
by Blog Staff | Jun 30, 2011 | Threat Lab
By Marco Giuliani












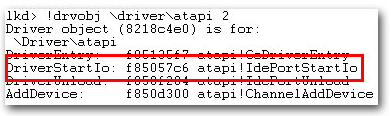 Last Wednesday, Microsoft published a blog post detailing a significant update to a piece of malware named Popureb. The malware adds code to the Master Boot Record, or MBR, a region of the hard disk that’s read by the PC during bootup, long before the operating system has had a chance to get started. Researchers sometimes refer to these kinds of malware as bootkits, or a rootkit which loads at such a low level during the boot process that it is invisible to the operating system, and therefore very difficult to remove.
Last Wednesday, Microsoft published a blog post detailing a significant update to a piece of malware named Popureb. The malware adds code to the Master Boot Record, or MBR, a region of the hard disk that’s read by the PC during bootup, long before the operating system has had a chance to get started. Researchers sometimes refer to these kinds of malware as bootkits, or a rootkit which loads at such a low level during the boot process that it is invisible to the operating system, and therefore very difficult to remove.
Microsoft researcher Chun Feng detailed some of the new features of Popureb.E, which includes a very low-level hook into the Windows driver responsible for disk writes and reads. When the driver on an infected system detects an attempt to write changes into the MBR — the kinds of changes a repair tool might try to make — it simply changes the command from write to read, effectively neutering any kind of tool running within Windows that might try to fix the infection.
(Update 2011-07-08: We’ve published a free command line tool that can remove Popureb.E from the master boot record of an infected computer.)
Microsoft’s initial cleanup guidance on Popureb.E was pretty drastic, and more than a little scary: Full removal of the bootkit requires a full reinstall of Windows, wiping out anything currently on the hard drive. We don’t think this is the case, and the Microsoft folks seem to have moderated their advice to include some manual fixes using the recovery console.
While the whole concept behind the Trojan is valid and technically powerful, the practical implementation of the malware is not as valid as the idea behind it. What follows is a fairly technical write-up that describes both the problem, and one solution we’ve come up with.
(more…)

by Blog Staff | Jun 24, 2011 | Threat Lab












 Ah, summer. Beaches, drinks with little umbrellas, 4th of July fireworks, baseball games, reading long cheesy novels in a lounge chair, teleconferencing with colleagues from your hotel room in Aruba. Wait, what?
Ah, summer. Beaches, drinks with little umbrellas, 4th of July fireworks, baseball games, reading long cheesy novels in a lounge chair, teleconferencing with colleagues from your hotel room in Aruba. Wait, what?
Yes, it’s true. It takes serious discipline to travel without schlepping along a laptop, smartphone, digital camera, MP3 player, portable hard drive, SD cards, and a host of support equipment. Well, it does for me, anyway. Along with those devices come pitfalls, from loss to data theft. So, in the spirit of safe summer travel, in advance of the big 4th of July travel weekend, what follows are Webroot’s five tips for summer travelers who can’t go anywhere without bringing along gadgets.
1. Watch where you WiFi
It can be tempting to take advantage of free WiFi access points in airports, hotels, or in cafes, but resist the urge to use those connections to do anything other than browse for a map or train schedule. Unsecured wireless connections — such as the open ones that some businesses provide as a service — can also leave you vulnerable to wireless snooping of your logins, email messages, or instant messages by other travellers or guests. The same can be said for untrusted computers in hotel business centers or cybercafes, which are magnets for data-stealing malware.
If the connection doesn’t ask you to provide a WPA key, assume the connection is not secure, and treat it as such; If you must use a free wireless connection, turn off any programs that automatically connect to the Internet (such as email clients or file-sharing tools) before you hook up. And please don’t use the untrustworthy PC in the hotel lobby to do anything more private than print your boarding pass to get home.
(more…)

by Blog Staff | Jun 21, 2011 | Threat Lab
By Ian Moyse, EMEA Channel Director












 It can seem at times that the only people who like change are Internet attackers. And they don’t just like it—they need it. Technology’s rapid changes give cybercriminals new attack vectors to exploit, and new ways to turn a profit out of someone else’s misfortune.
It can seem at times that the only people who like change are Internet attackers. And they don’t just like it—they need it. Technology’s rapid changes give cybercriminals new attack vectors to exploit, and new ways to turn a profit out of someone else’s misfortune.
Take phishing, for example. The concept is simple: Send an email disguised as a message from a bank, PayPal, or UPS. Wait for the user to click a link in the message, and enter their private details into a phishing site, and presto! The attacker attains financial or personal login details that can be used to commit fraud or theft.
Of course, it was only a matter of time before most people caught on to email scams. Users read again and again not to click on such links. Mail solutions became better at spotting phishing emails and filtering them into a junk email folder. Even free Web mail providers now catch the majority of these attacks.
Once cybercriminals noticed their traditional phishing approaches were returning lower response rates, they rapidly adjusted to new mediums. As a result, a new trend emerged: smishing (social media phishing) became the new trend in cyber attacks.
(more…)

by Blog Staff | Jun 20, 2011 | Threat Lab
By Stephen Ham and Andrew Brandt












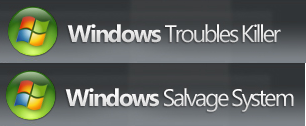 This week’s rogue, once again, mimics a system utility and not merely an antivirus product. Either way, the scam is the same: Convince the victim that their computer is broken, then coerce them to pay for useless snake oil.
This week’s rogue, once again, mimics a system utility and not merely an antivirus product. Either way, the scam is the same: Convince the victim that their computer is broken, then coerce them to pay for useless snake oil.
These rogue system utilities go by the names Windows Troubles Killer or Windows Salvage System; They are, for all intents and purposes, identical programs which have been “skinned” with different names. They actually appear to be a hybrid rogue, carefully blending a customized mix of malarkey and baloney into some sort of shenanigans smoothie. The program claims not only to be able to scan your computer for problems with software settings and other system optimization-sounding stuff, but also to perform some sort of check of your “Computer Safety” and “Network Security.” Oh yes, and there’s an antivirus component too, just to round out the complete package.
All in all, it’s a fairly rudimentary rogue to remove (whether you choose to do it manually or use our software), but it performs some unique system modifications that disable some legitimate security software, turns off some important Windows features, mimics some of Microsoft’s own software, and generally acts as a nuisance while reducing the actual security level of an infected computer. I’ll detail those after the jump.
(more…)

by Blog Staff | Jun 17, 2011 | Threat Lab












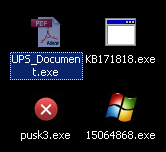 As if we didn’t have enough to deal with this week — after a Microsoft patch Tuesday that brought with it a boatload of security updates for Windows, Office, Silverlight, Visual Studio, and other programs — some enterprising malware distributor is emailing around bogus tracking number malware dressed up in the icon of a PDF document, and that malware is downloading payloads named after the updaters that Windows Update retrieves during an update.
As if we didn’t have enough to deal with this week — after a Microsoft patch Tuesday that brought with it a boatload of security updates for Windows, Office, Silverlight, Visual Studio, and other programs — some enterprising malware distributor is emailing around bogus tracking number malware dressed up in the icon of a PDF document, and that malware is downloading payloads named after the updaters that Windows Update retrieves during an update.
The malware arrived into one of our spam collection points with an attachment named UPS_document.zip. Way to be original there, criminals. Inside the Zip file was an executable downloader named UPS_Document.exe. Upon execution, it retrieves at least three payloads, including a copy of SpyEye (a password stealing Trojan), a tiny agent sending profiling information about the infected system, and a fraudulent “rogue system utility” called (on my XP testbed) Windows XP Restore.
The rogue takes on much of the appearance of a previous Rogue of the Week, named Windows Recovery. In fact, Windows XP Restore looks to be a very slightly modified duplicate of that software. If you’ve been hit with either rogue, there are some cool free tools for you to download that will repair some of the damage; Read on for details.
(more…)

by Blog Staff | Jun 10, 2011 | Threat Lab












 Most of yesterday, Threat Research Analyst Armando Orozco and I took a closer look at a piece of malware discovered by a university security researcher, Xuxian Jiang of North Carolina State. The malicious code, which the malware creator named Plankton, is embedded into a number of apps that were briefly posted to Google’s Android Market earlier this week, then rapidly pulled down after the researchers informed Google of their initial findings.
Most of yesterday, Threat Research Analyst Armando Orozco and I took a closer look at a piece of malware discovered by a university security researcher, Xuxian Jiang of North Carolina State. The malicious code, which the malware creator named Plankton, is embedded into a number of apps that were briefly posted to Google’s Android Market earlier this week, then rapidly pulled down after the researchers informed Google of their initial findings.
The Plankton code appears in a number of applications that were all focused on the popular game series Angry Birds. Some of the samples we looked at came as Android apps with names like Angry Birds Rio Unlocker v1.0, Angry Birds Multi User v1.00 or Angry Birds Cheater Trainer Helper V2.0.
When executed, the program displays the following text on the screen:
Welcome!
Simply click on the button below to unlock ALL levels in Angry Birds Rio. This will not delete your scores but might change the number of pineapples and bananas you have
None of the programs function as advertised. Instead, the malicious apps install additional code into the Android device into which they’re installed. These additional functions provide remote access and control of the Android device to, presumably, the distributor of the malicious apps, whose identity remains unknown at this time.
(more…)

by Blog Staff | Jun 9, 2011 | Threat Lab












 When malware ends up on an infected machine, one of the first things it will do is to ensure that it will start up again after the victim reboots their computer. For a criminal it makes sense. After all, what good is malware that stops working after a reboot?
When malware ends up on an infected machine, one of the first things it will do is to ensure that it will start up again after the victim reboots their computer. For a criminal it makes sense. After all, what good is malware that stops working after a reboot?
In Windows, there are tons of ways for malware to accomplish this small but critical task, most of which involve the Registry. Technical folks call the Registry keys that are used for this purpose load points or auto-start locations. There’s even a pretty good free app from Microsoft that will show you everything configured to start itself up using any of these load points.
The Threat Research Analysts here use their knowledge of load points to fine-tune definitions. Increasingly, we have to kill a load point then reboot the computer to remove a piece of malware. I wanted to call attention to some odd load point trends, where load points are stacked like dominoes, so the action that starts the execution process is several steps removed from the actual execution.
(more…)

by Blog Staff | Jun 7, 2011 | Threat Lab













This week, Webroot’s Thre@t Reply managed to steal some time with Ian Moyse, who knows a thing or two about the benefits of putting your computer and network security into the cloud, out where the threats are, rather than keeping your security inside your network or on individual computers.
[youtube=http://www.youtube.com/watch?v=JHAZxxWzBWk]
As always, feel free to submit your security question to @webroot, or by email to blog (at) webroot (dot) com, or in the comments below and we’ll get one of our threat researchers to answer it on an upcoming Thre@t Reply video. To see any of our other video replies to reader questions, visit the Webroot channels on YouTube or Vimeo.

by Blog Staff | May 27, 2011 | Threat Lab












 This week, we turn our attention temporarily away from the never-ending stream of rogue security products on the Windows platform and take a closer look at the Mac OS analogue, MacProtector (aka Mac Security, Mac Defender, MacGuard, and–if history serves–soon to be many, many other names).
This week, we turn our attention temporarily away from the never-ending stream of rogue security products on the Windows platform and take a closer look at the Mac OS analogue, MacProtector (aka Mac Security, Mac Defender, MacGuard, and–if history serves–soon to be many, many other names).
There’s been a lot of press coverage of these rogues — including a video blog post by us — in the past few weeks, so we thought it was high time we took a deeper dive.
Even though Webroot doesn’t offer an automated removal solution for the Mac, there’s good news for most Mac users — with only a little bit of effort, it’s fairly rudimentary to simply delete the rogue .app and be done with it. In this case, the Activity Monitor (Apple’s GUI process monitor, located by default in the Utilities folder inside the Applications folder) is your best friend.
The program appears as a stub .mpkg installer, which means that the application that installs the program isn’t a container with the full program stuffed inside. The installer drops an app named avRunner.app into the Applications directory, then executes it.
(more…)

by Blog Staff | May 24, 2011 | Threat Lab













This week’s Thre@t Reply video features Threat Research Analyst Armando Orozco answering one of the most frequently asked questions we receive: What is a firewall, and how does it work? Well, the actual question wasn’t put quite so politely, but that’s the gist of it. Armando is the primary researcher working on the Mobile Security for Android product, but he also researches malware on Windows and Mac malware, as well.
[youtube=http://www.youtube.com/watch?v=p9cK7wkrZRo]
As always, feel free to submit your security question to @webroot, or by email to blog (at) webroot (dot) com, or in the comments below and we’ll get one of our threat researchers to answer it on an upcoming Thre@t Reply video. To see any of our other video replies to reader questions, visit the Webroot channels on YouTube or Vimeo.

 Last Wednesday, Microsoft published a blog post detailing a significant update to a piece of malware named Popureb. The malware adds code to the Master Boot Record, or MBR, a region of the hard disk that’s read by the PC during bootup, long before the operating system has had a chance to get started. Researchers sometimes refer to these kinds of malware as bootkits, or a rootkit which loads at such a low level during the boot process that it is invisible to the operating system, and therefore very difficult to remove.
Last Wednesday, Microsoft published a blog post detailing a significant update to a piece of malware named Popureb. The malware adds code to the Master Boot Record, or MBR, a region of the hard disk that’s read by the PC during bootup, long before the operating system has had a chance to get started. Researchers sometimes refer to these kinds of malware as bootkits, or a rootkit which loads at such a low level during the boot process that it is invisible to the operating system, and therefore very difficult to remove.







































































