
by Blog Staff | Oct 9, 2013 | Threat Lab
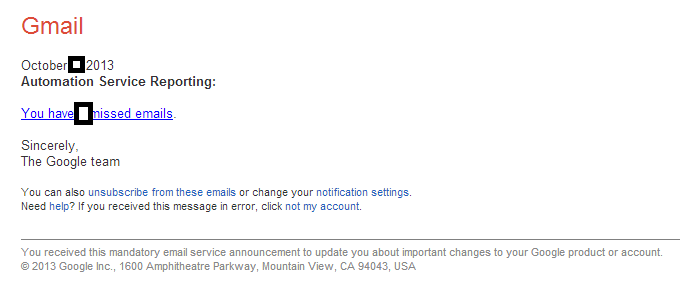
Pharmaceutical scammers are currently mass mailing tens of thousands of fake emails, impersonating Google’s GMail in an attempt to trick its users into clicking on the links found in the spamvertised emails. Once users click on them, they’re automatically exposed to counterfeit pharmaceutical items, with the scammers behind the campaign attempting to capitalize on the ‘impulsive purchase’ type of social engineering tactic typical for this kind of campaign.
Sample screenshot of the spamvertised email:
Sample screenshot of the landing pharmacautical scams page:
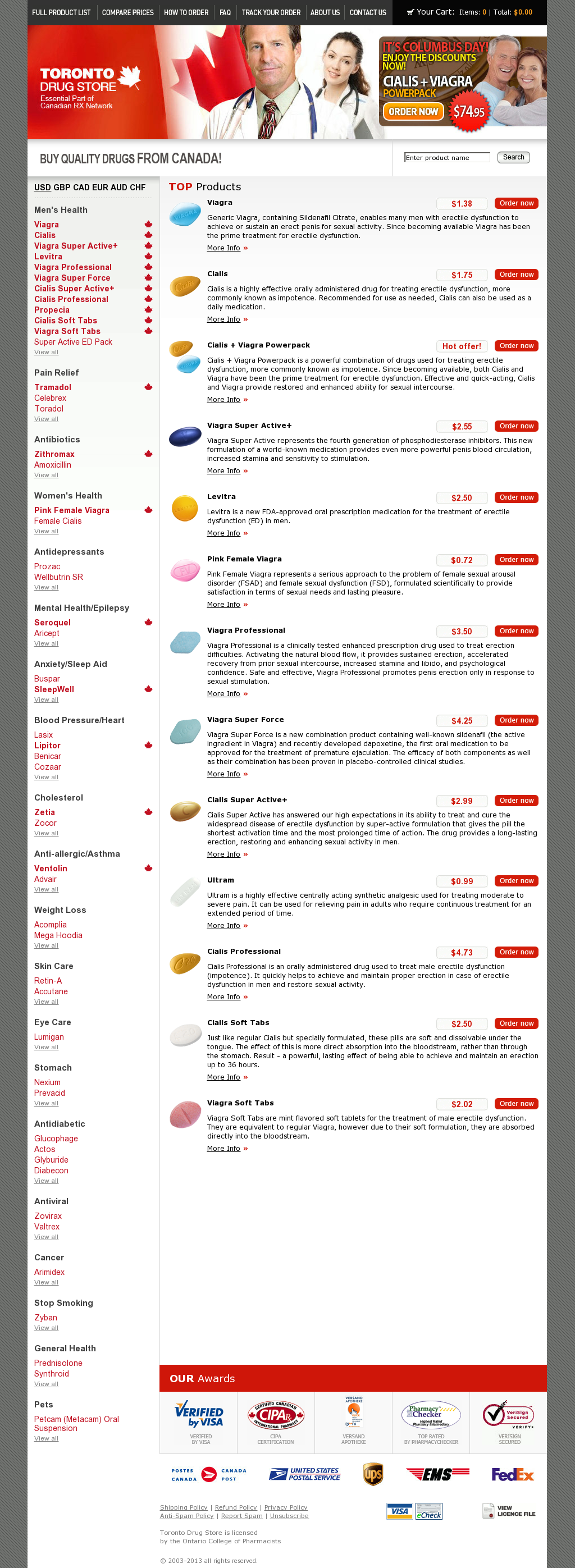
Landing URL: shirazrx.com – 85.95.236.188 – Email: ganzhorn@shirazrx.com
The following pharmaceutical scam domains also respond to the same IP:
asqrtplc.com
pharmlevitrafitch.com
myprescriptionhealth.com
viagrasequester.com
rxjeanstra.at
medoverdose.at
rxtreatments.ru
The following pharmaceutical scam domains are also known to have responded to the same IP (85.95.236.188):
albertapharm.com
albertapharm.net
antacid.fatwelnessdiet.com
anticlockwise.medwelopioid.com
antiquarianism.medwelopioid.com
assignment.healthcareviagrabiotech.com
canadaprescriptioninc.at
carburettors.opioidsalemeds.com
debars.dentalcarepharmacy.com
deliquescent.homemedicalrx.com
dipoles.fatdietpharm.com
drughealthcareprescription.com
drugstoreabortion.com
drugstorepharmetro.com
heads.fatpillsdiet.com
hebalk.ru
herbalviagrasildenafil.com
inflammatory.patientsprescriptionmedical.com
levitrachrome.at
levitrapillkorsinsky.com
This isn’t the first, and definitely not the last time pharmaceutical scammers brand-jack reputable brands in order to trick users into clicking on the links found in the fake emails, as we’ve already seen them brand-jack Facebook’s Notification System, YouTube, as well as the non-existent Google Pharmacy. Thanks to the (natural) existence of affiliate networks for pharmaceutical items, we expect that users will continue falling victim to these pseudo-bargain deals, fueling the the growth of the cybercrime economy and the need for more cybersecurity awareness.
Our advice? Never bargain with your health, spot the scam and report it.

by Blog Staff | Oct 8, 2013 | Threat Lab
Realizing the market segment potential of bulletproof hosting services in a post-Russian Business Network (RBN) world — although it can be easily argued that as long as its operators are at large they will remain in business — cybercriminals continue supplying the cybercrime ecosystem with market-relevant propositions. It empowers anyone with the ability to host fraudulent and malicious content online. A newly launched Virtual Dedicated Server (VDS) type of bulletproof hosting vendor is pitching itself to prospective cybercriminals, offering them hosting services for spam, malware, brute-forcing tools, blackhat SEO tools, C&C (command and control) servers, exploit kits and warez. In addition to offering the “standard cybercrime-friendly” bulletproof hosting package, the vendor is also excelling in terms of the hardware it relies on for providing the infrastructure to its customers.
Let’s take a peek inside the infrastructure ‘facility’, and discuss the vendor’s business model in the over-populated market segment for bulletproof hosting services, currently available to prospective cybercriminals.
(more…)

by Blog Staff | Oct 7, 2013 | Threat Lab
We continue to spot new cybercrime ecosystem propositions for spam-ready, cybercrime-friendly SMTP (Simple Mail Transfer Protocol) targeting QA (Quality Assurance) aware cybercriminals looking to gain access to dedicated mail servers with clean IP reputation, ensuring that their campaigns will reach the recipient’s Inbox. Relying on ‘in-house’ built infrastructure or direct outsourcing to bulletproof hosting providers, these services continue empowering prospective customers with managed, popular spam software compatible services, potentially exposing millions of users to fraudulent or malicious email campaigns.
Let’s discuss yet another managed service offering spam-ready SMTP servers, and connect it to malicious campaigns that have directly interacted with the same infrastructure it’s currently hosted on, indicating that it’s already “in business”.
(more…)

by Blog Staff | Oct 4, 2013 | Threat Lab
Thanks to the free, commercial availability of mass Web site hacking tools, in combination with hundreds of thousands of misconfigured and unpatched Web sites, blogs and forums currently susceptible to exploitation, cybercriminals are successfully monetizing the compromise process. They are setting up iFrame based traffic E-shops and offering access to hijacked legitimate traffic to be later on converted to malware-infected hosts.
Despite the fact that the iFrame traffic E-shop that I’ll discuss in this post is pitching itself as a “legitimate traffic service”, it’s also explicitly emphasizing on the fact that iFrame based traffic is perfectly suitable to be used for Web malware exploitation kits. Let’s take a closer look at the actual (international) underground market ad, and discuss the relevance of these E-shops in today’s modern cybercrime ecosystem.
(more…)

by Blog Staff | Oct 4, 2013 | Threat Lab
Standardization is the cybercrime ecosystem’s efficiency-oriented mentality to the general business ‘threat’ posed by inefficiencies and lack of near real-time capitalization on (fraudulent/malicious) business opportunities. Ever since the first (public) discovery of managed spam appliances back in 2007, it has become evident that cybercriminals are no strangers to basic market penetration/market growth/market development business concepts. Whether it’s the template-ization of malware-serving sites, money mule recruitment, spamming or blackhat SEO, this efficiency-oriented mentality can be observed in virtually each and every market segment of the ecosystem.
In this post, I’ll discuss a recent example of standardization, in particular, a blackhat SEO friendly VPS (Virtual Private Server) that comes with over a dozen multi-blackhat-seo-friendly product licenses from third-party products integrated. It empowers potential customers new to this unethical and potentially fraudulent/malicious practice with everything they need to hijack legitimate traffic from major search engines internationally.
(more…)

by Blog Staff | Oct 3, 2013 | Threat Lab
DDoS for hire has always been an inseparable part of the portfolio of services offered by the cybercrime ecosystem. With DDoS extortion continuing to go largely under-reported, throughout the last couple of years — mainly due to the inefficiencies in the business model — the practice also matured into a ‘value-added’ service offered to cybercriminals who’d do their best to distract the attention of a financial institution they’re about to (virtually) rob.
Operating online — under both private and public form — since 2008, the DDoS for hire service that I’ll discuss in the this post is not just offering DDoS attack and Anti-DDoS protection capabilities to potential customers, but also, is ‘vertically integrating’ within the ecosystem by starting to offer TDoS (Telephony Denial of Service Attack) services to prospective customers.
(more…)

by Blog Staff | Oct 2, 2013 | Threat Lab
A circulating malicious spam campaign attempts to trick T-Mobile customers into thinking that they’ve received a password-protected MMS. However, once gullible and socially engineered users execute the malicious attachment, they automatically compromise the confidentiality and integrity of their PCs, allowing the cybercriminals behind the campaign to gain complete control of their PCs.
(more…)

by Grayson Milbourne | Oct 1, 2013 | Threat Lab
In this edition of the Webroot ThreatVlog, Grayson Milbourne talks about the rise of digital phisihing schemes on the internet and how they affect the victims. He then unveils a brand new product from Webroot that is designed to keep users protected from websites that are malicious in nature that could be trying to capture credit card and other personal information.
http://youtu.be/ERyqo1Ljlno

by Blog Staff | Oct 1, 2013 | Threat Lab
The emergence and sophistication of DIY botnet generating tools has lowered the entry barriers into the world of cybercrime. With ever-increasing professionalism and QA (Quality Assurance) applied by cybercriminals, in combination with bulletproof cybercrime-friendly hosting providers, these tactics represent key success factors for an increased life cycle of any given fraudulent/malicious campaign. Throughout the years, we’ve witnessed the adoption of multiple bulletproof hosting infrastructure techniques for increasing the life cycle of campaigns,with a clear trend towards diversification, rotation or C&C communication techniques, and most importantly, the clear presence of a KISS (Keep It Simple Stupid) type of pragmatic mentality; especially in terms of utilizing HTTP based C&C communication channels for botnet operation.
In this post, I’ll discuss a managed botnet setup as a service, targeting novice cybercriminals who are looking for remote assistance in the process of setting up the C&C infrastructure for their most recently purchased DIY botnet generation tool. I’ll also discuss the relevance of these services in the content of the (sophisticated) competition, that’s been in business for years, possessing the necessary know-how to keep a customer’s fraudulent/malicious campaign up and running.
(more…)

by Blog Staff | Oct 1, 2013 | Threat Lab
The perceived decline in the use of blackhat SEO (search engine optimization) tactics for delivering malicious/fraudulent content over the last couple of years, does not necessarily mean that cybercriminals have somehow abandoned the concept of abusing the world’s most popular search engines. The fact is, this tactic remains effective at reaching users who, on the majority of occasions, trust that that the search result links are malware/exploit free. Unfortunately, that’s not the case. Cybercriminals continue introducing new tactics helping fraudulent adversaries to quickly build up and aggregate millions of legitimate visitors, to be later on exposed to online scams or directly converted to malware-infected hosts. This is achieved through cybercrime-friendly underground market traffic exchange networks offering positive ROI (Return on Investment) in the process.
In this post, I’ll take a peek inside a blackhat SEO/cybercrime-friendly doorways management script, discuss its core features, and the ways cybercriminals are currently abusing its ability to populate major search engines with hundreds of millions of search queries relevant bogus Web pages, most commonly hosted on compromised Web servers in an attempt by the cybercriminals behind the campaign to take advantage of the compromised Web site’s high page rank.
(more…)










