
by Blog Staff | Aug 8, 2011 | Industry Intel, Threat Lab
By Marco Giuliani












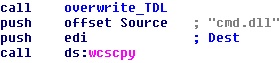 In our previous technical analysis of the ZeroAccess rootkit, we highlighted how it acts as a framework by infecting the machine — setting up its own private space in the disk, first through a dedicated file system on the disk, and more recently by using a hidden and locked directory. This is where the rootkit stores the modules it downloads from the command and control servers. Until now, the plugins we’ve monitored have been ad-clickers and search engine hijackers.
In our previous technical analysis of the ZeroAccess rootkit, we highlighted how it acts as a framework by infecting the machine — setting up its own private space in the disk, first through a dedicated file system on the disk, and more recently by using a hidden and locked directory. This is where the rootkit stores the modules it downloads from the command and control servers. Until now, the plugins we’ve monitored have been ad-clickers and search engine hijackers.
We have also noted how the ZeroAccess rootkit acts very similar to the TDL3 rootkit, either by infecting a random system driver, using its own file system to store its plugins or by filtering the disk I/O by analysing the SCSI packets – though in a pretty different way. It’s more effective in the TDL3 rootkit and less effective in the ZeroAccess rootkit, however ZeroAccess has many more self-protection mechanisms in place.
While analyzing the ZeroAccess rootkit, I’ve always had the feeling it was inspired by the TDL3 rootkit. But while looking at the latest updates of it I’ve found something pretty interesting: The ZeroAccess team is looking at TDL rootkit as an enemy that needs to be defeated. The questions remains, is there a link between the two rootkits? We suspect the answer is yes.
(more…)

by Blog Staff | Aug 5, 2011 | Industry Intel, Threat Lab












 The Black Hat briefings, held Wednesday and Thursday this week, once again brought together some of the best and brightest in the security industry to share knowledge about novel attacks and better defenses against old and new attacks. And, once again, there were some eye opening moments at the conference.
The Black Hat briefings, held Wednesday and Thursday this week, once again brought together some of the best and brightest in the security industry to share knowledge about novel attacks and better defenses against old and new attacks. And, once again, there were some eye opening moments at the conference.
Right from the beginning, it was clear the scope of the conference had shifted from the previous year. Conference founder Jeff Moss described a new, more rigorous committee-driven process that Black Hat had begun to employ to scrutinize and vet talk proposals. Talks this year would be more technical, go deeper into security threats, and would encompass a broader range of topics than had been done in years past.
But soon after Moss introduced former ambassador and CIA counterterrorism expert Cofer Black, the opening keynote speaker to the conference, someone pulled a fire alarm in the hall where the speech was taking place. While lights flashed and warning sirens sounded, Black joked about the prerecorded messages playing over loudspeakers.
(more…)

by Blog Staff | Aug 3, 2011 | Industry Intel, Threat Lab












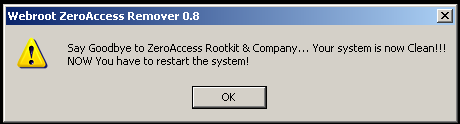 There are fewer types of malware infections more frustrating and annoying than a rootkit with backdoor capabilities. Over the past couple of years, we’ve seen the emergence of this new, tough-to-fight infectious code, and its transformation from nuisance to severe threat.
There are fewer types of malware infections more frustrating and annoying than a rootkit with backdoor capabilities. Over the past couple of years, we’ve seen the emergence of this new, tough-to-fight infectious code, and its transformation from nuisance to severe threat.
With the hard work and perseverance of Threat Research Analyst and master reverse-engineer Marco Giuliani, we’re proud to release the latest build of a tool we’ve used internally to clean the infections from the notable ZeroAccess rootkit off of victims’ computers. AntiZeroAccess exploits many of the vulnerabilities that Marco discovered in the rootkit to cleanly remove the rootkit code from infected machines.
The free tool removes the rootkit but does not restore the Access Control Lists (ACLs) that have been modified by the rootkit. For that, you’ll probably want to use a free tool like SetACL, which can make software functional that ZeroAccess disabled by modifying its ACL.

by Blog Staff | Aug 3, 2011 | Industry Intel, Threat Lab












 As I do every year, I’ve deliberately traveled to the most inhospitable climate zone in the continental US — that is, the city of Las Vegas — to attend the elite technical conference known as the Black Hat Briefings.
As I do every year, I’ve deliberately traveled to the most inhospitable climate zone in the continental US — that is, the city of Las Vegas — to attend the elite technical conference known as the Black Hat Briefings.
Black Hat is not just a technical conference, but a kind of calling for its attendees, which brings together experts in computer security, privacy, and attacks with high level officials in government and industry. In this rarefied environment, the security industry and its benefactors share information, tools, and techniques that help the entire industry coordinate their work against the interests of criminals, spies, and the vast numbers of Internet ne’er-do-wells.
I’ll be reporting from the conference about cool tools, new information about attacks, and deep analysis of malware all week. On Friday, the conference switches gears to become Defcon, which is a little less formal, a little less businesslike, and a lot more chaotic and interesting. Stay with us this week as we cover the most interesting conference in the security world.

by Blog Staff | Jul 29, 2011 | Industry Intel, Threat Lab












 Late Monday, after news about the death of troubled pop singer Amy Winehouse had been circling the globe for a little more than 48 hours, we saw the first malware appear that used the singer’s name as a social engineering trick to entice victims to run the malicious file. Abusing celebrity names, news, or even deaths isn’t a new (or even particularly interesting) social engineering tactic, but there was one unique aspect to this particular malware’s behavior that raised some eyebrows around here: It appears that Brazilian phisher-Trojan writers seem to be working more closely with their Chinese counterparts, using servers in China as dead drops for their stolen goods.
Late Monday, after news about the death of troubled pop singer Amy Winehouse had been circling the globe for a little more than 48 hours, we saw the first malware appear that used the singer’s name as a social engineering trick to entice victims to run the malicious file. Abusing celebrity names, news, or even deaths isn’t a new (or even particularly interesting) social engineering tactic, but there was one unique aspect to this particular malware’s behavior that raised some eyebrows around here: It appears that Brazilian phisher-Trojan writers seem to be working more closely with their Chinese counterparts, using servers in China as dead drops for their stolen goods.
The widely-reported case of the malware campaign continues to distribute new, randomized files via a download link managed through a dynamic DNS service, more than a week on. The file’s name, in Portugese, (“103684policia-inglesa-divulga-fotos-do-corpo-da-cantora-amy-winehouse-WVA.exe“) translates roughly to English police divulge photos of singer Amy Winehouse’s corpse, but victims who open this file are only going to see their computer become compromised.
The malware modifies the Hosts file in Windows to redirect traffic from 78 different Web sites — the vast majority of which are Brazilian banks and finance sites such as e-gold, with the rest being American Express, and Microsoft‘s Brazilian and US domains for Hotmail, Live, and MSN — to one of 9 IP addresses, almost all of which point to servers hosted in Chinese networks. One oddball outlier IP address in the modified Hosts file list points to an IP address belonging to the network operated by the Ford Motor Company, but that IP address was not allocated to an operational server when I did some tests.
(more…)

by Blog Staff | Jul 20, 2011 | Industry Intel, Threat Lab












 The criminals who push rogues at the world don’t really care about the reputations of the ISPs or Web hosting services they abuse. They leap from free service to free service until they’ve thoroughly worn out their welcome and, in some cases, destroyed the reputation of the service they abused. But they have behaved in one predictable way over the years: They’re stingy, and won’t pay for anything unless it’s absolutely necessary, despite the fact that they’re raking in cash by the boatload.
The criminals who push rogues at the world don’t really care about the reputations of the ISPs or Web hosting services they abuse. They leap from free service to free service until they’ve thoroughly worn out their welcome and, in some cases, destroyed the reputation of the service they abused. But they have behaved in one predictable way over the years: They’re stingy, and won’t pay for anything unless it’s absolutely necessary, despite the fact that they’re raking in cash by the boatload.
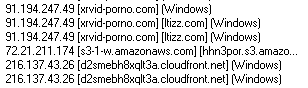
But that seemed to change this week when we saw a number of Web sites pop up on the radar. The sites employ the now well-worn scam of pretending to be some sort of video streaming service. In this case, they pretended to be a porn site, but the most surprising part was not what was hosted, but where: Amazon’s Cloudfront hosting service ended up, temporarily for a few hours, serving up malicious Web pages. Amazingly, it seems they actually paid for hosting instead of just stealing it.
Amazon shut the sites down quickly, but before they did, we visited one site called xrvid-porno.com. The page isn’t exactly family friendly, but the gist of the scam is that that page eventually redirected the browser to a server inside of Amazon’s cloud hosting service, and that’s where the trouble began.
(more…)

by Blog Staff | Jul 19, 2011 | Industry Intel, Threat Lab
By Marco Giuliani
 Among the most infamous kernel mode rootkits in the wild, most of them have had a slowdown in their development cycle – TDL rootkit, MBR rootkit, Rustock are just some examples. The same doesn’t apply for the ZeroAccess rootkit. The team behind it is working quite hard, which we know for a fact because I’ve seen it.
Among the most infamous kernel mode rootkits in the wild, most of them have had a slowdown in their development cycle – TDL rootkit, MBR rootkit, Rustock are just some examples. The same doesn’t apply for the ZeroAccess rootkit. The team behind it is working quite hard, which we know for a fact because I’ve seen it.
We already talked about this rootkit and its evolutions in several blog posts, along with a white paper that documents more in depth all the technical features of the malware. The last major update released by the team behind ZeroAccess dates back a couple of weeks; That update implemented a strong self-defense routine able to kill security software programs that try to get access to its code, blocking the security software from running by manipulating access control list, or ACL, settings.
Last week ZeroAccess received another update, and again it’s a major one. The rootkit shifted from a hidden encrypted file used as an NTFS filesystem volume to a more comfortable hidden directory created inside the Windows folder, where the rootkit still stores its configuration data and other malware in an encrypted form.
(more…)

by Blog Staff | Jul 8, 2011 | Industry Intel, Threat Lab












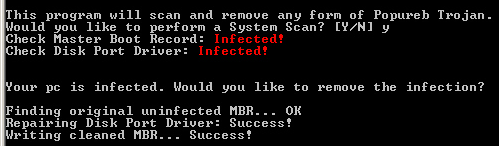 Last week, threat researcher and malware reverse-engineer Marco Giuliani wrote up a fairly technical description of a bootkit — a rootkit that infects the master boot record of the hard drive, making it very difficult to remove — called Popureb. Marco’s report made it clear that the bootkit does not require Windows users to format the hard drive and reinstall Windows from scratch, as Microsoft had initially claimed was required for victims of this drive-by infection.
Last week, threat researcher and malware reverse-engineer Marco Giuliani wrote up a fairly technical description of a bootkit — a rootkit that infects the master boot record of the hard drive, making it very difficult to remove — called Popureb. Marco’s report made it clear that the bootkit does not require Windows users to format the hard drive and reinstall Windows from scratch, as Microsoft had initially claimed was required for victims of this drive-by infection.
Andrea Allevi, one of our developers who works under Marco’s direction, subsequently wrote a tool that can remove the bootkit from an infected computer, which we’re releasing today to the public. We don’t offer technical support for the tool, but it’s fairly straightforward to use: Just launch it on a system infected with Popureb.E, using an account with Administrator privileges. It will ask your permission to clean the infected MBR, and once you say ‘yes’ it’ll do the rest. You’re welcome!

by Blog Staff | Jul 8, 2011 | Industry Intel, Threat Lab
By Marco Giuliani












 The latest generation of a rapidly evolving family of kernel-mode rootkits called, variously, ZeroAccess or Max++, seems to get more powerful and effective with each new variant. The rootkit infects a random system driver, overwriting its code with its own, infected driver, and hijacks the storage driver chain in order to hide its presence on the disk. But its own self-protection mechanism is its most interesting characteristic: It lays a virtual tripwire.
The latest generation of a rapidly evolving family of kernel-mode rootkits called, variously, ZeroAccess or Max++, seems to get more powerful and effective with each new variant. The rootkit infects a random system driver, overwriting its code with its own, infected driver, and hijacks the storage driver chain in order to hide its presence on the disk. But its own self-protection mechanism is its most interesting characteristic: It lays a virtual tripwire.
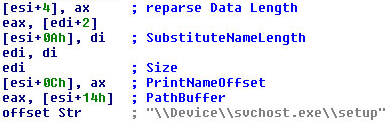
I’ve written about this rootkit in a few recent blog posts and in a white paper. On an infected computer, this new driver sets up a device called Devicesvchost.exe, and stores a fake PE file called svchost.exe – get it? The path is Devicesvchost.exesvchost.exe. The driver then attaches itself to the disk device stack. The driver creates a new system process, called svchost.exe, pointing to the path: \GlobalrootDevicesvchost.exesvchost.exe. This fake process serves as a kind of trap, specifically looking for the types of file operations performed by security software.
When a typical security scanner tries to analyze the rootkit-created svchost.exe file, the rootkit queues an initialized APC into the scanner’s own process, then calls the ExitProcess() function — essentially forcing the scanner to kill itself. The rootkit’s effectiveness, however, is hindered by a weakness in the way the rootkit filtered disk I/O. As it turned out, we can easily bypass the filtering technique and get to the masked data. We’ve also reversed the code the rootkit uses to generate domain names it will contact for command-and-control, and have provided a list of the domains it will use in the months of July, 2011 and August, 2011 so network managers can protect themselves proactively.
(more…)

by Blog Staff | Jul 6, 2011 | Industry Intel, Threat Lab












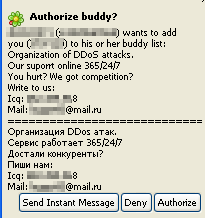 The other morning, I walked into the office to find a slew of instant messaging buddy requests from total strangers. This isn’t unexpected: I frequently get buddy requests on IM accounts I maintain for research purposes that contain malicious URLs and other useful research data. But this was one request I wasn’t expecting.
The other morning, I walked into the office to find a slew of instant messaging buddy requests from total strangers. This isn’t unexpected: I frequently get buddy requests on IM accounts I maintain for research purposes that contain malicious URLs and other useful research data. But this was one request I wasn’t expecting.
The inquiry, written in both English and Russian, was simply an advertisement for “Organization of DDOS attacks” from an ICQ account that has not been used since the friend request came in. The somewhat perplexing offer claims the service offers “support online 24/7/365” (finally, a DDOS service that works weekends and holidays, unlike those slacker DDOSers who only work during banker’s hours) and asks “You hurt? We got competition?”
Who’s this we you’re referring to, mister criminal mastermind?
The solicitation for business included a different ICQ user ID number than the one used to send the buddy request, as well as an email address. I’ve seen some strange solicitations for various kinds of business delivered this way, but never one so brazen over an ostensibly illegal (both in Russia and elsewhere) service.
It’s too bad I can’t tell the guy to just go DDOS himself, but the accounts used in the ad have all been shut down.

 In our previous technical analysis of the ZeroAccess rootkit, we highlighted how it acts as a framework by infecting the machine — setting up its own private space in the disk, first through a dedicated file system on the disk, and more recently by using a hidden and locked directory. This is where the rootkit stores the modules it downloads from the command and control servers. Until now, the plugins we’ve monitored have been ad-clickers and search engine hijackers.
In our previous technical analysis of the ZeroAccess rootkit, we highlighted how it acts as a framework by infecting the machine — setting up its own private space in the disk, first through a dedicated file system on the disk, and more recently by using a hidden and locked directory. This is where the rootkit stores the modules it downloads from the command and control servers. Until now, the plugins we’ve monitored have been ad-clickers and search engine hijackers.





















































































