by Blog Staff | Jan 16, 2014 | Threat Lab
In need of a good example, that malicious adversaries are constantly striving to ‘innovate’, thereby disrupting underground market segments, rebooting TTPs’ (tactics, techniques and procedures) life cycles, standardizing and industrializing their fraudulent/malicious ‘know-how’? We’re about to give you a pretty good one.
Regular readers of Webroot’s Threat Blog, are no strangers to the emerging TDoS (Telephony Denial of Service) underground market segment. Primarily relying on the active abuse of legitimate services, such as, for instance, Skype and ICQ, as well as to the efficient and mass abuse of non-attributable SIM cards, for the purpose of undermining the availability of a victim’s/organization’s mobile/communication’s infrastructure, the market segment continues flourishing. Rather a trend, than a fad, established DDoS (Distributed Denial of Service) for hire vendors, are already busy ‘vertically integrating’ within the underground marketplace, by starting to offer TDoS for hire services, either relying on a partnership with a TDoS vendor, or through the reliance on an in-house built infrastructure, established through the use of public/commercially available TDoS tools.
Back in July, 2012, a relatively unknown underground market entrant, publicly announced his ambitions to build a custom TDoS-ready GSM module, capable of supporting between 100-200 non-attributable SIM cards simultaneously, using custom coded management software. In a true product customer-ization style, he also started soliciting feedback, and touching base with potential customers of the custom module, in between promising them a “democratic” pricing scheme for the upcoming release. Then came the ‘innovation’. In November 2013, he made commercially available, what we believe is the first such public/commercially available TDoS-ready custom GSM module, whose very existence is poised to further fuel the growth of the TDoS market segment, tip potential competitors to the rise of the market segment, and directly contribute to the emergence of new TDoS vendors.
Let’s discuss the custom GSM module’s core functionalities, pricing scheme, and why its vendor can easily claim the market disruptor position in early 2014.
(more…)

by Blog Staff | Jan 15, 2014 | Threat Lab
In the marketing world, it’s widely known sex sells. This is so true the “adult” industry is a multi-billion dollar industry. This is also why malware authors have long used adult content to attract unwitting victims. Lately, this threat researcher has seen way too much of it. There has been an influx of Trojan-like APKs using adult content to trick users into sending premium SMS messages. Let’s take a deeper look at one of these apps.
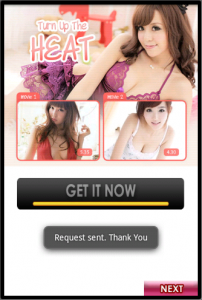
When you open the app it displays a page showing “GET IT NOW” in the middle, and “NEXT” at the lower right corner. If you tap “GET IT NOW”, it pops up a message saying “Request sent. Thank You”, and goes to the next screen. If you press “NEXT”, it goes to the next screen without a message. After several screens like this, it eventually gets to the last screen which may or may not have several buttons, but always has “T&C”, which I can only guess means “Terms & Conditions”. This opens up an SMS agreement screen.
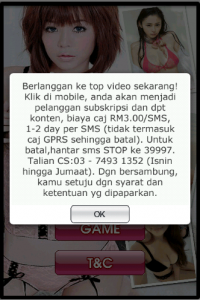
Using Google translate, the SMS agreement – which is in Indonesian – roughly translates to this:
Subscribe to a few videos now! Click on the mobile, you will be a customer subscription and retrievable content, cost RM3.00/SMS caj, 1-2 day per SMS (not including GPRS caj so canceled). To deselect, sms STOP conductivity to 39 997. Talian CS: 03-7493 1352 (Isnin to Friday). By concatenated, you agree with the terms and conditions that presented.
Click “OK” and you’ll be charged via premium SMS. So what about the “content” that’s promised? Sorry, not going to happen.
Not all, but quite a few of these apps are using the same package name pattern:
com.<naughty_word>.kma2
com.<naughty_word>.gmb2
com.<naughty_word>.lmt2
com.<naughty_word>.ymb2
com.<naughty_word>.mbf2
When looking for “content” out there, be smart about it. If an app is asking you to agree to subscribe to something via premium SMS messages, think twice. Of course, it always helps to have a malware scanner on your phone, like Webroot SecureAnywhere Mobile, as well.

by Blog Staff | Jan 13, 2014 | Threat Lab
Driven by popular demand, the underground market segment for TDoS (Telephony Denial of Service) attacks continues flourishing with established vendors continuing to actively develop and release new DIY (do-it-yourself) type of tools. Next to successfully empowering potential customers with the necessary ‘know-how’ needed to execute such type of attacks, vendors are also directly contributing to the development of the market segment with new market entrants setting up the foundations for their business models, using these very same tools, largely relying on the lack of situational awareness/understanding of the underground market transparency of prospective customers. Positioned in a situation as ‘price takers’, they’d be often willing to pay a premium to gain access to TDoS type of attack capabilities, with the intermediary in a perfect position to command a high profit margin, further improving the market segment’s capitalization.
A well known (Russian) vendor of TDoS products continues ‘innovating’ and utilizing basic customer-ization concepts, thereby introducing new features into well known TDoS ‘releases’, bug fixes, and overly-continuing to actively maintain a decent portfolio of multiple TDoS applications. Let’s take a peek at the most recently updated, 3G USB Modem/GSM/SIM card based of TDoS attack application, dubbed by the vendor as the most effective and cost-effective form of TDoS attack.
(more…)

by Blog Staff | Jan 9, 2014 | Threat Lab
First official working week of 2014 and cybercriminals are already busy pushing new releases into the underground marketplace. The goal? Setting up the foundation for successful monetization schemes to be offered through cybercrime-friendly boutique E-shops known for selling access to compromised accounting data obtained through the use of DIY (do-it-yourself) type of services. In this post, I’ll discuss a newly released passwords/game keys stealing tool whose Web-based command and control interface is successfully mimicking Windows 8’s Home Screen, and some of the most common ways through which this very same stolen accounting data would eventually be monetized.
(more…)

by Blog Staff | Jan 7, 2014 | Threat Lab
Happy New Year, everyone! Despite the lack of blog updates over the Holidays, we continued to intercept malicious campaigns over the same period of time, proving that the bad guys never take holidays. In this post, I’ll profile two prolific, social engineering driven type of malicious spam campaigns that we intercepted over the Holiday season, and naturally (proactively) protected you from.
More details:
(more…)

by Blog Staff | Jan 6, 2014 | Threat Lab
Over the Christmas period, we here at Webroot have noticed a large amount of Zeus infections that are spoofing the Bitdefender name.
While infections spoofing AV companies aren’t unusual, it’s been a while since we have seen such a spike on one particular vendor in such a short time period. Most of the names are slight variations, but the numbers are impressive – Overall, we have seen 40,000 unique MD5`s in the last week alone!
The infection being dropped is from the Zeus family of infections, which are banking Trojans designed to steal login information when the user logs into their online banking website.
Infection Information:
- File size is normally around 200-300kb
- It’s located in one path of the users appdata folder with a random path+file name
- C:\users\testPC\Appdata\<random letters>\<random letters.exe
- Usually dropped via an exploit kit (Blackhole being the most popular)
- However, it has also been seen attached to Spam emails
- Can disable Windows Firewall and Security Center
- Has the ability to connect to a remote server to download updates
- Can download other infections
Behaviour:
This infection can get onto a user’s PC via a number of different methods, but the most common is through an exploit kit. The commonly used Blackhole exploit kits uses Java Exploits to drop and execute a file.
Unless the user is very alert, they typically won’t even notice they are infected. Once executed, the infection will try a number of methods to make sure it is automatically ran on start-up.
The first is a registry key which points to the infection directly [1]
The second is a fake Security Center update scheduled task [2]
The third is to create a service that auto starts again point to the infection [3]
- hklm\software\microsoft\windows\currentversion\run “C:\Users\User\Application Data\Obunat\ongekie.exe”
- %windir%\tasks\ SECURITY CENTER UPDATE – 4048458695.JOB
- hklm\system\currentcontrolset\services\securitycenterserver673348880 U5″C:\WINDOWS\system32\igizhaot.exe” -service “C:\Users\User\Application Data\Obunat\ongekie.exe”
After this, the infection may connect to a remote server and receive updates and it can also download other infections (Cryptolocker/ICE and other Rogue AV`s)
Due to the large number of variants, I won’t go through all the behaviours, but generally the infection route follows one of the patterns above. This infection can disable the Windows security center or modify the Firewall settings to allow remote access to the PC.
Examples:
| MD5 |
PATH |
FILE NAME |
FILE SIZE |
|
|
|
|
| 83890496EB018EA524E72CE18CD37209 |
%appdata%\ukhecy |
REHEI.EXE |
221,334KB |
| 70AACDCEC7C9D35393CD9D382C8A0454 |
%appdata%\pawary |
YVPULUV.EXE |
217,222KB |
| ED098AB9A5E13D1B12BE816659C4172C |
%appdata%\qaxuile\ |
PAIDP.EXE |
217,222KB |
| 79776C5BE35DFC4089312D42EC70F903 |
%appdata%\hoydatem\ |
SAAFIFV.EXE |
217,222KB |
| 25D00FC9F06E1720A7B4E4C9293D32AE |
%appdata%\siuvmyw\ |
PYRUOV.EXE |
218,783KB |
| 79776C5BE35DFC4089312D42EC70F903 |
%appdata%\zoobir\ |
EQDUG.EXE |
215,105KB |
| MD5 |
PATH |
FILE NAME |
FILE SIZE |
PC Count |
|
|
|
|
|
| A748FEB8EE581E2225CE7F983E364EC0 |
%temp% |
JAVA_UPDATE_71972350.EXE |
222,827
|
181
|
| EC9FC4EE2AA75D0CD6E0490853F27B21 |
%temp% |
JAVA_UPDATE_7bb116be.EXE |
215,105
|
105
|
| DB97134AFFDA00379CAF3FCD00BBFFFF |
%temp% |
JAVA_UPDATE_93D4FD64.EXE |
216,678
|
231
|
| 4FCD4FD7D3D3A5D24EF663CE3419D7CC |
%temp% |
JAVA_UPDATE_0EEF9307.EXE |
217,222
|
174
|
| D4BC7886F04574E5628FD6BBFBB01C19 |
%temp% |
JAVA_UPDATE_8C3C4799.EXE |
218,873
|
134
|
In total, we have seen over 40k files and this is increasing every hour. Most of the files have a digital vendor that is close to the real version (shown below). As you can see from the screenshot above, a number of the files are pretending to be Java updates.
BitKefender S.R.L. with 869 unique MD5`s
BitNefender S.R.L.|BitNefender Antivirus Scanner with unique 19,305 MD5`s
Removal:
Due to the infection route of this particular infection, it is advisable to have the latest version of Java installed and preferably use a modern secure browser with the latest Windows updates installed. The latest build of Firefox disables Java plugins by default, which should help stop this particular attack vector.
As mentioned earlier, this infection has also been seen to be spread by email. It is advisable to use an email provider that has good SPAM filtration. Google and Microsoft mail services are efficient at blocking these emails.
Always be alert to any email attachments, even if they’re from friends/relatives, and especially executable files that are inside a zip file. Over the Christmas period, we have also noticed a targeted attack from malware authors using well known store names lie Costco, Walmart, etc. in spoof emails.
Since SecureAnywhere doesn’t rely on traditional definitions, we can react instantly to this new trend of Zeus. Webroot SecureAnywhere can safely block this infection. Likewise, if installed on a pre-infected PC, Webroot SecureAnywhere can remove the infection.

by Tyler Moffitt | Dec 31, 2013 | Threat Lab
Top Predictions for 2014
- FBI/ICE MoneyPak
- Cryptolocker
- Rogues
As this year comes to a close we’ve seen some measurable progress on the infiltration techniques for malware. We’re going to give you some insight into some of the top threats of 2013 and what it could mean for 2014.
FBI/ICE MoneyPak
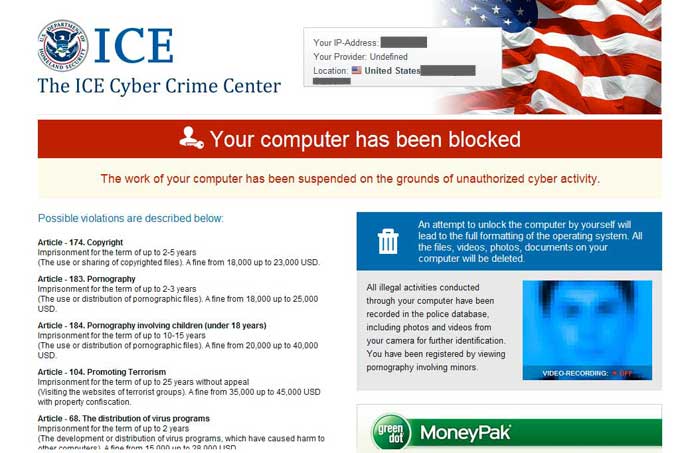
We saw some frightening improvements with Ransomware this year. FBI/ICE MoneyPak or Win32.Reveton was a huge hit to the PC community. Although first seen in 2012 it wasn’t until 2013 that it was tweaked to be one of the most annoying and difficult Ransomware to remove. Once dropped on your computer and executed, either by email attachment, “video codec” (or the like), it eliminates all the safemodes, taskmanager and shows nothing but this screen. You have no options to launch any applications like system restore, regedit as the explorer shell hijacked. Most of these also start themselves in new user accounts so the only removal is to be blocked at dropped by your Anti-Virus or boot to a linux disc and remove it there. Since this is still super effective (especially zero day variants) against most anti-virus I would expect to see more of this. I foresee naming changing and the typical scare tactics text of “violations” to change as once more and more people become educated on these threats its really easy to just slap on a new image and text and fool you again.
Cryptolocker
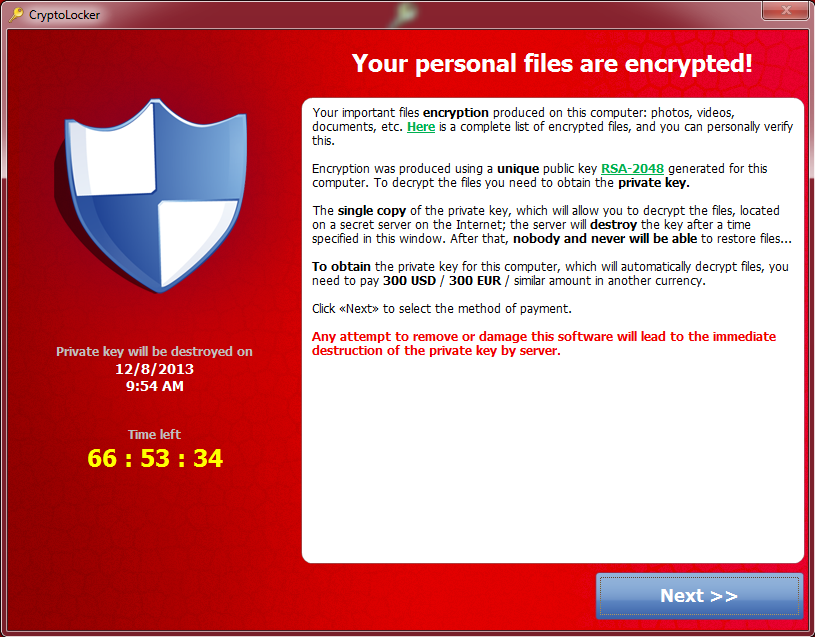
Not a good sight to see
This new Cryptolocker that’s got everyone in a scare is no joke. Once on your machine this Ransomware will use about 10% CPU power to encrypt all your documents unnoticed (*.odt, *.ods, *.odp, *.odm, *.odc, *.odb, *.doc, *.docx, *.docm, *.wps, *.xls, *.xlsx, *.xlsm, *.xlsb, *.xlk, *.ppt, *.pptx, *.pptm, *.mdb, *.accdb, *.pst, *.dwg, *.dxf, *.dxg, *.wpd, *.rtf, *.wb2, *.mdf, *.dbf, *.psd, *.pdd, *.pdf, *.eps, *.ai, *.indd, *.cdr, *.jpe, *.jpg, *.avi, *.mp3, *.wma, *.wmv, *.wav, *.divx, *.mp4, *.dng, *.3fr, *.arw, *.srf, *.sr2, *.bay, *.crw, *.cr2, *.dcr, *.kdc, *.erf, *.mef, *.mrw, *.nef, *.nrw, *.orf, *.raf, *.raw, *.rwl, *.rw2, *.r3d, *.ptx, *.pef, *.srw, *.x3f, *.der, *.cer, *.crt, *.pem, *.pfx, *.p12, *.p7b, *.p7c).
Once it’s encrypted all files found on your local drives as well as mapped network drives it will then show you the above screen. This isn’t like previous versions that stored the decryption key in the initial drop, but instead has the key created and stored on a remote server and the key is different with every unique infection. This leaves you with little to no recourse unless you have a back up or a system restore point saved. Shadow Explorer is a lovely tool that will allow you to restore all files that you had at any given restore point using the windows built-in Volume Shadow Service (Vista/7/8 only). Be warned however, this only works on files stored on the same hard drive the operating system is on so if you lost files on other slave drives in your box or network drives then you have no option but to pay. Also a growing percentage of the Cryptolockers we’ve seen are now executing this command off the bat:
“C:\Windows\SYsWOW64\cmd.exe” /C “C:\Windows\Sysnative\vssadmin.exe” Delete Shadows /All /Quiet
This completely removes all hope of using tools like Shadow Explorer. Expect to see plenty more Cryptolocker in the future, and expect them to pack more tricks to prevent you from using tools to restore files and prevent Anti-virus from detecting them.
Rogues
We saw some impressive improvements in Rogues over the year 2013. Not only are the malware authors putting more effort into the interface to make it more realistic, but they’re even taking pictures of you! Specifically we came across some samples that if you didn’t pay in 10 minutes or so it would actually capture pictures using the built-in webcam. It claimed that “detected viruses took these pictures and would send them to unauthorized users.” However, we saw no network traffic other than the initial drop of components. What I expect to see in the future is a merge of this and cryptolocker techniques. Given the extreme violation of privacy that taking unauthorized pictures with the webcam poses I can definitely see variants actually threatening to distribute this data as leverage to win over the ransom.
If you have any questions or comments please let us know!

by Blog Staff | Dec 27, 2013 | Threat Lab
It’s that time of the year! The moment when we reflect back on the cybercrime tactics, techniques and procedures (TTPs) that shaped 2013, in order to constructively speculate on what’s to come for 2014 in terms of fraudulent and malicious campaigns, orchestrated by opportunistic cybercriminal adversaries across the globe. Throughout 2013, we continued to observe and profile TTPs, which were crucial for the success, profitability and growth of the cybercrime ecosystem internationally, such as, for instance, widespread proliferation of the campaigns, professionalism and the implementation of basic business/economic/marketing concepts, improved QA (Quality Assurance), vertical integration in an attempt to occupy market share across multiple verticals, as well as the re-emergence of known, and well proven cybercrime-friendly concepts like standardization and DIY (do-it-yourself) type of propositions.
Eager to learn more? Keep reading!
(more…)

by Blog Staff | Dec 19, 2013 | Threat Lab
The over-hyped market valuation of the buzzing P2P E-currency, Bitcoin, quickly gained the attention of cybercriminals internationally who promptly adapted to its sky rocketing valuation by releasing commercially available stealth Bitcoin miners, Bitcoin wallet stealing malware, as well as actually starting to offer the source code for their releases in an attempt to monetize their know-how and expertise in this area. Throughout 2013, we profiled several subscription based stealth Bitcoin mining tools, and predicted that it’s only a matter of time before this still developing market segment starts proliferating with more cybercriminals offering their stealth Bitcoin releases to prospective customers. Not only are we continuing to see an increase in terms of the number of tools offered, but also, some cybercriminals are actually starting to offer the source code for their releases, which, as we’ve seen in the past, has resulted in an increase in ‘vallue-added’ releases on behalf of fellow cybercriminals implementing features based on their perceived value, or through interaction with prospective customers.
What are cybercriminals up to in terms of stealth Bitcoin miners these days? Let’s profile several of the (international) underground market share leading commercially available stealth Bitcoin miners, emphasize on their features, as well as just how easy it is to fraudulently mine Bitcoin/Litecoin these days, with the affected user never really knowing what’s taking place on their PC.
(more…)

by Grayson Milbourne | Dec 18, 2013 | Threat Lab
Top 5 Enterprise Threat Predictions for 2014
- Ransomware for the enterprise
- Compromised clouds
- Advanced mobile phishing tactics
- APT’s focus on mobile
- Mobile device linked to major compromise
When thinking about cyber-security and looking back over the years, there is a clear and unfortunate trend which doesn’t show any signs of slowing. The trend is that year over year, more and more cyber-attacks occur while at the same time, the sophistication of attacks continues to evolve. Additionally, a matured cyber-crime as a service (CCaaS) ecosystem has enabled practically anyone to get involved. Combine this with the growing cost of defenses and the reality that many solutions are only somewhat effective and you can see that the feasibility of cyber-security is, well, getting farther and farther way.
Now, I could go into the various factors which are causing this losing battle, such as societies overwhelming desire to pick convenience over security, or the mentality that, ‘it will never happen to me;’ but I’ll save that for another blog. Instead, I’m going to consider the cyber-security events from the past few years and predict the top 5 threats enterprises are likely to face in 2014.
First, I should note that these predictions are not ordered or ranked in any way, they are simply 5 enterprise focused security events you will likely read about next year along with my supporting reasons for the prediction. So let’s get started!
Prediction # 1 – Ransomware for the enterprise
Early in 2013, a new type of ransomware, self-named Cryptolocker, was discovered which included a few very significant and very frightening changes. Unlike older ransomware, which would store the decryption key within the executing binary, Cryptolocker stores the encryption key in their C&C server network and with each new infection, a new key is used. This makes it next to impossible to decrypt files modified by the infection. The other big change is that Cryptolocker doesn’t give you a lot of time to pay the ransom, often around $300, with only 72 hours to comply before the decryption key is destroyed. These tactics have made Cryptolocker the most advanced and most aggressive ransomware discovered to date, however Cryptolocker’s focus remains primarily on individual users which is evident by the distribution tactic of spam email.
Based on Cryptolocker’s tactical advancements and success, it is only a matter of time before an enterprise becomes the target of a similar form of attack. Many people are gladly handing over $300 to regain access to their personal files, imagine what an enterprise would pay to restore its data. My guess is at least, in my best Dr. Evil voice, 1 million dollars!
Prediction # 2 – Compromised clouds
While cloud infrastructure has been around for a while, 2013 saw very widespread adoption as companies looked to save money and to run more efficiently. While the cloud has a number of benefits, additional security isn’t always one of them and not are all clouds are equal. In cases where companies are opting for public cloud infrastructure, they trust the security measures put in place by the cloud hosting service. This basically extends the attackable surface, increases vectors for attack and reduces the overall control a business has to prevent an attack. Of course, there is the option for a private cloud, but for most this option is too expensive and/or overkill for their needs.
As utilizing cloud services becomes the new norm, it will also become a more ideal target for cyber-crime and attack. Consider, if you successfully compromise a cloud hosting provider, you likely gain access to all data within which would include that of dozens if not hundreds or even thousands of companies.
Prediction # 3 – Advanced mobile phishing tactics
Phishing isn’t new by any means, however the utilization of this attack vector continues to grow at record pace while the tactics used continue to evolve. In 2013 we saw new innovative attacks involving the human experience, either over the phone or in person. Waterhole attacks which identify and compromise websites likely to be visited by the primary target. And mobile attacks ranging from phishing SMS messages to rogue and misleading advertisements. Then, of course, there is the mass of phishing spam email contrasted by the ultra-precise spear-phishing attack. The trouble is, phishing attacks are so effective because they pay especially close attention to the human experience and our desire to trust someone we know. When aimed at an enterprise, all an attacker has to accomplish is tricking one individual and research has shown it only takes about 15 targets for this to be guaranteed.
But what about mobile? As today’s workforce continues to shift to mobile devices and platforms, so will the tactics used by attackers. Mobile is a ripe target for attack as the user experience is focused on convenience over security. Combine this with the one touch access and lack of authentication and it is easy to see why I predict new advanced phishing tactics aimed at compromising mobile devices.
Prediction # 4 – APT’s focus on mobile
2013 saw a massive migration to smartphones and mobile OS’s as well as widespread adoption of BYOD; and the cyber-crime community definitely took notice. This past year, Webroot’s mobile research team discovered over 1 million malicious Android apps which is over 1000% growth from the previous year. But compromising a mobile device doesn’t have to start with an app. We’ve seen recent website hacks only modify pages for mobile devices, a tactic avoid detection, but also evidence that mobile is becoming a primary focus. Additionally, there have been numerous new mobile related services popping up in underground markets. Services range from SMS flooding, malicious app creation, mobile botnet building tools and even, and most disturbing, trusted developer credentials which can be used to post apps to major app markets like Google Play.
Because mobile devices contain so much information and very little security or authentication, they will increasingly be the focus for attacks. When considering the planning that goes into today’s APT backed attack, it only makes sense that highly organized cyber-crime gangs and/or state launched attacks will target mobile devices as part of their future attacks.
Prediction # 5 –Mobile device linked to major compromise
My final prediction again relates to mobile, and the reasons are largely expressed in the previous two predictions. There is a clear trend for the adoption of personal mobile devices in the workplace but it isn’t being matched with employee education, policy or security. The reality is that BYOD can be done correctly when four key areas are secured. These are app protection, web protection, data protection and device protection. By securing these areas, personal devices can be used for personal use and also safe to connect to the corporate network.
The trouble however, is that most enterprises are allowing BYOD without proper planning, education or policy in place. This lack of regulation combined with lacking security features for mobile devices will eventually lead to a major compromise.
So, what can your company do to stop these threats? Well, employee education to drive awareness of the types of attacks and their consequences is a good first step. Security solutions have also advanced with better threat awareness, and in Webroot’s case, are harvesting the power of crowds in the cloud to rapidly identify the newest threats. For more information, feel free to shoot me an email at gmilbourne@webroot.com or visit our website at http://www.webroot.com/.











