
by Blog Staff | May 19, 2011 | Threat Lab












 Word from the AMR group last week was that there weren’t many changes from the previous week; Many of the same rogue antivirus previously reported in this blog continue to plague the Internet.
Word from the AMR group last week was that there weren’t many changes from the previous week; Many of the same rogue antivirus previously reported in this blog continue to plague the Internet.
This week I decided to focus on a rogue that’s recently become a problem. It goes by the name Windows Recovery, though it’s also been called Ultra Defragger or HDD Rescue by other AV vendors. Bottom line, it’s still a fraudulent program which relies on deception and trickery to convince a victim to fork over some cash for a “fix.” It’s just not a rogue antivirus; Call it a rogue system utility. Fortunately, the damage caused by this rogue is actually relatively straighforward to manually clean up.
The gist of this rogue’s deception comes down to trying to convince the victim that their computer hard drive has experienced some sort of major malfunction. To accomplish this, the rogue does a lot of sneaky stuff: For instance, it flags all files on the boot drive with the “hidden” attribute, then uses registry tricks to prevent Windows from displaying any hidden icons.
It also moves any shortcuts that point to programs (both from the start menu and on the desktop) into the Temp folder, effectively neutering the utility of the Start menu. (We have a free tool that can fix this.) And it uses the Registry to disable the user’s ability to open the Task Manager, changes the system wallpaper (and prevents you from changing that wallpaper), and hides the entire desktop from view. (And we have another free tool that can fix this, too.)
(more…)

by Blog Staff | May 11, 2011 | Threat Lab
By Andrew Brandt and Armando Orozco












 A Trojaned application that displays a cutesy image of a 2011 calendar on an Android device’s desktop comes with a nasty surprise: The app sends text messages to a premium service that charges the phone’s owner money.
A Trojaned application that displays a cutesy image of a 2011 calendar on an Android device’s desktop comes with a nasty surprise: The app sends text messages to a premium service that charges the phone’s owner money.
As first reported by the Taiwan-based AegisLab, a single developer, which went by the name zsone, published the apps to Google’s Android Market. All apps from that developer were pulled from the Market today by Google, though only some of them appeared to contain the undesirable code.
We took a closer look at one of the apps, called iCalendar, that AegisLab was kind enough to share with us, and it didn’t take long to find the malicious code inside. Fortunately for most non-Chinese Android users, the premium numbers reportedly only work within China. We’re still testing to make sure that’s correct.
(more…)

by Blog Staff | May 10, 2011 | Threat Lab
By Andrew Brandt and Brenden Vaughan












 Our Advanced Malware Removal group reported seeing several cases of a rogue called Antivirus Center this past week. The rogue isn’t new – we began seeing samples of it last year – but has re-emerged as a threat.
Our Advanced Malware Removal group reported seeing several cases of a rogue called Antivirus Center this past week. The rogue isn’t new – we began seeing samples of it last year – but has re-emerged as a threat.
This rogue is characterized by a close mimicry of some aspects of Microsoft’s free Windows Defender product, including the use of a program icon that looks like a castle, as well as some distinctive characteristics of its active file components. For example, the rogue’s application consistently uses a naming convention that looks like a long string of random alphanumeric characters, with a .dat extension, located in the Application Data folder of the “All Users” profile. As we’ve written before, no programs should run from the Application Data folder, so anything in that location is automatically suspect.
That said, it’s still going through the same stupid rogue AV motions, with all the exaggerated detections and predictably hilarious bad grammar we’ve come to expect. Read on for more details.
(more…)

by Grayson Milbourne | May 9, 2011 | Threat Lab













In the second of a two-part series with Threat Research Analyst Grayson Milbourne, we answer a question about how to stay safe when shopping online. In the previous video, Grayson discussed how to identify a phishing page. In this episode, he continues his discussion by explaining how to tell whether the site you’re trying to purchase something from is operating safely and whether the site is able to protect your personal information when you click the “buy” button.
[vimeo 23488027]
As always, feel free to submit your security question to @webroot, or by email to blog (at) webroot (dot) com, or in the comments below and we’ll get one of our threat researchers to answer it on an upcoming Thre@t Reply video. To see any of our other video replies to reader questions, visit the Webroot channels on YouTube or Vimeo.

by Grayson Milbourne | May 2, 2011 | Threat Lab













In the latest Thre@t Reply video, Threat Research Analyst Grayson Milbourne answers a reader’s question about how to avoid being phished. The first step is to be able to identify whether you’re on the legitimate Web site you think you are, and if you’re not, what are the telltale signs that indicate you may be looking at a fake site designed solely to steal your user account and password information.
[youtube=http://www.youtube.com/watch?v=KklPP891bZ8]
To see the second half of the video, or any of our other video replies to reader questions, check out this post or visit the Webroot channels on YouTube or Vimeo.

by Blog Staff | Apr 25, 2011 | Threat Lab
By Brenden Vaughan and Andrew Brandt












 This week, our support and advanced malware removal (AMR) team did not have a lot of new data to report about rogue security products. The most commonly encountered infection continues to be one of the rogues we reported about last week.
This week, our support and advanced malware removal (AMR) team did not have a lot of new data to report about rogue security products. The most commonly encountered infection continues to be one of the rogues we reported about last week.
While we may refer to it as XP Total Security, it actually chooses one of a series of names at random, based on the operating system on the victim’s computer. Last week’s post contains a more comprehensive list of these names. As previously reported, you can remove the rogue by scanning (with our product, not theirs) while the computer is in Safe Mode.
Its main executable has a random, three-character filename, and gets installed into a random, three-character folder inside the Application Data folder for the user who is currently logged on at the time of the infection. The rogue’s install location is:
%UserProfile%Local SettingsApplication Data<random><random>.exe
AMR reported seeing another rogue called Antivirus IS. While this is the first time they have mentioned it, Brenden believes it is a bit older, and has been floating around since late last year. Its logo is a blue shield with a single red diagonal stripe; its tagline, “Innovative protection for your PC,” is utter nonsense.
(more…)

by Blog Staff | Apr 18, 2011 | Threat Lab












 It’s been said that sunlight sanitizes almost everything it shines on. Beginning this week, and every week from now on, we’ll focus a concentrated beam on the rogue antivirus programs our support staff and Threat Research team have been working to remediate.
It’s been said that sunlight sanitizes almost everything it shines on. Beginning this week, and every week from now on, we’ll focus a concentrated beam on the rogue antivirus programs our support staff and Threat Research team have been working to remediate.
Rogues have a tendency to switch up their names, user interface, and other outward characteristics, while retaining most of the same internal functionality — and by functionality I mean the fraudulent tricks these forms of malware use to make it difficult for someone to identify them as malicious or remove them from an infected computer. It’s not as though the charlatans behind these scams (or their parents) ever made anything that was actually useful or desirable.
So for our inaugural Rogue of the Week post, we bring you notes on MS Removal Tool and XP Total Security, courtesy of Threat Research Analysts Brenden Vaughan and Stephen Ham.
(more…)

by Blog Staff | Apr 11, 2011 | Threat Lab












The other day, Threat Reseacher Dan Para sent along the video clip below, which gave us all a good laugh. Dan had been researching a Korean-language Trojan downloader, but when he ran the file, he didn’t expect the downloader to retrieve not one…not two…but three separate rogue antivirus products.
The most amusing thing about the video is that these three rogues — named Smartscan, Antiguard, and Bootcare — decided to duke it out amongst themselves to be front-and-center on the desktop. But each time one of the apps would bring itself to the front, both of the others would respond in what can only be generously described as a slap fight. The results were, well, you can see for yourself.
In addition to pushing one another out of the top position, each vied with the other to concoct outrageous numbers of detections on what was, ostensibly, a clean testbed system. Antiguard reported 215 items of concern, while Smartscan reported 225 “detections” and Bootcare reported 245. Like their English-only counterparts, these rogues require you to make a purchase to clean up these purported problems.
[vimeo 22264051]

by Blog Staff | Apr 6, 2011 | Threat Lab
(Update, July 11, 2011: On May 25, 2011, we were contacted by representatives of Future Ads, LLC, the parent company of both Playsushi and Gamevance. Future Ads informed us that they, too, had been victims of a scam perpetrated by rogue affiliates who seemed to be involved with the malicious campaigns we described in this post. Future Ads claims that it has taken action to prevent this type of abuse from happening in the future.)












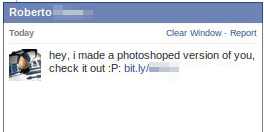 A worm that has been circulating on Facebook in the form of a Facebook application appears to have been engineered to drive traffic to a sleazy online advertising network which tries to connive people into installing software and disclosing a great deal of personal information about themselves in return for the promise of outrageously large gifts or prizes. As I write this, nearly 5 million people have fallen victim to this scam in just the past two days.
A worm that has been circulating on Facebook in the form of a Facebook application appears to have been engineered to drive traffic to a sleazy online advertising network which tries to connive people into installing software and disclosing a great deal of personal information about themselves in return for the promise of outrageously large gifts or prizes. As I write this, nearly 5 million people have fallen victim to this scam in just the past two days.
Last month, we published a report about a spam campaign designed to lure people into clicking a link to a bogus YouTube video. In that case, when you tried to play the video, your browser was instead redirected into an advertising network called CPALead. A convoluted series of steps eventually led victims to a page where they were prompted to fill out surveys (with outrageous promises for high-value gift cards or other valuable prizes) or download and install software from a Web site named Gamevance, which publishes online games and promises players cash prizes for high scores.
In this case, the campaign uses a clearly deceptive Facebook app — actually, dozens of duplicate apps with slightly different names — that (when you click the Accept button in Facebook) spams a shortlink to all of the victim’s contacts through Facebook’s chat mechanism. The spam messages all imply that the link leads to some sort of modified photo of the message recipient, but lead into a feedback loop which tries to spread itself further by infecting the Facebook accounts of new victims. Then it displays the ads.
(more…)

by Blog Staff | Apr 5, 2011 | Threat Lab












I’m very pleased to present today the first in a series of videos we’ve produced. The videos have the lofty goal of addressing the most pressing questions relating to malware, cybercrime, and online fraud. We’ll take you behind the scenes at Webroot and introduce you to some of our Threat Research team in the process.
In this first video, Webroot’s Director of Threat Research, Jeff Horne, answers a question submitted to us via Twitter direct message about the motives behind most cybercrime, and whether there are any examples of malware or other types of malicious online activity that have been motivated by anything other than financial gain.
[vimeo 21951624]
We’re planning to release a new video every other Monday from now on. When you’ve thought of that question you always wanted to know the answer to, tweet @webroot or send an email to blog (at) webroot.com, and we’ll answer the ones about cybercrime. We’ll try not to disappoint, but offer no promises. If you think of questions about something else, send them to Dr. Phil or Craig. We look forward to your letters!

 Word from the AMR group last week was that there weren’t many changes from the previous week; Many of the same rogue antivirus previously reported in this blog continue to plague the Internet.
Word from the AMR group last week was that there weren’t many changes from the previous week; Many of the same rogue antivirus previously reported in this blog continue to plague the Internet.

























































