by Connor Madsen | Dec 14, 2018 | Threat Lab
Clemson Supercomputer Susceptible to Cryptojacking
IT staff at Clemson University have been working to remove the recent introduction of a cryptominer on its supercomputer, known as Palmetto. As they compromised the system for the mining of Monero, the attackers’ ploy was only spotted due to spikes in computing power and rising operating costs for the supercomputer, since manually monitoring the entire system is nearly impossible. It’s still unknown who was responsible for the mining, but Clemson staff have already begun increasing security measures to discourage copy-cat crimes.
Cyberattack Strikes Italian Oil Company
Italian oil and gas company Saipemfell victim to a cyber-attack earlier this week that knocked several critical servers offline. The attack appears to have focused specifically on servers located in Middle Eastern countries in which the company operates. It’s presently believed the attackers were also involved in prior cyberattacks on Saudi Aramco, for whom Saipem is a supplier.
Data Breach Affects Topeka Residents
A data breach that could expose the personal details of nearly 10,000 residents of Topeka, Kansas was recently discovered. The breach could affect anyone who made online payments to the Topeka Utilities Department between October 31 and December 7. Officials are still working to determine the cause of the breach. The city’s utility department is in the process of contacting all 10,000 potential victims.
Google+ Reaches End of Life Sooner than Expected
While the consumer version of Google+was destined to be shut down in mid-2019, a new bug will hasten its end to April. This final vulnerability had the potential to expose entire user profiles to any applications searching for data, even if the account was set to private. This vulnerability left over 52 million accounts accessible to any number of app developers during the six days it was left exposed.
Android-based Trojan Steals Credentials
A new Trojan has been spotted on the Android OS that uses screen overlays for popular applications to trick users into entering credentials for apps like PayPal, Google Play, and even several banking apps. By displaying the overlay in the lock foreground screen, users are unable to close the pop-ups with normal methods, and can only do so by completing a form requesting login information. Additionally, the malware can identify if a legitimate app is currently installed and prompt the user to open it and log in, thereby removing a step in gaining access to the victim’s funds.
by Emily Kowalsky | Dec 13, 2018 | Webroot Blog
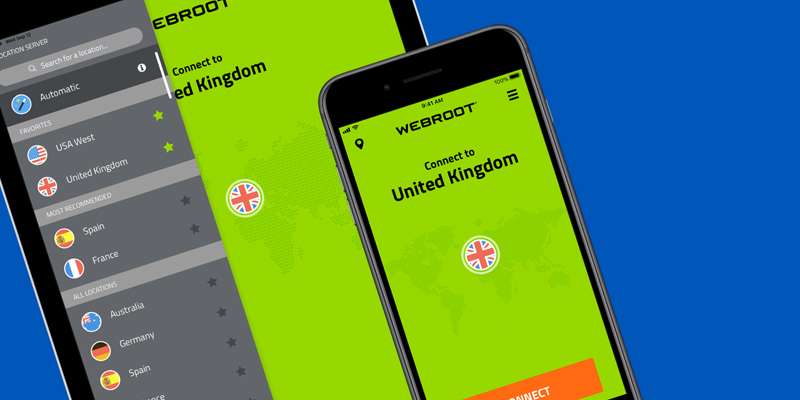
Virtual Private Networks (VPNs) are quickly becoming a fundamental necessity for staying safe online. From large corporations to family households, people are turning to VPNs to ensure their data is encrypted end to end. But as with any emerging technology, it’s easy to become overwhelmed with new and untested VPN options. So, how does Webroot® WiFi Security distinguish itself from other VPNs?
Whether or not you can trust your VPN provider should be the first thing to consider when selecting a VPN. A recent analysis of nearly 300 mobile VPN services on the Google Play store found that, unlike Webroot WiFi Security, almost one in five didn’t encrypt data as it was transmitted through their private network, a core tenant of VPN protection. At Webroot we have decades of cybersecurity experience. We’ve built confidence with every customer, from the world’s leading IT security vendors to families just like yours. Security and privacy are what we do best, and Webroot WiFi Security was purpose-built to always encrypt your data without screening, storing, or selling your private information.
“New products from unknown companies can be risky—what data are they capturing, what are they doing with the data, and how are they protecting that information?” notes Andy Mallinger, Webroot director of product. “Webroot has been in the security business for more than 20 years, and has built machine learning-based security systems for more than a decade. We designed our products to evolve with the ever-changing threat landscape. Adding VPN protection with Webroot WiFi Security, is a perfect next step in our continued evolution.”
Best-in-class security
Webroot WiFi Security was built to provide best-in-class security, while still being easy to use. A one-click setup automatically enables security features without any confusion or missed steps. For extra security, Android®, Mac®, and Windows® users can enable Webroot WiFi Security’s unique “killswitch” feature. If your VPN connection is lost, the kill switch prevents the transmission of your data over an unsecure network until you are reconnected to the VPN.
“Webroot WiFi Security also helps protect your privacy by obscuring your location,” says Randy Abrams, senior security analyst at Webroot. “Websites are able to precisely pinpoint your location and use that information to track your browsing habits. With Webroot WiFi Security, you can be in Broomfield, Colorado, but your VPN IP address can make it look like you are in any one of the more than 30 countries where our VPN servers are located.”
Privacy plus security
Webroot WiFi Security also offers Web Filtering powered by BrightCloud® Threat Intelligence*. This feature provides an extra layer of protection that keeps your financial information, passwords, and personal files from being exploited. Webroot goes a step above other VPNs by safeguarding users from visiting malicious or risky websites known to be associated with malware, phishing, key logging spyware, and botnets. Web Filtering is a feature that the user can choose to enable or disable.
The combination of consumer trust and the power of best-in-class threat intelligence makes Webroot WiFi Security one of the most unique and secure VPN offerings on the market. Webroot has a deep history of protecting its customers’ privacy, and we are excited to showcase this dedication in the VPN market.
Ready to make the switch to Webroot WiFi Security? Learn more after the jump.
*The BrightCloud Web Filtering feature is only available on Windows®, Mac®, and Android® systems.

by Connor Madsen | Dec 7, 2018 | Threat Lab
Touch ID Used to Scam Apple Users
Two apps were recently removed from the Apple App Store after several users reported being charged large sums of money after installing the app and scanning their fingerprint. Both apps were fitness-related and had users scan their fingerprint immediately so they could monitor calories or track fitness progress. But the apps launched a payment confirmation pop-up with the user’s finger still on the device to charge any card on file for the account. Luckily, the apps were only available for a brief period before being removed and refunds issued.
Signet Jewelers Expose Customer Order Data
Signet Jewelers, the parent company for Kay and Jared jewelers, was informed last month by an independent researcher of a critical flaw in their online sites. By simply altering the hyperlink for an order confirmation email, the researcher was able to view another individual’s order, including personal payment and shipping information. While Signet resolved the issue for future orders, it took additional weeks to remedy the flaw for past orders.
WeChat Ransomware Hits over 100k Chinese Computers
In the five days since December began, a new ransomware variant dubbed WeChat Ransom has been spreading quickly across China. With over 100,000 computers currently infected and thousands more succumbing each day, WeChat has made a significant mark. Though it demands a ransom of only roughly $16 USD, the variant quickly begins encrypting the local environment and attempts to steal login credentials for several China-based online services. Fortunately, Tencent banned the QR code being used to send ransom payments and disabled the account tied to it.
Nearly 100 Million Users Compromised in Quora Breach
Servers containing sensitive information for nearly 100 million Quora.comusers were recently compromised by unknown hackers. In addition to personal information about users, any posts or messages sent over the service were also breached. While informing affected users of the leak, Quora stated that all password data they store was fully encrypted using bcrypt, which makes it considerably more expensive and time-consuming for the hackers to break the algorithms and obtain the data.
Marriott Hotels Breach Leaves Half a Billion Users Vulnerable
In one of the largest data breaches to date, Marriott International is under fire for exposing the personal data of nearly 500 million individuals. A class-action lawsuit has been filed against the hotel chain. For many victims, their names, home addresses, and even passport information was available on an unsecured server for nearly four years after the company merged with Starwood, whose reservation systems were already compromised.

by Connor Madsen | Nov 30, 2018 | Threat Lab
USPS Website Leaves Personal Data Available to Anyone
Within the last week, The U.S. Postal Service (USPS) has been working to resolve a vulnerability that allowed any authenticated user to view and modify the personal information for any of the other 60 million users. Fortunately, USPS was quick to fix the vulnerability before any detectable alterations were made, which could have included changes to social security numbers, addresses, and even live tracking information on deliveries.
Amazon Exposes Customer Data
Many Amazon shoppers recently received an email informing them that their personal information was released, though the announcement was light on details. To make matters worse, Amazon’s only response was that the issue has been fixed. It did not mention what the actual issue was or what may have caused it. Official Amazon forums have been bombarded with concerned customers in advance of the approaching holiday season.
IRS Audit Reveals Fraud Protection Failure
It was revealed during a recent audit of the IRS that victims of at least 89 unique data breaches received no fraud protection for their tax filings. The number of affected victims is just over 11,000, some of whom have already fallen victim to tax filing fraud for either their 2016 or 2017 tax return. IRS staff have made promises to include the missing breaches in their tracking systems as quickly as possible and to begin assisting the victims of these incidents.
Atrium Health Breach Involves 2.65 Million Patients
The names and other sensitive personal information have been compromised for over 2.65 million patients of Atrium Health after a third-party provider experienced a data breach. Over the course of a week in late September, several servers belonging to AccuDoc were illegitimately accessed, though none of the data was downloaded. Fortunately, the servers didn’t contain payment or personal medical records and Atrium Health was informed just 2 days after the incident was discovered.
New Jersey Police Computers Hit with Ransomware
Since Thanksgiving Day, the computer systems for one New Jersey police force have been taken completely offline after experiencing a ransomware attack. Computer and email systems normally used by office administrators were also shutdown as a precaution. It’s possible that the attack originated from one of the two official devices that have been missing for several months following the previous mayor’s abrupt passing.

by LeVar Battle | Nov 27, 2018 | Threat Lab
At Webroot, we stay ahead of cybersecurity trends in order to keep our customers up-to-date and secure. As the end of the year approaches, our team of experts has gathered their top cybersecurity predictions for 2019. What threats and changes should you brace for?
General Data Protection Regulation Penalties
“A large US-based tech company will get hammered by the new GDPR fines.” – Megan Shields, Webroot Associate General Counsel
When the General Data Protection Regulation (GDPR) became law in the EU last May, many businesses scrambled to implement the required privacy protections. In anticipation of this challenge for businesses, it seemed as though the Data Protection Authorities (the governing organizations overseeing GDPR compliance) were giving them time to adjust to the new regulations. However, it appears that time has passed. European Data Protection Supervisor Giovanni Buttarelli spoke with Reuters in October and said the time for issuing penalizations is near. With GDPR privacy protection responsibilities now incumbent upon large tech companies with millions—if not billions—of users, as well as small to medium-sized businesses, noncompliance could mean huge penalties.
GDPR fines will depend on the specifics of each infringement, but companies could face damages of up to 4% of their worldwide annual turnover, or up to 20 million Euros, whichever is greater. For example, if the GDPR had been in place during the 2013 Yahoo breach affecting 3 billion users, Yahoo could have faced anywhere from $80 million to $160 million in fines. It’s also important to note that Buttarelli specifically mentions the potential for bans on processing personal data, at Data Protection Authorities’ discretion, which would effectively suspend a company’s data flows inside the EU.
AI Disruption
“Further adoption of AI leading to automation of professions involving low social intelligence and creativity. It will also give birth to more advanced social engineering attacks.” – Paul Barnes, Webroot Sr. Director of Product Strategy
The Fouth Industrial Revolution is here and the markets are beginning to feel it. Machine learning algorithms and applied artificial intelligence programs are already infiltrating and disrupting top industries. Several of the largest financial institutions in the world have integrated artificial intelligence into aspects of their businesses. Often these programs use natural language processing—giving them the ability to handle customer-facing roles more easily—to boost productivity.
From a risk perspective, new voice manipulation techniques and face mapping technologies, in conjunction with other AI disciplines, will usher in a new dawn of social engineering that could be used in advanced spear-phishing attacks to influence political campaigns or even policy makers directly.
AI Will Be Crucial to the Survival of Small Businesses
“AI and machine learning will continue to be the best way to respond to velocity and volume of malware attacks aimed at SMBs and MSP partners.” – George Anderson, Product Marketing Director
Our threat researchers don’t anticipate a decline in threat volume for small businesses in the coming year. Precise attacks, like those targeting RDP tools, have been on the rise and show no signs of tapering. Beyond that, the sheer volume of data handled by businesses of all types of small businesses raises the probability and likely severity of a breach.
If small and medium-sized businesses want to keep their IT teams from being inundated and overrun with alerts, false positives, and remediation requests, they’ll be forced to work AI and machine learning into their security solutions. Only machine learning can automate security intelligence accurately and effectively enough to enable categorization and proactive threat detection in near real time. By taking advantage of cloud computing platforms like Amazon Web Services, machine learning has the capability to scale with the increasing volume and complexity modern attacks, while remaining within reach in terms of price.
Ransomware is Out, Cryptojacking is In
“We’ll see a continued decline in commodity ransomware prevalence. While ransomware won’t disappear, endpoint solutions are better geared to defend against suspicious ransom-esque actions and, as such, malware authors will turn to either more targeted attacks or more subtle cryptocurrency mining alternatives.” – Eric Klonowski, Webroot Principal Threat Research Analyst
Although we’re unlikely to see the true death of ransomware, it does seem to be in decline. This is due in large part to the success of cryptocurrency and the overwhelming demand for the large amounts of computing power required for cryptomining. Hackers have seized upon this as a less risky alternative to ransomware, leading to the emergence of cryptojacking.
Cryptojacking is the now too-common practice of injecting software into an unsuspecting system and using its latent processing power to mine for cryptocurrencies. This resource theft drags systems down, but is often stealthy enough to go undetected. We are beginning to feel the pinch of cryptojacking in critical systems, with a cryptomining operation recently being discovered on the network of a water utility system in Europe. This trend is on track to continue into the New Year, with detected attacks increasing by 141% in the first half of 2018 alone.
Targeted Attacks
“Attacks will become more targeted. In 2018, ransomware took a back seat to cryptominers and banking Trojans to an extent, and we will continue see more targeted and calculated extortion of victims, as seen with the Dridex group. The balance between cryptominers and ransomware is dependent upon the price of cryptocurrency (most notably Bitcoin), but the money-making model of cryptominers favors its continued use.” – Jason Davison, Webroot Advanced Threat Research Analyst
The prominence of cryptojacking in cybercrime circles means that, when ransomware appears in the headlines, it will be for calculated, highly-targeted attacks. Cybercriminas are now researching systems ahead of time, often through backdoor access, enabling them to encrypt their ransomware against the specific antivirus applications put in place to detect it.
Government bodies and healthcare systems are prime candidates for targeted attacks, since they handle sensitive data from large swaths of the population. These attacks often have costs far beyond the ransom itself. The City of Atlanta is currently dealing with $17 million in post-breach costs. (Their perpetrators asked for $51,000 in Bitcoin, which the city refused to pay.)
The private sector won’t be spared from targeting, either. A recent Dharma Bip ransomware attack on a brewery involved attackers posting the brewery’s job listing on an international hiring website and submitting a resume attachment with a powerful ransomware payload.
Zero Day Vulnerabilities
“Because the cost of exploitation has risen so dramatically over the course of the last decade, we’ll continue to see a drop in the use of zero days in the wild (as well as associated private exploit leaks). Without a doubt, state actors will continue to hoard these for use on the highest-value targets, but expect to see a stop in Shadowbrokers-esqueoccurrences. Leaks probably served as a powerful wake-up call internally with regards to access to these utilities (or perhaps where they’re left behind). – Eric Klonowski, Webroot Principal Threat Research Analyst
Though the cost of effective, zero-day exploits is rising and demand for these exploits has never been higher, we predict a decrease in high-profile breaches. Invariably, as large software systems become more adept at preventing exploitation, the amount of expertise required to identify valuable software vulnerabilities increases with it. Between organizations like the Zero Day Initiative working to keep these flaws out of the hands of hackers and governmental bodies and intelligence agencies stockpiling security flaws for cyber warfare purposes, we are likely to see fewer zero day exploits in the coming year.
However, with the average time between the initial private discovery and the public disclosure of a zero day vulnerability being about 6.9 years, we may just need to wait before we hear about it.
The take-home? Pay attention, stay focused, and keep an eye on this space for up-to-the-minute information about cybersecurity issues as they arise.

by Tyler Moffitt | Nov 26, 2018 | Webroot Blog
‘Tis the season of giving, which means scammers may try to take advantage of your good will. A surprising fact about American donation habits is that everyday folks like yourself are the single largest driver of charitable donations in the United States. Giving USA’s Annual Report on Philanthropy found that individuals gave $286.65 billion in 2017, accounting for 70 percent of all donations in the country.
Last year, Giving Tuesday donations alone grew by 22 percent, with an average household donation of $111. With the seventh annual Giving Tuesday on November 27 fast approaching and technology that makes it increasingly easier to support your favorite causes, it’s more important than ever to keep your guard up before you click the “donate” button.
Unsolicited donation requests are fairly normal during the holiday season —especially since non-profits depend on year-end giving for the success of their organizations—but look out for a few behaviors as red flags. Overly aggressive pitches including multiple phone calls and emails, or high-pressure tactics that require your immediate donation, should always be avoided. Be on high alert for “phishy” emails and links; make sure to check the sender’s email address and hover over links to reveal their true destination before clicking on them. Even if a website looks legitimate, it may be a spoofed. Check that the domain matches the company you intended to visit. This can be trickier than it sounds. For instance, stjudehospital.com may appear to be genuine, but an easy Google search of “St. Jude Hospital” reveals their actual site to be stjude.org.
If you’re donating to a charity you’ve never worked with before, do a little research before committing your funds. Charity Navigator is a particularly useful resource; just type in the organization’s name and check out their rating. If they are not listed on Charity Navigator, it’s probably best to err on the side of caution and donate your hard-earned dollars elsewhere. Also, be sure to only enter sensitive or personal information into websites that have an SSL certificate; you’ll be able to tell if a page is secure if the link begins with “https”. (This is a great tip for shopping online this holiday season too.) Finally, before making any online donations, make sure you have a strong antivirus program installed that can detect phishing sites and that it’s up-to-date on all your devices.
If you are contacted by a charitable organization by telephone and want to make a donation, don’t give them your credit details over the phone. Have them mail you a donation form for you to evaluate and mail back. Remember: no legitimate charity will ask you to wire them money or pay them in gift cards. If you encounter a charity that is urging you to do so, cut all contact and block them on all platforms.
Bear in mind that not all charity scams are out for money, either—some are hoping to skim personal information. There is absolutely no reason to provide a charitable organization with information like your Social Security Number or driver’s license number—these are major red flags. Also, be especially cautious of requests to send an SMS code to donate via text message.
Social Media Scams
Social media is an easy and typically secure way to donate to legitimate charitable organizations, but scammers know how to use these platforms as well. Social media scams are on the rise, but a little bit of common sense goes a long way with donations on social channels. If you’re looking to donate to someone through a crowdfunding site, be sure the campaign fully answers these questions:
- Can you verify if the organizer of the campaign has an existing relationship with the intended donation recipient?
- Is there a plan for how the funds be used to aid the intended recipient?
- Are verifiable friends and family of the intended recipient making donations and leaving supportive comments?
- How will the intended recipient access the funds?
If you cannot easily find the answers to these questions, we recommend you avoid donating to that campaign.
Another pervasive social media scam is celebrity imposters who pretend to raise funds for charities or disaster relief. These imposters use the familiar faces of some of our favorite media personalities to gain our trust and access our wallets. If you have been solicited by a celebrity for donations, stop and take moment before you give. Make sure it’s their official social media page, which can be often verified on Twitter and Facebook by a small blue checkmark next to their name. You may also Google the celebrity’s name and “scam” to see if others have already reported a trap.

Source: @PatrickDempsey on Twitter
Attacks Targeting Seniors
While scams that target our aging loved ones are a problem year-round, the Consumer Financial Protection Bureau says scammers tend to ramp up their efforts during the holidays to take advantage of seasonal generosity. Most charity scams that target seniors are similar to the ones we all face, including phishing emails, phishing sites, and false charities. However, “Grandkid Scams” are a unique variety.
For this type of fraud, an older adult is contacted by a someone pretending to be a family member in desperate need of money or assistance, often impersonating a grandchild. Speak with the older adults in your life about the common signs of scams, like misspelled emails and requests for wire transfers, and teach them how to hover over a link to check its destination. Remind them to verify whether a family member is reaching out for money, and check in with them more often leading up to the holidays to catch any potential security issues early.
Stop Attacks Early
Vigilance is key in stopping a potential security breach in its tracks. If you believe you may have unwittingly sent money to a scam charity, reach out to the organization you used to send the money, such as your bank or credit card company. Tell them the transaction was fraudulent and ask them to cancel it, if possible. If you believe your personal information was exposed, you can freeze your credit to prevent any long-term damage. Also, if you think you may have encountered a charity scam of any type, be sure to report it to the FTC to help keep others safe.
Even if you don’t think you have suffered a breach, keep an eye on your credit score and monitor your banking and credit accounts closely this holiday season. Paying a little extra attention will help you act quickly if your information has been compromised, potentially saving you and your family major holiday heartache. For an added layer of protection, secure all of your family’s devices behind a trusted VPN, which will keep your private data encrypted and safe should anyone try to intercept information you send over WiFi.
Do you know of a common scam we missed? Have some advice you think we should have included? Let us know in the comments!

by Drew Frey | Nov 21, 2018 | Webroot Blog
As digital natives become more immersed in and dependent upon technology, they are likely to experience “cyber fatigue,” which can be thought of cybersecurity complacency. Paired with the invincible feeling that often accompanies being young, this can be a dangerous combination. It’s easy to mistakenly believe that hacked devices and identity theft are things that only happen to adults. Kids and teenagers, however, are just as high-risk and the impacts of cybersecurity breaches could potentially affect them for years into their future. So how can we protect our kids’ digital lives in the same way we protect their offline lives?
Frank Conversations
The internet may seem like a playground of endless entertainment, but we need to educate our children about the dangers that exist there as well. Have you had a friend or family member who’s been hacked or somehow had important information compromised? Talk to your kids about it, how it happened, why it happened, and the work needed to fix it. These real-life examples may be one of your most powerful education tools, as they help children more concretely understand the concept of cybersecurity threats. Demonstrating that these things can happen to anyone, including them, is the quickest way to get their cybersecurity guard up. Looking for fresh ideas on how to talk to your kids about cybersecurity? Check out the Webroot Community for advice and tips.
Common Scams
Teach your children about the most common cybersecurity threats, especially ones that are particularly pervasive on social media, including phishing, identity theft, and malicious websites. They should never accept private messages from people they don’t know, or click on links from friends or family that seem out of character or suspect. If they aren’t sure a message from a friend is actually from that individual, they should not hesitate to verify their identity by calling them, or by asking specific questions only that individual would know. The comments sections of websites like YouTube are also potential flashpoints. Clever comments can entice users into clicking on a risky link that navigates them to a malicious site.
Illegal Downloads
The temptation to download an illegal copy of a favorite movie, game, or album can be strong, but ethical and legal implications aside, it remains one of the most risky online behaviors. In fact, a recent study found that there was a 20% increase in malware infection rates associated with visits to infringing sites. Make sure your kids know the impact illegal downloads have on their security, and inform them of alternative streaming and download options. If you’re able, give your child an allowance for services like Steam for video games, or Amazon Video for films and shows. Providing them with alternative options is the best way to keep your child from giving into the temptation of illegally torrenting content.
Mobile Safety
A recent study found that people aged 15 to 24 spend about four hours a day on their phones. This works out to roughly 1,456 hours of mobile engagement a year, making mobile devices one of the most vulnerable entry points for cybersecurity breaches. Make sure your child’s phone is protected with a pin number, password, or biometrics on the lock screen, and that they know to leave Bluetooth turned off when not in use. Connecting to public WiFi networks could also leave your child vulnerable, but you can protect their devices from open networks by securing them with a VPN.
Digital Footprint
Many young people today use anonymous or “private” messaging services, like Whisper, Sarahah, or Snapchat, believing that they are protected by the apparent anonymity. However, cybersecurity experts have long been critical of these services, as nothing online is 100% anonymous.
“There is no single app that is capable of providing complete anonymity,” says Randy Abrams, Sr. Security Analyst at Webroot. “Even though someone may think they are anonymous, our online behavior allows people to track and identify us. Apps that claim to provide anonymity often collect and sell personally identifying data left behind from internet searches.”
“Some apps may offer much higher degrees of anonymity, but it takes a tremendous amount of knowledge and discipline to be anonymous,” he adds. “If an app requires access to your contacts, pictures, storage, location or the ability to make and receive phone calls or SMS messages, anonymity quickly starts to disappear.”
Free applications have to make a profit somewhere, which often means that they are storing, tracking and selling user data. This is particularly dangerous as users are lulled into a false sense of security, which can quickly be shattered when these services are affected by a cybersecurity breach. Make sure your kids know nothing they say online is truly private, and that a negative digital footprint can drastically alter the course of their lives.
Shared Responsibility
We believe cybersecurity is a shared responsibility, and that it is not just up to parents to educate digital natives. This is why we’ve developed a cybersecurity awareness initiative with the Aurora Public School System in Colorado. In addition to providing students with online safety tips, we’ve given them insights on potential career paths, and connected them with our engineers to solve problems using skills like math and coding that could benefit them later in their careers.
We encourage parents to explore and advocate for cybersecurity and STEM education opportunities for children in their local communities. For more educational content to help keep your family safe from cyber threats, visit the Home + Mobile section of our blog.

by Connor Madsen | Nov 16, 2018 | Threat Lab
Infowars Online Site Compromised by MageCart Attack
Earlier this week, a security researcher found payment card-stealing scripts running on the Infowars online site. The scripts managed to stay active for nearly 24 hours. At least 1,600 users of the site may have been affected during this period, though many were returning customers who wouldn’t have had to re-enter their payment information into the compromised forms. As of writing, the malicious scripts being used by Magecart are active on nearly 100 other online stores, with almost 20% getting re-infected within a two-week period.
Scammers Syphon €19 Million From French Film Company
A lawsuit recently revealed that savvy scammers successfully took nearly €19 million through a series of unauthorized transfers from a spoofed personal email address of the company’s CEO. After requesting additional information from the scammers, who continued to provide highly-detailed documents suggesting their legitimacy, several payments were transferred from the company’s main cash pool with promises of a quick payback from the scammers.
Chinese Headmaster Caught Cryptomining on School’s Systems
The headmaster of a Chinese school was fired after staff discovered an excessively high power bill previously written off as a faulty HVAC system was actually caused by several cryptomining rigs running off the school’s electricity. The headmaster brought the mining machines into the school in mid-2017 and evaded blame for the excess power consumption until the physical proof was discovered. While it appears no other harm was done, cryptomining software can be dangerous, as you can never be sure nothing else is bundled with it.
New Botnet Exploits Unpatched Bug in Over 100,000 Devices
Researchers have been monitoring a relatively new botnet that is currently controlling over 100,000 devices, including 116 device types from multiple manufacturers. By taking advantage of well-known bugs within Universal Plug n Play, hackers can quickly take control of the device and begin monitoring traffic from outside of the network.
Cathay Pacific Airlines Cyberattack Occurred Over Several Months
After originally claiming a data breach had taken place last month, affecting 9.4 million customers, new findings have shown the attacks have been happening regularly since March. Even though local laws didn’t require the company to notify authorities regarding a data breach, it is still surprising that it has taken almost nine months to determine what data had been exposed and what hadn’t.

by LeVar Battle | Nov 15, 2018 | Threat Lab
What business owners and MSPs should know about the year’s biggest online retail holiday
It’s no secret that Black Friday and Cyber Monday are marked by an uptick in online shopping. Cyber Monday 2017 marked the single largest day of online sales to date, with reported sales figures upwards of $6.5 billion. Data from Webroot charted a 58 percent increase in traffic to shopping sites on that day. And while Black Friday originated as a day to tussle with your neighbors for deals in person, online retailers like Amazon and eBay wouldn’t be left out and have begun offering their own deals.
What’s less often discussed is the corresponding rise in cybercrime that accompanies these online retail holidays. Webroot noted a surge in phishing and fraud sites of 203 percent between November 19 and December 5, with the number of such sites peaking on Cyber Monday. Instances of spyware and adware also rose 57 percent during the busy holiday shopping period, again peaking on Cyber Monday.
The Problem with Cyber Monday
For business owners and those in IT, Cyber Monday likely means lost productivity as employees bargain hunt at work rather than actually work. (It’s interesting to note that, according to CNET, the first Cyber Monday in 2005 was intentionally made to fall on a weekday so workers could browse shopping sites on faster computers.) As our data shows, more than just a few hours of lost productivity are at stake.
Employees expose business owners to greater risks of phishing scams, ransomware, and other types of attack that could significantly lengthen downtimes for all employees, or even shutter a business completely. According to a Better Business Bureau study on cybercrime, more than half of businesses would cease to be profitable within a month if a ransomware attack were to lock them out of essential data.
What’s a Business Owner to Do about Cyber Monday?
Whether you’re a business owner or provide IT services, you’re likely to see employees or clients indulging in deals this Cyber Monday. But there are strategies for limiting your risk on November 26. As with much of cybersecurity, you can manage your policy for online shopping based on what you consider acceptable levels of risk.
With network-level protection it’s possible to block access to any sites categorized as “shopping,” while still whitelisting trusted domains. Our research shows Amazon, the Apple iTunes Store, and Walmart rounded out the top three most visited shopping sites last Cyber Monday, so employers may want to consider whitelisting those sites specifically, while still blocking less reputable ones. Webroot offers DNS protection with the ability to filter according to more than 80 categories, including gambling, adult content, and weapons, as well as shopping. Set a policy to block the shopping category this Cyber Monday, with your own tailored exceptions and presto, problem solved.
There are also other, less prohibitive strategies for protecting employees and clients, too. Tools like Webroot’s Web Classification and Reputation services forecast the risks of visiting more than 27 billion URLs, which can help user determine if that deal really is a little too good to be true. IP Reputation Services make a similar determination based on an IP’s risk score.
Real-Time phishing protection and hands-on phishing simulations can go a long way toward improving security, too. The surge in these types of attacks represents cybercriminals focus on the weakest element of a company’s IT security: the end users themselves. Catching phishing attacks before they’re clicked and teaching users to be vigilant about threats by using custom phishing templates are paramount to your business’s security posture.
So there are a variety of methods for limiting disruption from online shopping in the workplace, so business owners and managed service providers shouldn’t let Cyber Monday come and go without preparation. Employees will almost certainly be on an online hunt for deals and cybercriminals know it.
Focus on security now, before a user’s big savings end up costing you.
by Connor Madsen | Nov 9, 2018 | Threat Lab
Data Breach Nabs HSBC Account Info
HSBC has been monitoring some unauthorized access occurring over a ten-day period on their customer’s online accounts. During this time, attackers used credentials that were likely part of prior breaches to access numerous accounts. HSBC worked quickly to disable online access to any accounts that showed suspicious activity. The bank also began notifying potential victims of the incident and have taken additional steps in securing their online access points.
Latest Chrome Iteration Cracks Down on Annoyances
With the rollout of Google’s Chrome 71, the company is looking to enhance the user experience by blocking all advertisements on sites that have continued to allow the hosting of offensive material. Chrome 71 will also be more efficient at blocking phishing attacks and misleading pop-up notifications that may redirect users. Fortunately, sites that are flagged can check their status and are given 30 days to correct for offending content.
University Shuts Down Network Over Cryptomining
A Canadian University was forced to shut down its entire network after IT staff discovered a cryptocurrency miner operating illicitly on several university systems. While they are still unsure who installed the cryptominer, they have removed the software from the systems and brought the remainder of the networks back online. Along with slowly restoring the remaining services taken offline, the university also forced a password change for all current users.
Cardless ATMs Lead to Rise in Phishing Attacks
Several arrests in Ohio have recently revealed a new scam that leverages SMS phishing attacks to withdraw money from ATMs that don’t require the use of a bank card. By sending a victim’s smartphone an SMS message containing a link to “unlock” their accounts, they are redirected to a phony site that steals their credentials. The scam has netted the attackers nearly $68,000 over a two-week period.
Twitter Bitcoin Scammers Take Over Verified Accounts
Even as Twitter-based Bitcoin scams have slowed, a new Elon Musk spoof account has popped up with the usual offer to multiply any amount of Bitcoins received and return the inflated amount. This scammer may have the benefit of taking over a verified account, but modifications to the profile name and obvious spelling errors reveal its clearly not legitimate, though it does leave raise questions regarding the verification system’s security.