
by Blog Staff | Jan 28, 2011 | Industry Intel, Threat Lab
By Jeff Horne, Director, Threat Research












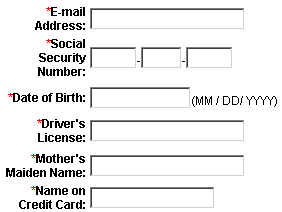 As tax season rolls around again in the US and UK, it seems like a good time to revisit the perils taxpayers face seemingly every year at around this time.
As tax season rolls around again in the US and UK, it seems like a good time to revisit the perils taxpayers face seemingly every year at around this time.
Phishing attacks against taxpayers are already in full swing — not that they haven’t been going continuously since last year. But this is high season for scams involving Web pages that look like the IRS or HMRC’s own Web site.
Scam messages typically contain dire warnings or outrageously large promises for a refund. The messages often are presented as if they originate from a tax authority, but contain links leading to phishing Web pages, or malicious attached files.
These scam pages typically appear to look exactly like a page on the real IRS or HMRC Web site. If you receive such a message, don’t reply to the sender, don’t email any sensitive information, and don’t follow any link in the message.
The pages promise to automatically transfer a tax refund to the recipient’s bank account, if you only would provide the scam artist with your complete banking, credit card, and personal details.
(more…)

by Blog Staff | Jan 15, 2011 | Industry Intel, Threat Lab












 It’s been a few months since Google implemented new ways that it displays search results, and in that time, it’s been difficult to find the kinds of hijacked search results we saw in huge numbers a year ago. But if you thought the search engine manipulators were laying down on the job, you’d be wrong.
It’s been a few months since Google implemented new ways that it displays search results, and in that time, it’s been difficult to find the kinds of hijacked search results we saw in huge numbers a year ago. But if you thought the search engine manipulators were laying down on the job, you’d be wrong.
A new campaign seems to have hijacked Google search terms of not just products or words, but of people’s names, towns, and phrases in both English and Spanish to lure victims into a trap. One of our Threat Research analysts stumbled upon the new scheme while searching for information about a friend. We were surprised to find that the top four results of that search led directly to that dreaded Sarlaac Pit of malware, the rogue antivirus fakealert.
At first, visiting the four top links in our searches led to the same fakealert. After an hour passed, however, the pages started to shake things up, leading to fakealerts that mix up their appearance. One screen displays something that looks like an alert from the Windows Security Center in Windows Vista; Another generates a dialog that looks like the Security Center alert from Windows 7. Still others take on the now-classic faux-Windows Defender appearance.
(more…)

by Blog Staff | Jan 6, 2011 | Industry Intel, Threat Lab












 On the morning of January 2nd, still bleary eyed, I checked my email to find a charming notification informing me that I’d received an electronic greeting card. Yay! I thought to myself: The first targeted malware of 2011 plopped right into my lap.
On the morning of January 2nd, still bleary eyed, I checked my email to find a charming notification informing me that I’d received an electronic greeting card. Yay! I thought to myself: The first targeted malware of 2011 plopped right into my lap.
I immediately pulled up my research machine, browsed to the URL in the message (don’t try this at home, kids), and found my test system swamped in malware. After classifying the files and their source URLs into our definitions — I didn’t want this to happen to you, after all — I turned the computer back off and slept until Tuesday, when I resumed my analysis.
As it turns out, the payloads delivered by the drive-by download are as common as sand at the beach, but some of the techniques used by the malware’s distributor to obfuscate the true nature of the executable payload files (which may have been stored on what appears to be a hijacked, legitimate server running Joomla) are fairly novel, and also a bit ridiculous.
(more…)

by Blog Staff | Jan 1, 2011 | Industry Intel, Threat Lab












 With 2010 finally behind us, and an unknown number of cyberattacks likely to come in the new year, I thought I’d run down a brief list of the malicious campaigns criminals pulled off last year that I’d really dread to see anyone repeat. Now that they’re in the past, they should stay there.
With 2010 finally behind us, and an unknown number of cyberattacks likely to come in the new year, I thought I’d run down a brief list of the malicious campaigns criminals pulled off last year that I’d really dread to see anyone repeat. Now that they’re in the past, they should stay there.
Operation Aurora: Google’s accusation (with Adobe, Juniper Networks, Rackspace, Yahoo! and Symantec) that China hacked its servers, allegedly stealing private emails stored on the company’s servers. The big surprise wasn’t that it was happening, but that companies were publicly talking about it.
Abused ccTLDs: 2010 saw lots more malicious content originating from previously un-abused country code top-level domains, which are assigned to national authorities, such as the .in (India) and .cc (Cocos (Keeling) Islands) top-level domains. The Cocos Islands’ .cc domain deserves particular note because the more than 2200 malicious domains (discovered during 2010) hosted under this ccTLD outnumber the approximately 600 human inhabitants of the tiny archipelago by nearly 4-to-1.
Koobface: “the little social network worm that could” employed new URL obfuscation techniques, introduced its own keylogger, and focused efforts on a smaller number of social media sites, while Facebook got more proactive at shutting down the worm’s operations quickly. Maybe this year they’ll disappear altogether.
(more…)
by Blog Staff | Dec 27, 2010 | Industry Intel
By Ian Moyse, EMEA Channel Director












I continue to read doom and gloom news about the future of the software distribution channel, in particular, how it’s being impacted by the global recession, by catalogue providers, and most importantly, the cloud security delivery model. We already know that cloud software will change the security landscape as we know it today, and it looks likely to change the software marketplace as well.
In my opinion, this change is long needed, and for the better. Resellers who find the right education and support for transitioning to a mixed world with both traditional and cloud delivery mechanisms will find this a much-needed improvement.
The security landscape is constantly changing. With new attacks coming from far more sophisticated sources and in greater volumes than ever before, channel partners now have an unprecedented opportunity to help their customers protect themselves with cloud-based services, which are far more effective and easier to maintain than traditional, on-premises products.
But two potential roadblocks may stand in the way of progress: Many CIOs or IT administrators and other potential customers may not be well versed in the cloud, and they’ve likely become sensitive to budget constraints during the recession. Naturally, they tend to turn to a balance of price versus relationship and support.
(more…)

by Blog Staff | Dec 23, 2010 | Industry Intel, Threat Lab












 Yesterday, two different 0 day exploits against Internet Explorer were published, just in time for the holidays when most of you (and many security researchers as well) are taking time off from work. The exploit, named CVE-2010-3971, is fairly serious, affecting the latest builds of IE versions 6 through 8.
Yesterday, two different 0 day exploits against Internet Explorer were published, just in time for the holidays when most of you (and many security researchers as well) are taking time off from work. The exploit, named CVE-2010-3971, is fairly serious, affecting the latest builds of IE versions 6 through 8.
Well, I’d normally get all hot and bothered about the fact that this kind of event might force some of our research team to spend their precious vacation time working the problem and coming up with a comprehensive solution. Normally, but not this time.
This time we headed the Black Hats off at the pass, and put a stop to these shenanigans before they started. Word from the Webroot Web Security Service team — the builders of our very slick cloud protection service for businesses — is that their Javascript heuristics engine is able to block any Web page that’s trying to use the exploits to try to take over your computer. The screenshot above shows what happened when we tried to browse to the proof-of-concept exploit page on a machine protected by the Web Security Service.
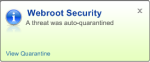 Of course, that’s great for corporate folks, but what about our home users running Webroot Antivirus or Internet Security Essentials or Complete? Well, we block it there, too. If you happened to stumble upon a Web page with the exploit running inside it, you might see a popup like the screenshot here, which is just telling you that we’ve prevented the page containing the exploit from loading in your browser. For the people playing at home, please ensure that you’re running the latest version of your antivirus with the most current updates, with the File System Shield and the Execution Shield turned on (and turn Gamer Mode off while you’re surfing).
Of course, that’s great for corporate folks, but what about our home users running Webroot Antivirus or Internet Security Essentials or Complete? Well, we block it there, too. If you happened to stumble upon a Web page with the exploit running inside it, you might see a popup like the screenshot here, which is just telling you that we’ve prevented the page containing the exploit from loading in your browser. For the people playing at home, please ensure that you’re running the latest version of your antivirus with the most current updates, with the File System Shield and the Execution Shield turned on (and turn Gamer Mode off while you’re surfing).
So, tough luck exploit writer guys. Better luck next time. I know someone is getting a bigger lump of coal than usual in his stocking this year, and I can’t think of anybody who deserves it more.

by Blog Staff | Dec 21, 2010 | Industry Intel, Threat Lab












 Where’s the work ethic, malware geniuses? If this latest example of shenanigans is the best you can deliver, you’re not even trying to generate convincing scams — or even something that makes sense — anymore.
Where’s the work ethic, malware geniuses? If this latest example of shenanigans is the best you can deliver, you’re not even trying to generate convincing scams — or even something that makes sense — anymore.
One of our Threat Research Analysts pointed me to a Web page hosting a fake update program for Firefox the other day, and the only thing it was useful for was a pretty good laugh.
In replicating the Firefox “you’re now running…” page, the malware distributor managed only to build something that looks remarkably similar to a more sophisticated, and ultimately more plausible, scam we first described this past summer. But the scam is full of fail.
The malicious page, which had been hosted at firefoxlife.cz.cc (and is now, thankfully, shut down), looks like the page that automatically pops up when you first launch the Firefox browser after you’ve applied an update. Ultimately, it not only fails the smell test, giving the user contradictory information, but also fails at the effective malware test, delivering multiple different samples, all of which crashed when we tried to run them on test systems or in debuggers.
(more…)

by Blog Staff | Dec 14, 2010 | Industry Intel, Threat Lab
By Ian Moyse, EMEA Channel Director












 Recent studies demonstrate that upwards of 25% of Internet bandwidth in an office are consumed by employees misusing the internet. According to Gartner, the average growth of business email volume is 30% annually, with the average size of the email content growing in parallel. Add to this the growth of Web misuse from streaming media, downloads, file sharing, social networking, and spam, and it becomes pretty clear that the mismanaged cost to business of non-work-related Internet use is already bad and getting worse.
Recent studies demonstrate that upwards of 25% of Internet bandwidth in an office are consumed by employees misusing the internet. According to Gartner, the average growth of business email volume is 30% annually, with the average size of the email content growing in parallel. Add to this the growth of Web misuse from streaming media, downloads, file sharing, social networking, and spam, and it becomes pretty clear that the mismanaged cost to business of non-work-related Internet use is already bad and getting worse.
There are plenty of examples, including employees wasting more than two hours a day on recreational computer activities (according to a survey fielded by AOL & Salary.com) and that, according to an IDC report, “30% – 40% of Internet use in the workplace is unrelated to business.”
Studies and surveys such as these typically focus only on lost productivity — and there’s no doubt that’s bad enough. But they rarely discuss the significant hidden financial impact of bandwidth wastage from these activities.
(more…)

by Blog Staff | Dec 13, 2010 | Industry Intel, Threat Lab
By Gerhard Eschelbeck












 As 2010 winds down, I wanted to pull out the crystal ball and talk for a moment about where the security industry seems to be heading in the coming year, and where we anticipate threats and targets.
As 2010 winds down, I wanted to pull out the crystal ball and talk for a moment about where the security industry seems to be heading in the coming year, and where we anticipate threats and targets.
Mobile platforms: If you’re reading this, there’s a good chance you have either an iPhone, an Android phone, or a Blackberry in your pocket, case, or on your desk right now. If that’s true, then the data on that device is the next big target for criminals, and the newest front in the war on cybercrime. Users have embraced the advantages of mobile platforms, and even though IT admins may officially consider some or all of them “unsupported” in some organizations, you can’t abandon users who will choose convenience over strict IT policy. I predict that mobile platforms will continue to grow at a rapid pace, and we’ll soon reach the threshold level where malware creators start to take notice in significant numbers. IT admins should embrace these new platforms, and take steps to protect users who insist upon having them, even though doing so may make their work harder.
Social engineering: Whether you use a single PC at home, or manage a network of 25,000 laptops and desktops at work, social engineering scams have become so convincing that it’s a wonder IT admins ever get a good night’s rest.
It doesn’t matter how comprehensive your patch and update schedule is — when a sufficiently convincing spam email reaches a gullible employee, all bets are off. With targeted attacks becoming more common, the best defense against this threat continues to be education. Every user, from the newest administrative assistant to the C-level executives, needs training in identifying and avoiding fraudulent email and other messages, harmful file attachments, and Internet behavior that can lead to trouble.
Cloud vs. Desktop: We’ve seen demand for cloud-based services increasing across all segments of the business. In small and medium-sized businesses, we’re continuing to see strong demand for cloud-based solutions, and we expect that to continue next year. Overworked admins like the ease of administration and the performance benefits of cloud security services. And for the first time, we’re seeing consumers getting interested in the advantages the cloud brings to PC protection, including the speed that updates make it to the user of an infected computer.
At the larger end of the enterprise business segment, IT administrators must juggle the requirements of government regulations with the performance advantages that cloud services have to offer. In those cases where security regulations may not permit some kinds of data to move out into the wider Internet, we’ve seen a demand for what we call private cloud architecture — something that offers the performance benefits and features of a cloud solution, within an organization, while, at the same time, satisfying regulatory constraints on how companies move or store data.
We also can see how criminals have developed a taste for the vast volumes of sensitive data stored in the cloud, and anticipate that malware creators and other attackers will try to steal data stored in the cloud with increasing frequency.
Security Updates: More than 60 percent of malware attacks come from known vulnerabilities, so no matter whether you’re a one-person shop, or manage many thousands of desktops, maintaining not only the operating system but also the third party applications on which you (and your organization) depend should be a top priority. Besides office applications, attacks in the past year have focused on programs like Adobe Reader, Java, Flash, AutoCAD, media players, graphic design tools, and various browsers and browser plug-ins. IT departments should never let a new computer get to an employee that has anything older than the very latest build of these critical applications.
Consolidation: While not expressly a security trend, larger companies — some in the security space, and some that have not previously played there — have been augmenting their offerings. Intel’s purchase of McAfee, for example, appears to extend their platform beyond mere chipmaking. Other acquisitions, such as Webroot’s purchase of Brightcloud and Prevx, help companies acquire capabilities that can defend against, or remediate, a specific kind of threat. HP, IBM, and Symantec have done similar things, and with each acquisition, the companies gain another part of a toolkit they can use to respond to emerging threats. We expect to see more companies in this space merge and transform themselves over the next year.

by Blog Staff | Dec 4, 2010 | Industry Intel, Threat Lab












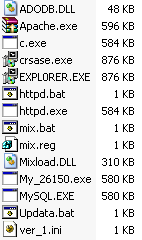 A complex and elaborately conceived family of malware that originates in China installs the Apache Web server, as well as half a dozen keylogger and downloader payloads, disguised as components of legitimate apps. We and a few other antivirus vendors are calling this type of malware Taobatuo.
A complex and elaborately conceived family of malware that originates in China installs the Apache Web server, as well as half a dozen keylogger and downloader payloads, disguised as components of legitimate apps. We and a few other antivirus vendors are calling this type of malware Taobatuo.
It just so happens that I’ve been setting up a Windows virtual machine with the latest versions of Apache, MySQL, and PHP for an unrelated project. I hadn’t installed these apps onto a Windows box before, and Apache in particular is notoriously finicky about Windows installations, so after several days of trial and error (mostly error) I was somewhat amused to discover, after finally getting Apache to work, that the malware sample I tested actually pulls down its own working, customized Apache installer…along with a bunch of phishing Trojans, keyloggers, and downloaders, all dressed up to look like the services you might see on a Microsoft-based Web server.
It just goes to show how much good these malware creators could accomplish, simply if they wanted to. But that’s clearly not the goal. The malware, along with text files containing instructions for the malware, came from taobao.lylwc.com. That’s not to be confused with Taobao.com, one of China’s most heavily trafficked Internet portals. This site and the real Taobao are not related in any way I can determine, other than the (ab)use of the Taobao name.
 The lylwc.com domain itself is quite a piece of work. It claims to offer free downloads or streams of current Hollywood movies, as well as an extensive library of films and TV shows. The operative word is “claims” — when you try to view those movies, the site attempts to push a download of a Trojaned installer for the QVOD media player (a streaming media app that’s popular in China). So let’s just say I wasn’t all that surprised to find the taobao subdomain of this Web site hosting a raft of malware.
The lylwc.com domain itself is quite a piece of work. It claims to offer free downloads or streams of current Hollywood movies, as well as an extensive library of films and TV shows. The operative word is “claims” — when you try to view those movies, the site attempts to push a download of a Trojaned installer for the QVOD media player (a streaming media app that’s popular in China). So let’s just say I wasn’t all that surprised to find the taobao subdomain of this Web site hosting a raft of malware.
(more…)

 As tax season rolls around again in the US and UK, it seems like a good time to revisit the perils taxpayers face seemingly every year at around this time.
As tax season rolls around again in the US and UK, it seems like a good time to revisit the perils taxpayers face seemingly every year at around this time.






























































