
by Blog Staff | Jun 3, 2010 | Industry Intel, Threat Lab












 A small-time Trojan has decided to butt heads with a big-time anti-phishing tool, and ended up with dirt on its face. The malware looks like a fairly generic clone of Trojan-Phisher-SABanks, with an extra feature that sounds like it might be a good selling point for cheap cybercrooks intent on stealing a few bank passwords for fun and profit. The trojan attempts to disable or delete parts of Trusteer’s Rapport anti-phishing software.
A small-time Trojan has decided to butt heads with a big-time anti-phishing tool, and ended up with dirt on its face. The malware looks like a fairly generic clone of Trojan-Phisher-SABanks, with an extra feature that sounds like it might be a good selling point for cheap cybercrooks intent on stealing a few bank passwords for fun and profit. The trojan attempts to disable or delete parts of Trusteer’s Rapport anti-phishing software.
And fails, miserably.
One version of the Trojan drops, then executes, a batch file that attempts to delete the main application. Another drops a batch which targets a binary file named config.js, buried a few levels below Trusteer’s program folder — four different ways.
Banks use Trusteer as a way to prevent phishers from using falsified Web pages or Trojans from capturing their customers’ passwords when those customers log in.
Unfortunately for the cyberschnooks who wrote this claptrap, and luckily for the rest of us, they didn’t count on Trusteer protecting its components or files in any way. Fortunately, in each of our tests, Rapport handily defeated the meager, unsuccessful attempts by the spy (which we call Trojan-Phisher-Rancor) to delete the application or its configuration file.
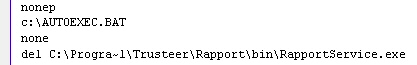 Banks contract with Trusteer to use Rapport to handle the security of online banking logins, so you can’t just use the software with any bank Web site, but the list of banks using the service includes some of the banks targeted most frequently by phishers: HSBC, SunTrust, BBVA Compass, Royal Bank of Scotland, and Fifth Third Bank (among others).
Banks contract with Trusteer to use Rapport to handle the security of online banking logins, so you can’t just use the software with any bank Web site, but the list of banks using the service includes some of the banks targeted most frequently by phishers: HSBC, SunTrust, BBVA Compass, Royal Bank of Scotland, and Fifth Third Bank (among others).
While this appears to be an isolated (and, for now, totally inept) incident of an easily defeated phishing Trojan that attempts to disable this particular anti-phishing software, it isn’t a good idea to underestimate the enemy. Clearly this attempt was a failure, but the next one might not be.


by Blog Staff | May 28, 2010 | Industry Intel, Threat Lab












 Annoying as they are, the spam emails circulating that supposedly come from Facebook don’t merely lead the recipient to one of those so-called Canadian Pharmacy pill-vendor websites. They now come with a bonus: An infection, courtesy of a malicious iframe which attempts a series of exploits against the browser, Adobe Reader, and Adobe Flash in an attempt to push a drive-by download down to the victim’s PC.
Annoying as they are, the spam emails circulating that supposedly come from Facebook don’t merely lead the recipient to one of those so-called Canadian Pharmacy pill-vendor websites. They now come with a bonus: An infection, courtesy of a malicious iframe which attempts a series of exploits against the browser, Adobe Reader, and Adobe Flash in an attempt to push a drive-by download down to the victim’s PC.
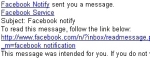
The messages, which say they come from a service called Facebook Notify (or, sometimes, just Facebook Service) inform the recipient that they’ve received a message. In order to read the message, the recipient is encouraged to click a link in the email that looks like it leads to Facebook.
It’s a sham: The spammers have hotlinked a Facebook URL so it points to another Web site. That Web site redirects the browser to the Canadian Pharmacy page, but that’s not all: In a few cases, while checking out what happens when one visits the page, I found that the test PC was infected afterwards.
As it turns out, a script embedded within the Canadian Pharmacy page loads an iframe that points to yet another site. And that iframe runs through a number of tricks to push down a Trojan installer we classify to Trojan-PWS-Daonol.
 Daonol is an obnoxious thief, because in addition to stealing passwords, the Trojan also prevents the browser from loading certain Web sites; redirects the browser to sites other than the one the user clicks in search result pages on Google, Bing, and Yahoo; and prevents Windows from running some applications.
Daonol is an obnoxious thief, because in addition to stealing passwords, the Trojan also prevents the browser from loading certain Web sites; redirects the browser to sites other than the one the user clicks in search result pages on Google, Bing, and Yahoo; and prevents Windows from running some applications.
(more…)

by Blog Staff | May 20, 2010 | Industry Intel, Threat Lab












 PC gamers have a new threat to contend with, one that has your personal information in its crosshairs and you can’t dispatch with a sniper rifle or BFG9000: A Trojan designed to steal game passwords that uses Microsoft’s own graphics engine, DirectX, against you.
PC gamers have a new threat to contend with, one that has your personal information in its crosshairs and you can’t dispatch with a sniper rifle or BFG9000: A Trojan designed to steal game passwords that uses Microsoft’s own graphics engine, DirectX, against you.
The Trojan, which appears to have originated in China, modifies one or more of the DirectX driver files — such as DirectSound, Direct3D, or DirectDraw — so it only loads when Windows fires up the modified DirectX driver. Because DirectX is typically used by games, it means this sleeper cell Trojan activates when you fire up a PC game, then terminates when you stop playing. As a result of using this unusual load point to start itself up, instead of a more typical Run key or Services entry in the Windows Registry, the Trojan is unusually low key.
In our tests, the installer drops one or more randomly named DLLs (the keylogger component) in the c:windowssystem directory, then modifies one or more DirectX files. Each modified DirectX file is used to load one keylogger payload, so if the installer happens to drop four keyloggers, it will also modify four DirectX files. It also adds instructions that call functions from another, unmodified, legitimate system file named mscat32.dll. MSCAT32 is completely benign: Windows uses mscat32.dll to create Microsoft Cabinet .cab files, which are similar to .zip archive files. We’ve named this aide-du-vol Trojan-PWS-Cashcab (though some of our competitors call it Kykymber).
As a result of the modifications, the keylogger component loads whenever any program initializes the modified DirectX driver file. Fortunately, it also loads when you run the DirectX Diagnostics program included with DirectX, DxDiag (click Start, Run, then type dxdiag and click OK to start it up). That’s also the easiest way to determine if your PC is infected.
(more…)

by Blog Staff | May 17, 2010 | Industry Intel, Threat Lab












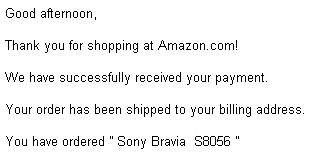 An ongoing campaign where malware distributors use email spam to deliver dangerous programs to unwitting victims has begun to change its tune, switching the scam to incorporate different brands. In the latest scam, the message appears to be an order confirmation from Amazon.com for the purchase of an expensive consumer electronics item, or a contract (spelled, tellingly, “conract“) for expensive home improvement work, purportedly to be done on the recipient’s home.
An ongoing campaign where malware distributors use email spam to deliver dangerous programs to unwitting victims has begun to change its tune, switching the scam to incorporate different brands. In the latest scam, the message appears to be an order confirmation from Amazon.com for the purchase of an expensive consumer electronics item, or a contract (spelled, tellingly, “conract“) for expensive home improvement work, purportedly to be done on the recipient’s home.
A few weeks ago, the emails switched from a “shipping confirmation” hook to one which claims the contents of the attachment include a code worth $50 on Apple’s iTunes online store.
The spam messages for several months have included a .Zip compressed attachment. The file inside the .Zip, which looks like a Microsoft Word document, is a malicious program we classify to the definition Trojan-Downloader-Tacticlol.
An extremely dangerous downloader, the Web sites and domains from which Tacticlol (aka Oficla or Sasfis) retrieves its payloads have been remaining online longer than normal. Typically the download site is shut down within a few days, effectively neutralizing the downloader and preventing it from retrieving anything. Recent variants, however, have use Web domains that remain online for weeks or even months.
Malicious sites that remain active only increase the danger that someone who inadvertently opens the attachment a few weeks after the message arrives will still infect their computer.
In addition, the payloads delivered by the download site Tacticlol contacts are being rotated as the days go on. In the initial infection period, within about 36 hours after the spam messages arrive, the download sites deliver a number of different payloads, including the Trojan-Backdoor-Zbot keylogger, the Trojan-Pushu (aka Pushdo) spam bot, and rogue antivirus installers. After a week, the payloads switch to the installers for botnets, which zombify the infected machines and turn them into longer-term hacker workhorses. Recent payloads have included a “dead man switch” which can render the infected computer unbootable.
I’ll discuss the ramifications of opening attachments such as these in an upcoming blog post. Nevertheless, it should be second nature that you avoid opening any attachment that arrives through email unless you can confirm — by telephone, or some other method — that the attached document is legitimate and was deliberately sent to you. Also, train yourself to avoid opening any attachment with an .exe file extension, regardless of its appearance or origin.

by Blog Staff | May 12, 2010 | Industry Intel, Threat Lab












 If you received one or more email messages over the past week that claim to contain an attached gift certificate for the Apple iTunes store or an unsolicited résumé, you probably received the latest scam involving the Tacticlol downloader.
If you received one or more email messages over the past week that claim to contain an attached gift certificate for the Apple iTunes store or an unsolicited résumé, you probably received the latest scam involving the Tacticlol downloader.
The iTunes-themed spam messages use the forged return address of gifts.certificate@itunes.com and read, in part, You have received an iTunes Gift Certificate in the amount of $50.00. You can find your certificate code in the attachment below. The resume messages simply say Please review my CV, Thank you! — using the abbreviation for Curriculum Vitae, the British analogue to the word résumé.
 The Trojan’s ongoing campaign attempts to trick victims into opening Zip-compressed attached files, which themselves contain an executable installer. The attachments almost always use the icon of a Microsoft Word document, and we usually see the Trojan launch an instance of Word and modify the default document template (named normal.dot) in the course of the infection.
The Trojan’s ongoing campaign attempts to trick victims into opening Zip-compressed attached files, which themselves contain an executable installer. The attachments almost always use the icon of a Microsoft Word document, and we usually see the Trojan launch an instance of Word and modify the default document template (named normal.dot) in the course of the infection.
We followed this Trojan down its particular rabbit hole and discovered logs and other files that indicate that, in just one day of operation, the Trojan had infected more than 9000 computers around the world and had begun to download one of three payloads, one of which was immediately identifiable as the prolific spambot we call Trojan-Pushu (aka Pushdo or Cutwail). The other two payloads were a keylogging password stealer, and a rogue antivirus installer.
The campaign is clearly connected to the most recent spamming of something we saw a few weeks ago, in which the message (in hilariously misspelled English) claims the attachment is a recording contract of some kind, with a forged return address of what appears to be a record company. A similar campaign was waged over the past several weeks, in which the recipient was told that the document contains a new password for their Facebook account. However, the end result of opening the alleged iTunes Gift Certificate is no different than opening the Facebook document, the “Conract,” or the shipping label or invoice documents: Instant infection, with the promise of more infections to come.
(more…)

by Blog Staff | May 6, 2010 | Industry Intel, Threat Lab












 When you see an online order form that bears Microsoft’s logo and the words “pay to: Microsoft Inc.,” are you any more likely to enter a credit card number into the form and click submit? That’s the psychological experiment currently being undertaken by a company that calls itself DefenceLab, which subjects unsuspecting users to its peculiar blend of fakealert with rogue antivirus.
When you see an online order form that bears Microsoft’s logo and the words “pay to: Microsoft Inc.,” are you any more likely to enter a credit card number into the form and click submit? That’s the psychological experiment currently being undertaken by a company that calls itself DefenceLab, which subjects unsuspecting users to its peculiar blend of fakealert with rogue antivirus.
Last year, our friends at Sunbelt wrote two very interesting blog items about DefenceLab. At the time, DefenceLab was accused of lifting content from the products and Web sites of legitimate comapnies such as Microsoft and AVG, inserting that text into their own Web site. They had stolen AVG‘s “awards” links from that company’s Web site, and posted it on their own; They were also lifting, whole cloth, copy from Microsoft’s Web site, then replacing words in the pages (like “Microsoft”) with “DefenceLab.”
Well these slugs are at it again, only this time they’ve dragged a US-based electronic payment processor into their scam. The payment processor handles the credit card transactions from victims who fall prey to the scam’s fake alert message about a nonexistent infection. Most rogues use fly-by-night processors, based overseas, who provide scant contact information, and never respond to requests for a refund. DefenceLab, however, provides would-be snake oil purchasers with both an email address and toll-free telephone number, in case of a transaction problem.
The only problem I can imagine would be if anyone actually paid perfectly good money to buy their bogus app.
The DefenceLab rogue also uses some time-honored techniques to trap victims, essentially locking nontechnical users out of their computer. Click through to the next page to see exactly how they do it; I’ll even throw in, free of charge, a simple trick that will let you prevent the program from popping up fake antivirus alerts.
(more…)

by Blog Staff | May 4, 2010 | Industry Intel, Threat Lab
By Ian Moyse












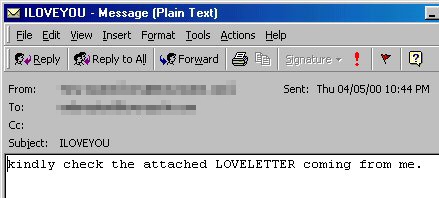 A decade on from the ILOVEYOU worm, what has changed—apart from ‘we’re older and (supposedly) wiser?’
A decade on from the ILOVEYOU worm, what has changed—apart from ‘we’re older and (supposedly) wiser?’
We have allowed the bad in the real world to progressively infect our online world, giving criminals a way to attack victims that is more dangerous for the victim and, coincidentally, safer for the attacker. As recently as a decade ago, bank robbers had to physically enter the bank premises and overcome its defenses. Today, they simply need to be clever enough to trick you, rather than break the defenses of the bank itself.
In humanizing the Internet we have dehumanized cybercrime.
The individual computer user was, and remains, the weak link. The concept of social engineering still poses the principal online threat affecting everyone.
At last week’s Infosecurity Europe show in the UK, I spoke about the latest threats, and how they clash with the realities of the Internet and the Web 2.0 world we live in today. Attendees who spoke to me afterward, many of whom provide support and IT services to business of all sizes, told me they live with these threats every day.
I asked the people watching my talk who thinks malware is still as much of a threat as it ever was, and the sea of hands that shot up spoke volumes: Ten years on, we face the same problem on an increasingly large scale. The attackers however have gotten smarter, and more malicious. We have seen more malware in the last 18 months than the last 18 years combined — and the attacks which deliver that malware to victims are equally creative, ingenious, and devious.
(more…)

by Blog Staff | Apr 30, 2010 | Industry Intel, Threat Lab












 If you’re a rock-and-roll star, anticipating the imminent arrival of a new recording contract from your lawyer, you can stop reading this post. If you’re not, I’m sorry to be the one to tell you, it was not your hours of practice playing Rock Band, or singing in the shower, that attracted the attention of the music industry. A spammed message, supposedly from a record company, which claims to have a contract attached, is (surprise!) malicious.
If you’re a rock-and-roll star, anticipating the imminent arrival of a new recording contract from your lawyer, you can stop reading this post. If you’re not, I’m sorry to be the one to tell you, it was not your hours of practice playing Rock Band, or singing in the shower, that attracted the attention of the music industry. A spammed message, supposedly from a record company, which claims to have a contract attached, is (surprise!) malicious.
The contract, in this case, is no contract at all, but a Trojan that can brick your computer if you run the file inside the Zip archive attached to the message.
We’ve been watching our favorite spam-propagated malware, Trojan-Downloader-Tacticlol (aka Oficla, Sasfis, Fregee, or Losabel). This is its new, extra stupid come-on of the moment. The message appears to come from Rock Out Records and says, in part:
“We have prepared a contract and added the paragraphs that you wanted to see in it. Our lawyers made alterations on the last page. If you agree with all the provisions we are ready to make the payment on Friday for the first consignment. We are enclosing the file with the prepared contract.”
In our tests of the Trojan, it pulls down a number of malicious payloads, some of which modify key Windows files responsible for the operation of the computer. As a consequence of the infection, your computer may not be able to boot up, instead leaving you stuck with a blue screen of despair.
(more…)

by Blog Staff | Apr 22, 2010 | Industry Intel, Threat Lab












 If you’re a customer or an employee of McAfee, chances are, you’re having a rough week. The company published a false positive, or FP, in its antivirus definitions that went out to customers a few days ago. The FP resulted in some computers going into a loop where the antivirus engine misidentified a key component of the Windows operating system as malicious, Windows replaced the quarantined file, and then the McAfee engine removed it again.
If you’re a customer or an employee of McAfee, chances are, you’re having a rough week. The company published a false positive, or FP, in its antivirus definitions that went out to customers a few days ago. The FP resulted in some computers going into a loop where the antivirus engine misidentified a key component of the Windows operating system as malicious, Windows replaced the quarantined file, and then the McAfee engine removed it again.
I really feel badly both for McAfee’s customers as well as their researchers. The customers certainly didn’t deserve or want their protection to go haywire. Security firms that make antimalware programs, like Webroot and McAfee do, confront the risk of publishing false positives every day. I don’t think there’s a single company that doesn’t strive for a zero percent false positive rate (aside from the snake oil pitchmen who sell rogue antivirus products, whose entire business model is predicated on lies and deception).
Every legitimate company in this space has had to retract some definition set at some point because it misidentifies or removes the wrong thing. We’ve done it, too; It’s nothing to be proud of, but it’s the reality of the situation in which anti-malware researchers work. The malware creators do their best to make this task as difficult as possible. We also know that every minute longer it takes to work on an updated definition, is another minute where our customers roam the Web unprotected from the dangers that lurk around virtually every corner. In the rush to press forward, we sometimes make mistakes. And as a result of those mistakes, we’ve made some improvements over time: Our desktop Webroot Antivirus product can’t, for example, accidentally quarantine some of the key system files Windows needs just to remain operational, as long as those system files remain unmodified by malware.
What happened with McAfee has been the subject of a lot of water-cooler discussion here, too. One of the bright points that has come out of the internal conversations I’ve shared with some of my colleagues is this: Putting the definitions into the cloud, instead of letting them reside on the “endpoint” (the desktop computer running the antivirus software) has a clear advantage in cases like this. If a definition hosted in the cloud goes horribly, horribly wrong, we can pull that definition from circulation immediately, thereby limiting the scope of the damage, and hopefully containing it to the small number of users who happen to be in the unlucky position to be first to use a defective definition set.
Another point that someone made concerned the Webroot Web Security Service, which is a Web filtering service we sell to businesses as a way to protect their entire network from dangerous Web sites hosting malware-pushing exploit kits or phishing pages. Web SaaS provides a critical layer of protection from Web-based threats in the unlikely event that you might have to temporarily remove a misbehaving endpoint anti-malware product. Our Email SaaS service does the same for threats that might come through corporate mail systems. SaaS security won’t ever totally replace some sort of security app running on the computer, but it does a bang-up job keeping you safe from most threats.
When it comes to offering protection, the state of the Internet today demands a far more rapid response to threats. We need to respond immediately to new attacks, so our customers are protected the minute we discover something new. And likewise, we need to be able to pull back changes immediately, so we can limit the damage if we make mistakes. This immediacy is the benefit of keeping some security components out in the cloud, and we’re working towards a goal that protects not just the computer, but the people using that computer, the minute new threats reveal themselves. Waiting days and days for protection just isn’t an option anymore. 

by Blog Staff | Apr 21, 2010 | Industry Intel, Threat Lab












 For the past couple of weeks, owners of Web sites have been hit with a wave of attacks that surreptitiously infect unsuspecting visitors with a wide variety of malware types. The first wave inflicted rogue antivirus on unlucky victims, but late last week victims who visited infectious sites were redirected into a drive-by download site that pushes clickers onto a vulnerable visitor’s computer.
For the past couple of weeks, owners of Web sites have been hit with a wave of attacks that surreptitiously infect unsuspecting visitors with a wide variety of malware types. The first wave inflicted rogue antivirus on unlucky victims, but late last week victims who visited infectious sites were redirected into a drive-by download site that pushes clickers onto a vulnerable visitor’s computer.
The affected web sites have been modified to add malicious, obfuscated Javascript code to the footer of each page. Some Web hosts are trying to notify customers or fix the problems. At first, the problem affected sites that run the open-source WordPress publishing system, but the attack has broadened into non-Wordpress (and non-blog) Web sites. The gobbledygook Javascript opens an iframe hosted from a different Web site, and the code that loads inside that iframe redirects the victim’s browser to yet another site, which loads the infection and executes it.
I’m going to name (domain) names in this post, so please, for your own sake, use this information only to block the domains at your gateway or in your Hosts file — don’t go visiting them just to see what happens. I guarantee you won’t like what happens.
In the earlier attacks that began the week of April 5th, the malicious script directed victims to a page hosting the Eleonor exploit kit; The kit uses several well-worn methods to try to push executable malware (typically the Tacticlol downloader, which malware distributors have been using of late to push down rogue antivirus programs) at susceptible browsers, or computers running vulnerable versions of Adobe Acrobat or the Java Runtime Engine.
Those attacks originated from several domains, including corpadsinc.com, mainnetsoll.com, and networkads.net — all of which are hosted on the same IP address in Turkey, and are still live and hosting the exploit page.
 But last week the script began directing users into a page on the domain name yahoo-statistic.com, a site which, despite its name, has nothing at all to do with the giant portal. That page, which loads in an iframe, opens other malicious sites which push the infection.
But last week the script began directing users into a page on the domain name yahoo-statistic.com, a site which, despite its name, has nothing at all to do with the giant portal. That page, which loads in an iframe, opens other malicious sites which push the infection.
The list of affected sites is global, including a newspaper in Florida; the English-language page of a government’s Ministry of Women’s Affairs Web site; the Web site of a Spanish lawyer’s association; and a car dealership Web site in Indonesia. And as of today, visitors to this growing list of Web sites are still getting hit with Trojans.
(more…)

 A small-time Trojan has decided to butt heads with a big-time anti-phishing tool, and ended up with dirt on its face. The malware looks like a fairly generic clone of Trojan-Phisher-SABanks, with an extra feature that sounds like it might be a good selling point for cheap cybercrooks intent on stealing a few bank passwords for fun and profit. The trojan attempts to disable or delete parts of Trusteer’s Rapport anti-phishing software.
A small-time Trojan has decided to butt heads with a big-time anti-phishing tool, and ended up with dirt on its face. The malware looks like a fairly generic clone of Trojan-Phisher-SABanks, with an extra feature that sounds like it might be a good selling point for cheap cybercrooks intent on stealing a few bank passwords for fun and profit. The trojan attempts to disable or delete parts of Trusteer’s Rapport anti-phishing software.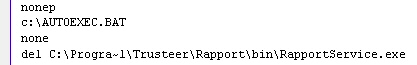 Banks contract with Trusteer to use Rapport to handle the security of online banking logins, so you can’t just use the software with any bank Web site, but the list of banks using the service includes some of the banks targeted most frequently by phishers: HSBC, SunTrust, BBVA Compass, Royal Bank of Scotland, and Fifth Third Bank (among others).
Banks contract with Trusteer to use Rapport to handle the security of online banking logins, so you can’t just use the software with any bank Web site, but the list of banks using the service includes some of the banks targeted most frequently by phishers: HSBC, SunTrust, BBVA Compass, Royal Bank of Scotland, and Fifth Third Bank (among others).
































































