently enjoying the monetary joys of its mature state.
In this post, I’ll profile a recently advertised DIY IRC-based DDoS bot, with an emphasis on how market followers, like the author of the bot, attempt to steal market share from the competition. Successful or not, this trend has been taking place for years, and based on the positive type and number of “satisfied customer” comments for this bot, market followers can also secure a revenue stream thanks to the fact that the prospective buyers of such “me too” type of malicious software releases don’t know where to acquire the latest cutting-edge DIY DDoS bot technology from.
More details:
Recap from RSA2013: Android Malware Exposed

On Wednesday, February 27th, Webroot’s Security Intelligence Director (Grayson Milbourne) and Senior Mobile Analyst (Armando Orozco) presented at the RSA Conference in San Francisco. Their topic, Android Malware Exposed – An In-depth Look at its Evolution, is an expansion on their previous year’s presentation, highlighting the severity of Android malware growth. Focusing on the history of operating system releases and the diversity across the market, as well at the threat vectors and behaviors in the evolution of Android malware, the team has established strong predictions for 2013. read more…
How much does it cost to buy 10,000 U.S.-based malware-infected hosts?
Earlier this month, we profiled and exposed a newly launched underground service offering access to tens of thousands of malware-infected hosts, with an emphasis on the fact that U.S.-based hosts were relatively more expensive to acquire, largely due to the fact that U.S.-based users are known to have a higher online purchasing power. How much does it cost to buy 10,000 U.S.-based malware-infected hosts? Let’s find out.
In this post, I’ll profile yet another service offering access to malware-infected hosts internationally, that’s been operating since the middle of 2012, and despite the fact that it’s official Web site is currently offline, remains in operation until present day.
More details:
How mobile spammers verify the validity of harvested phone numbers
Have you ever received a blank call, and no one was on the other side of the line? What about a similar blank SMS received through your mobile carrier’s Mail2SMS gateway? There’s a high probability that it was a mobile spammer who’s automatically and efficiently verifying the validity of a recently harvested database of mobile numbers, with QA (Quality Assurance) in mind. These verified databases will be later on used as the foundation for a highly successful spam/scam/malicious software disseminating campaigns, thanks to the fact that the cybercriminals behind them will no longer be shooting into the dark. How do they do that? What kind of tools do they use?
Let’s find out by profiling a Russian DIY (do it yourself) software vendor, that’s been operating since 2011, and is currently offering a Session Initiation Protocol (SIP) based phone number verification tool, as well as USB-modem based phone number verification application.
More details:
Malicious ‘Data Processing Service’ ACH File ID themed emails serve client-side exploits and malware
A cybercriminal/gang of cybercriminals that we’ve been closely monitoring for a while now has just launched yet another spam campaign, this time impersonating the “Data Processing Service” company, in an attempt to trick its customers into interacting with the malicious emails. Once they do so, they are automatically exposed to the client-side exploits served by the Black Hole Exploit Kit.
In this post, I’ll profile their latest campaign and the dropped malware. I will also establish a direct connection between this and three other previously profiled malicious campaigns, as well as an ongoing money mule campaign, all of which appear to have been launched by the same cybercriminal/gang of cybercriminals.
More details:
How do we use, secure, and share the information that surrounds us?
 The mobile landscape has boomed in the last couple of years mostly in part because of Android devices and social networking. This has opened the door for everyone to have access to a smartphone and have the cyber world at their fingertips. Smartphones have become an extension of us, and we now have our email, banking, social networking, television and internet on the go. We live in a world of instant access.
The mobile landscape has boomed in the last couple of years mostly in part because of Android devices and social networking. This has opened the door for everyone to have access to a smartphone and have the cyber world at their fingertips. Smartphones have become an extension of us, and we now have our email, banking, social networking, television and internet on the go. We live in a world of instant access.
With this excitement and convenience, we may lose track something we take serious is our privacy and security. Looming in this mobile landscape are people who want benefit from our oversight and continuous usage. read more…
DIY malware cryptor as a Web service spotted in the wild
Just how easy is it to generate an undetected piece of malware these days? Too easy to be true, largely thanks to the rise of managed crypting services, and the re-emergence of the DIY (do it yourself) trend within the entire cybercrime ecosystem.
With hundreds of thousands of new malware variants processed by the industry on a daily basis, it’s fairly logical to conclude that over the years, the bad guys have adapted to signature-based antivirus scanning protection mechanisms, and have achieved disturbing levels of automation and efficiency. How do they do that?
Let’s find out by profiling a recently spotted Web-based DIY malware cryptor, emphasize on the future potential of such underground projects, as well as provide MD5s of malware samples known to have been generated using it.
More details:
Fake ‘Verizon Wireless Statement” themed emails lead to Black Hole Exploit Kit
On a periodic basis, cybercriminals are spamvertising malicious campaigns impersonating Verizon Wireless to tens of thousands of Verizon customers across the globe in an attempt to trick them into interacting with the fake emails. Throughout 2012, we intercepted two campaigns pretending to come from the company, followed by another campaign intercepted last month. This tactic largely relies on the life cycle of a particular campaign, intersecting with the publicly generated awareness of its maliciousness.
In this post, I’ll profile one of the most recently spamvertised campaigns impersonating Verizon Wireless. Not surprisingly, once users click on any of the links found in the malicious emails, they’re automatically exposed to the client-side exploits served by the Black Hole Exploit Kit.
More details:
New underground E-shop offers access to hundreds of hacked PayPal accounts
On a daily basis, largely thanks to the efficiency-centered malicious campaigns circulating in the wild, cybercriminals get access to tens of thousands of accounting credentials across multiple Web properties, and most disturbingly, online payment processing services like PayPal.
We’ve recently spotted a newly launched underground E-shop that’s exclusively selling access to hacked PayPal accounts. How much does it cost to purchase a hacked PayPal account on the underground marketplace these days? What pricing method is the cybercriminal behind the service using, and does the newly launched E-shop share any similarities with the E-shop selling access to hacked PayPal accounts that we profiled in 2012?
Let’s take a peek inside the E-shop.
More details:
Sample login page for the E-shop:
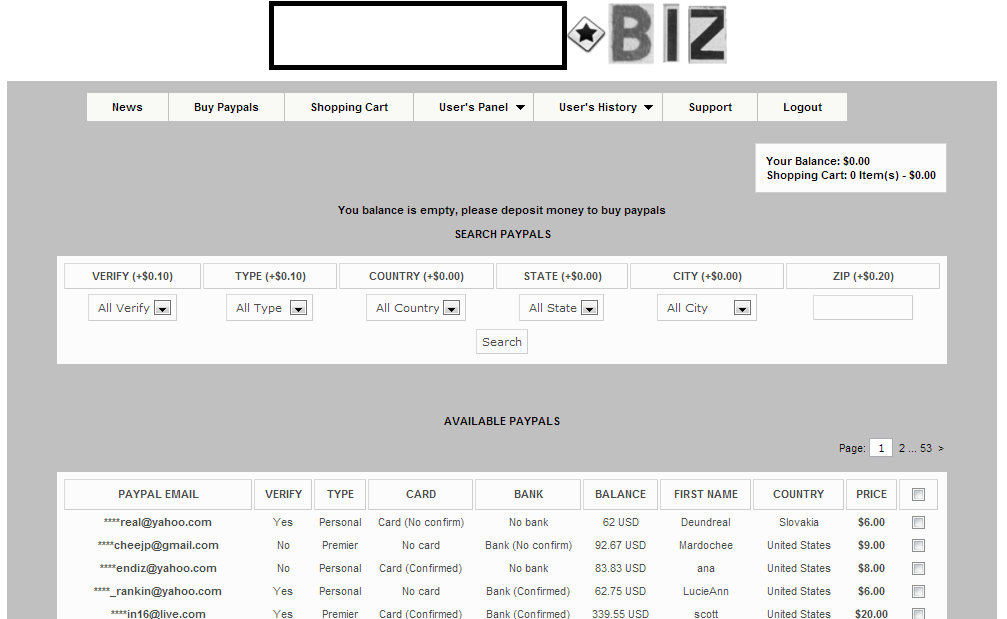
Sample entry page for the E-shop:
As you can see in the attached screenshot, the data is segmented in the following way: Email of the affected victim, verified/not verified account, type of account, Card confirmed or not, Bank confirmed or not, Balance, First name of the victim, the country of origin, and the actual selling price.
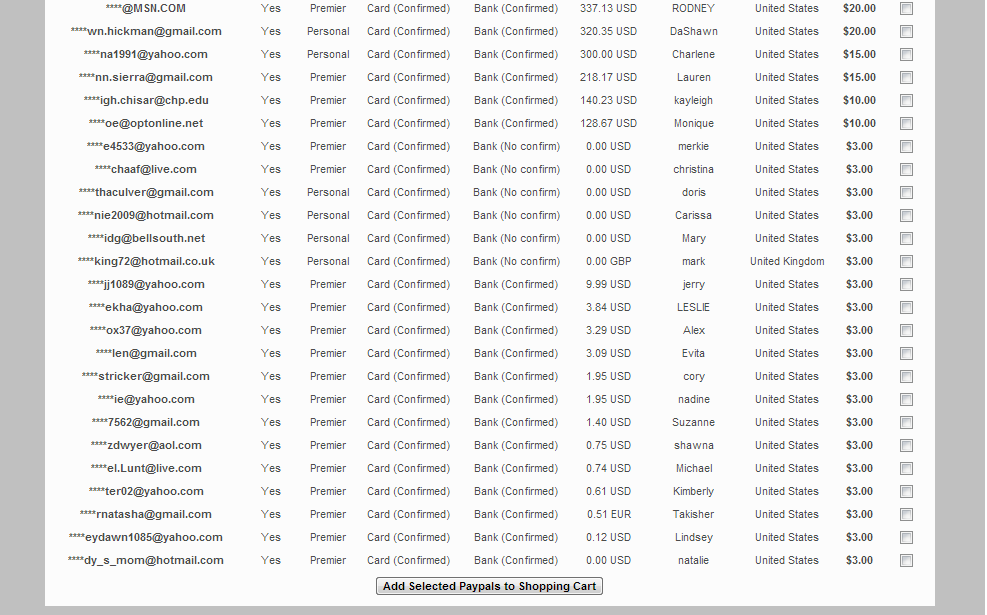
Screenshot of the inventory of the E-shop:
What about the prices? As you can see, accounts with virtually no assets — at least for the time being — are offered for sale at a static $3 per account. The price for accounts with a balance varies between $20-$15. It’s pretty obvious that the cybercriminal behind the E-shop is using perceived value for his pricing scheme, in the same way as another cybercriminal whose operations we profiled in 2012. Back then, he was selling access to a compromised bank account with a balance of $6,000 for $165. What we’ve got here is a decent example of how these inexperienced cybercriminals are looking for ways monetize the fraudulently obtained data as soon as possible, instead of “cashing out” the accounts by themselves, which could lead to possible risks to their OPSEC (Operational Security).
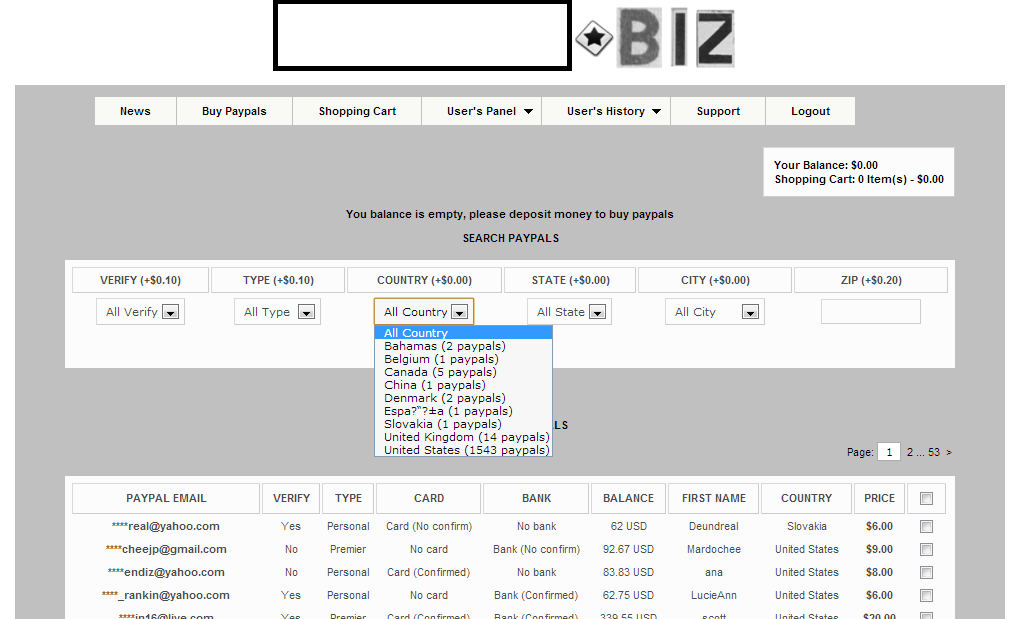
Second screenshot of the inventory of the E-shop:
The E-shop is exclusively targeting United States citizens, and currently has an inventory of 1,543 hacked PayPal accounts, followed by another 14 for the United Kingdom.
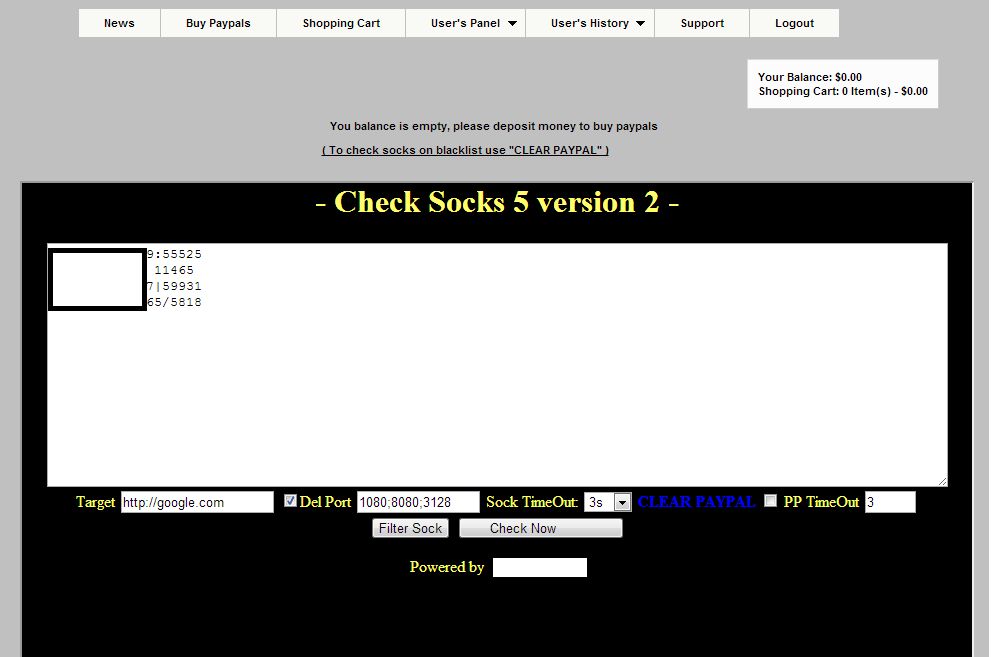
What’s particularly interesting regarding this E-shop is the fact that the cybercriminal behind it tried to come up with a value-added service, in this case a built-in Socks5 proxy checker, to be used when interacting with the hacked PayPal accounts for greater anonymity.
Sample screenshot of the built-in Socks5 proxy server checker:
These are not publicly obtainable Socks5 servers. Instead, they are compromised malware-infected hosts converted into anonymization proxies, allowing the cybercriminals who are about to “cash out” the hacked PayPal accounts to risk-forward the possibility of getting traced back to the IP of an innocent malware-infected victim.
How did the cybercriminal behind the service shape the prices for each hacked PayPal account? Pretty simple. Based on perceived value with asset liquidity in mind. Thanks to his inability/unwillingness to “cash out” the accounts by himself, launching an E-shop to monetize the fraudulently obtained financial data seems a logical development. Unlike the E-shop selling access to hacked PayPal accounts that we profiled in 2012, this one isn’t selling any other type of compromised accounting data, other than PayPal accounts.
We’ll continue monitoring the emergence of these E-shops, and post updates as soon as new developments take place.

Malicious ‘RE: Your Wire Transfer’ themed emails serve client-side exploits and malware
Over the last couple of days, we’ve been monitoring a persistent attempt to infect tens of thousands of users with malware through a systematic rotation of multiple social engineering themes. What all of these campaigns have in common is the fact that they all share the same malicious infrastructure.
Let’s profile one of the most recently spamvertised campaigns, and expose the cybercriminals’ complete portfolio of malicious domains, their related name servers, dropped MD5 and its associated run time behavior.
More details: